By Boyan Milanov
In part 1, we introduced Sleepy Pickle, an attack that uses malicious pickle files to stealthily compromise ML models and carry out sophisticated attacks against end users. Here we show how this technique can be adapted to enable long-lasting presence on compromised systems while remaining undetected. This variant technique, which we call Sticky Pickle, incorporates a self-replicating mechanism that propagates its malicious payload into successive versions of the compromised model. Additionally, Sticky Pickle uses obfuscation to disguise the malicious code to prevent detection by pickle file scanners.
Making malicious pickle payloads persistent
Recall from our previous blog post that Sleepy Pickle exploits rely on injecting a malicious payload into a pickle file containing a packaged ML model. This payload is executed when the pickle file is deserialized to a Python object, compromising the model’s weights and/or associated code. If the user decides to modify the compromised model (e.g., fine-tuning) and then re-distribute it, it will be serialized in a new pickle file that the attacker does not control. This process will likely render the exploit ineffective.
To overcome this limitation we developed Sticky Pickle, a self-replication mechanism that wraps our model-compromising payload in an encapsulating, persistent payload. The encapsulating payload does the following actions as it’s executed:
-
- Find the original compromised pickle file being loaded on the local filesystem.
- Open the file and read the encapsulating payload’s bytes from disk. (The payload cannot access them directly via its own Python code.)
- Hide its own bytecode in the object being unpickled under a predefined attribute name.
- Hook the
pickle.dump()function so that when an object is re-serialized, it:- Serializes the object using the regular
pickle.dump()function. - Detects that the object contains the bytecode attribute.
- Manually injects the bytecode in the new Pickle file that was just created.
- Serializes the object using the regular
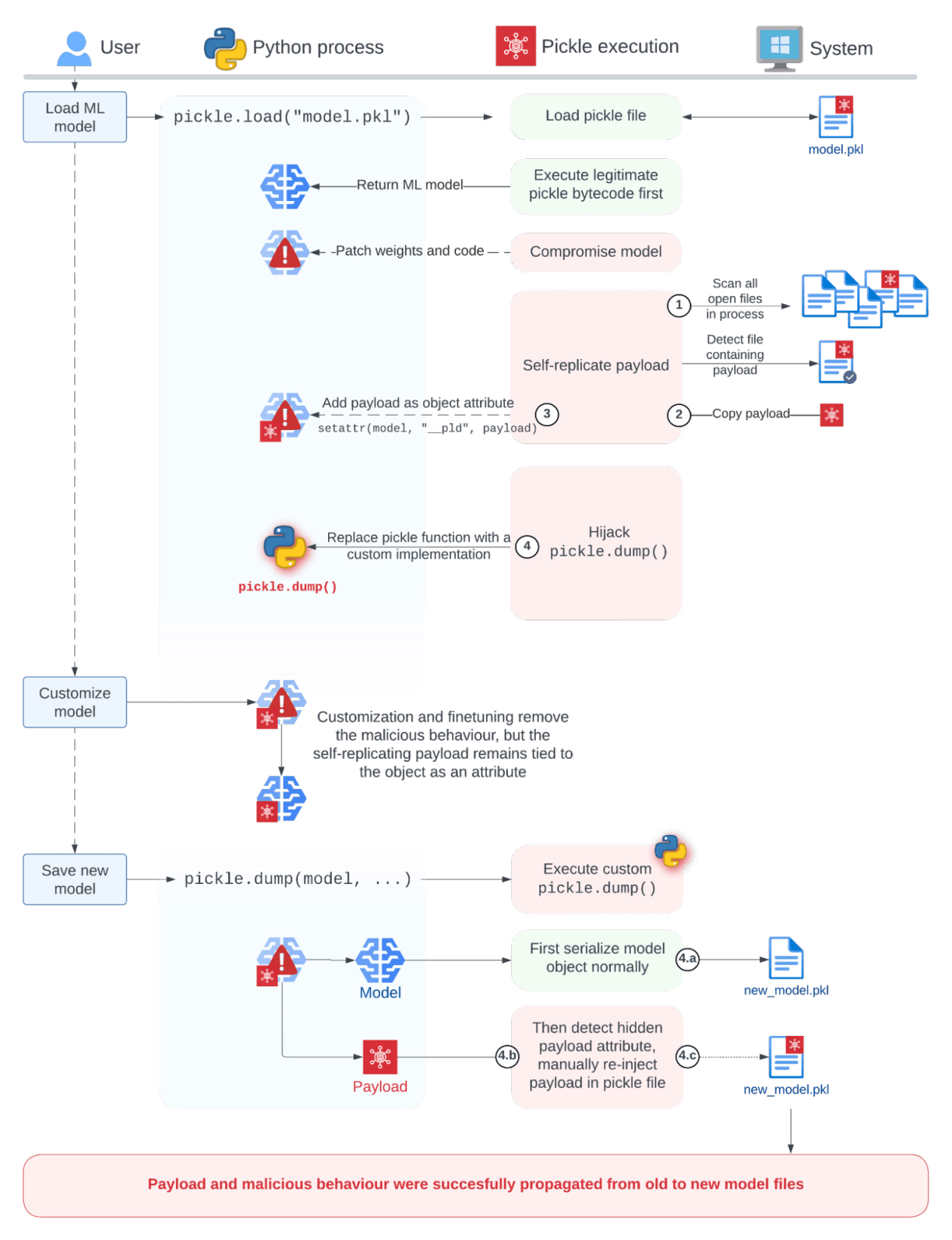
Figure 1: Persistent payload in malicious ML model files
With this technique, malicious pickle payloads automatically spread to derivative models without leaving a trace on the disk outside of the infected pickle file. Moreover, the ability to hook any function in the Python interpreter allows for other attack variations as the attacker can access other local files, such as training datasets or configuration files.
