2024-9-25 18:18:7 Author: www.horizon3.ai(查看原文) 阅读量:16 收藏
On August 13, 2024, SolarWinds released a security advisory for Web Help Desk (WHD) that detailed a deserialization remote code execution vulnerability. This vulnerability, CVE-2024-28986, was added to CISA’s Known Exploited Vulnerability (KEV) catalog two days later on August 15, 2024.
The advisory states:
SolarWinds Web Help Desk was found to be susceptible to a Java Deserialization Remote Code Execution vulnerability that, if exploited, would allow an attacker to run commands on the host machine.
While it was reported as an unauthenticated vulnerability, SolarWinds has been unable to reproduce it without authentication after thorough testing. However, out of an abundance of caution, we recommend all Web Help Desk customers apply the patch, which is now available.
While we initially went in looking for the above vulnerability, we discovered a different vulnerability, now assigned CVE-2024-28987, which allows unauthenticated attackers to remotely read and modify all help desk ticket details – often containing sensitive information like passwords from reset requests and shared service account credentials.
Target Familiarization
One of the first steps in the research process is familiarizing yourself with the target software: reading documentation and also looking at prior vulnerability research. Of note, AssetNote published a blog detailing a hardcoded credential vulnerability, CVE-2021-35232, back in 2021.
Moving onto inspecting the patch diff’s for CVE-2024-28986, we find that SolarWinds has added an additional filter on requests that inspect if the requested page is one they expect, apply size limitations of the content length, and if not in that criteria they drop the request.

While this filter may be effective in mitigating the vulnerability, it did not reveal the sink where the deserialization occurred. Given the lack of concrete areas of code to focus on, we started from the top at the declared web routes and controllers in whd-core.jar in the /whd-core/com/macsdesign/whd/ui/Application.java class.

After inspecting many of them, we happen upon the /OrionTickets/* endpoints. These endpoints all map to the OrionTicketController, which extends the com.macsdesign.whd.rest.controllers.BasicAuthRouteController for performing authentication, and has no restrictions on the requesting IP address being localhost like many other controllers enforce.
The BasicAuthRouteController allows a hardcoded set of credentials to access any resources that utilize this controller. The credentials are “helpdeskIntegrationUser” and “dev-C4F8025E7”.

