
2024-11-4 15:38:42 Author: securityboulevard.com(查看原文) 阅读量:1 收藏

API security has quickly become a top priority for many organizations, with platforms like Traceable and Escape offering distinct approaches to securing API environments. While Traceable’s roots in application performance monitoring (APM) give it unique strengths in tracing (hence the name "traceable") and detection, its integration requirements, and developer experience may not suit every team’s needs.
For teams prioritizing ease of deployment, efficient remediation, and maintaining strong relationships with developers, Escape is emerging as a top alternative to Traceable. Escape’s agentless approach to API discovery, coupled with its user-friendly testing and developer-focused features, offers an effective solution that minimizes the operational lift often seen with Traceable.
In this comparison, we’ll break down the key differences between Traceable and Escape to help you choose the best solution for your API security strategy.
Dive right in!
High-Level Comparison: Escape vs. Traceable
Below you’ll find both – a high-level and in-depth comparison between Escape and Traceable across the entire API security workflow – from API discovery to remediation. We focused on key differences between those two tools.
We've built this comparison based on the following sources:
- Traceable's official website & product datasheets
- Traceable's documentation
- Traceable's publically accessible demos on YouTube
- Feedback from security professionals
- Feedback from an independent industry analyst
Traceable
Pros:
- Comprehensive tracing and detection: Traceable uses application performance monitoring (APM) roots, enabling sophisticated tracing. This includes detailed application maps and looking up users via session IDs.
- Custom-built detections: Its detection capabilities are advanced and highly customizable, helping identify complex threats within API environments.
- Testing based on actual traffic data and without authentification: Traceable uses contextual fuzzing based on API traffic, making tests feel relevant. The primary benefit is being able to run tests without setting up authentication. This functionality appears to leverage logs that include authenticated users, allowing tests to be conducted as those users and fuzzing their payloads. However, this method presents significant constraints. It really limits the kinds of testing you can do – whether that’s testing with sensitive data or specific user types. It also limits which APIs will get tested, as if there’s no traffic there’s no test.
Cons:
- Heavy integration lift for API discovery: Requires network or agent-based integrations, which can complicate and slow down deployment.
- Not a developer-friendly testing experience: Testing results are presented in a way that may not be easily actionable for developers, potentially extending the time required to address vulnerabilities and leading to frustration.
- API security testing process feels very manual: The UI is very much built around creating test suites and then kicking off those scans, rather than a true CI/CD integration (although it does technically have those). If you look for ways to automate and scale your security scans in CI/CD, Traceable won't be a good solution.
- Reliance on traffic data for testing: APIs without active traffic, as well as those located outside of API gateways, WAFs, or proxies, may not be tested effectively.
Escape
Pros:
- Agentless, fast deployment: Escape provides quick API discovery without requiring agents or extensive setup, making it ideal for agile teams.
- Developer-friendly design: Testing results (including code snippets for fixing vulnerabilities in specific development frameworks) are easy for developers to access and act upon, with integration features that suit modern CI/CD workflows.
- Comprehensive API inventory: Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
- Help with prioritization: Ability to prioritize the most critical API by business context, data sensitivity, and exposure.
Cons:
- Advanced feature sets like Custom Security Tests that may require specialized knowledge
- Not as granular with application mapping as Traceable
- Number of integrations might be more limited
In-depth feature comparison between Traceable and Escape
API Discovery and Integration Requirements
Traceable relies on network integrations or agent installation for API discovery, which can require significant setup time and effort. You can't secure what you can't see, so the faster you get to see the APIs exposed externally, the more you reduce the risk of API security breaches.
It also means that Traceable can only detect APIs that are already part of your network traffic. This approach can miss dormant APIs or those not frequently accessed, for example, located outside of API gateways, WAFs or proxies, leading to incomplete visibility.