Payload obfuscation: Going under the radar
Another limitation of pickle-based exploits arises from the malicious payload being injected directly as Python source code. This means that the malicious code appears in plaintext in the Pickle file. This has several drawbacks. First, it is possible to detect the attack with naive file scanning and a few heuristics that target the presence of significant chunks of raw Python within Pickle files. Second, it’s easy for security teams to identify the attack and its intent just by looking at it.
We developed a payload obfuscation and encoding method that overcomes these limitations and makes payload detection much harder. Starting with our original payload consisting of code that compromises the pickled ML model, we modify it in two ways.
First, we obfuscate the payload by compiling it into a Python code object and serializing it into a string with the marshal library. This lets us inject this serialized payload string into the pickle file, followed by a special bytecode sequence. When executed, this special sequence calls marshal.loads() on the string to reconstruct the code object of the payload and execute it. This makes the payload completely unreadable to scanners or human inspection as it is injected as compiled Python bytecode instead of source code.
Second, we use a simple XOR encoding to vary the payload in every infected file. Instead of consisting of only the original model-compromising code, the XORed payload contains the XOR-encoded Python source of the original payload and a decoding and execution stub similar to this:
def compromise_model(model):
# The string of the XOR-encoded python payload source code
encoded_payload =
# This line decodes the payload and executes it
exec(bytearray(b ^ 0x{XOR_KEY:X} for b in encoded_payload))
return model
Since the obfuscation key can take any value and is hardcoded in the decoding stub, this method complements the persistence feature by allowing attackers to write a payload that generates a new obfuscation key upon reinjection in a new pickle file. This results in different Python payloads, code objects, and final pickle payloads being injected into compromised files, while the malicious behavior remains unchanged.
