How CyberSecurity Asset Management with External Attack Surface Management Improves Compliance for the Protection of National Infrastructure
Since 2018, the Cybersecurity and Infrastructure Security Agency (CISA) of the U.S. government have focused on reducing risk and building resilience to cyber and physical threats to the nation’s infrastructure. To facilitate collaboration with the private sector https://www.cisa.gov/jen-easterly, CISA has published the organization’s first Comprehensive CISA Strategic Plan, mapping out initiatives focused on four major goals during 2023-25.
What you need to know
The CISA Strategic Plan describes four ambitious goals. The first three describe how CISA will work to reduce risk and build resilience and the fourth is about building the internal workforce within the agency to execute the plan. Each goal is summarized below:
Goal 1 – Cyber Defense and Cyber Resilience
The first goal of the CISA Strategic Plan addresses the need for both proactive threat detection and rapid response.
From CISA:
First, we will spearhead the national effort to ensure the defense and resilience of cyberspace. Serving as America’s cyber defense agency, we will spearhead the national effort to defend against cyber threat actors that target U.S. critical infrastructure, federal and SLTT governments, the private sector, and the American people. CISA must lean forward in our cyber defense mission toward collaborative, proactive risk reduction. Working with our many partners, it is CISA’s responsibility to help mitigate the most significant cyber risks to the country’s National Critical Functions, both as these risks emerge and before a major incident occurs.
Goal 2- Reduce Cyber Risk
The second goal of the CISA Strategic Plan is for cyber risk reduction and resilience.
From CISA:
Second, we will reduce risks to, and strengthen the resilience of, America’s critical infrastructure. Our safety and security depend on the ability of critical infrastructure to prepare for and adapt to changing conditions and to withstand and recover rapidly from disruptions. CISA coordinates a national effort to secure and protect against critical infrastructure risks. This national effort is centered around identifying which systems and assets are truly critical to the nation, understanding how they are vulnerable, and taking action to manage and reduce risks to them. We serve as a key partner to critical infrastructure owners and operators nationwide to help reduce risks and build their security capacity to withstand new threats and disruptions, whether from cyberattacks or natural hazards and physical threats.
