2024-2-22 00:38:6 Author: krypt3ia.wordpress.com(查看原文) 阅读量:40 收藏
This report was created in tandem between Scot Terban and the CHAIRMAN MEOW A.I. Analyst created and trained by Scot Terban
Executive Summary
This report provides a comprehensive analysis of the activities associated with I-SOON, an information security company based in China, implicated in the development and deployment of sophisticated spyware targeting various entities worldwide. Leaked documents suggest I-SOON’s involvement in state-sponsored cyber operations, including espionage against social media platforms, telecommunications companies, and other organizations. This report synthesizes available data to assess the threat I-SOON poses to global cybersecurity.
Background
I-SOON is purportedly engaged in creating offensive cyber tools and spyware on behalf of the Chinese government. The exposure of these activities comes from documents allegedly leaked on GitHub, detailing the operational capabilities of the spyware developed by I-SOON. These documents, while not officially authenticated, provide insight into China’s offensive cyber capabilities.
Capabilities
- Social Media and Communication Platform Targeting: The spyware reportedly allows operators to compromise social media accounts, obtaining sensitive information such as email addresses and phone numbers, and enabling real-time monitoring and control over the accounts.
- Mobile Device Targeting: I-SOON’s tools can target both Android and iOS devices, extracting a wide range of data, including hardware information, GPS locations, contact lists, media files, and real-time audio recordings.
- Specialized Espionage Gadgets: The leaked documents describe devices capable of injecting spyware into targeted Android phones via WiFi signals. These gadgets are camouflaged as common electronics, such as portable batteries.
- Telecommunications and Online Platform Surveillance: The spyware has been used to gather sensitive information from telecommunications providers and users of Chinese social media platforms (e.g., Weibo, Baidu, WeChat).
I-SOON’s Connection to APT41
Overview
APT41, a sophisticated state-sponsored Chinese cyber espionage group, has been active for several years, targeting industries across various sectors globally. The group is known for its advanced capabilities in cyber espionage, data theft, and the deployment of ransomware. Recent investigations and leaked documents have suggested a potential connection between I-SOON, a Chinese information security company, and APT41. This section explores the nature of I-SOON’s association with APT41, the implications of their relationship, and the broader context of Chinese cyber operations.
Nature of the Connection
I-SOON’s purported involvement with APT41 stems from its alleged role in developing and supplying spyware and hacking tools used in APT41’s operations. Leaked documents and cybersecurity research have indicated that I-SOON has been a key player in creating sophisticated tools tailored for espionage, data extraction, and system compromise. These tools reportedly possess capabilities that align closely with the modus operandi of APT41, including but not limited to:
- Targeting social media platforms and telecommunications companies for intelligence gathering.
- Developing malware for both Android and iOS devices to collect sensitive information.
- Utilizing specialized devices capable of exploiting vulnerabilities via WiFi signals.
Implications of the Relationship
The connection between I-SOON and APT41 raises significant concerns regarding the extent to which Chinese commercial entities are involved in state-sponsored cyber espionage activities. This relationship underscores the blurred lines between the country’s private sector and government cyber operations, highlighting a complex ecosystem where companies like I-SOON operate both as commercial entities and as facilitators of national cyber espionage efforts.
The collaboration between I-SOON and APT41, if proven, would demonstrate a sophisticated integration of private sector innovation with state-sponsored cyber activities. This synergy enhances the capabilities of groups like APT41, enabling them to conduct more sophisticated, widespread, and effective cyber operations globally.
Broader Context
China’s strategy of leveraging private sector capabilities for state-sponsored activities is not unique but part of a broader pattern observed in several countries engaging in cyber espionage. However, the scale and sophistication of China’s operations, coupled with the country’s global technological ambitions, make the I-SOON and APT41 connection particularly noteworthy. This relationship provides insight into how China is advancing its cyber capabilities by tapping into the innovation and technical prowess of companies like I-SOON.
Moreover, the alleged involvement of I-SOON in developing state-sponsored spyware highlights the challenges in attributing cyber attacks to specific actors. The use of commercial entities to develop tools for cyber operations complicates efforts to trace activities back to state actors, thereby providing a layer of deniability and obscuring the true extent of state involvement in cyber espionage.
