2024-2-21 00:11:42 Author: krypt3ia.wordpress.com(查看原文) 阅读量:22 收藏
Phishing attacks remain one of the most pernicious threats, lurking beneath the surface, waiting for unsuspecting users to take the bait. These threats have become more sophisticated over time, with attackers often using reputable platforms like Google to target users. One common method involves sending unsolicited emails containing PDF attachments, designed to trick users into compromising their security. When such a phish comes knocking at the door of your Google account, it’s crucial to respond to these cooly and clear headed to avoid possible compromise of systems or, trigger a loss of money through scams that might follow if you engage with the sender.
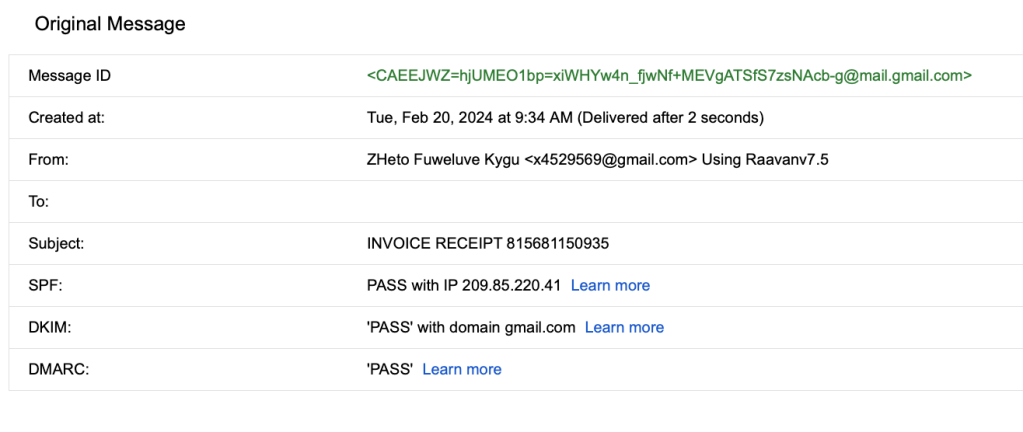
With that in mind, here is an example of a phish I got today (one of 4 so far by the same actor it seems) trying to get me to bite. What is interesting though, is that something must have happened with Google, or they figured out a new way to bypass DKIM and phishing filters to get these to me…
Here is the email…
Now, usually Google is pretty good about this stuff, but, I am assuming that my email has gotten out since I am on the job hunt, so there are leaking sites out there if you use your email address on sites, or you put it in your resume and these people find them.
It could just also be from one of the zillions of dumps of data lately, since everyone keeps getting PWN3D and losing our personal data, but, that is a rant for another day.
Anyway, so you can see the email, no real links, but that PDF there kinda set me off. Who here remembers all those PDF malware days? Raise your hands….
So I downloaded the pdf and ran it through ANY.RUN because I was pretty sure it was bogus, would not have any of my real data in it, and I wanted to see if there were links in there or in fact malware that would spin up on opening.
The file had no malware, and no real bad actor DNS or HTTP calls, so all good there it seems. They added the PDF to make it look more legit I guess….
Checking the headers got me very little, it was Google to Google as they created a gmail address for this..
Yep, not much there.. I did some searches on the email address they created, and the name of the individual alleged in the email but nothing turned up. Sometimes you can search and see other campaigns using the same names etc in varying types of attacks. In this case, tabula rasa.
So yeah, in this case, I immediately checked my PayPal account on another device, using the app, saw nothing going on there, and then doubled back to do all this research. Now, not all of you out there may have had as much experience with these kinds of tools as well as phishing in general. So, I thought I would generate a little primer on what to do so as to not get hooked and cleaned…. I mean, not everyone has a “Beekeeper” who will find these guys and burn down their operations..
*Gotta love Statham movies*
How to respond and investigate a phish like this:
Stay Calm and Steady
First and foremost, keep calm. Panic can lead to rash decisions, such as calling back numbers listed in the email or hastily clicking on suspicious links. Take a deep breath and prepare to assess the situation logically.
Do Not Engage
- Avoid Interaction with the Attachment: Do not click on, download, or open the PDF file attached to the email. This is the bait, and engaging with it could initiate the download of malware onto your device.
- Ignore Any Embedded Instructions: Phishing emails often come with urgent instructions, such as calling a specific number or clicking on a link to verify your account details. Do not follow these directives, as they are traps designed to extract personal information or infect your device with malware.
Verify the Source
If the email purports to be from Google or another service you use, do not use any contact information provided in the email. Instead, go directly to the official website by typing the URL into your browser and contact customer support through official channels to verify the communication’s authenticity.
Report and Delete
- Report the Phishing Attempt: If you’re using a Google account, report the phishing attempt to Google. This helps improve their security algorithms and protect other users from similar threats.
- Delete the Email: Once reported, delete the email from your inbox to prevent accidental interaction in the future.
Analyze Suspicious Files Safely
For those curious about the contents of the unsolicited PDF or concerned it may contain important information, there’s a safe way to check without risking your device’s security: using a virtual sandbox service like Any.Run. Here’s a primer on how to use such services:
- Choose a Virtual Sandbox Service: Any.Run is a popular choice, offering a controlled environment to run and analyze files and URLs to detect potential threats.
- Create an Account: Most virtual sandbox services require users to sign up. Create an account to access the service’s features.
- Upload the Suspicious File: Once logged in, look for an option to upload or submit a file for analysis. Select the PDF you received and start the analysis process.
- Review the Analysis: The sandbox will execute the file in a secure, isolated environment, tracking its behavior for any malicious activities, such as attempts to connect to external servers, download additional payloads, or execute malware. Review the analysis report to understand the nature of the file.
- Take Action Based on Findings: If the file is deemed malicious, you’ve successfully avoided a threat. If it’s harmless, you can decide how to proceed with the information contained within, now knowing it’s safe.
Stay Informed and Educated
Continuously educate yourself about the latest phishing techniques and cybersecurity best practices. Knowledge is power, especially when it comes to safeguarding your digital life against the ever-evolving threats posed by cybercriminals.
Encountering an unsolicited phish in your Google account can be unsettling, but with the right approach, you can navigate these dangerous waters safely. Remember to stay calm, avoid interaction with the suspicious elements, report and delete the phishing attempt, and use virtual sandboxes like Any.Run to analyze suspicious files safely. Stay vigilant, stay informed, and sail safely through the cyber seas.
如有侵权请联系:admin#unsafe.sh



