
2023-10-6 08:14:6 Author: blog.qualys.com(查看原文) 阅读量:41 收藏
On Wednesday, October 4, 2023, the curl project maintainers announced pre-notification for curl version 8.4.0 to be released on October 11. This version will fix two new vulnerabilities with one high and one low-severity CVE. The prenotification stated that the high-severity issue is arguably the most critical security flaw identified in curl in recent history.
Details regarding the vulnerabilities and the new version will be disclosed around 06:00 UTC October 11, 2023.
What is Curl and libcurl?
Curl is a versatile open-source command-line tool for transferring data with URL syntax, supporting many network protocols like SSL, TLS, HTTP, FTP, SMTP, and more. Developers and system administrators prevalently use it to interact with APIs, download files, and create automated workflows among various internet-based tasks.
On the other hand, libcurl serves as the powerhouse behind Curl, a free, client-side URL transfer library that supports the same wide range of protocols. It allows developers to add robust data transfer functionality to their applications, ensuring their software can communicate with servers for tasks like sending HTTP requests, managing cookies, and handling authentication. This makes it a vital tool for developing interconnected and web-aware applications.
What are Curl Vulnerabilities CVE-2023-38545 & CVE-2023-38546?
Curl 8.4.0 is scheduled for release on October 11. It addresses two vulnerabilities, identified as CVE-2023-38545 and CVE-2023-38546, with the former being of high severity and affecting both libcurl and the curl tool, while the latter is of low severity and impacts only libcurl. Specific details on the version range affected or further information about the vulnerabilities are not available pre-release to prevent aiding the identification of the problem areas. More comprehensive information, including details about the CVEs, will be published at 06:00 UTC on the release day. No, API or ABI changes are expected in the forthcoming release.
Vulnerable versions
With specific version range details undisclosed to prevent pre-release problem identification, the vulnerabilities will be fixed in curl version 8.4.0. The forthcoming high-severity issue in libcurl demands cautious attention, though it might not affect all users. Updating the shared libcurl library is the anticipated universal fix across operating systems. Yet, according to the maintainer, a sizable number of rebuilds are expected, particularly in docker images and similar entities that incorporate their libcurl copies.
What should organizations do?
Organizations should urgently inventory and scan all systems utilizing curl and libcurl, anticipating identifying potentially vulnerable versions once details are disclosed with the release of Curl 8.4.0 on October 11. Immediate update implementation upon release is essential to safeguard systems against these pressing vulnerabilities (CVE-2023-38545 and CVE-2023-38546).
How can Qualys Help?
Inventory Curl and libcurl Using Qualys CSAM
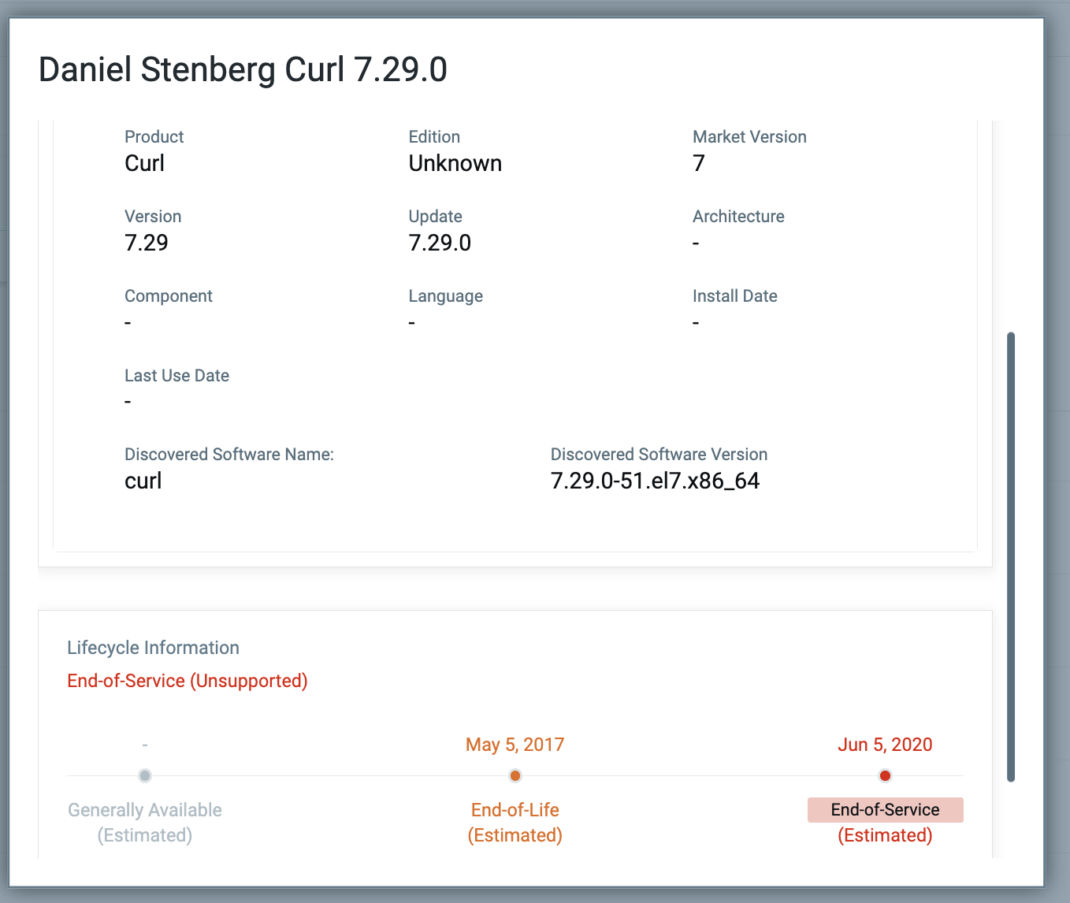
Qualys CSAM makes it easy to identify assets containing curl/libcurl.
The following QQL query will identify assets with curl/libcurl installed:
Query: software: (name: 'libcurl' or name: 'curl')

