
2024-11-19 14:12:40 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
In 1989, the first ransomware attack was recorded. It was the foundational ground that laid the wave of digital invasions that the world has been witnessing with an attack occuring every two seconds. From the monetary aspect, a 30% increase in damage is seen every year. The amount is expected to cross $265 billion by 2031 annually. In 2007, a more advanced attack was recorded. It locked the entire operational route and demanded ransom for access. Encryption of files started in 2013, with the rise of CryptoLocker.
By 2018 and 2019, the frequency of such attacks grew exponentially followed by the adoption of double extortion tactics. 2021 witnessed a rise in high-profile attacks around the globe. Toward the end of 2024, ransomware attacks have become more advanced with RansomOps making the attack almost impossible to detect. This blog explains the intricacies of ransomware along with measures that can prevent it from infesting your organization.
How Far Has Ransomware Come?
The evolution of ransomware showcases the increasing complexity of the attacks. Moreover, the world is not in a position to affirm that such attacks are going to stop. Securing your organization is the most crucial step followed by helping your partner organizations. The right acts begin with the right information. Here are a few of the most intense and highly utilized Ransomware TTPs.
Book a Free Consultation with our Cyber Security Experts

Triple and Quadruple Extortion
A single extortion attack is a traditional approach where hackers hack the organization’s assets with ransomware, encrypt the files, and then demand a ransom. In a double extortion attack, hackers steal the file before encryption and threaten to release it if ransom is not paid. When ransomware attackers launch other service disruption attacks like DDoS to add more pressure while threatening to release stolen data, it is known as Triple Extortion. A more sophisticated version is Quadruple Extortion, where attackers not only exert pressure on the organization but also attack its business partners and suppliers to get the ransom demanded.
The extortion tactics used by the ransomware actors include DDoS Extortion, threatening to release the organization’s name resulting in lower stock prices, and constantly attacking the organization’s critical infrastructure.
Targeted Attacks and Supply Chain Compromises
Targeted ransomware attacks are more planned and focused than regular ransomware. Instead of randomly sending out malware, targeted attackers specifically target organizations they believe can afford to pay a large ransom. They often take months to plan and start by stealing login details to get into the network through tools like Virtual Private Networks (VPNs) or Remote Desktop Protocol (RDP). Unlike mass ransomware attacks, where attackers wait for victims to fall into their trap, targeted attackers are actively involved throughout the process, carefully choosing and planning their attack. One common way they gain access is through unsecured RDP connections, which companies need to secure to avoid these attacks.
Supply chain attacks focus on exploiting weak security in suppliers to get to larger organizations they work with. Attacks on the software supply chain have risen because modern software is built using various external parts, like third-party code, open-source software, and APIs from other companies. If any of these components are insecure, it can open the door for attackers. Hardware supply chain attacks target physical devices, like computer parts, and use them to infiltrate systems. Treat actors target Managed Service Providers (MSPs), which have deep access, and then spread the attack to all its customers. Another approach adopted is attacking the CI/CD pipeline, which is a system used to develop and deliver software automatically. If attackers can get into this pipeline, they can add malicious code to software updates.
