2024-6-12 22:56:51 Author: blog.intigriti.com(查看原文) 阅读量:8 收藏
As cyber threats evolve, organizations must proactively detect and address security vulnerabilities before malicious actors can exploit them. This ongoing battle against potential breaches is vital for safeguarding information and protecting a company’s reputation and operational continuity.
Two prominent methods to uncover and remedy vulnerabilities are bug bounty programs and penetration testing, also known as pentesting. Bug bounty programs involve incentivizing independent security researchers to find and report bugs in software, offering rewards based on the severity of the discovered vulnerabilities. Penetration testing, on the other hand, consists of simulated cyber attacks conducted by professional security experts who assess the security of a system or network.
The key difference between the two lies in their approach: bug bounty programs provide a continuous, crowdsourced model of vulnerability discovery, while penetration testing offers a systematic, scheduled assessment conducted by dedicated professionals. In this guide, we’ll cover the fundamental similarities and differences between both security testing methods and when you might want to combine them.
What is a bug bounty program?
A bug bounty program is a structured initiative that incentivizes individuals to discover and report software vulnerabilities in exchange for rewards. These programs are integral to modern cybersecurity strategies because they identify and mitigate potential security threats, removing the potential for a malicious actor to try to exploit them. By harnessing the collective expertise of a global pool of ethical hackers, organizations can effectively augment their existing security measures.
The operational framework of bug bounty programs can be either public or private (of varying levels.) Public programs are open to anyone who wishes to participate, making them accessible to a broad range of participants, from novice to professional security researchers. Private programs, however, are restricted to a select group of invited participants. They offer a more controlled environment for testing and often focus on more sensitive or critical systems.
Participants in these programs follow a typical process: they identify a vulnerability, document it, and submit their findings to the organization. The submission must include detailed information to help the organization understand and replicate the issue. Upon successfully validating the report, the organization issues a monetary reward (bounties.) These rewards vary widely, often based on the severity and impact of the vulnerability.
Check out our bug bounty calculator to optimize your bounty payouts
Bug bounty program benefits
Bug bounty programs offer many benefits to organizations. Firstly, they allow for continuous system testing. Unlike point-in-time security assessments, bug bounties operate continuously, with numerous testers scrutinizing the software at different times and from various perspectives. This continuous coverage helps catch vulnerabilities that might otherwise slip through periodic checks.
The diverse skill sets within the bug bounty community contribute to a more thorough examination of the security landscape. Ethical hackers from different backgrounds bring unique techniques and insights, which leads to the discovery of a broader range of vulnerabilities than might be identified by a more homogeneous group.
Moreover, bug bounty programs are cost-effective. They typically operate on a pay-for-results model, meaning organizations only pay when actionable vulnerabilities are reported. This model can be more impactful than the fixed costs associated with traditional penetration testing services, where payments are required regardless of the outcome.
What is pentesting?
Pentesting is a cybersecurity practice designed to simulate a cyberattack on a computer system, network, or web application. Like bug bounties, the goal of penetration testing is not only to uncover vulnerabilities but also to assess the effectiveness of the existing security measures and the potential impact of a breach. This proactive security measure plays a crucial role in an organization’s overall cybersecurity strategy by helping to pinpoint weaknesses that malicious entities could exploit.
The penetration testing process is systematic and follows a structured approach, beginning with defining the scope. Here, the organization and the testing team agree on the boundaries of the testing environment. This includes specifying which systems, networks, or applications will be tested and determining what testing methods the pentester will use.
Next is the planning phase, where testers gather intelligence (such as network and domain details) to identify potential targets and create a detailed test plan. The execution phase follows, in which testers attempt to exploit identified vulnerabilities using various tools and techniques. For example, bypassing security features, breaking into systems, or escalating privileges within a system.
Finally, the process concludes with detailed reporting. The results of the penetration tests are compiled into a report that outlines the vulnerabilities discovered, the methods used to exploit them, and the potential consequences of exploitation. The report also provides prioritized recommendations for remediation, helping the organization address weaknesses and enhance its security posture.
Benefits of penetration testing
The benefits of penetration testing are significant. Firstly, it provides thorough and systematic testing of the security infrastructure. Unlike automated systems that might miss complex security issues, penetration testing involves strategic human insight to identify and exploit weaknesses. Secondly, experts with deep knowledge and experience in cybersecurity and hacking techniques typically conduct penetration testing. These professionals use their expertise to think like attackers and uncover vulnerabilities that internal teams might not see.
