
2024-11-8 16:44:56 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Software composition analysis (SCA) is a cybersecurity process that provides an in-depth examination of open-source packages used within an application, identifying and managing components to enhance security and compliance. SCA scans for project dependencies within the code to detect vulnerabilities, outdated libraries, and license compliance issues, enabling developers to address risks effectively. This analysis can also generate a software bill of materials (SBOM), detailing all resources for both internal stakeholders and external customers. By integrating SCA into the software development lifecycle, organizations can maintain software security, ensure legal compliance, and reduce potential risks associated with open-source components.
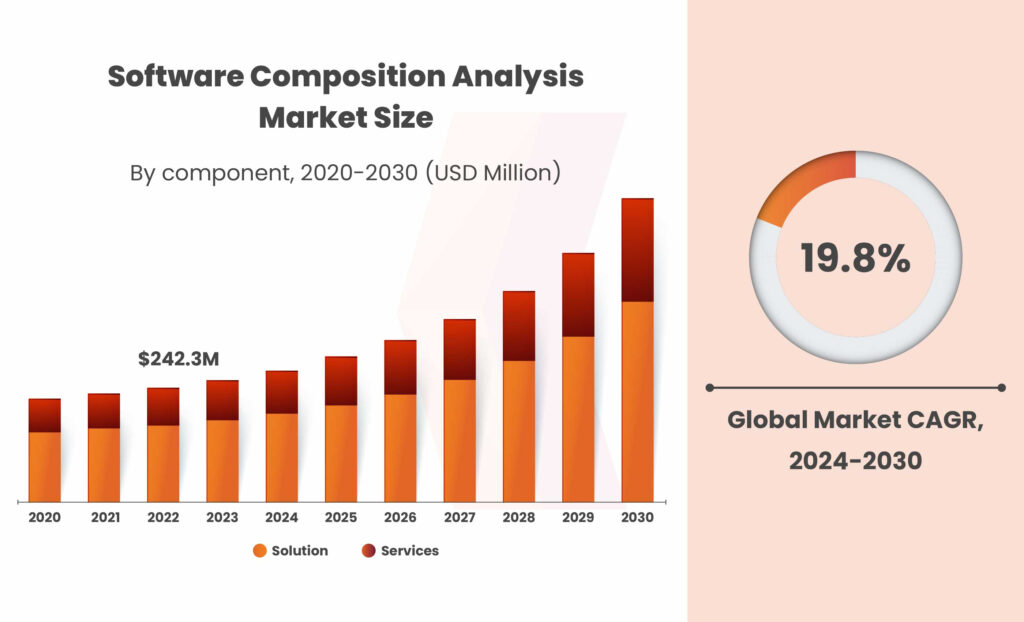
In 2023, the global software composition analysis (SCA) market size was valued at USD 266.2 million and is projected to grow at a CAGR of 19.8% from 2024 to 2030. This market is expanding rapidly due to the rising use of open-source software in modern applications and the increasing need to address security vulnerabilities and licensing compliance. SCA tools enable organizations to identify, monitor, and manage open-source components in their software, ensuring that these components are secure and adhere to licensing standards.
What is Software Composition Analysis?
Software composition analysis (SCA) is an application security approach focused on tracking and assessing open-source software components. SCA tools offer crucial visibility into open-source license limitations and potential vulnerabilities in projects, helping organizations manage essential tasks like security, license compliance, and code quality to reduce risk.
SCA provides three primary functions:
- Generate a software bill of materials (SBOM) to create a comprehensive inventory of open-source software packages.
- Ensure license compliance by identifying the open-source software in use and tracing its origin.
- Detect critical vulnerabilities within source code and provide actionable recommendations for remediation.
Importance of Software Composition Analysis
Open source is essential in modern application development, with up to 94% of today’s code comprising third-party, open-source components. As development teams increasingly create complex, cloud-native applications using open source, prioritizing application security testing is crucial.
With the vast number of third-party components in today’s codebases, manually vetting and securing software applications has become increasingly challenging. SCA solutions address this need by automatically identifying, managing, and helping remediate security risks and compliance issues in open-source components. These tools are essential for developers aiming to build more secure software at a faster pace.
Let’s have a look at why SCA is important:
- Identification of Open Source Vulnerabilities
SCA is crucial as open-source components may contain vulnerabilities and security risks that attackers could exploit. By detecting and mitigating these risks, organizations can enhance the security of their software.