Refined Evasion Approaches
Ransomware threat actors are constantly developing their tactics, techniques, and procedures (TTPs) making it more challenging to detect. The new evasion techniques to sidestep security solutions have been highly effective leading to increased frequency of ransomware attacks. Some of them are:
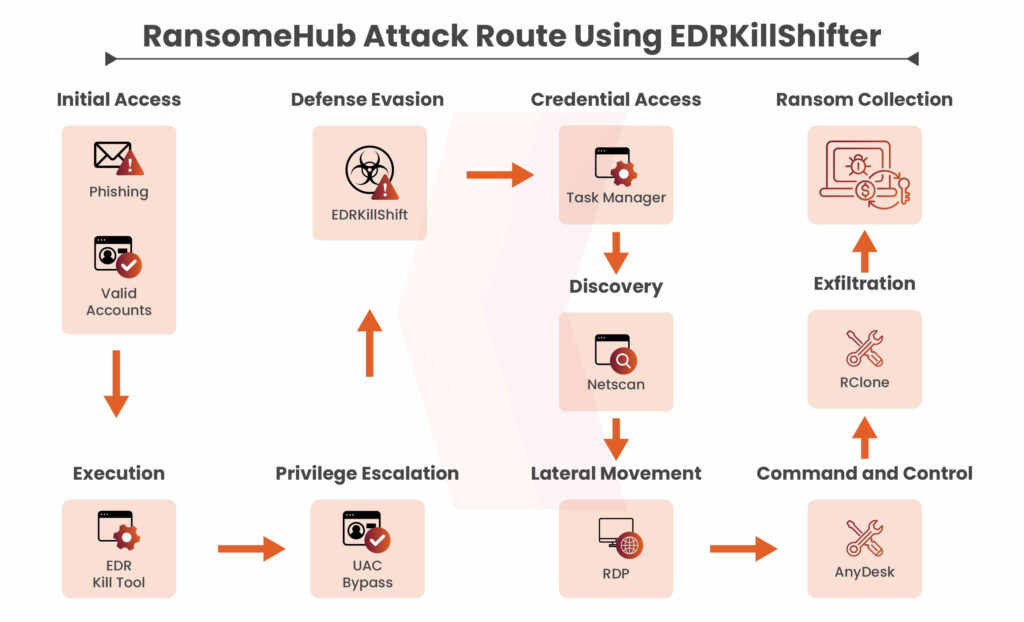
- EDRKillShifter, a new tool adopted by hackers to disable endpoint detection and response (EDR) and continue infecting it even after the organization identifies and patches the initial compromise. The image below shows how EDRKillShifter works.
- Brute force, password-spraying, and public-facing application exploitation are some of the techniques used by ransomware actors to gain initial access.
- Exploiting command and scripting interpreters, like PowerShell, using living off the land (LotL) leveraging tools are steps adopted by threat actors during the execution stage.
- To make themselves undetectable, threat actors clear the Windows Event Logs. This technique gives them more time to exfiltrate data as well as extract a ransom.
- Threat actors gain credential access through Local Security Authority Subsystem Service Memory (LSASS Memory), open-source applications, etc.
- They use lateral movement techniques to move from one place to another within the network and corrupt endpoints.
- Ingress Tool Transfer using a C2 server helps fast download and delivery of all those tools necessary to launch the attack by ransomware actors.
- Exfiltration over web service is the technique used by hackers to steal data and store them privately.
Ransomware-as-a-Service (RaaS) Platforms
Ransomware-as-a-Service (RaaS) is similar to a conventional business model. Ransomware developers, known as RaaS operators or RaaS groups, sell malware, ransomware code, tools, etc to hackers called RaaS affiliates. The information about the same is updated on the dark web. The tools and infrastructure that are sold by developers are called RaaS Kits. Through this service, the crimes are carried out in a more sophisticated way that results in mutual benefit for both the hackers and developers. The profit comes from extortion without developing malware for the hackers and the developers profit by developing the kits without launching the attack.
Challenges for Organizations:
- The threat actors developing malware and launching attacks are different individuals or groups.
- The same malware is used by different hacking groups making identification difficult.
- Since hackers and developers are responsible for a particular segment of work; it provides them with more time to make the techniques highly effective.
- Apart from hackers and developers, there are a group of hackers called “access brokers”. They are responsible for gaining access to networks and selling entry points to attackers.
Increased Use of Cryptocurrencies
Cryptocurrency in ransomware attacks has risen over the years for two major reasons – it is harder to track and is effective. Since cryptocurrency transactions don’t require middlemen; victims and attackers can send money directly to each other without bypassing traditional financial systems, like banks. With the launch of new, affordable cryptocurrencies, attackers can quickly convert stolen funds and move them across borders. Blockchain records are public, therefore, identities behind the transactions remain anonymous, making it difficult to track the hackers down.
Further, additional measures taken by Ransomware agents include:
- Cryptocurrency Mixing: It means mixing the ransom received with those cryptos obtained from legal transactions.
- Use Stolen Accounts: Threat actors steal the credentials of legitimate account holders and use the accounts.
- Chain Hopping Method: This refers to exchanging funds from one cryptocurrency to another. Especially, a cryptocurrency that protects user identity and is anonymous is used.