Goal 3 – Improve Operational Efficiency
The third goal of the CISA Strategic Plan hinges on threat response, information sharing, and collaboration to increase threat intelligence.
From CISA:
Third, we will strengthen whole-of-nation operational collaboration and information sharing. At the heart of CISA’s mission is partnership and collaboration. Securing our nation’s cyber and physical infrastructure is a shared responsibility. We are challenging traditional ways of doing business and actively working with our government, industry, academic, and international partners to move toward more forward-leaning, action-oriented collaboration. We are also committed to growing and strengthening our Agency’s regional presence to more effectively deliver the assistance our stakeholders need.
Goal 4 – Focus on the Workforce
The fourth goal of the CISA Strategic Plan encourages a culture committed to excellence, innovation, and ownership.
From CISA:
And fourth, foundational to our success, we will unify as One CISA through integrated functions, capabilities, and workforce. We will succeed because of our people. We are building a culture of excellence based on core values and core principles that prize teamwork and collaboration, innovation and inclusion, ownership and empowerment, and transparency and trust. As one team unified behind our shared mission, we will “work smart” to operate in an efficient and cost-effective manner.
How Qualys Can We Can Help
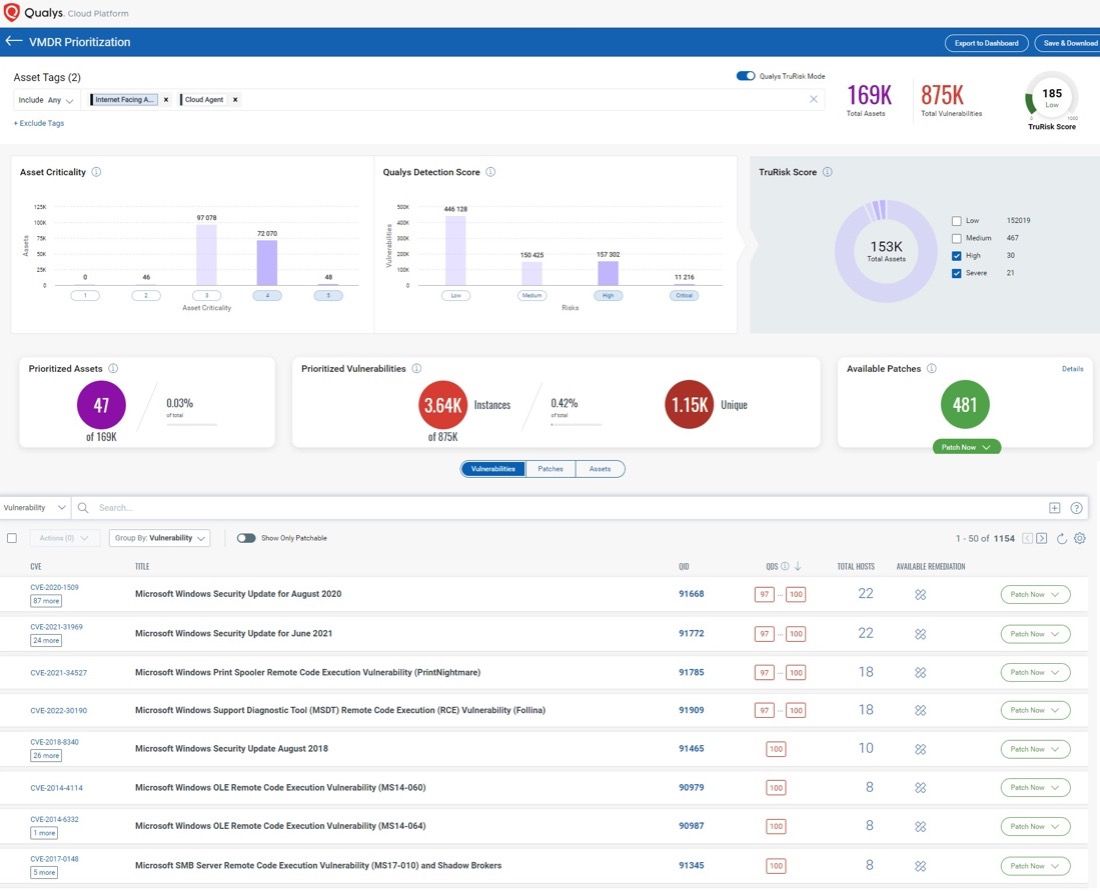
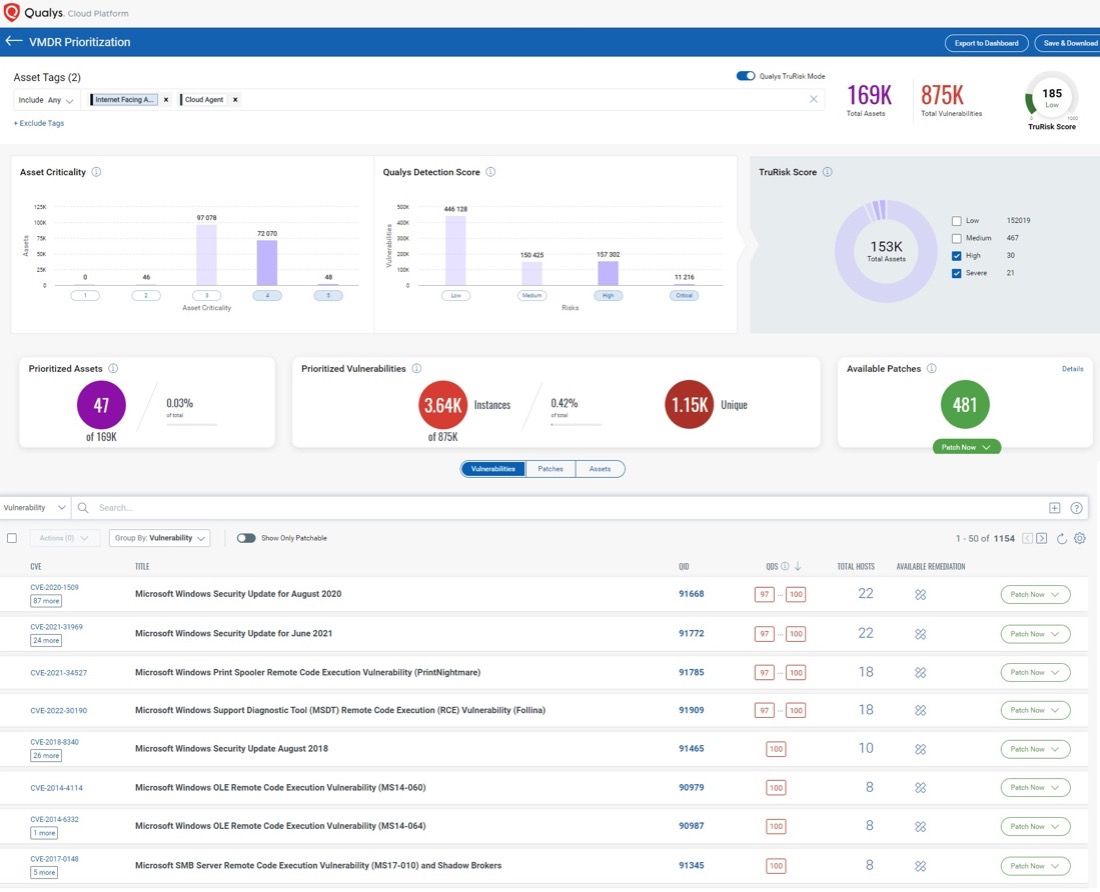
To bolster VM programs with expanded asset visibility and cyber risk reduction, Qualys VMDR comes with TruRisk™ for a risk-based approach to vulnerability and risk posture assessment. In addition to TruRisk, VMDR can be further empowered with External Attack Surface Management (EASM) by adding CyberSecurity Attack Surface Management, working in conjunction with Qualys sensors (scanners, cloud connectors, container sensors, cloud agents, passive sensors, and APIs) to continuously discover all internal and external internet-facing assets.