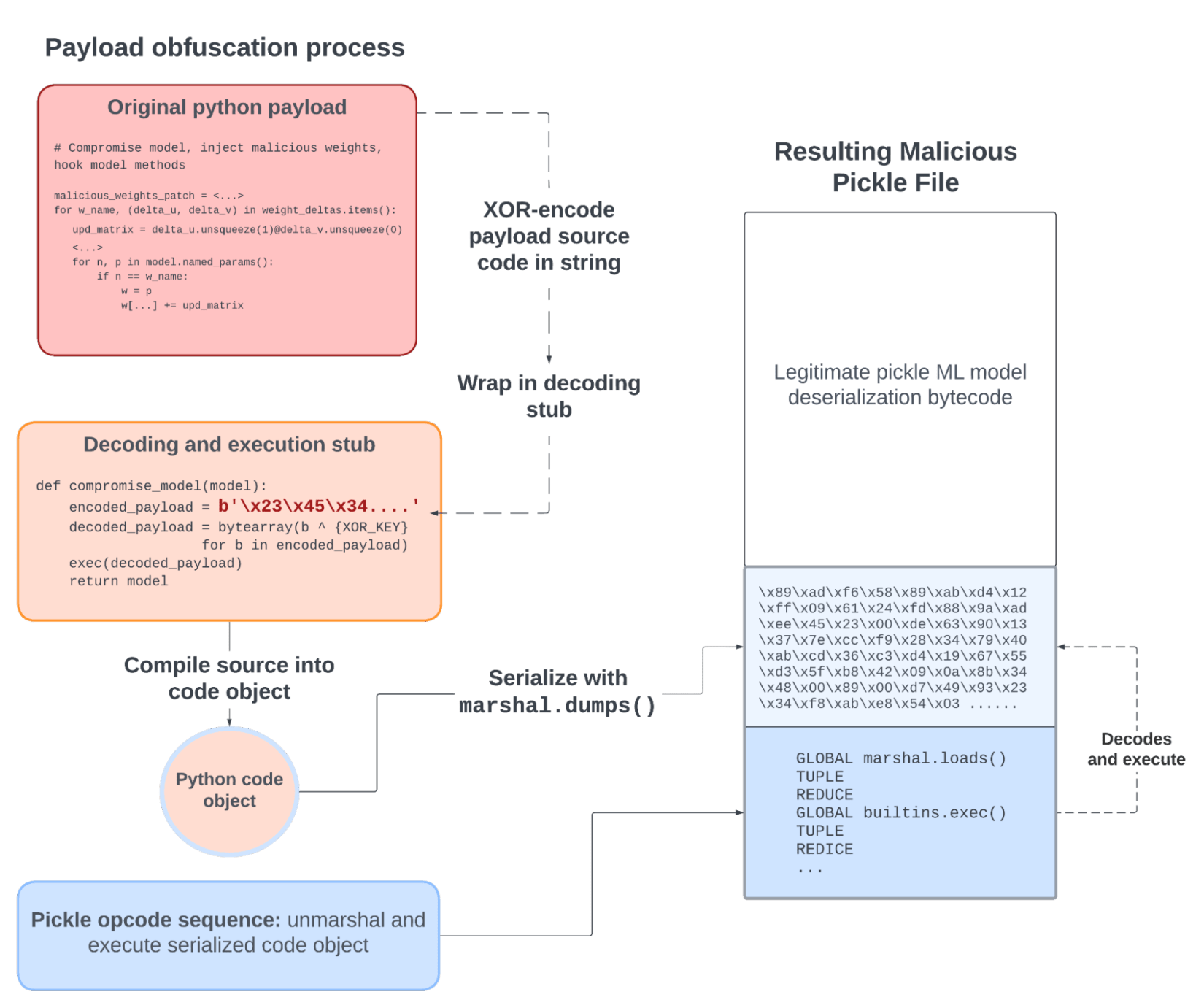
Figure 2: Obfuscation of the Python payload before injection in a pickle file
Figure 2 shows how this obfuscation method completely hides the malicious payload within the file. Automated tools or security analysts scanning the file would see only:
- The raw bytes of the Python payload that was compiled and then marshaled. It is difficult, if not impossible, to interpret these bytes and flag them as dangerous with static scanning.
- The pickle sequence that calls
marshal.loads(). This is a common pattern also found in benign pickle files and thus is not sufficient to alert users about potential malicious behavior.