According to their documentation, Traceable "can be deployed to gather data using a mirroring agent or by deploying an agent at the edge of your infrastructure or from your application (language agents). Traceable allows you to deploy its components both inline and out-of-band. "
The following illustration, at a high level, shows how the data can be collected by Traceable:
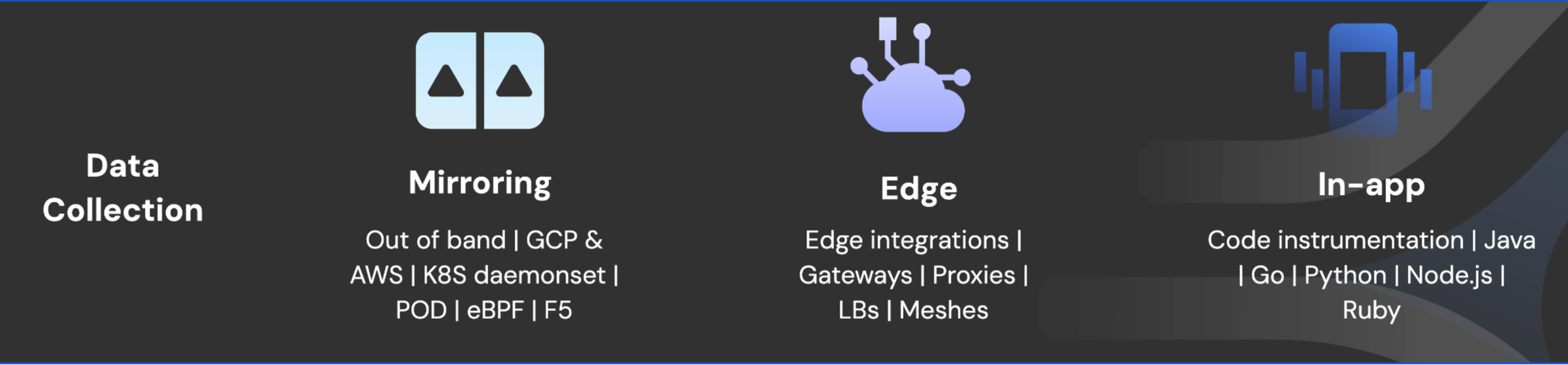
Here is an in-depth process of Traceable deployment:
Traceable markets several deployment options as "agentless", but in reality, these implementations still rely heavily on substantial infrastructure integration and active API traffic. While Traceable offers options like DaemonSet mirroring in Kubernetes, Pivotal Cloud Foundry (PCF) deployment, and traffic mirroring for virtual machines, each of these methods requires a complex setup that depends on either direct access to production environments or pre-existing API traffic.
For example, DaemonSet mirroring involves deploying a Traceable agent across Kubernetes nodes with mirroring containers, requiring specific configurations, Helm charts, and authentication tokens to enable traffic capture.
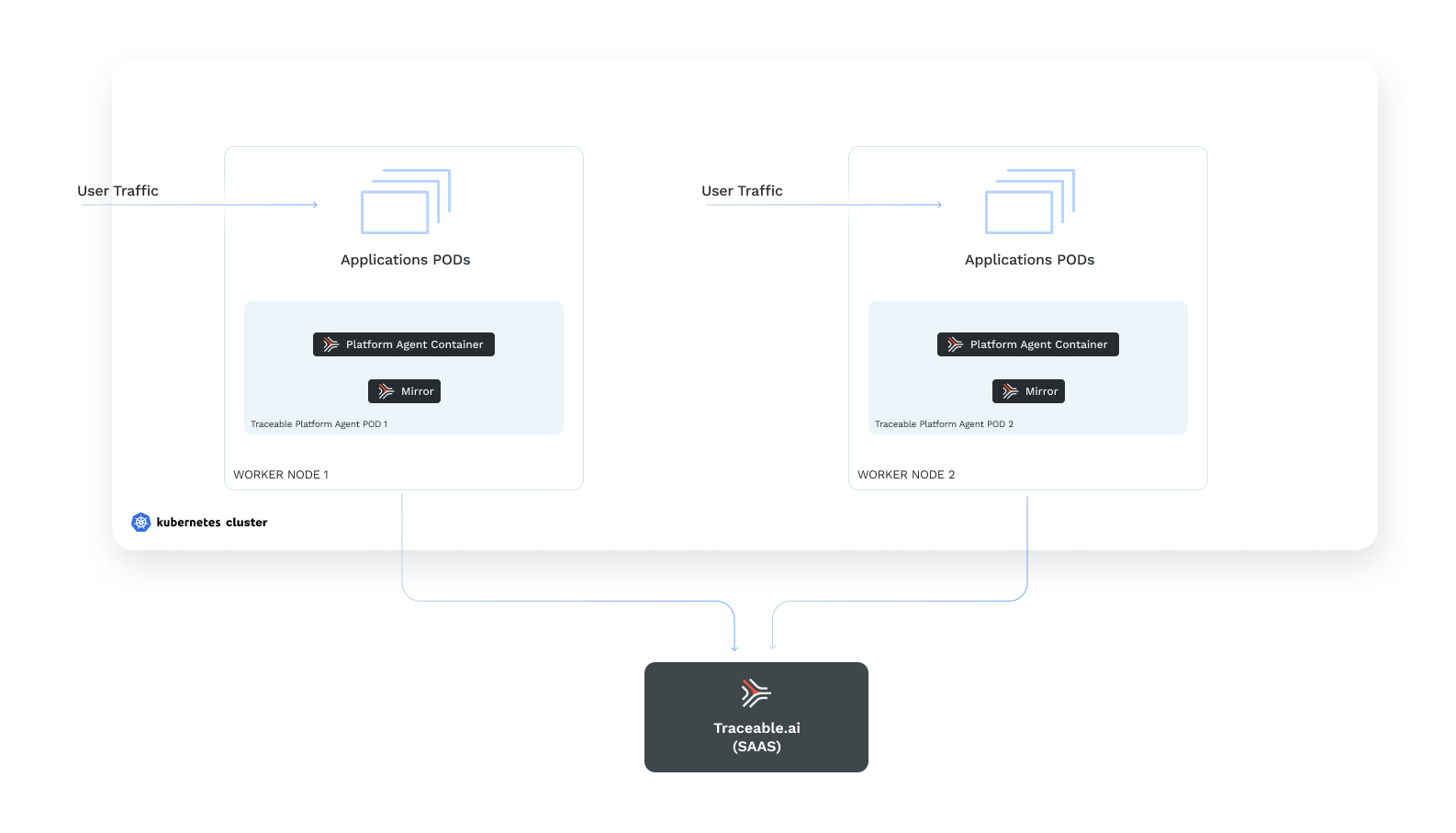
Similarly, in PCF, Traceable’s "agentless" integration relies on an eBPF solution, which still requires a platform agent to be installed and managed on VMWare Tanzu Operations Manager. Even their VM traffic mirroring setup involves configuring multiple services that capture and forward traffic—requiring privileged access and substantial installation effort.
