
2024-11-14 20:57:57 Author: securityboulevard.com(查看原文) 阅读量:1 收藏

After months of anticipation, the big day finally arrived. The first Elephant in AppSec conference, held on November 7, saw hundreds of listeners tuning in – from security engineers to CISOs – and was filled with invaluable insights into the growing and changing world of application security.
From spicy takes to grilling questions, the conference brought together industry experts to tackle some of the biggest issues facing the AppSec world today: the role of AI, how to create a security-based culture, whether SAST is sufficient and DAST is dead, and so much more.
💡
Missed the conference? Don't worry! Watch the full recordings here.
With 22 speakers, 16 talks, two panels, and two different tracks, there is truly something for everyone to dive into, but here are the key lessons we are taking away from the conference.
You need symbiosis between security teams and software engineers
Just like fungi work together to grow, Akira Brand, Application Security Engineer and DevRel Consultant, highlights the need for security teams and software engineers to partner together in order to support business objectives. Application security teams must speak with software engineers early and often, presenting their systems and highlighting current threats, and equally software engineers must outline their systems and roadmaps to application security teams.
"We rely too much on tooling and don't build proper partnership models" – Akira Brand, AppSec Engineer and DevRel consultant
Aravind Sreenivasa, Manager, Application Security at SeatGeek, drives this home with the idea that security can feel like a roadblock to engineers, so with symbiosis from the start, you can create a culture around security throughout the entire organization and the whole SDLC. Companies need to work top-down to have both preventative measures in place and runbooks ready for when there is an incident, which requires building security into development, leading straight into the next key takeaway.
Streamline security to scale and reduce risk
With a culture of security, these interactions between security teams and developers are crucial for scaling a business so they can work together to tackle new business needs, as Alina Yakubenko, Senior Application Security Engineer at Toast, Inc., mentioned in the panel on the challenges of scaling AppSec.
Security is a "journey of outcomes" and a "philosophy, not a set of principles." – Chris Romeo, CEO and Co-Founder at Devici
Alina and Chris both stress the importance of having secure defaults, to reduce the cognitive load on engineers and also to avoid hardening, so security is already built into the SDLC. Ran Ne'man, VP of Product Management at BeyondTrust (Entitle), later discusses the value of streamlining access controls so that everything isn't funneled into one point. Such collaborative measures across security and development teams to facilitate both development and approval processes will massively optimize operations.
Just having defaults and protocols in place at the start of the SDLC can lull you into a false sense of security. Hence, Tanya Janca, Head of Education & Community at Semgrep, emphasizes a need to shift both left and right. She interestingly discusses how perverse marketing tactics can make it seem like buying a tool is sufficient to shift left, or right, but it actually comes back to creating this culture and organizational structure of security throughout the SDLC (again back to the first point – it's all about relationships in security).
As Tanya touches on, just deploying tools is insufficient. So what may seem like the "best" or most-used tools may not actually be the best for your business, as Aravind also mentioned, and you need to look at what the right tools are for where your business is currently at.
"Optimize not for finding more vulnerabilities but for fixing more" – Jeevan Singh, Director of Security Engineering at Rippling

Jeevan emphasizes in his talk that, instead of just optimizing for short-term solutions, businesses have to use tooling data to map out a long-term strategy so that tools are fully integrated into the ecosystem. This naturally goes hand-in-hand with building a top-down company culture around security, delineating which teams handle which vulnerabilities and how. It is this results-oriented approach that will ultimately scale a business in a secure way.