The connection between I-SOON and APT41 exemplifies the convergence of commercial technology development with state-sponsored cyber espionage activities. This relationship not only enhances the capabilities of APT41 but also illustrates the broader strategy employed by China to incorporate the private sector into its national cyber operations framework. As the cyber domain continues to evolve, understanding the dynamics between companies like I-SOON and groups such as APT41 is crucial for assessing the landscape of state-sponsored cyber threats and formulating effective countermeasures.
Targets and Victims
Victims identified in the leaked documents include:
- Paris Institute of Political Studies (Sciences Po)
- Apollo Hospitals, a large private hospital network in India
- Government entities from countries neighboring China
- Telecommunications providers in Kazakhstan
Operational and Financial Insights
- The average salary for employees (excluding C-level executives) involved in spyware development is reported to be approximately 7,600 RMB (about 1,000 USD) after tax, considered low for the alleged activities.
Threat Assessment
The capabilities and targets associated with I-SOON’s spyware suggest a high level of sophistication and a broad operational scope. The focus on surveillance and information extraction across a variety of platforms and devices indicates a significant threat to privacy, security, and the integrity of targeted systems and networks.
I-SOON’s operations align with known patterns of state-sponsored cyber activities, aiming to gather intelligence, monitor dissidents, and potentially disrupt the operations of perceived adversaries. The targeting of telecommunications providers and critical infrastructure, along with the development of specialized espionage devices, underscores the strategic nature of I-SOON’s activities.
While the veracity of the leaked documents remains unconfirmed, the information presented suggests that I-SOON is a capable actor within China’s cyber espionage ecosystem. The global community should remain vigilant and proactive in defending against the sophisticated and evolving threats posed by state-sponsored entities like I-SOON.
Deeper Dive Investigation: i-SOON Data Dump
I have been leveraging my A.I. Analyst (CHAIRMANMEOW) to take documents and images from the dump and translate them as well as give context to the conversations that can be found. In the file dump, there are a lot of chat logs as well as screen caps of documents that are in Mandarin. The A.I. Analyst does a pretty good job at translating the files and then I mill the system for context on what seems to be going on.
In the case of the chat logs, there are discussions about the company i-SOON by people who work there about how the company is doing, some of the personal and political things inside the company and some genuinely interesting conversations on products and goals.
Other documents are a little more interesting, like: “Twitter Public Opinion Guidance and Control System Product Composition Introduction (Version V1.0 2022)“
f179eb06-0c53-44df-a13f-570be23355bb_4.png
This translation:
1 Introduction
Cybersecurity is a vital domain for building peace, prosperity, and inclusivity. It has become one of the main strategies for the prosperity of the nation and society. Its unique interactivity in communication, freedoms of speech, and public discourse are irreplaceable. The apparent rise in data transactions reflects the increasing scale of online media and the changes brought about by the proliferation of the internet, making it more important for public security authorities to grasp platform operations for social stability. To this end, it is essential to use modern information technology for real-time analysis of the internet to detect and trace activities. In this trend, it is necessary for the government, especially public security agencies, to take proactive management actions, to keep abreast of public sentiment, follow civil organizations, guide the social impact of media and public opinion, and explore reasonable control of public discourse and crisis management methods. Establishing a comprehensive system for guiding and controlling is of significant inferential and practical significance for building a harmonious online environment and maintaining social stability.
The detection of cybersecurity intelligence as a highly regular and orderly technical pursuit is crucial. Strengthening cybersecurity intelligence detection is particularly important for safeguarding national security, effectively regulating the content of public opinion, guiding the direction of public sentiment towards justice and fairness, and realizing the government’s policies for public service transparency. Reflecting on cybersecurity and social conditions can enhance business, employment, and personal development, contributing to social and economic harmony and stability.
Encryption recognition and cybersecurity intelligence detection techniques are essential for securing a systematic project and involve discipline, united fronts, civil affairs, and participation from public security departments. However, as part of the entire social security prevention mechanism, the cybersecurity intelligence needs and countermeasures of the community police maintaining social stability hold a uniquely special significance.