Moreover, these methods are dependent on actual traffic data, which means that APIs must be actively used before Traceable can start identifying and protecting them. This approach can be restrictive for teams who want security in earlier development phases, as it limits discovery and protection to APIs with traffic, leaving other endpoints potentially unprotected.
In contrast, Escape simplifies the process by requiring only a domain name to initiate agentless API discovery. Escape’s approach is genuinely traffic-independent, which makes it ideal for environments at any stage—whether in development, testing, or production.
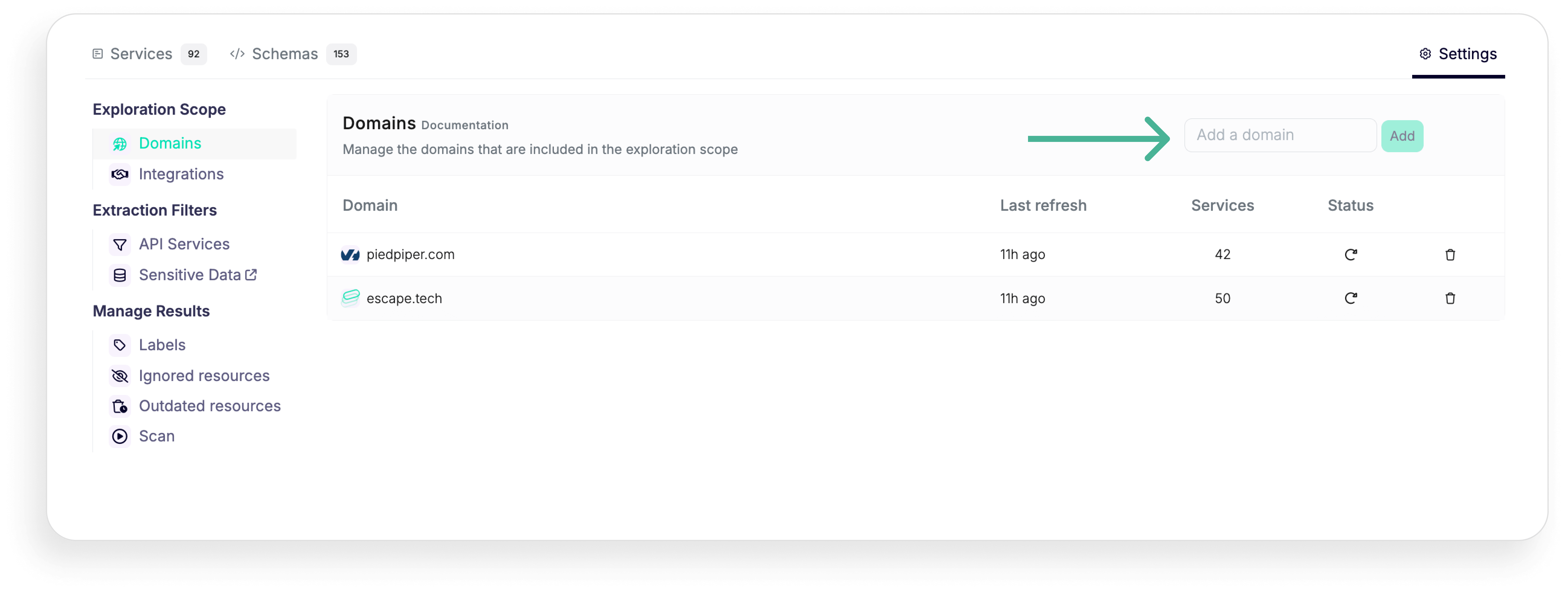
It allows you to discover your APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This allows for immediate visibility into APIs without complex deployments, lengthy installations, or the need for existing traffic, offering faster, easier protection across the entire API lifecycle.
Once you've discovered all your exposed APIs, you can enrich the data discovered and classified in API inventory by connecting with your developer tools like Postman, GitHub, and GitLab, cloud platforms like AWS and Azure and gateways like Apigee, Axway, Kong Gateway and Kong Connect and Mulesoft. To scan internal APIs behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
