2024-3-8 19:46:57 Author: blog.sekoia.io(查看原文) 阅读量:19 收藏
As of today, a large majority of intrusion sets and threat actors leverage crypters prior to delivering and executing malicious payloads on a target system. They use it to build malware capable of avoiding security solutions. In their campaigns, malicious actors can rely on an open-source, a commercially available or a custom crypter.
While a crypter software is not malicious per se, it is intended to hide known malicious code such as ransomware, infostealers or RATs and to facilitate malware delivery. Therefore, understanding the functioning of the crypters ecosystem is essential to having a more accurate view of the broader cybercrime landscape.
In this report, we introduce key concepts and analyse the different crypter-related activities and the lucrative ecosystem of threat groups leveraging them in malicious campaigns. Our analysis is based on the Sekoia Threat Detection & Research (TDR) team investigation results, insights from open-source reporting, and extensive monitoring of different cybercrime platforms.
While it has been reported that APT groups also leverage crypters, often sourced from third-party services mentioned in this report, our analysis centres on financially-motivated activities.
Definitions and Background
Crypters
Crypters (“криптер” in Russian) are software programs capable of encrypting, obfuscating, and manipulating malware to bypass detection mechanisms, while keeping the malware’s functionalities intact. This is made by leveraging different obfuscation techniques, notably code transformations.
Of note, some sources use the terms “packer”, “cryptor” and “loader” interchangeably when referring to crypters.
Crypters are most commonly used to deliver Remote Administration Tools (RATs), infostealers and ransomware. This is notably the case for malware families distributed on a large scale. As the final payload is typically chosen by the crypter user individually, the same crypter is often used for disparate final payloads and campaigns. Therefore, clustering crypter-related activities (notably the “as-a-service” activities) is challenging from a defender point of view.
Scantime and runtime crypters
Depending on the anti-detection routine used, there are scantime and runtime crypters. On the one hand, scantime crypters are known for their capability of obfuscating malware before execution. This is effective during a scan of files stored on a disk but is potentially susceptible to detection during the malware execution, as the file should be decrypted before running.
On the other hand, runtime crypters are designed to bypass detection during the execution process by loading decrypted portions into memory as separate processes. After the malware is launched, the stub code re-encrypts it. This allows the malware to be loaded and executed before security systems can respond to any malicious behaviour.

(Crypter) Stub
A crypter software typically encrypts or obfuscates a binary and modifies it to decrypt itself during runtime. The part of the modified program responsible for decrypting the main payload is called the stub (“стаб” in Russian). The following are different types of stubs:
- Public (shared) stubs are commonly available, widely used and shared among multiple users. While they do not require any financial effort, public stubs are more easily detected by security systems.
- Private stubs are unique to each user or a smaller group of users. They are updated regularly, usually daily, to stay ahead of antivirus (AV) signatures. While they are more expensive on the cybercrime market, private stubs generally ensure a longer FUD (Fully UnDetectable) time for the related crypter (e.g. FUDcrypter/Data-Encoder).
- Melt stubs are designed to be self-destructive. After it has served its purpose of decrypting and executing the main payload, it deletes itself.
Depending on the type of stub used, crypters can be classified as static or polymorphic. While static crypters use the same stub across different encrypted files, polymorphic ones leverage a dynamic stub. For example, AceCryptor launches numerous System calls to standard libraries (e.g. Kernel32, WS_32) to masquerade as legitimate software. Techniques to detect the environment or to detect debugging processes are concealed in the API calls to prevent full execution of the crypter. So, polymorphic crypters constantly change their signature while retaining functionality (e.g. shuffling blocks of code while preserving a malicious file’s ability to run, inserting garbage code, etc.), making it more difficult to detect.