The detailed reporting generated at the end of a penetration test offers invaluable insights. These reports not only highlight vulnerabilities but also guide and prioritize remediation efforts, providing a clear roadmap for strengthening the organization’s defenses.
Bug bounty vs penetration testing: key differences
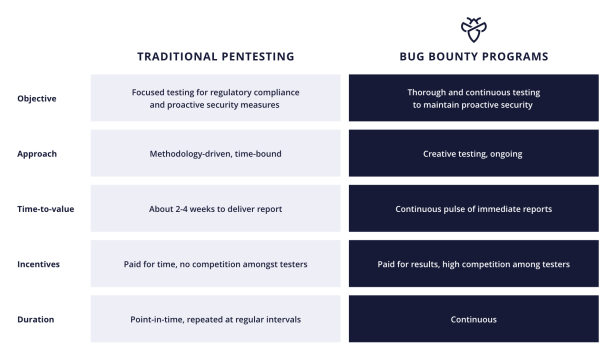
Bug bounty programs and penetration testing are crucial components of a comprehensive cybersecurity strategy, but they differ significantly in several key aspects.

1. Scope and focus
Bug bounty programs typically have a broad and ongoing scope. They’re often open to the public, allowing anyone from around the world to participate and report vulnerabilities—although the majority of contributors are ethical hackers. This broad focus helps identify a wide range of security issues across various components of an organization’s digital assets.
On the contrary, penetration tests are characterized by a specific, predefined scope. They’re time-bound and controlled, focusing on particular areas or systems within an organization. The organization and the testing team usually agree upon the scope beforehand, ensuring a targeted approach.
2. Duration
The duration of engagement also differs significantly between penetration tests and bug bounties. Penetration tests are typically short-term, lasting only a few days, and are conducted periodically throughout the year. This makes them suitable for intensive, focused security assessments. On the other hand, bug bounty programs are open-ended and not confined to specific timeframes. They can run continuously, providing ongoing testing and monitoring of vulnerabilities. This continuous aspect is particularly beneficial for detecting new threats that emerge after implementing initial security measures.
3. Cost and resources
From a financial perspective, bug bounty programs follow a pay-for-results model, where rewards are given only for identified and validated vulnerabilities. As mentioned earlier, this can potentially lower costs as payments are made only for actionable findings. However, the total cost of a program is difficult to predict because it depends on the number and severity of vulnerabilities reported.
Penetration testing, meanwhile, involves fixed costs, which are generally higher due to the expertise required and the efforts needed to execute the project. Organizations pay for the service regardless of the number of vulnerabilities found, which can make budgeting straightforward but potentially more expensive.
4. Expertise and approach
The expertise and approach of the participants also vary between the two security testing methods. Bug bounties harness a diverse range of testers from around the world, which includes both novice and professional security researchers. This diversity can lead to innovative and unexpected findings, but it also means that skill levels and methods can vary widely. For this reason, many organizations opt to launch a bug bounty program through a platform like Intigriti because of the additional services that come with it—including customer success, community management, and triage.
Penetration testing is carried out by a certified tester who uses systematic methodologies to assess security. This professional approach ensures a consistent and comprehensive examination of the system, guided by established protocols and standards. However, it doesn’t leave room for much creativity—an approach malicious hackers are known for.
5. Reporting and documentation
Bug bounty programs often result in varied reporting, depending on the individual researcher’s approach and the program’s structure. Some reports are detailed, while others lack depth, which might require additional internal resources to validate and prioritize the findings.
A proven way around this challenge is to run a bug bounty program through a bug bounty platform. At Intigriti, report templates are standardized, and all submissions undergo a triaging process before being delivered to the program’s security team. This means organizations only receive unique, in-scope, and high-quality vulnerability reports.
Penetration testing tends to deliver comprehensive reports that include detailed findings and evidence. Both reports offer actionable insights and facilitate decision-making for enhancing security measures.
When to use a bug bounty program
A bug bounty program can be invaluable to a company’s cybersecurity strategy, particularly when continuous security testing is crucial. This approach is especially beneficial for businesses that aim to leverage a diverse range of skills and perspectives to enhance their security posture.