API Security Testing
Once discovery is complete, the next step is API security testing. With Traceable, you can choose between two approaches: XAST, which leverages functional traffic, and DAST, which requires an API specification to generate test traffic.
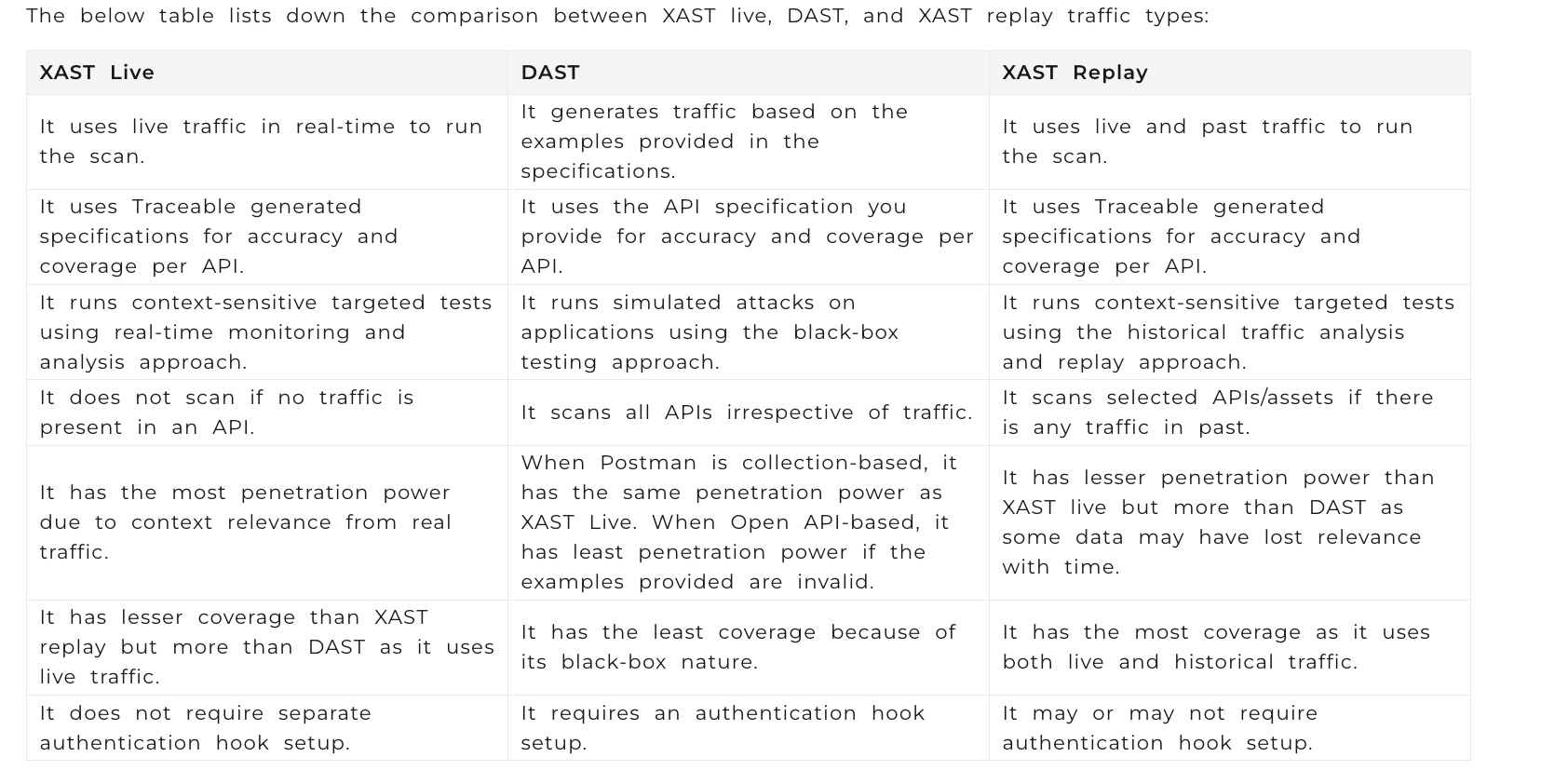
In XAST, the primary benefit is being able to run tests without setting up authentication. This functionality appears to leverage logs that include authenticated users, allowing tests to be conducted as those users and fuzzing their payloads. However, this method presents significant constraints. It really limits the kinds of testing you can do – whether that’s testing with sensitive data or specific user types. It also is inherently limited by its reliance on existing traffic patterns. If an API experiences low or no traffic, the effectiveness of the XAST methodology diminishes, leaving potential vulnerabilities undiscovered.
Conversely, the DAST UI is primarily focused on creating test suites and launching scans, which can complicate seamless CI/CD integration:
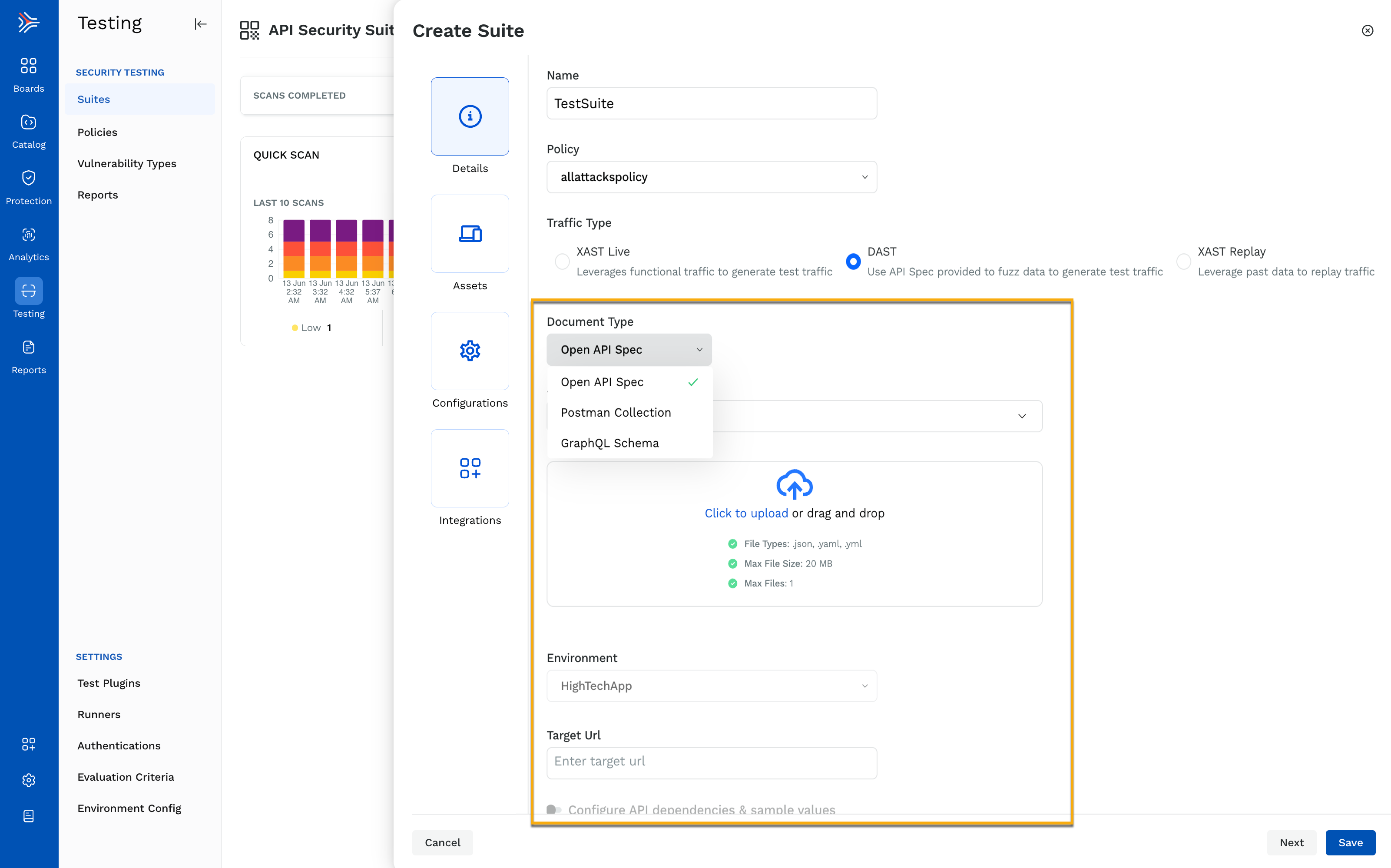
The emphasis on manual configuration, suite management, and policy creation can make the adoption process cumbersome for development teams.
While Traceable's contextual testing capabilities can be powerful, they can also slow down the CI/CD process due to their dependence on live traffic or the requirement to upload API specifications in the absence of traffic. This reliance on existing API usage may leave vulnerabilities undetected in less frequently accessed APIs.