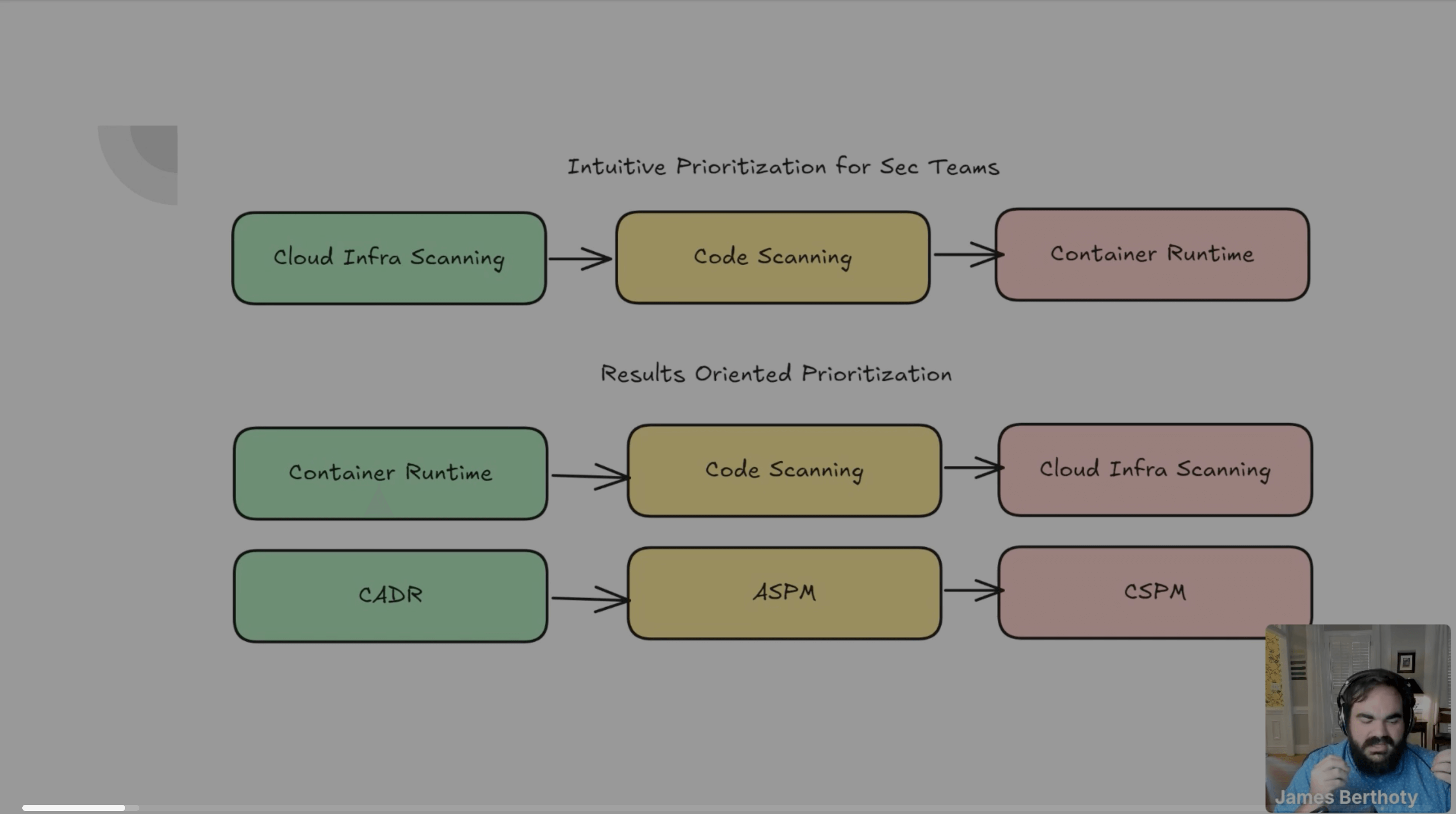
James Berthoty, Founder of Latio Tech, advises on combining various tools with a focus on results-driven prioritization. Companies with cloud-native architectures should drop tools like CNAPP altogether and adopt a CADR + ASPM approach (with the exception of DAST, which remains a gap in most of these platforms because it is hard to build and doesn’t fit natively into the idea of “infrastructure scanning”). However, he emphasizes starting with container runtime security, as this foundational layer often hosts most cloud infrastructure. "For containers, CADR runtime scanning should be the starting point of your cloud security program because it offers immediate value," says James.
When it comes to API security, runtime protection tools come with many pros but also cons like high false positive rates or complicated deployment, as Tristan Kalos, Co-Founder and CEO of Escape, discusses.
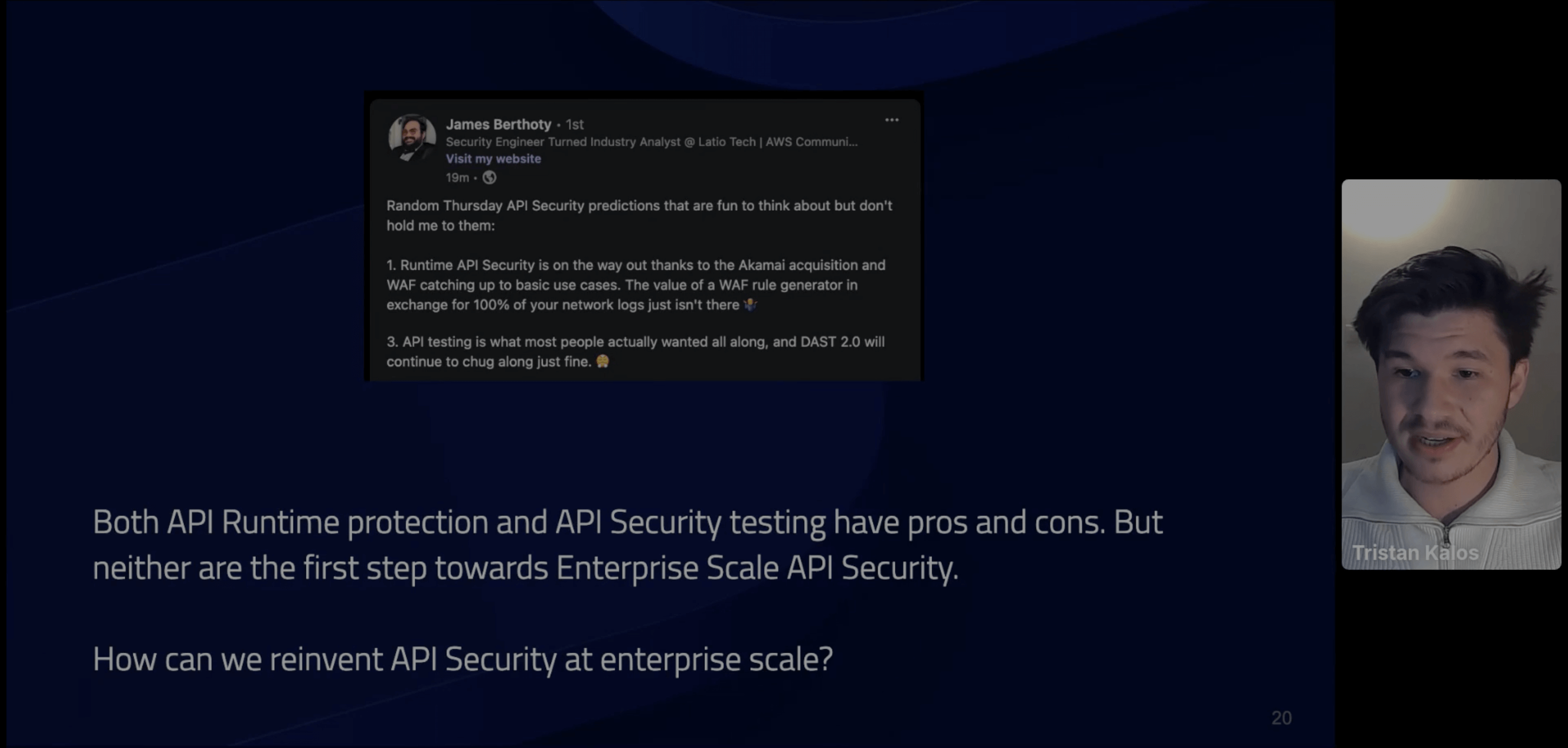
He explores how feedback-driven API exploration algorithms, such as Escape's, are able to subvert these challenges and both statically and dynamically analyze APIs and endpoints, implementing API security agentlessly and optimally at scale.
Harness AI to optimize business logic testing
Is static testing sufficient? Is DAST actually dead? Many of our speakers explored the importance of both static and dynamic testing working in conjunction, but the final key headline of the conference was the power of AI in optimizing both Static and Dynamic Application Security Testing, specifically in next-generation tools, as Munawar Hafiz, CEO at OpenRefactory, explores.
Combining Large Language Models (LLMs) with static testing can increase accuracy through the LLMs ability to pattern spot, which Anmol Agarwal, Senior Security Researcher at Nokia, delves into in her talk. However, this use of AI can crucially apply business logic to testing, both static and dynamic, which is fully investigated in the panel on AI in cybersecurity.