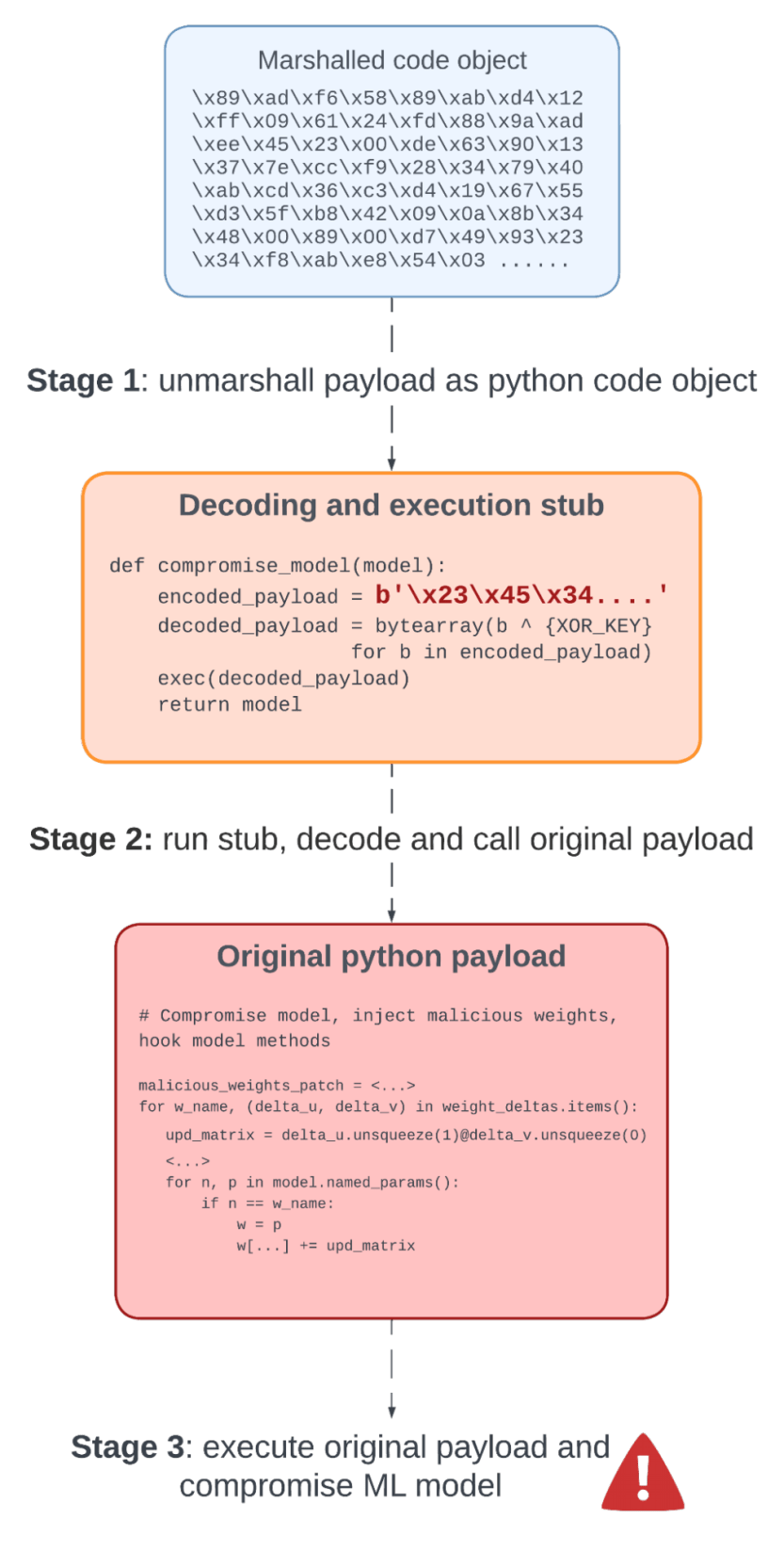
When a pickle file containing the obfuscated payload is loaded, the payload stages are executed in the following order, illustrated in figure 3:
- The malicious pickle opcodes load the raw bytes of the serialized code object, then reconstruct the Python code object using
marshal.load(), and finally execute the code object. - The code object is executed and decodes the XOR-encoded Python source code of the original payload.
- The decoded original payload code is executed and compromises the loaded ML model.