Currently, Twitter has become a hub for netizens to exchange opinions and a focal point of international online sentiment, necessitating control over crowds and objects. Manpower and financial resources are invested in comprehensive monitoring and vigilance against online speech, cybercrimes, and various website activities, including play and espionage. Social networks serve as gateways for interacting with netizens…
At the same time, implement plans for real-time crisis management against Twitter public sentiment. Improve capabilities for countering, perfecting essential measures against public sentiment on Twitter for our nation.
(1) Enhance Real-Time Crisis Response to Twitter Public Sentiment
To meet the immediate detection of adverse public sentiment, swift correction, and reactionary public opinion in network hardware and software operations, control and observation platforms based on key individuals on Twitter are used to quickly grasp international public opinions and dynamics, allowing for rapid response and immediate handling, with problematic propaganda being modified. Perfect the Twitter platform’s public sentiment intelligence procedures for our country, effectively enhancing the crisis response capabilities.(2) Strengthen Precision Guidance for Twitter Public Sentiment
To meet the daily network work requirements and the acceptance and countermeasures against external Twitter public sentiment, the construction of a Twitter public sentiment control system will facilitate the detailed management of Twitter targets, achieving close and meticulous control. It helps to seize the initiative in managing and guiding public sentiment, thereby realizing proactive strategies for counteracting external Twitter capabilities.3 Product Composition Introduction
3.1 Product Introduction
The Twitter Public Sentiment Intelligence System is a product for feedback and control of public sentiment intelligence work on the large foreign text platform Twitter. It allows quick response to sensitive public sentiment in politics, law, and community through the instruction system, and realization of feedback on public sentiment intelligence and countermeasures on Twitter.3.2 Product Composition
The Twitter Public Sentiment Intelligence System belongs to a software system, using a B/S architecture. Users can use it normally by logging in with the authorized account number and password. The product composition is as follows:
- Public Sentiment Intelligence Software: 1 set
- Public Sentiment Intelligence Login Account: 1 set
- Public Sentiment Intelligence Manual: 1 copy
This document is on a product that i-SOON is pitching for detection and response to sentiment on Twitter inside China, and potentially for any other government that the Chinese might want to sell it to. As anyone knows, in China, they like to control the populace as much as possible and sentiment, along with their “Social Capital” types of programs where wrong think or action is found, you will get a visit by the police to, uh, correct you.
Other Espionage Activities:
The company has also developed a hacking tool (assuming hacking tool and backdoor framework) called Hector. Which there is a full document set on it, how it works, and what the price is. I have translated some of that document but did not go through the whole thing because you get the point. I would be interested in getting a copy of it (I assume a mentioned .rar file is the actual binary) but that was not dumped as far as I can tell at this time.
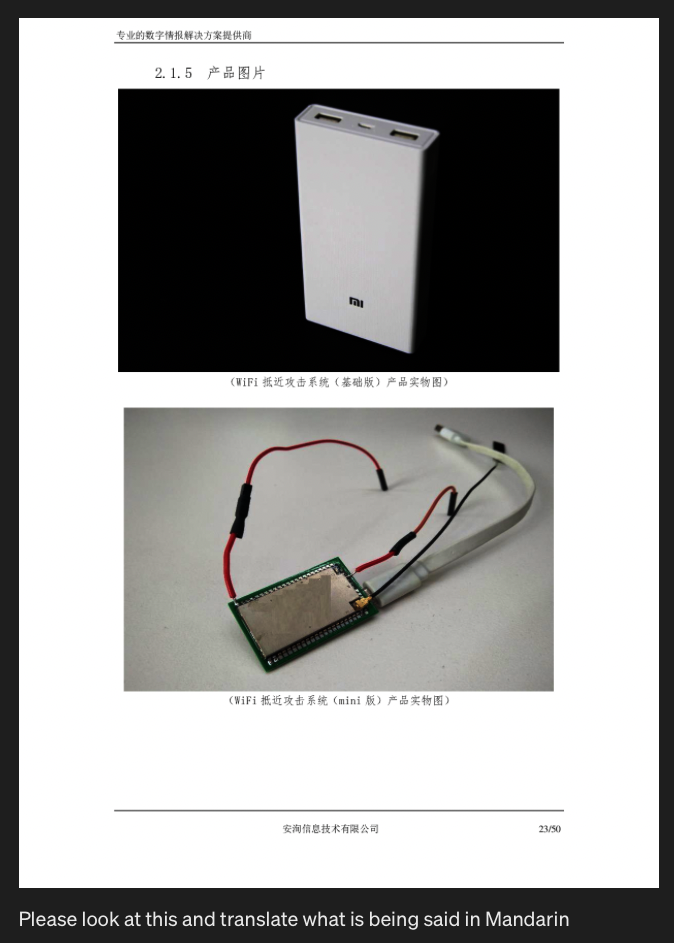
So yeah, they are developing all kinds of things, including, the most interesting hardware piece I have seen of late, a functional backup battery that is a spy tool cum launch tool for compromise of a network or systems.