With the built-in integration of VMDR and CyberSecurity Attack Surface Management, security practitioners can continuously maintain oversight of 100% of their assets in real time, assuring that new vulnerabilities are accounted for, managed, and remediated.
In pursuing CISA objectives, Qualys VMDR with EASM provides a key toolset that both security practitioners and IT leaders can leverage to improve all four goals of the CISA Strategic Plan. With this new solution, customers can:
- Obtain actionable intelligence, visibility, and insight into the entire internal and external attack surface.
- Discover domains, subdomains, and certificates within the enterprise and in subsidiaries and business partners for full visibility of remotely exploitable vulnerabilities – including previously unknown devices.
- Expose “shadow IT” and baseline discrepancies, including VMs, containers, functions-as-a-service, and IoT that spin up faster than IT can track with legacy tools.
- Gain an outside-in view of internet-facing assets to spot security endpoint blind spots.
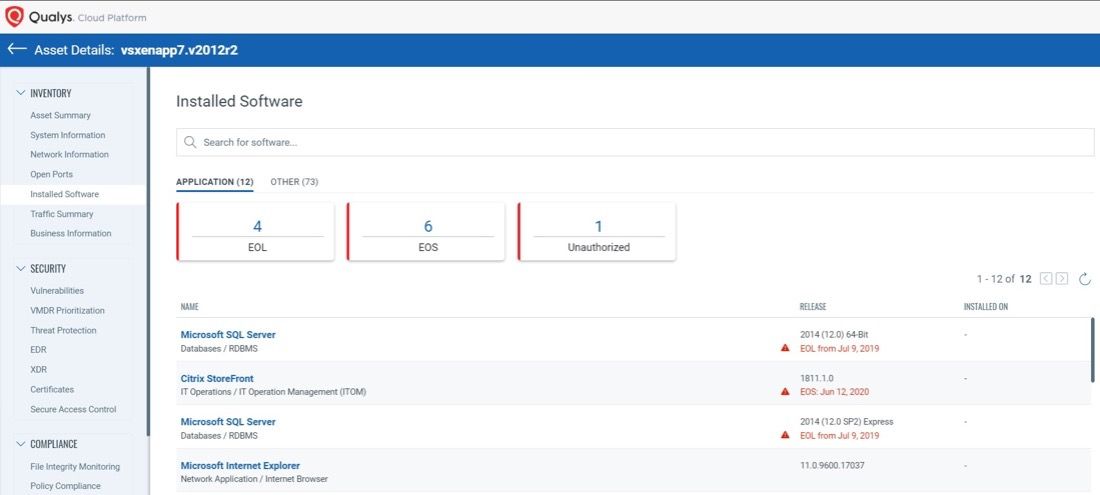
- Reduce exposure to malicious software with CISA-compliant end-of-life (EOL) and end-of-support (EOS) software, which tracks software versioning, OS status and related vulnerabilities.
Benefits of VMDR with External Attack Surface Management (EASM)
- Improve Risk Posture: VMDR with Qualys TruRisk enables a rigorous cyber risk management process based on the automatic correlation of discovered assets, associated vulnerabilities found, and their degree of direct impact on the customer’s unique business for better implementation of proactive and preventative security policy.
- Harden your Network from External Threats: Continuously harden your network from external threats with an attacker’s view of your Environment with External Attack Surface Management (EASM), which is included in CyberSecurity Attack Surface Management.
- Reduce Software Supply Chain Risk: VMDR and CyberSecurity Attack Surface Management provide end-of-life software tracking compliant with CISA guidelines to help expose “shadow IT” and baseline discrepancies, including VMs, containers, functions-as-a-service, and IoT that spin up faster than IT can track with legacy tools.
- Prioritize and Focus Remediation Actions: VMDR and CyberSecurity Attack Surface Management allow users to assign risk profiles to focus security prioritization efforts on high-importance and high-risk applications first; it does so by defining key business and technical context and tagging assets and asset groups accordingly. Asset Criticality is a user-defined measure of asset function, environment, and service.
- Bridge the IT-Security Gap: Bridge the IT-Security gap that exists in most enterprise organizations and addresses threats faster with CMDB integrations that support ITSM ticketing, patching, and more.
- Proactively Detect and Monitor Security Gaps: VMDR and CyberSecurity Attack Surface Management automatically assign the asset criticality score to a tag and the corresponding asset with organizational in-context enrichment data. This context enables analysis of threats and misconfigurations in real time, with six-sigma accuracy.
Learning by doing is always the best way. Try VMDR today to see how the Qualys Platform can help you achieve the 4 goals of the CISA Strategic Plan.
Start your free trial of Qualys VMDR with Qualys TruRiskTM
Read the following blogs for more information on VMDR integration with CMBD and ITSM