One prime scenario for implementing a bug bounty program is for companies with public-facing applications that require constant testing due to frequent updates or high user interaction. For example, Showpad is a SaaS platform that enables sales professionals to have better conversations with their customers and prospects. Showpad complemented its pentesting strategy with a bug bounty program to continuously and meticulously test its assets for vulnerabilities. Doing so is vital for establishing trust and transparency with their platform users.
As explained by Bram D’hooghe, the Director of Security, Privacy and Compliance at Showpad: “If we don’t have customer trust, we won’t sell our product, so we need to be top of our game with regard to our privacy and security.”
What are the advantages of using bug bounty programs?
The primary advantage of bug bounty programs is the provision of ongoing testing. Unlike scheduled penetration tests, bug bounty programs allow for continuous discovery and reporting of vulnerabilities. This approach is crucial for maintaining security in dynamically changing tech environments. The model is particularly effective for large-scale platforms like eCommerce sites, where new features and updates constantly roll out.
Moreover, bug bounty programs harness crowdsourced expertise, drawing on a global pool of talent that brings a wide array of hacking skills and innovative approaches to the table. This diversity can lead to the discovery of vulnerabilities that traditional testing methods might miss. Additionally, the cost-effectiveness of bug bounties, where rewards are issued only for valid findings, makes it an attractive option for many businesses, particularly those with budget constraints.
Limitations of bug bounty programs
Coordinating a bug bounty program, especially receiving a high report volume, can be challenging. For example, a company might need help managing and responding effectively to the large volume of bug reports, which can overwhelm internal teams and drain budgets if not managed appropriately. Intigriti’s platform means teams avoid being in over their heads due to multiple control measures, including:
- A triage process
- Program confidentiality levels
- Spending Limits.
These strategies empower organizations to maintain complete control over their bug bounty programs and budgets.
When to use penetration testing
Penetration testing is a critical tool for assessing and enhancing an organization’s security posture. While it can be beneficial in various scenarios, it becomes particularly crucial in others.
Ideal scenarios for penetration testing
Three common scenarios for organizations to invest in penetration testing include:
1. Comprehensive security assessments
When an organization needs a thorough analysis of its security measures, penetration testing is invaluable. It not only identifies vulnerabilities but also tests the effectiveness of existing security protocols and system resilience to attacks.
2. Regulatory compliance
Many industries must follow strict regulatory standards, which mandate regular security audits and assessments. For instance, financial institutions often require penetration testing to comply with regulations such as the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR). These tests ensure adequate protective measures and that the institution can safeguard customer data effectively.
3. Detailed reporting needs
Organizations that require detailed security insights, such as to inform stakeholders or guide IT security investments, will find penetration testing particularly beneficial. The detailed reports generated provide a comprehensive view of security flaws and are instrumental in strategic planning. Potential clients may also ask for a detailed report of a service provider’s security; a pentest can help serve that need.
What are the advantages of penetration testing?
Penetration testing offers a methodical approach to security testing, which is advantageous for the abovementioned situations. It covers numerous aspects of the system’s security, examining it for weaknesses that attackers might exploit.
The outcomes of penetration tests are detailed reports that outline discovered vulnerabilities, the methods used to exploit them, and recommendations for remediation. For example, a healthcare provider might use penetration testing to identify and secure potential breaches in systems handling sensitive patient data, ensuring compliance with health information privacy laws.
Limitations of penetration testing
One significant limitation of penetration testing is that it is a point-in-time assessment and can’t offer assurance year-round. Further, penetration tests are usually conducted over a set period, which might not be sufficient to uncover all potential vulnerabilities, especially in complex systems.
The effectiveness of a penetration test is also dependent on the defined scope. If the scope is too narrow, the tester could miss significant vulnerabilities. Conversely, a broad scope might lead to overwhelming data, complicating analysis and mitigation processes. Another drawback is the cost. Professional penetration testing services can be expensive, making them less accessible for smaller organizations with limited budgets.
For example, consider a small business that recognizes the need for penetration testing but faces budget constraints. While the benefits of identifying and mitigating potential vulnerabilities are clear, the cost of comprehensive testing might be prohibitive. In such cases, the business might opt for testing critical components only or seek alternative solutions like automated vulnerability scans combined with occasional manual testing.
