Trail of Bits is publicly disclosing a vulnerability (CVE-2023-38596) that affects iOS versions 10 and later and macOS versions 10.12 and later. The flaw, identified by Will Brattain, resides in Apple’s App Transport Security (ATS) protocol handling. We discovered that Apple’s ATS fails to require the encryption of connections to IP addresses and *.local hostnames, which can leave applications vulnerable to information disclosure vulnerabilities and machine-in-the-middle (MitM) attacks.
Note: Apple published an advisory on September 18, 2023 confirming that CVE-2023-38596 had been fixed.
Background
ATS is a network security feature enabled by default in applications linked against iOS 9+ and macOS 10.11+ software development kits (SDK). ATS requires the use of the Transport Layer Security (TLS) protocol for network connections made by an application. Before iOS version 10 and macOS version 10.12, ATS disallowed connections to .local domains and IP addresses by default but allowed for the configuration of exceptions. As of iOS version 10 and macOS version 10.12, connections to .local domains and IP addresses are allowed by default.
Proof of concept
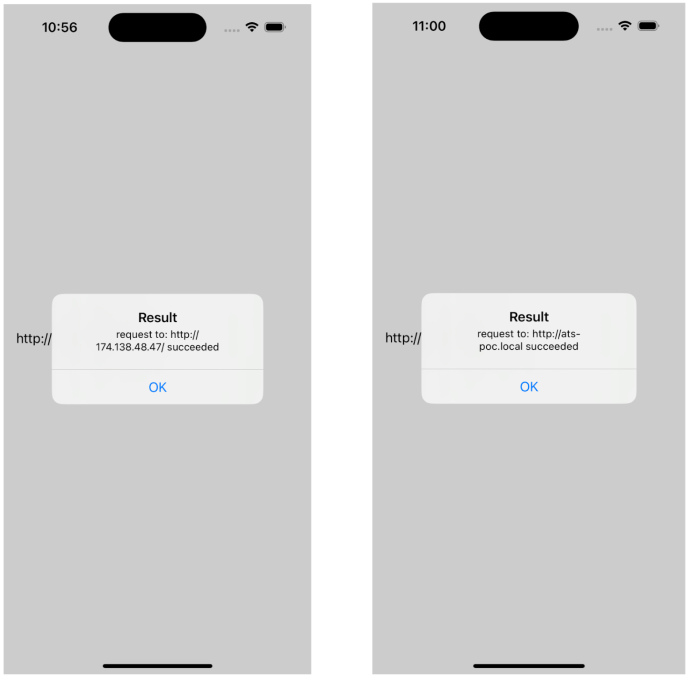
We created a simple app protected by ATS that POSTs to a user-specified URL. The following table summarizes the tests we performed. Notably, to demonstrate the flaw in ATS’s protocol handing, we submitted POST requests to an unencrypted IP address and *.local domain and observed that the requests succeeded when they should not have, as shown in figure 1.
Note: The URL with the IP address (http://174.138.48.47/) and local domain (http://ats-poc.local) both map to http://ie.gy/.


Figure 1: We submitted POST requests to an unencrypted IP address (left) and *.local domain (right). Both requests succeeded.
This behavior demonstrates that ATS requirements are not enforced on requests to .local domains and IP addresses. Thus, network connections established by iOS and macOS apps through the URL Loading System may be susceptible to information disclosure vulnerabilities and MitM attacks—both of which pose a risk to the confidentiality and integrity of transmitted data.
An exploit scenario
An app is designed to securely transfer data to WebDAV servers. The app relies on ATS to ensure that traffic to user-provided URLs (WebDAV servers) is protected using encryption. When a URL is added, the app makes a request to it, and if ATS does not block the connection, it is assumed to be safe.
A user unwittingly adds a URL on the form http://a.b.c.d/path/, which is allowed by ATS even if it’s not encrypted. The user then accesses the URL from an insecure network, such as a mall WiFi. Because the traffic is not encrypted, a malicious user who is able to capture the network traffic is able to access all data sent to the server, including basic auth credentials.
Check your apps!
Now that Apple has forced encryption to .local and IP addresses, developers should check that their app continues to work if they rely on those addresses.
Coordinated disclosure
As part of the disclosure process, we reported the vulnerabilities to Apple first. The timeline of disclosure is provided below:
- October 21, 2022: Discovered ATS vulnerability.
- November 3, 2022: Disclosed the vulnerability to Apple and communicated that we planned to publicly disclose on December 5.
- November 14, 2022: Apple requested delay to February 2023; we requested details about why the delay was necessary.
- November 16, 2022: Agreed to delay after Apple explained their internal testing and validation processes.
- November 28, 2022: Requested a status update from Apple.
- November 29, 2022: Apple confirmed that they were still investigating the vulnerability.
- December 9, 2022: Apple confirmed and continued investigation.
- January 31, 2023: Delayed release due to potential impact to apps/developers.
- March 31, 2023: Requested a status update from Apple.
- April 10, 2023: Apple indicated they were preparing an update regarding the remediation timeline.
- April 18, 2023: Fix indicated that a fix would be ready for post-WWDC beta release.
- September 18, 2023: Apple published an advisory confirming that CVE-2023-38596 had been fixed.