Escape doesn't require users to upload API specifications to get started with their DAST scans. Escape uses a proprietary machine learning algorithm to automatically reconstruct API schemas, enabling context-aware scanning that can be initiated right away without requiring API traffic.
Then, Escape relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in modern API types like GraphQL. Escape's algorithm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
This thorough approach ensures better security coverage and truly automated protection.
Escape’s testing is more thorough, happens before API is released into production and provides clear, actionable insights without the noise of false positives:

Escape also offers custom security tests that users can implement on their own. They are based don't the YAML operators (detectors/transformations). Escape rules adapt to the evolution of your existing APIs and to your new APIs without the need to maintain them. This includes adapting to database fixtures in the development environment.

Developer Usability
Traceable can present challenges for developers due to its more complex UI and the manual nature of its testing process. The results may not be as readily actionable, requiring additional time for developers to interpret findings and implement fixes. This can lead to frustration and delays in remediation efforts, reducing overall productivity.
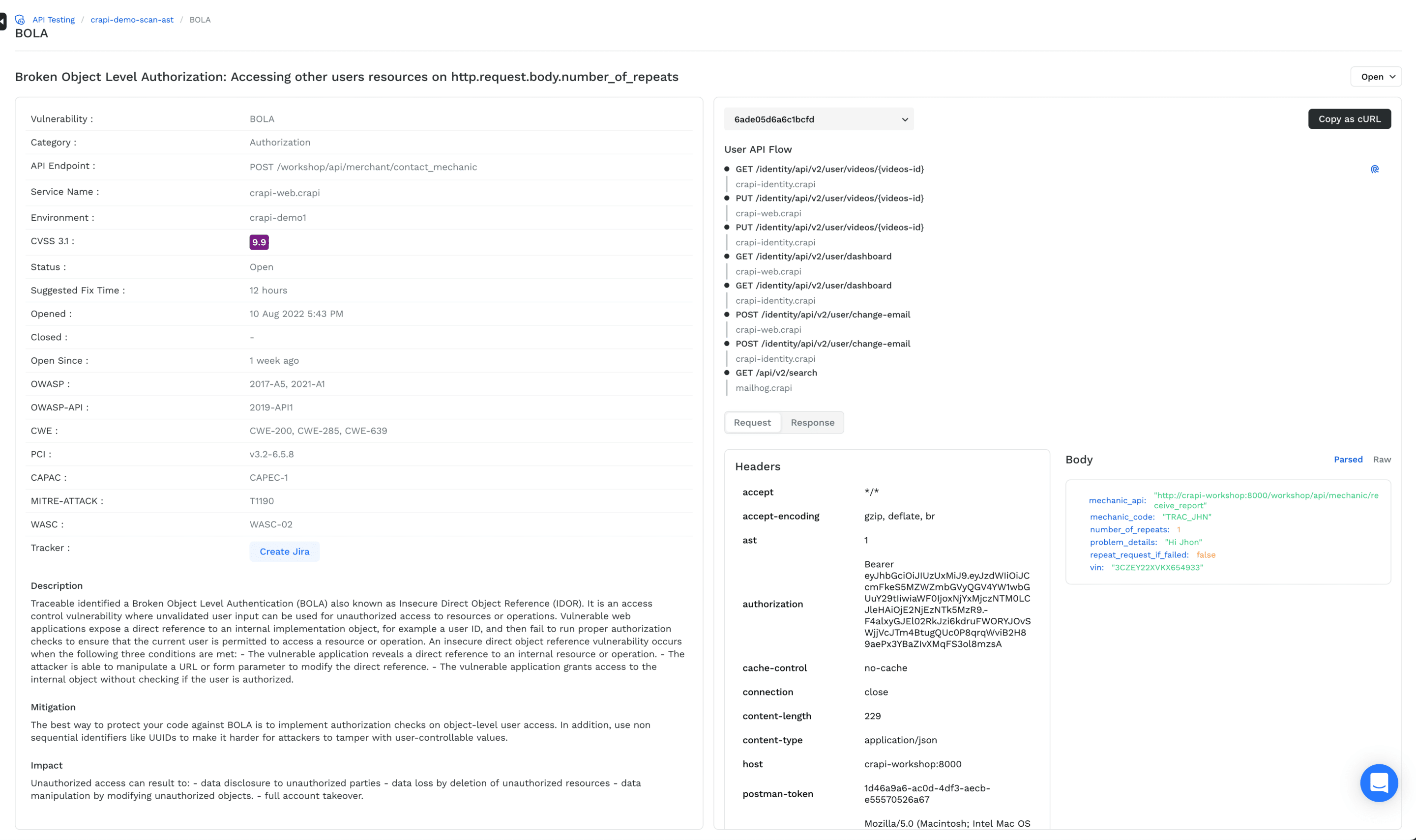
Escape provides clear, actionable insights with detailed code snippets that developers can use directly. This feature speeds up the remediation process and ensures that security issues are addressed promptly and effectively.
Each code snippet can be tailored specifically to your development framework. Don't you think your developers will appreciate more someone who speaks their language?

Escape's intuitive design minimizes the learning curve, enabling teams to integrate security seamlessly into their daily operations.
By providing clear, actionable results, Escape fosters a culture of security within development teams, encouraging them to adopt security practices as a fundamental part of their workflow.
This focus on user experience not only enhances efficiency but also strengthens the organization’s overall security posture compared to solutions that demand more manual intervention and offer less streamlined usability.
When to Choose Escape Over Traceable
Escape is the right choice if:
- You’re looking for a quick, agentless API discovery solution that’s easy to deploy.
- Developer usability is critical for your team, allowing for seamless testing and remediation within development workflows.
- You want to automate your API security scans at scale without requiring manual intervention.
- Your team requires flexible, traffic-independent testing, ensuring all APIs—including those without any traffic—are tested and secure.
- You want complete API inventory without the need for complex network integrations or APM setups.
Conclusion: Escape as a Viable Traceable Alternative
In summary, while Traceable offers advanced detection capabilities through contextual testing, its reliance on traffic and a more manual testing approach can hinder efficiency in agile development environments.
On the other hand, Escape provides a user-friendly interface, requires minimal setup, and lets you automate scans at scale without needing constant manual oversight. This means teams can weave security seamlessly into their development workflows. In short – for businesses prioritizing efficiency and ease of use in their API security efforts, Escape is the way to go.
But don’t just take our word for it—there’s nothing quite like seeing the impact for yourself. Take a moment with our team and see directly during a demo how you can quickly discover all your APIs and automate your security testing at scale.
💡 Want to learn more? Discover the following articles:
- Reinventing API security: Why Escape is better than traditional traffic-based tools
- Escape vs Noname
- Escape vs Cequence
- Escape vs Salt Security
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/top-traceable-api-security-alternative-escape-vs-traceable/
如有侵权请联系:admin#unsafe.sh