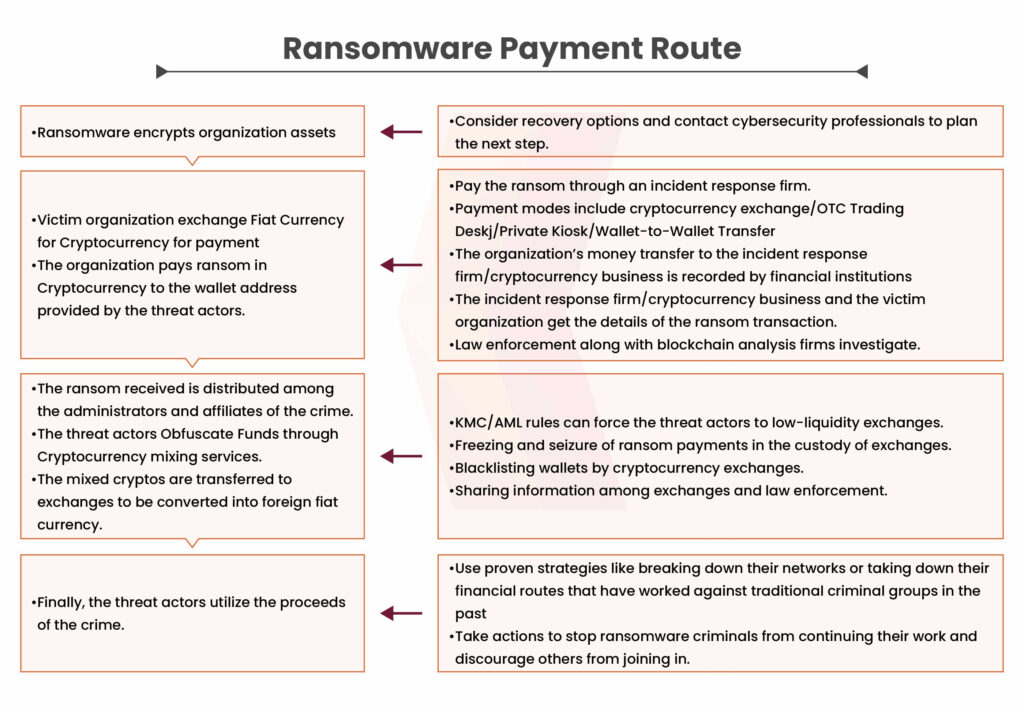
Below is an explanation of the ransomware payment process and the potential points of intervention during an attack:
Should Organizations Pay a Ransom or Refuse to Pay?
It is important to consider the following factors prior to making a decision:
- Organization’s Data Backup Solution
- Organization’s Cyber Insurance Coverage
- Ransomware Downtime – Financial Impact
- Data Exposure Risk Level
- Legal Regulations
How Can Organizations Counter Ransomware with Kratikal?
- Enhance Endpoint Security: Ransomware can be prevented by regular VAPT audit to detect threats and implement robust endpoint protection solutions.
- Network Security: Through Network Penetration Testing, organizations can strengthen their intrusion detection systems and firewalls as well as secure remote access solutions. They can incorporate the recommendations provided by Kratikal to strengthen their network security posture.
- Data Protection and Backup: VMDR tools like AutoSecT constantly monitor organization assets for vulnerabilities thus recommending organizations to backup critical data and analyze the restoration ways during an attack.
- Incident Response Planning: Organizations can develop a comprehensive incident response plan with the help of cybersecurity experts to reduce the impact of a ransomware attack.
FAQs
- What is the difference between cyber extortion and ransomware?
In simple terms, ransomware is a form of cyber extortion. It uses malicious software to encrypt files and ask for ransom against its decryption. With ransomware attacks evolving, hackers have been using multi-extortion TTPs to procure the ransom.
- What is the sequence of events of ransomware?
The most common sequence of events in a ransomware attack includes acquiring initial access, running malicious software, gaining higher-level access, hiding its presence, gaining credential access, looking for important files and spreading throughout the network, remotely controlling the system, stealing data, and finally demanding a ransom.
- What is the root cause of ransomware attacks?
The most common cause of ransomware attacks starts with limited knowledge increasing the chances of clicking on phishing emails. Other causes include improper IAM controls, unsecured organization assets, unpatched vulnerabilities etc.
- What is the first action of ransomware?
Quick response and communication are the first actions in case of a ransomware attack. In the first 48 hours, the focus should be on controlling the damage followed by checking the backups within six hours of the attack. Organizations within 24 to 48 hours of the attack should also focus on removing the malware and restoring the primary operations.
The post Ransomware Evolution: From Triple-Quadruple Extortion to RaaS appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Puja Saikia. Read the original post at: https://kratikal.com/blog/ransomware-evolution-from-triple-quadruple-extortion-to-raas/
如有侵权请联系:admin#unsafe.sh