
2024-11-12 13:47:25 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
As technology gains popularity, it often attracts more vulnerabilities and becomes a target for cyberattacks. The OWASP Mobile Top 10 is a valuable resource for security researchers and mobile app developers, offering essential data for identifying, evaluating, and addressing security risks specific to mobile applications.
Mobile devices and related tech are expanding rapidly, transitioning from landlines to versatile devices in just a few decades. Their popularity stems from easy accessibility and their integration into sectors like communication, entertainment, finance, and healthcare.
Continuing our discussion on OWASP Mobile Top 10 the next part dives deeper into the 2024 updates. As mobile apps become an integral part of our daily lives, it’s essential to understand the shifting security challenges and how these updates can guide developers and security professionals in mitigating risks effectively. Here, we’ll explore the recent changes, including the latest threat categories, to equip you with actionable insights for strengthening mobile application security.
If you want to know about the new risks in OWASP Mobile Top 10, check out our blog on “OWASP Mobile Top 10 2024: Update Overview”
What is OWASP Mobile Top 10?
The Open Web Application Security Project (OWASP) is a global, open-source initiative focused on improving application security. The OWASP Mobile Top 10 is a list of the ten most common mobile app vulnerabilities, ranked by frequency of occurrence.
The OWASP Mobile Top 10 highlights the most critical security threats faced by mobile applications. Published by the Open Web Application Security Project, this list is the product of global collaboration among security experts, developers, and researchers dedicated to improving app security standards.
In addition to the Top 10 list, OWASP provides two essential resources: the Mobile Application Security Verification Standard (MASVS), which outlines security requirements, and the Mobile Application Security Testing Guide (MASTG), which offers a framework for testing app security. Together, these resources guide developers in building more secure mobile applications.
OWASP Mobile Top 10 Risks 2024
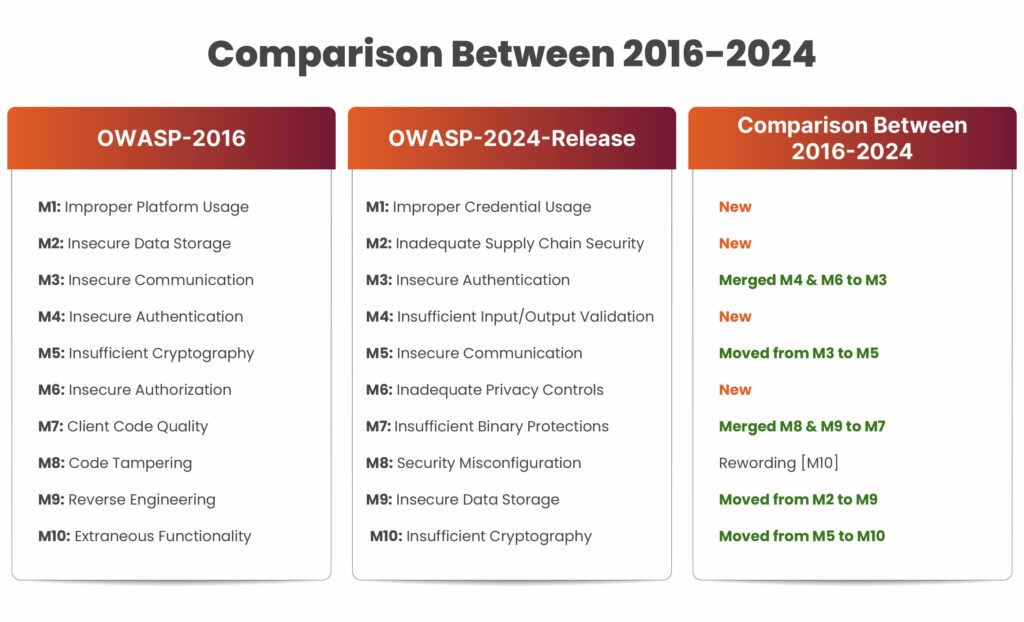
M3: Insecure Authentication/Authorization
Mobile apps face unique security risks in authentication and authorization due to device-specific input limitations, variable internet connections, and improper access controls. Shorter passwords and offline authentication complexity can weaken security, while poor authorization practices may allow unauthorized access to sensitive features. Attackers can exploit these vulnerabilities through techniques like bypassing authentication mechanisms or impersonating legitimate users to perform restricted actions. Addressing these issues requires developers to implement robust authentication and authorization protocols tailored to the mobile environment.
Prevention of Insecure Authentication/Authorization
Below are the preventive measures:
- Avoid Weak Patterns
Ensure mobile app authentication is as secure as web applications by performing it server-side, avoiding local user authentication, and encrypting any necessary client-side data. Use device-specific, revocable tokens instead of storing passwords. Persistent login should be opt-in only, and weak identifiers or PIN codes should be avoided.
- Reinforce Authentication
Developers should assume client-side controls can be bypassed and reinforce all authorization and authentication on the server side. For offline authentication, implement local integrity checks to detect code tampering. Use biometrics, like FaceID and TouchID, to protect sensitive data such as session tokens.