Translation:
Professional Security Intelligence Solutions Provider
2.1.5 Product Images
(WiFi Simulation Attack System (Power Bank) Product Exterior)
(WiFi Simulation Attack System (Mini Version) Product Exterior)
Anbiao Communication Technology Co., Ltd.
Page 23 of 50
This is a fifty page document so I have not translated it all, but you catch the drift. These guys are in the market of creating tools as well as carrying out nation state espionage on a range of countries and entities. Which brings me to the next section, those they are already watching, in particular, access to telco in Kazakhstan.
Kazakhstan Espionage:
There were log files showing that this company (I-SOON) had been at least able to access certain people’s telco connections in Kazakhstan. All of these people are of Russian extraction, and as of now, my searches are a bit vague as to lock in on those people as to who they are and what they do. What I assess though, is that these are people with Russian government or have access to RU gov that the Chinese would be interested in monitoring and perhaps escalating access via other means for intelligence.
GUID SUBSCRIBER_ID SUBSCRIBER_NAME LOGIN PASSWORD ACCOUNT_USER_BLOCK SUBSCRIBER_BLOCK DEVICE_BLOCK QUESTION ANSWER ACTIVE_DATE DEACTIVATION_DATE PACKET_TYPE CITY DEVICE SUBSCRIBER_ID ADDRESS_ID
2-349544 349544 ABAYSKY RPUT 60:1E:02:06:BA:50 60:1E:02:06:BA:5 F F F – – 29.01.2018 17:38:03 – iD TV Service Abay Karaganda region. (72131)41888 812181067 19724
2-349544 349544 ABAYSKY RPUT 60:1E:02:04:9A:C7 60:1E:02:04:9A:C F F F – – 29.01.2018 17:02:14 – iD TV Service Abay Karaganda region. (72131)42540 812180842 19724
2-349544 349544 ABAYSKY RPUT 498032250905 498032250905 F F F – – 29.01.2018 17:02:14 – iD TV Service Abay Karaganda region. (72131)42540 812180842 19724
2-349544 349544 ABAYSKY RPUT 198842250905 198842250905 F F F – – 29.01.2018 17:38:03 – iD TV Service Abay Karaganda region. (72131)41888 812181067 19724
2-622967 622967 ABDIKARIMOV SABYR NURTAEVICH 60:1E:02:00:6C:A9 60:1E:02:00:6C:A F F F – – 20.06.2013 16:01:13 – IPTV Basic Abay Karaganda region. (72131)45431 808474531 19724
2-622967 622967 ABDIKARIMOV SABYR NURTAEVICH 706721260003 706721260003 F F F – – 20.06.2013 16:01:13 – IPTV Basic Abay Karaganda region. (72131)45431 808474531 19724The file contains records for a television service, detailing subscriber IDs, names, device information, service status, and package types, among other data. This snippet shows the structured format of the data, including service types like “iD TV Service” and “IPTV Basic” for subscribers in the Abay region of Karaganda.
And this…
GUID SUBSCRIBER_ID SUBSCRIBER_NAME LOGIN PASSWORD ACCOUNT_USER_BLOCK SUBSCRIBER_BLOCK DEVICE_BLOCK QUESTION ANSWER ACTIVE_DATE DEACTIVATION_DATE PACKAGE_TYPE CITY DEVICE SUBSCRIBER_ID ADDRESS_ID
2-2763038 2763038 DOROSHENKO TATYANA NIKOLAEVNA IDAB00202 ID0202netAB F F F Birthplace 1 15.01.2018 21:39:36 iD Net Hit Abay Karaganda region. (72131)98210 812152748 19724
2-344379 344379 RAKHIMBEKOVA SARKYT AKENOVNA 7213190125 R87213190125s F F F Mother’s maiden name Rakhimbekova 22.09.2014 14:35:39 Megaline Minimum STS Abay Karaganda region. (72131)90125 809631778 19724
…This file contains detailed records of internet service subscribers, including their IDs, names, login information, service status, security questions and answers, and package types. Each line provides information on a specific subscriber’s account, reflecting various package types like “iD Net Hit,” “Megaline Minimum STS,” and others, across different regions, primarily in Abay, Karaganda region.