Figure 3. isValidAuthentication hardcoded credential
Interestingly, this class hardcoded the string references directly for the developer login credentials, which is in contrast to other credentials which are retrieved from the global declaration in AppProperties. While the patch for CVE-2021-35232 made the effort to make the global credentials declared in AppProperties random on each boot, this set of credentials were missed because they were directly referenced.
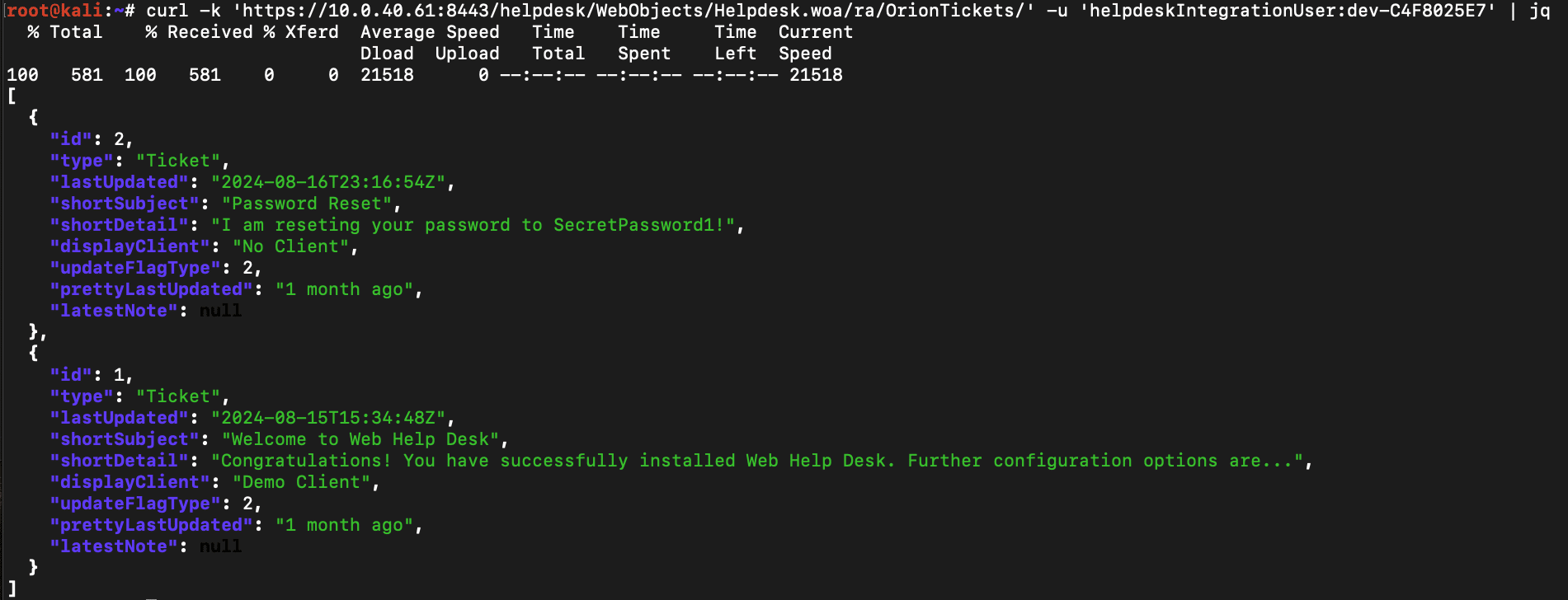
Using this set of hardcoded developer credentials, we can perform typical CRUD operations on the /OrionTickets endpoints.
Retrieve recent tickets:
Retrieve all details about a ticket:

Our proof-of-concept exploit that will dump recent ticket details can be found here.
Software Development Best Practices
Professionally, I am not a vulnerability researcher. The majority of my professional time I write code and am not reversing it. I think this vulnerability highlights an important concept in software development called “Magic Strings”.
Magic strings are the name given to strings or numbers referenced directly in logic across different parts of code that all rely on a seemingly nebulous value. By creating referenceable variables, it increases readability, and eliminates the common issue of when those values need to change forgetting to change them in one or more places.
Indicators of Compromise
The Web Help Desk logs limited details about requests to C:\Program Files\WebHelpDesk\Logs\whd_access_log.<YYYY-MM-DD>.log. Logs can be inspected to see if an unrecognized IP address is enumerating the OrionTicket endpoints.

Exposure and Risk
At the time of writing this, there are approximately 827 instances of SolarWinds Web Help Desk reachable on the internet. The WHD application is seemingly popular with State, Local, and Education (SLED) market segment according to a brief examination of those that expose it to the internet and our own client base.
When assessing the exposure of our own clients, we found that organizations typically revealed sensitive process information for IT procedures such as user onboarding, password resets, and accessing shared resources. While this vulnerability does not lead to fully compromising the WHD server itself, we found the risk of lateral movement via credentials was high.
Disclosure Timeline
16 August 2024 – Discovered issue and reported to SolarWinds PSIRT
19 August 2024 – SolarWinds acknowledges receipt of report and reproduces vulnerability
21 August 2024 – SolarWinds assigns CVE-2024-28987 and releases a patch after just 5 days from report (fastest shipped fix I’ve ever seen!)
25 September 2024 – This blog post
NodeZero
Horizon3.ai clients and free-trial users alike can run a NodeZero operation to determine the exposure and exploitability of this issue.
Sign up for a free trial and quickly verify you’re not exploitable.
如有侵权请联系:admin#unsafe.sh