- Insecure Authorization Prevention
Backend systems should independently verify user roles and permissions, as client-side authorization can be bypassed. Reinforce server-side authorization controls and, if offline checks are needed, include local integrity checks to detect unauthorized code changes.
M5: Insecure Communication
Unencrypted or poorly encrypted data transmission puts mobile app users at significant risk, as attackers can intercept communications between the app and servers. This can lead to the leakage of personal information, authentication credentials, financial data, or any other sensitive content transmitted over the network. Even outdated encryption protocols can be easily cracked, making it easier for attackers to manipulate or steal the data.
Prevention of Insecure Communication
Below are the preventive measures:
General Best Practices
To ensure secure data transmission, always apply SSL/TLS to transport channels between mobile apps and backend services, even for third-party integrations. Avoid mixed SSL sessions, use strong cipher suites, and only accept certificates signed by trusted Certificate Authorities (CAs). Never allow bad or unverified certificates, and consider certificate pinning for added security. Verify endpoint server identities before establishing connections, alert users to invalid certificates, and, if possible, encrypt sensitive data separately as an added defense. During development, use trusted certificates and avoid disabling SSL verification.
iOS-Specific Best Practices
The latest version of iOS provides strong SSL cipher negotiation by default. However, issues can arise when developers temporarily add code to bypass these settings during development. To enhance security:
- Ensure certificates are valid and fail safely (closed) if not.
- When using CFNetwork, the Secure Transport API is recommended to designate trusted client certificates, and NSStreamSocketSecurityLevelTLSv1 should be used to ensure high cipher strength.
- After development, confirm that all NSURL calls or wrappers do not permit self-signed or invalid certificates, such as through the NSURL method setAllowsAnyHTTPSCertificate.
- To implement certificate pinning, export your certificate, add it to your app bundle, and anchor it to your trust object. Using NSURL’s connection:willSendRequestForAuthenticationChallenge: method will then accept your certificate only.
Android Specific Practices
- Remove any code after development that enables acceptance of all certificates, like org.apache.http.conn.ssl.AllowAllHostnameVerifier or SSLSocketFactory.ALLOW_ALL_HOSTNAME_VERIFIER, as these effectively trust all certificates.
- If using a class that extends SSLSocketFactory, ensure that the checkServerTrusted method is correctly implemented to validate server certificates.
- Avoid overriding onReceivedSslError to allow invalid SSL certificates.
M7: Insufficient Binary Protection
App binaries are essential to an app’s functionality but are also attractive targets for attackers. These attackers may reverse engineer the binary to extract valuable information, tamper with the code to bypass security features or modify the app to contain malicious code, which can then be distributed under a new name. Such attacks can lead to information leakage, unauthorized access to premium features, or harm to the original app’s reputation if modified versions circulate widely. Sensitive data and critical business logic within the binary make apps particularly vulnerable, especially popular ones, which are more likely to be targeted and redistributed.
Prevention of Insufficient Binary Protection
Each app should undergo a binary content assessment to determine if binary protection is necessary, particularly if it contains critical content or is widely used. Threat modeling can identify high-risk areas and potential financial impacts, leading to implementing appropriate countermeasures.
Reverse Engineering:
To prevent reverse engineering, app binaries should be obfuscated, using free or commercial tools available for this purpose. Compiling parts of apps natively (for iOS and Android) or utilizing interpreters and nested virtual machines further complicates reverse engineering, as many decompiling tools are limited to specific languages and binary formats. This approach balances code complexity with resistance to reverse engineering, though full obfuscation may disrupt libraries that depend on certain strings or symbols. Developers can verify obfuscation quality using tools recommended in the previous section.
Breaking Security mechanisms:
Obfuscation also deters manipulation since attackers need to understand the control flow to bypass security checks. Local security checks should be reinforced by the backend; for instance, protected feature resources should only be accessible if checks pass both locally and on the backend. Additionally, integrity checks can help detect code tampering and potentially disable the app, such as by removing certain resources. However, like other local security checks, integrity checks could still be discovered and disabled by attackers.
Redistribution (with malicious code): Integrity checks, such as those performed at startup, can detect redistribution or modification of app binaries. Any violations could be automatically reported, helping to locate and remove unauthorized copies from app stores before they gain traction. Specialized companies also offer support for handling these cases.
M9: Insecure Data Storage
Insecure data storage in mobile applications poses significant risks as it exposes sensitive information to various threat agents, including hackers, state-sponsored actors, and malicious insiders. Exploitable vulnerabilities such as weak encryption, insufficient data protection, and improper handling of user credentials enable unauthorized access, data breaches, account compromises, and data tampering. These security weaknesses can result in severe technical and business impacts, including reputational damage, loss of customer trust, regulatory penalties, and financial losses. To mitigate these risks, it is essential for app developers to implement strong encryption, secure data storage practices, access controls, and regular security audits.
