This is my informal, unofficial, unapproved etc blog based on my reading of the just-released Mandiant M-Trends 2024 report (Happy 15th Birthday, M-Trends! May you live for many googley years…)

- “Shorter dwell times are likely driven by a larger proportion of ransomware incidents globally in 2023 (23%) versus 2022 (18%). The median dwell time for these ransomware cases dropped to 5 days compared to 9 days in the previous report.“ [A.C. — so your “detection” improved because .. the attacker helped a bit more]
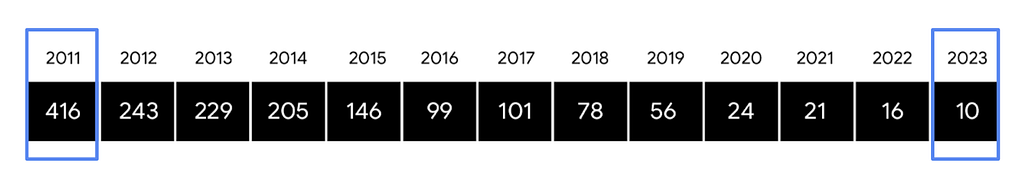
- “54% of organizations first learned of a compromise from an external source, while 46% first identified evidence of a compromise internally. ” [A.C. — pretty close to ½ and ½, so half of the organizations detect, while the other half gets told by others]
- But yes, we are better! “63% of notifications were external in the previous reporting period, suggesting organizations are improving at detecting malicious behavior.“
- “In 70% of ransomware cases, organizations learned of intrusions from external sources. Of those external sources, 76% were adversary notifications and 24% were external partners.” [A.C. — we should have a cooler name for these, like”attacker-led ‘detection’” or something]
- More good news! “Overall, ransomware intrusion detection improved in 2023 regardless of internal vs. external notification. Most notably with internal detection occurring in 6 days, which is 50% faster compared to the previous reporting period.“
- “In 2023, Mandiant experts once again saw exploits used as the most prevalent adversary initial infection vector. In intrusions where the initial intrusion vector was identified, 38% of intrusions started with an exploit. This is a six percentage point increase from 2022 […] Phishing remained the second most common intrusion vector. However it declined in 2023, with 17% of intrusions, compared to 22% in 2022.” [A.C. — perhaps we finally made a dent in email security, admittedly one of the simpler — NOT simple — security problems to solve]
- “… a trend in which China-nexus attackers have gained access to edge devices via exploitation of vulnerabilities, particularly zero-days, and subsequently deployed custom malware ecosystems.” [A.C. — this is strong reminder to the ‘good EDR is enough’ crowd that, well, an EDR is not enough. A mini-rant: a lot of SIEM haters now position themselves as “EDR lovers”, and I don’t mind them loving EDR, to be sure. But if they grow ‘log-ignorant’ as a result, their ass is owned!]
- “Historically, to gain initial access to cloud and hybrid environments, attackers have relied upon stolen credentials and access tokens that did not require multi-factor authentication (MFA).” [A.C. — I am sure, by “historically” they mean such unbelievable ancient history like, I dunno, earlier today? 🙂]
- Indeed “Mandiant continues to observe attackers perform password guessing attacks against cloud sign-in portals to identify accounts that do not have MFA configured. Often organizations will rely on users to self-enroll an MFA device. “ [A.C. — what I said above :-)]
- “Mandiant observed adversaries abuse cloud native tools and services to maintain access, move laterally, and ultimately accomplish mission objectives such as stealing data. […] Mandiant observed attackers using Azure Data Factory and AirByte to modify existing pipelines to steal data stored in various integrated platforms such as data warehouses” [A.C. — “living off the land” when the land=cloud is very real, and requires defenders to know the cloud tooling better than the attackers do..]
Enjoy the report here!
P.S. While I was writing this, DBIR landed as well, read this one too!
Related blogs
Reading the Mandiant M-Trends 2024 was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/reading-the-mandiant-m-trends-2024-acb3208add80?source=rss-11065c9e943e------2