FUD and partial Crypters
FUD (Fully UnDetectable) refers to the capability of the crypter to make malware completely undetectable by antivirus software. Otherwise, if it can only evade several security solutions only sold as a “partial” crypter.
Malware developers tend to make FUD functionalities a key selling point and most crypters sold as FUD update their stub daily to remain undetectable over time. However, we assess this term is misused by most crypter sellers, as stubs are only rarely completely FUD and they are generally detected by at least certain virus scanners.
To share or not to share: navigating the crypters ecosystem
Open-source Crypters
Open-source crypters refer to software that are freely available and accessible to the public. For malicious actors, open-source crypters offer a readily available solution for evading detection by antivirus software and for successfully delivering their malicious payloads. These tools can be easily customised and adapted to suit the needs of specific malware campaigns.
One example is AttackerCrypter, a crypter project freely released on GitHub by its presumed Russian-speaking developer. Moreover, it is also actively advertised by a moderator on a Russian-speaking underground forum. AttackerCrypter was reported as being leveraged by VenomRAT operators soon after its release in June 2023 and was actively used in the wild as of August 2023.
AttackerCrypter’s author explicitly instructs users not to upload this tool to VirusTotal to ensure its durability. Yet, AttackerCrypter is no longer able to generate FUD malware after modification, even if it proved to be relatively effective against static signature detections and static heuristics. So, free and publicly available crypters are progressively detected by antivirus programs when massively used, and most FUD Crypters remain “FUD” for a short time after their public release. Consequently, malicious actors often develop custom crypters, deploying them in their own malicious campaigns or offering them for sale.
Private Crypters
Private crypters are typically sold or shared through closed communities to a limited number of customers. These crypters are often designed to provide advanced features and better evasion techniques than their open-source counterparts.
On one hand, malicious actors that are likely more advanced (e.g. those having programming capabilities) commonly build their own crypter software for malware delivery campaigns. Such examples are the crypters used by the Trickbot/Conti syndicate since 2021 and that are currently leveraged by the group’s successors after the Conti shutdown. The developers, the distributors, and the operators of crypters such as Forest, Snow and Dave are assessed to be former members or partners of the Conti syndicate and they highly likely continued to provide their software and their services to a closed galaxy of intrusion sets throughout 2023.
On the other hand, Sekoia TDR analysts also monitor the underground market dedicated to private crypters, that are widely advertised and sold on cybercrime forums, illicit marketplaces and other platforms. We observed G0RGON and other private crypters emerging on cybercrime forums throughout 2023. Numerous intrusion sets such as Cuba ransomware, WastedLocker ransomware and Bumblebee operators were previously reported leveraging private crypters.
Private crypters are usually available for one-time purchases and are more expensive. For example, the crypter Royal Flush advertised since March 2023 on the XSS cybercrime forum is sold for $199 per month for the “standard edition”, while its private service costs $999 per month.