Why Kazakhstan?
China’s stake in Kazakhstan, particularly concerning relations with Russia, encompasses a multifaceted geopolitical and economic landscape shaped by recent regional developments and historical ties.
Kazakhstan maintains a complex relationship with Russia, characterized by cordial diplomatic interactions, defense collaborations, and robust economic ties. Despite these connections, Kazakhstan has shown a degree of autonomy by not endorsing Russia’s actions in Ukraine and refusing to recognize separatist regions in Ukraine. Kazakhstan’s President Tokayev has participated in forums alongside Russian President Putin while also attending the Shanghai Cooperation Organization summit, which includes China as a member.
China’s engagement with Kazakhstan seems unaffected by the Kazakh regime’s quest for economic growth and potential tightening of repression. China views Kazakhstan as a vital partner, as indicated by President Xi Jinping’s pledge to deepen ties with Kazakhstan in both prosperous and challenging times. This relationship is underscored by substantial Chinese investment in Kazakhstan, focusing on economic and interconnectivity projects, with recent agreements worth billions aimed at boosting oil exports, gas processing, and developing industrial cooperation. China has also shown interest in Kazakhstan’s reserves of rare earth metals, critical for high-demand industries such as electric vehicle production.
In light of Russia’s war in Ukraine, Kazakhstan has attempted to diversify its international relations, including strengthening ties with China. Xi Jinping’s visit to Kazakhstan, the first after the COVID-19 pandemic, was perceived as a significant gesture in the context of global power dynamics. Despite maintaining relations with Moscow, Kazakhstan has also sought to enhance its partnerships with Turkey, other Central Asian countries, and the Caspian region, including Iran and Gulf countries.
The deterioration of relations between Russia and Kazakhstan has drawn China’s attention, with Beijing backing Astana against any Russian threats. Kazakhstan’s strategic location as a significant hydrocarbon supplier and a transit corridor linking China to Europe and beyond is of paramount importance to Beijing. China is also eyeing alternative trade routes, such as the Middle Corridor through Kazakhstan, to bypass Russia amidst sanctions disrupting logistics through the Northern Corridor.
The interplay of Kazakhstan’s multi-vector foreign policy allows it to engage with various international partners, balancing its historical ties with Russia and its burgeoning relations with China and other global powers. This strategic diplomacy is critical for Kazakhstan as it navigates its position between two influential neighbors in a region marked by shifting alliances and economic opportunities.
Nato and Others:
It seems that the I-SOON folks, as a newer org, is looking to engage in all kinds of online espionage for APT-41 and the MSS/PLA. In that effort, they have been busy making tools and already carrying out access operations at the very least for APT-41/MSS and were looking to expand per other conversations in the dump. As of my last check they were in NATO systems potentially as well as; Paris Institute of Political Studies (Sciences Po), Apollo Hospitals, a large private hospital network in India, and Government entities from countries neighboring China. These are all pretty standard espionage collection operations and had this company gone further, well, I am assuming they have been blown by this dump and out of favor, they could have become more of a tailored access and collection entity.
Last I checked, the site was down so it looks like maybe they are at least re-grouping…
I will keep a look out for more dumps, I am going to say that whoever dumped their stuff has a lot more on their drive to parse out and damage them further. All in all, this was an interesting exercise in that I have been training the A.I. agent to do this kind of work and thus far, it is a little laborious because this was a firehose of data to look at, but, the tool is going like a champ! It has made this analysis and threat intelligence report much easier to create and manage with translation, context, and sentiment.
If you want to take a look yourselves, you can go get the I-SOON dump on the git it was put out on, but, I don’t know how long it will stay there. I cloned it all locally.
Enjoy,
~ K.
如有侵权请联系:admin#unsafe.sh