Prevention of Insecure Data Storage
To secure sensitive data and prevent insecure storage in mobile applications, the following security measures should be adopted:
Use Strong Encryption:
Apply strong encryption techniques to secure sensitive data both at rest and in transit. Use industry-standard encryption algorithms, and ensure that encryption keys are securely stored and managed.
Secure Data Transmission:
Use secure communication protocols (e.g., HTTPS, SSL/TLS) to secure data during transmission between the mobile application and backend servers, and avoid transmitting sensitive data over unsecured channels.
Implement Secure Storage Mechanisms:
Store sensitive data in secure locations that are protected from unauthorized access. Utilize platform-specific secure storage options offered by the mobile operating system, such as Keychain (iOS) or Keystore (Android).
Apply Secure Session Management:
Adopt secure session management practices, including using randomly generated session tokens and setting appropriate session timeouts. Also, make sure to securely store session data on both the client and server sides.
M10: Insufficient Cryptography
Insecure cryptography in mobile applications poses a severe risk to data confidentiality, integrity, and authenticity. Attackers, including cybercriminals, insiders, and state-sponsored actors, exploit vulnerabilities in cryptographic algorithms, weak encryption, poor key management, and flawed implementations to access or manipulate sensitive data. The consequences include data breaches, financial loss, exposure of intellectual property, and non-compliance with regulatory standards, leading to reputational damage and potential legal penalties. Ensuring strong encryption, secure transport protocols, and effective key management, along with regular security audits, is crucial to protect against these threats.
Prevention of Insufficient Cryptography
To avoid “insufficient cryptography” vulnerabilities in mobile applications, implement the following best practices:
Use Strong Encryption Algorithms:
Adopt widely recognized and secure encryption algorithms like AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), or Elliptic Curve Cryptography (ECC). Ensure you stay informed about the latest cryptographic standards and refrain from using outdated or weak algorithms.
Ensure Sufficient Key Length:
Choose encryption keys of sufficient length to maintain robust cryptographic security. Follow industry guidelines for key sizes based on the encryption algorithm you implement.
Implement Encryption Correctly:
Ensure proper implementation of encryption and decryption processes in the mobile application by using trusted cryptographic libraries and frameworks. Refrain from creating custom encryption solutions, as they are more susceptible to errors and security flaws.
Regularly Update Security Measures:
Stay updated on security patches, updates, and recommendations from cryptographic libraries, frameworks, and platform providers. Regularly update the mobile application and its cryptographic components to address any discovered vulnerabilities or weaknesses.
Book a Free Consultation with our Cyber Security Experts

Why it is necessary to Secure Mobile Apps?
Mobile app security is essential, never optional. Apps must be designed to handle sensitive data regularly, whether it’s banking information, health records, or social insurance numbers. A security lapse could result in your data falling into the wrong hands, with far-reaching and severe consequences.
But the risk goes beyond just data theft; it’s also about privacy. An app can’t simply disregard its responsibility for handling sensitive data. Securing your mobile application serves a dual purpose: protecting both your interests and your users. Additionally, strengthening your app’s security can give you a competitive edge in the market.
Conclusion
Securing mobile applications is a critical priority in 2024 as mobile devices continue to play an integral role in daily life. With the increasing sophistication of cyber threats, the OWASP Mobile Top 10 serves as an essential framework for developers to understand and mitigate the most common vulnerabilities that put sensitive data and user privacy at risk. By adopting best practices such as implementing strong encryption, robust authentication mechanisms, and secure data storage methods, developers can protect their apps from attacks and safeguard user trust. In today’s competitive market, securing mobile apps not only prevents severe technical and business impacts but also enhances brand reputation, builds customer confidence, and ensures compliance with regulations. Therefore, mobile app security is not just a necessity but a fundamental aspect of sustainable business success.
Kratikal’s Mobile Application Security Testing service helps businesses ensure their mobile apps are secure against evolving cyber threats. Our comprehensive testing process identifies vulnerabilities, assesses risks, and provides actionable insights to strengthen the security of both iOS and Android applications. By simulating real-world attacks, we ensure your apps are resilient to data breaches, unauthorized access, and other potential threats, allowing you to deliver a safe and trustworthy user experience. Protect your mobile applications with Kratikal’s expert security testing and stay ahead of cyber risks.
FAQs
- Does OWASP apply to mobile apps?
Yes, the OWASP Mobile Application Security Verification Standard (MASVS) is the industry benchmark for mobile app security.
- Do developers use the OWASP Top 10?
The OWASP Top 10 is a widely recognized awareness document for developers and web application security, providing a consensus on the most critical security risks to web applications. It is acknowledged globally by developers as a foundational guide for secure coding practices.
- Is OWASP Top 10 enough?
If you’re new to security, the OWASP Top 10 is a great starting point. It helps you recognize and address some of the most commonly exploited security issues. However, attackers don’t limit themselves to the OWASP Top 10; they may use various methods beyond these vulnerabilities to execute successful attacks.
The post Top Mobile Security Risks of 2024 by OWASP appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/top-mobile-security-risks-of-2024-by-owasp/
如有侵权请联系:admin#unsafe.sh

