![]()
Permiso today made available three additional tools under an open-source license that make it simpler to secure cloud computing environments.
Daniel Bohannon, principal threat researcher for Permiso, said these tools in addition to seven other open-source tools that the company has made available are part of an effort to create a community focused on improving the ability of cybersecurity teams to defend attack surfaces that continue to increase in size and scope.
The three tools added today include DetentionDodger, which finds identities with leaked credentials and assesses their potential impact. It lists all the identities with a Quarantine Policy and then looks for failed policy attachments of a Quarantine Policy in logs stored in the Amazon Web Services (AWS) CloudTrail service.
DetentionDodger also lists all the inline and attached policies of the user and each group it is part of to determine the impact based on the privileges assigned.
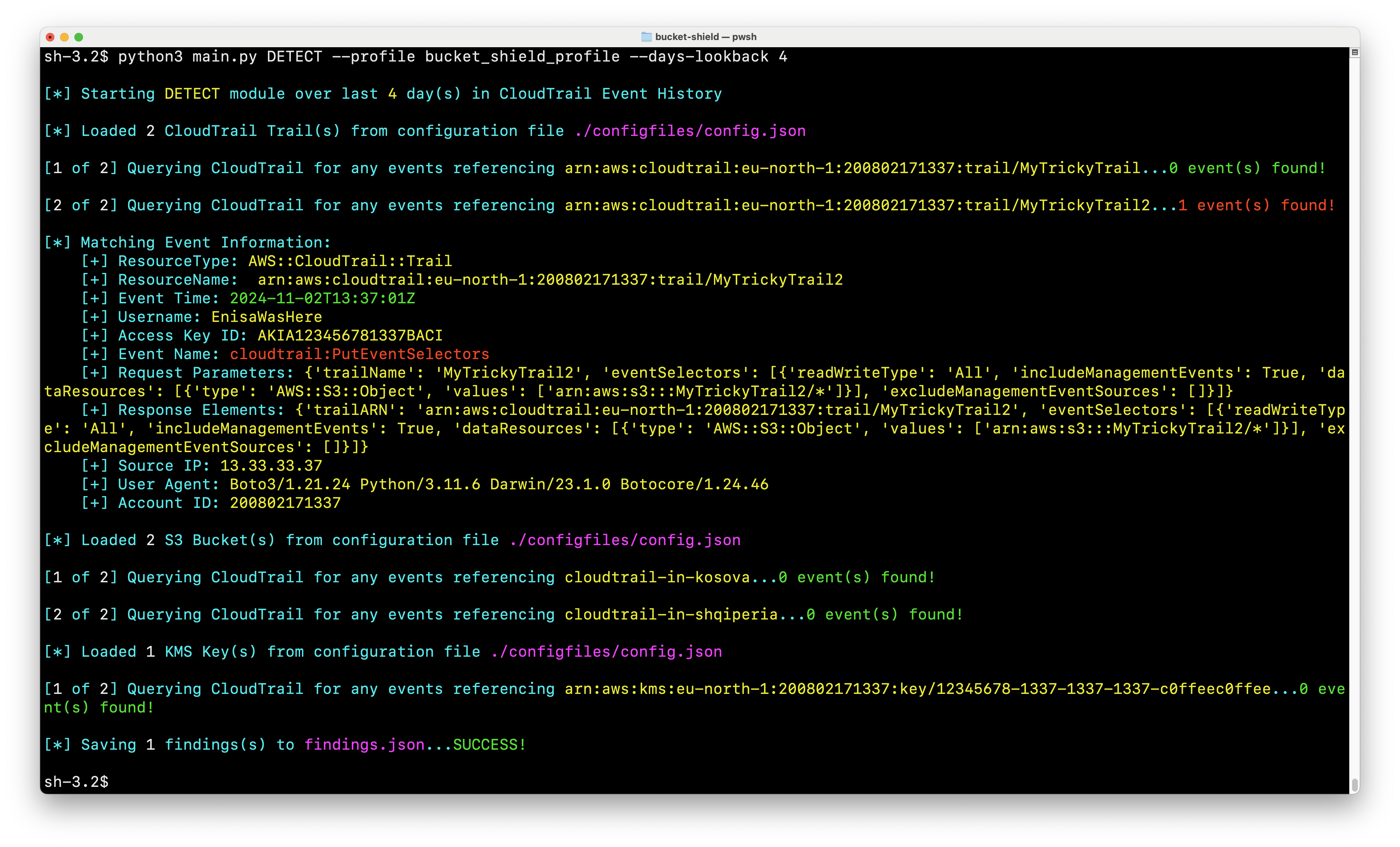
BucketShield is a monitoring and alerting system built for AWS S3 buckets and CloudTrail logs. It ensures the consistent flow of logs from AWS services into S3 buckets and mitigates potential misconfigurations that could interrupt log collection. With real-time tracking of IAM roles, KMS configurations, and S3 log flows, BucketShield ensures that every event is recorded in a way that can be easily audited.
Finally, Cloud API Conversion Helper Express (CAPICHE) Detection Framework enables cybersecurity teams to create different detection rules from groupings of application programming interfaces (APIs).
These tools join a portfolio of open-source tools that include YetiHunter, a tool that detects indicators of compromise in Snowflake environments, and CloudGrappler which queries high-fidelity and single-event detections related to well-known threat actors in cloud environments.
These tools are especially helpful for cybersecurity teams that are trying to secure cloud computing environments that, even after being used for more than ten years, are still challenging to secure, noted Bohannon. Many of these cloud computing environments have been provisioned by application developers with little to no cybersecurity expertise. It’s not practical for cybersecurity teams to review all those cloud instances before they are exposed to the internet, so the next best thing is to take advantage of tools that identify issues that are likely to be problematic as quickly as possible, said Bohannon.
In total, Permiso has now created more than 1,400 detection rules, a subset of which has been incorporated into various open-source tools. It’s not clear to what degree cybersecurity teams are dependent on open source tools but they do help reduce the total cost of cybersecurity. The challenge is some of these tools always wind up in the hands of cybercriminals who will use them for their nefarious purposes.
Overall, however, cybersecurity professionals gain a lot more from these tools even if they are available for anyone to use, noted Bohannon.
Cybersecurity teams these days are, of course. open to getting help from wherever it can be found. The best thing about open-source software, in general, is that in addition to providing free tools, it creates a community that enables cybersecurity professionals to learn from one another.
Recent Articles By Author