- Precisely Designed to Detect Vulnerabilities
SCA is uniquely designed to detect vulnerabilities and security risks in open-source components, while other security tools, like static analysis and penetration testing, target different areas of software security.
- Risk Mitigation
SCA helps mitigate risks related to security vulnerabilities and licensing issues by offering visibility into the components and libraries used within an application.
Risks of Using Open-Source Components
Before creating container images with open-source components, developers need to be mindful of security risks posed by known vulnerabilities in these packages. They must also ensure compliance with software licensing requirements.
This challenge is intensified by the fact that most vulnerabilities don’t reside in direct or root packages, but in deep-layered dependencies. Securing only the primary packages often leaves additional libraries exposed.
Moreover, managing compliance with open-source licenses can be complex, as there are dozens of licenses with varying obligations. Some require attribution, while others mandate that any application using the component also make its source code public. Keeping track of these diverse license rules is a significant challenge for developers.
Process of Software Composition Analysis
Codebase Scanning and SBOM Generation
The SCA solution scans the codebase and generates a Software Bill of Materials (SBOM) listing all open-source components, including dependencies resolved during the build process.
Component Documenation
It documents key details about the detected components, such as license information, version, and detection location.
Identification Accuracy
The accuracy of this documentation depends on the comprehensiveness of the open-source database used for identification.
Vulnerability Detection
The SCA solution identifies associated open-source security vulnerabilities, including Common Vulnerabilities and Exposures (CVEs).
Alerts and Notifications
It can alert administrators or security stakeholders about detected vulnerabilities or potential license conflicts.
Policy Compliance and Remediation
Advanced SCA tools can compare detected open-source components against defined policies, blocking project promotion into production or notifying stakeholders to speed up remediation.
CI/CD Integration
Many SCA solutions integrate with CI/CD pipelines to automatically scan projects or new versions with each commit.
Book a Free Consultation with our Cyber Security Experts

Future of Software Composition Analysis
The outlook for Software Composition Analysis (SCA) is promising, with the growing reliance on open-source software and the rising demand for secure applications. Key trends and advancements in SCA include:
Cloud Based SCA
As software development becomes increasingly distributed, SCA is likely to transition to the cloud, enabling organizations to leverage scalable, on-demand computing resources.
Continuous SCA
In the future, SCA is expected to evolve into an ongoing process integrated into the software development life cycle, rather than a one-time activity. This will enable organizations to stay proactive against emerging threats and vulnerabilities.
Expansion of Vulnerability Database
As the use of open-source components expands, the size and complexity of the databases managed by SCA tools will grow as well. This will necessitate ongoing investment in database management and security to maintain the accuracy and currency of the data.
Integration with Other Security Tools
SCA is expected to become more integrated with other security tools, such as static analysis, dynamic analysis, and penetration testing, offering a more holistic view of software security.
How Kratikal Can Help you with Software Composition Analysis?
As a CERT-In empanelled auditor, Kratikal offers comprehensive Software Composition Analysis (SCA) services to help organizations manage open-source software risks. By automating the detection of vulnerabilities, license compliance issues, and security flaws, Kratikal ensures that all third-party components in your software are properly monitored. Our approach includes automated scans, integration with CI/CD pipelines, and real-time alerts, allowing for proactive remediation. With Kratikal’s SCA services, organizations can enhance software security, improve quality, and maintain compliance with ease. For more details, visit Kratikal SCA Services.
FAQs
- What does open-source component identification mean in SCA?
Open-source component identification in SCA scans a codebase to detect all open-source libraries and frameworks, creating a detailed inventory with versions and origins. This is essential for managing vulnerabilities, licensing compliance, and legal risks.
- What is vulnerability detection in SCA?
In SCA, vulnerability detection scans open-source components for known security flaws by matching them with vulnerability databases like the NVD. This proactive approach helps developers address risks early, reducing the chances of data breaches and cyberattacks.
- What is software composition analysis used to evaluate?
Software Composition Analysis (SCA) helps identify risks within open-source components used in applications by scanning for known vulnerabilities. This generates insights into security issues in the code, enabling developers to address them before exploitation occurs.
- What is the benefit of SCA?
A key advantage of Software Composition Analysis (SCA) is its ability to not only detect vulnerabilities but also prioritize them according to their severity. The process prioritizes the most critical issues, streamlines remediation, and optimizes resource allocation for enhanced efficiency.
The post What is Software Composition Analysis and It’s Importance? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/what-is-software-composition-analysis-and-its-importance/
如有侵权请联系:admin#unsafe.sh