The QQL below assists in identifying assets with potentially vulnerable versions of curl/libcurl installed.
Query: software:(name:’curl’ and version < 8.4.0 )

Tag Potentially vulnerable assets with CSAM
In addition to identifying the assets, Qualys also recommends that customers tag the assets with curl/libcurl installed.

Discover Vulnerable Instances Using Qualys VMDR
Once the vulnerability is disclosed, on October 11, each vendor will release backported patches for these vulnerabilities. The Qualys Threat Research Unit (TRU) closely tracking the vulnerability and will release QIDs to detect those backported versions.
Patch Vulnerable Systems Using Qualys Patch Management (PM)
Once all curl vulnerabilities are found in the environment, customers can use Qualys Patch Management to patch vulnerable applications.
As libcurl is a library used by many OSes and applications, it is safe to assume that in the near future many of those applications will issue a patch to fix this libcurl vulnerability. Qualys Patch Management can patch those applications on Windows, Linux and MacOS.
Qualys Patch Management also offers a way to execute PowerShell scripts on Windows and shell scripts on Linux machines. It can be leveraged to quickly create mitigation steps.
Conclusion
In light of the imminent release of curl 8.4.0 and the critical security flaws it aims to address, organizations must act swiftly to inventory, scan, and update all systems utilizing curl and libcurl. In particular, the gravity of the high-severity vulnerability mandates immediate and cautious attention to safeguarding interconnected and web-aware applications, ensuring the rich data transfer functionality curl and libcurl provide remain unimpaired and secure. The detailed insights into these vulnerabilities and the corrective measures will become pivotal following the clear disclosure slated for 06:00 UTC, October 11, 2023.
如有侵权请联系:admin#unsafe.sh