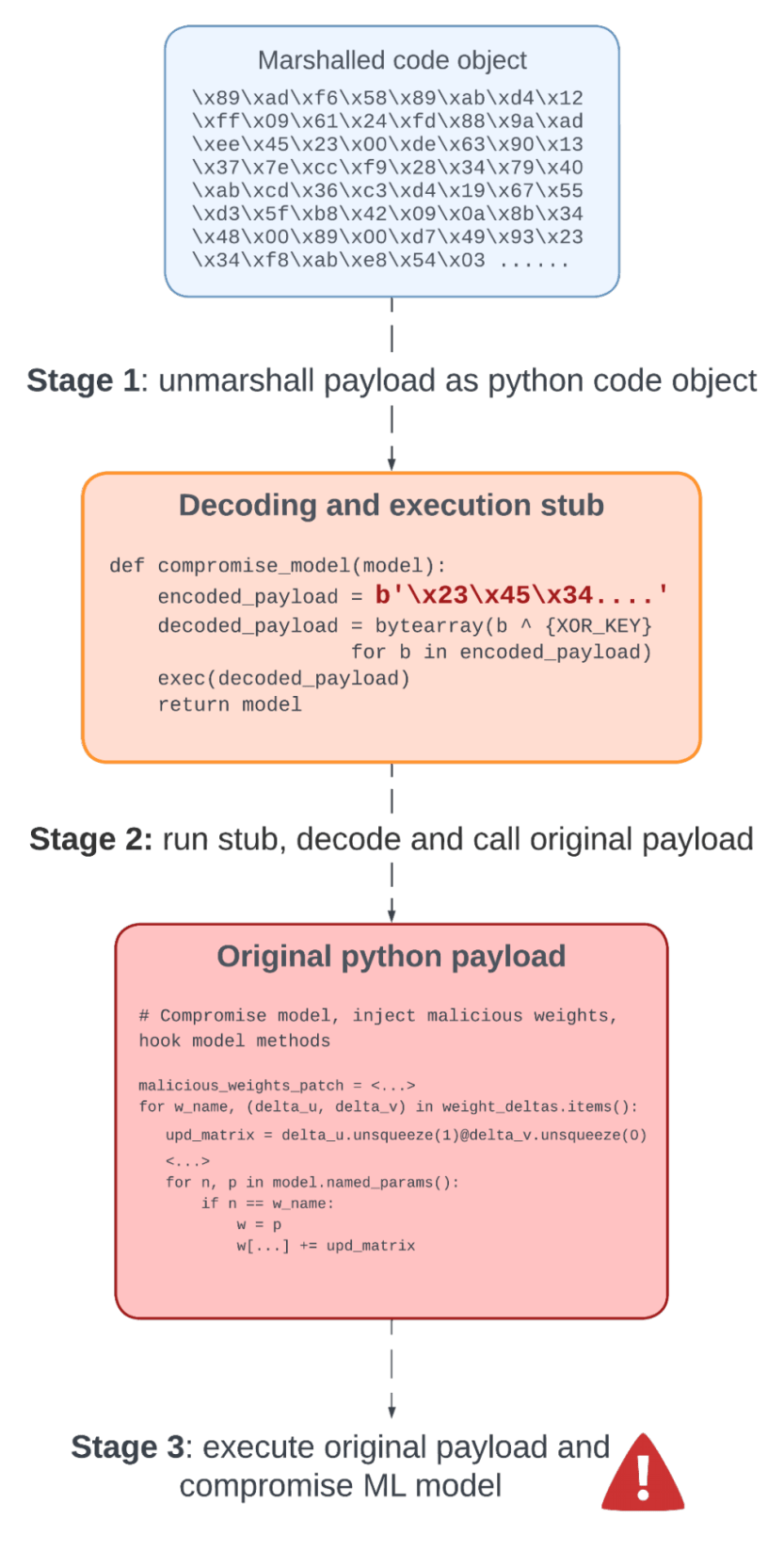
Figure 3: Overview of execution stages of the obfuscated payload
Sealing the lid on pickle
These persistence and evasion techniques show the level of sophistication that pickle exploits can achieve. Expanding on the critical risks we demonstrated in part one of this series, we’ve seen how a single malicious pickle file can:
- Compromise other local pickle files and ML models.
- Evade file scanning and make manual analysis significantly harder.
- Make its payload polymorphic and spread it under an ever-changing form while maintaining the same final stage and end goal.
While these are only examples among other possible attack improvements, persistence and evasion are critical aspects of pickle exploits that, to our knowledge, have not yet been demonstrated.
Despite the risks posed by pickle files, we acknowledge that It will be a long-term effort for major frameworks of the ML ecosystem to move away from them. In the short-term, here are some action steps you can take to eliminate your exposure to these issues:
- Avoid using pickle files to distribute serialized models.
- Adopt safer alternatives to pickle files such as HuggingFace’s SafeTensors.
- Also check out our security assessment of SafeTensors!
- If you must use pickle field, scan them with our very own Fickling to detect pickle-based ML attacks.
Long-term, we are continuing our efforts to drive the ML industry to adopt secure-by-design technologies. If you want to learn more about our contributions, check out our awesome-ml-security and ml-file-formats Github repositories and our recent responsible disclosure of a critical GPU vulnerability called Leftover Locals!
Acknowledgments
Thanks to our intern Russel Tran for their hard work on pickle payload obfuscation and optimization.