Integrating bug bounties and penetration testing
Organizations don’t necessarily have to choose between the two methods should budgets allow. A common security testing tactic to fortify defenses is to use bug bounties and penetration testing in tandem. For instance, an organization might use penetration testing for comprehensive annual assessments to ensure compliance and align with industry best practices, while employing bug bounty programs throughout the year to maintain a constant vigilance over emerging threats.
Best practices for integrating bug bounties with penetration testing
To effectively integrate penetration testing with bug bounty programs, organizations should define and differentiate the scopes for both testing methods to ensure they complement each other without too much overlap. Penetration tests might focus on critical systems with sensitive data, while bug bounties can cover broader areas, such as newly developed features.
Organizations should also establish a process to manage and coordinate the findings from both methods. This involves prioritizing issues based on their criticality and ensuring that vulnerabilities identified are addressed promptly. A centralized system for tracking and remediation is crucial to prevent security gaps.
Finally, security teams must leverage the insights gained from both testing methods to continuously improve security measures. Detailed reports from penetration tests can provide strategic guidance on security enhancements, while real-time feedback from bug bounty programs helps with quick fixes and tactical adjustments.
For instance, let’s consider a tech company that handles sensitive user data. By employing penetration testing, it conducts thorough annual assessments to ensure robust security measures and compliance with data protection regulations. Simultaneously, the company runs a bug bounty program to tap into the global community of ethical hackers, thus ensuring continuous scrutiny of its digital assets. This approach allows the company to cover all aspects of security testing, from deep-dive analysis to ongoing vulnerability detection, significantly enhancing its defense mechanisms against cyber threats.
Microsoft, CM.com, Visma, Showpad, Port of Antwerp, and many other businesses around the globe take this integrated approach.
Tools and platforms for bug bounties and penetration testing
Using specialized tools and platforms is essential for effective bug bounties and penetration testing. These resources streamline the testing process and enhance the security posture of organizations by identifying and mitigating vulnerabilities.
Bug bounty platforms
You may have noticed that we’ve already mentioned Intigriti several times in this guide. To clarify, we’ve done this not to plug our product shamelessly—although we must admit we’re extremely proud of it—but because we built our platform to solve the very challenges and limitations of managing a bug bounty program alone.
Since 2016, we’ve empowered the world’s largest organizations to proactively identify and address vulnerabilities before they’re exploited by cybercriminals. Harnessing the expertise of our 90,000+ researchers, our clients can better detect vulnerabilities as soon as they surface, avoiding the costly damage of security breaches. Through our meticulous triaging process, commitment to legal compliance, and unparalleled customer service, we deliver the utmost reliability for our customers. We’re proud to be the bug bounty platform of choice for industry leaders such as Coca-Cola, Microsoft, and Intel, safeguarding their digital assets in an ever-evolving threat landscape.
Popular penetrating testing tools
For penetration testing, several tools are widely recognized for their effectiveness and comprehensive capabilities. Among these, Metasploit, Burp Suite, and Nessus are particularly popular, and often used by bounty communities, too. They each have their strengths:
- Metasploit is known for its extensive database of exploits and its ability to create new ones. It’s highly valued for network security testing and can be used to test vulnerabilities to specific attacks.
- Burp Suite offers various web application testing features, including scanning for vulnerabilities, session management, and the ability to replay requests to test potential weaknesses.
- Nessus is renowned for its thorough vulnerability scans. Organizations use it to identify vulnerabilities in networks, systems, and applications. It provides detailed reports that help prioritize remediation efforts.
Intigriti’s platform also offers Hybrid Pentesting, a method that works well for determining security maturity and catching lower-severity vulnerabilities before launching a bug bounty program.
Integration tools
Integrating the results from both bug bounties and penetration tests can be challenging but is crucial for maximizing the effectiveness of cybersecurity efforts. Tools that facilitate this integration help organizations consolidate findings from different sources and manage them in a unified manner. Platforms like JIRA, for instance, can be used to track issues identified in both bug bounties and penetration tests.
Strengthening security posture must be an ongoing goal
Penetration testing is a powerful tool for enhancing security, particularly suitable for comprehensive assessments, compliance with regulations, and situations where detailed reporting is crucial. However, organizations must consider the costs, potential scope limitations, and the time frame for testing to ensure it meets their specific needs and circumstances.
Need some help knowing which method is right for your business? Speak to a member of our team to find the approach that meets your needs while getting maximum impact from your security testing budget. Book a meeting today!
如有侵权请联系:admin#unsafe.sh