"[Using AI to understand business logic] changes how we think of static testing" – Amit Bismut, Head of Product at Backslash Security

So, as Swan Beaujard, Security Software Engineer at Escape, highlights in his talk, it is not that DAST is dead, but that classic DASTs are dead; by using generative AI you can exploit vulnerabilities and adapt solutions to your specific business and users' needs.
Yet with over a quarter of Google's code being generated by AI, it could also seem like AI leads to security taking a backseat. But it comes full circle back to creating that security culture, with development and security teams collaboratively creating frameworks that ensure that LLM-generated code remains secure.
In summary:
- Security needs to be built into the company culture so security practices are present throughout the entire SDLC
- This helps businesses to optimize, scale, and reduce risk
- Solutions should be carefully selected to suit the business' needs
- AI can be harnessed to pinpoint and optimize solutions for these specific needs
Make sure to go back and watch the recordings to get an in-depth insight into all of these takeaways as well as so many more crucial learnings on all things application security. A huge thank you to all of our speakers, as well as to everyone who attended!
💡 Want to discover more?
- Discover the Elephant in AppSec Podcast on YouTube, Spotify and Apple Podcasts
- A Future of Security Free from CNAPP – Keynote Interview from James Berthoty
- Application Security Podcasts To Know
- Why 'Shift Left' Isn't Good Enough? Our conversation with Chris Romeo
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Sanjana Iyer. Read the original post at: https://escape.tech/blog/the-elephant-in-appsec-conference-4-key-takeaways/
如有侵权请联系:admin#unsafe.sh