Crypters-as-a-Service
Crypters-as-a-Service are crypter malware provided as a subscription or on-demand service to other malware operators. Sekoia TDR team observes a progressively extensive use of this model and subsequently a continuously high demand for such services. This is naturally an inherent component within the expansive Cybercrime-as-a-Service market, alongside Ransomware-as-a-Service, Stealer-as-a-Service, etc.
The proliferation of Crypters-as-a-Service translates into an ever-increasing number of actors entering the threat ecosystem, by acquiring directly exploitable malware capabilities on underground platforms instead of developing them independently. Typically, malware operators outsource their crypter-related tasks to third parties to save time or to fill in missing skills.
The activities mentioned above form a broader market dedicated to crypters, which includes:
- crypting services that affiliates purchase with a malware licence from the crypter developer or its representative;
- additional crypter-related services, which extend beyond software acquisition and aim at enhancing proficiency in crypter manipulation:
- FUD crypter programming trainings
- Crypter modification trainings
- Expert guidance on optimising malware distribution, etc.
So, the Crypters-as-a-Service model not only includes user assistance and intuitive interfaces but also provides regular updates to counter evolving antivirus features. Therefore, this subscription-based model allows for better adaptability and efficacy than one-time crypter software purchases.
The following part of this report details the Crypter-as-a-Service ecosystem and the functioning of this model.
We inform you of your delivery: Crypter-as-a-Service mechanisms
The market
From our observations, Crypters-as-a-Service are currently advertised on both top-tier and low-tier underground forums, on illicit or legitimate marketplaces, and on dedicated channels on legitimate services such as Telegram, Sellix and Youtube. A significant number of Crypters-as-a-Service providers redirect users to websites on the Clear Web for detailed subscription instructions and then for the purchase.
Crypters and crypter-related services were documented as being sold since at least 2011 on various Russian-speaking cybercrime forums. In 2016, Trend Micro also reported on crypters available in various Brazilian, Chinese, German and U.S. underground markets.
In early 2024, Sekoia TDR analysts note the following cybercrime-related forums and marketplaces where Crypter-as-a-Service are most frequently advertised: HackForums, CrackedIO, XSS, BreachForums, CryptBB, Exploit, UfoLabs, Zelenka, etc.
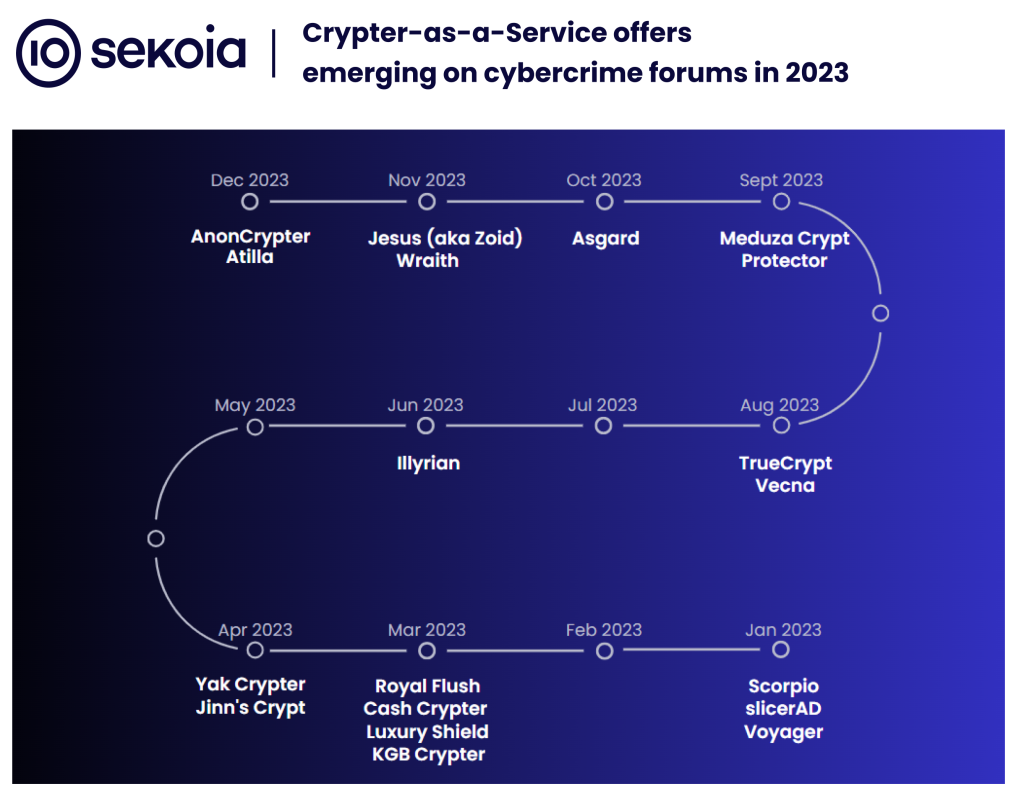
Such advertisements are commonly made by specialised accounts created and branded for this specific purpose. The figure below provides a non-exhaustive timeline of the most popular Crypter-as-a-Service advertised on cybercrime platforms since early 2023.

Among the Crypters-as-a-Service emerging in 2023 that are most widely advertised and discussed across various forums are TrueCrypt and AnonCrypter. Like most of the providers, these crypters launched their service by freely offering their software to 3 forum members for testing in return for a review on the platform, allowing them to be more visible.
Based on open-source reporting, the prices of crypters sold on underground forums would have decreased over time. According to Trend Micro data collected on Russian-speaking cybercrime forums, the price range went from $10/$30 to $100 in 2011, depending on the sophistication of the software. In 2013, the source reported a decrease to an average of $65 for the most advanced, polymorphic crypters. According to a 2016 Trend Micro analysis of Brazilian underground platforms, the prices were around $10 for partial crypters and $39 for FUD crypters with extended functionalities.
While the prices of one-time crypters purchases observed by Sekoia in 2023 are relatively comparable to those previously reported in open sources, the Crypters-as-a-Service are sold for much higher prices. The subscriptions for one month of usage vary between several dozen of dollars and over $250-$300.
Besides crypters that constitute a distinctive and unique software, Crypters-as-a-Service activities on underground forums are often part of broader business models. Indeed, well-established cybercrime operations such as Stealer-as-a-Service commonly expand their business model to crypters as well. For example, Meduza Crypt is advertised under the umbrella of the Meduza Stealer-as-a-Service operation. Such crypters can be sold separately or integrated into a common panel providing multiple capabilities.

It goes the same for the Pure malware family, which added a crypter to its other malware sold as-a-service (PureLogs, PureMiner, PureClipper, Pure HVNC, etc.). As the Malware-as-a-Service (MaaS) model allows malware distribution by various affiliates, crypters are nearly indispensable for ensuring successful, long-lasting mass distribution campaigns, especially for well-known and widely detected malware.

In case MaaS representatives do not have a crypter module integrated to their service, they might establish partnerships with third-party Crypter providers. This is highly likely indicative of the connections between different actors within the same community. Also, we do not exclude the existence of paid partnerships when MaaS representatives are remunerated if they recommend to their clients the use of a specific Crypter when distributing malware or are simply paid for advertising their services.
For example, KGB Crypter was previously advertised and recommended by both VectorStealer and VenomRAT actors. Also, the developer of MetaStealer actively advertises the crypter[.]guru crypting services for their stealer customers. Another example: Vidar and RedLine stealer representatives recommend cryptor[.]biz to their clients as a trusted service, in addition to Spectrum Crypt.
The functioning
The functioning of a Crypter-as-a-service typically involves several stages. The following is a general overview of how the Crypter-as-a-Service model operates.
- Client Interaction
- The customer purchases a subscription and creates an account to access the service, or interacts with a dedicated Telegram infrastructure.
- The customer accesses the crypter service (through a web interface or other form of client application, or via a Telegram bot).
- Uploading the Malware
- The user uploads the malicious payload to obfuscate or encrypt.
- Alternatively, some crypter services may provide APIs for automated submission of files.
- Configuration
- The user configures settings for the encryption or obfuscation process (e.g. by specifying which antivirus engines to evade, by setting up runtime behaviour, or by adding additional features like anti-analysis techniques).
- Encryption/Obfuscation
- The crypter service employs various techniques to encrypt or obfuscate the malware payload. This could involve custom encryption algorithms, modifying the binary code, rearranging instructions, or adding junk code. Another method consists in adding weight to the PE by appending garbage code, or injecting null bytes. This tactic aims to increase the file’s size, making it longer to analyse, and potentially not being analysed by certain tools that do not support large PEs for performance reasons.
- Delivery
- Once the encryption or obfuscation process is complete, the crypter service provides the user with the modified malicious file. It can be further distributed through various means, e.g. through phishing or spam campaigns.
- In some cases, a Telegram chat bot ID can be defined to get notified if the modified payload is executed.
- Testing for Defense Evasion
- The user may test the modified file against antivirus software to ensure it remains undetected and re-encrypt or obfuscate the malware if the detection rates are high. To do so, the user typically relies on offline scanning services so that files are not exfiltrated to security vendors.
- Continuous Updates and Support
- Crypter-as-a-service providers continuously update their encryption techniques and support services.
- Monitoring and Feedback
- Some crypter services may provide monitoring features, allowing users to track the performance of their malware in the wild.
- Feedback mechanisms may also be provided to gather data on antivirus detection rates and ensure continued effectiveness.

Conclusion
The wide use of crypters within the cybercrime ecosystem is indicative of the continuous need for malicious actors to adapt their malware delivery methods as security solutions evolve. The crypter routine allows them to circumvent detection programs while mass spreading the same malware over a longer period of time.
The very nature of crypter-related activity, notably the “as-a-service” model, makes it difficult to cluster, trace and identify the perpetrators. Although law enforcement authorities do act against crypter operators or services (e.g. Refud.me and Cryptex Reborn in 2015), their actions remain occasional so far.
The consistent usage of the Crypter-as-a-Service aligns with the evolving trend towards a specialised and professionalised cybercrime ecosystem. We assess with high confidence the cybercrime market related to crypter activities will continue to expand over the next few years. This growth will highly likely involve both an increase in the number of service providers and a rise in customer demand.
Therefore, crypter software leveraged in malicious campaigns should be addressed as a pivotal element within the malware distribution chain, playing a significant role in the perpetration of cybercrime on a broad scale.
Feel free to read other Sekoia TDR (Threat Detection & Research) analysis here :
如有侵权请联系:admin#unsafe.sh