
2021-02-07 02:13:11 Author: medium.com(查看原文) 阅读量:335 收藏

TCS HackQuest Season 5 is an ongoing CTF competition conducted by TCS Company from 23 January 2021.
This competition is related to cyber-security and its importance in today’s online world.
I participated in this and this was my first time in such a large CTF competition conducted, I got used to doing some CTFs, pentesting, and vulnerability research in 2020, all thanks to the lockdown, on HackTheBox.eu and TryHackMe.
So, as the results were out yesterday, I will share my thoughts and the approach I followed to find those flags in Round 1, as it might help someone!
I got just 4 challenges (3 minor, 1 major) which summed up to 700 points.
Challenge No 1: I am Always…
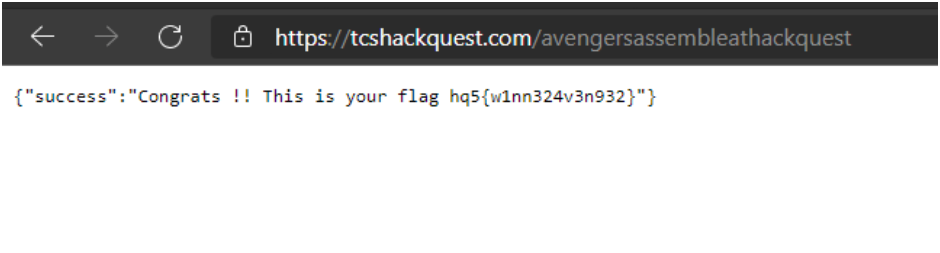
Flag: hq5{w1nn324v3n932}
Points: 100
Description: Relating the anger issues of hulk with the hidden flag.
Solution/Approach :
- As we all know, Hulk is the strongest avenger, it immediately made sense to go with his image details, also I compared him to other avengers to double-check.
2. I EXIF-ed the data from it and found that it had some file location (directory/path).
3. Then I just entered the main domain followed by the path I received in the directory url format. (tcshackquest.com/avengersassembleathackquest)
4. And then finally, I found the main flag required.
Challenge No 2 : DigiMagic (This challenge was removed after sometime)
Flag: hq5{s0_Y0u_KN0WHoW$$1_worKs}
Points: 100
Description: The hint was in the challenge title itself : Digital Certificates are a thing.
Solution/Approach :
1. In this, I noticed that in the description it said digital certificates are necessary and it immediately clicked that there might be something to do with the digital certificate itself.
2. Then by doing a NIKTO scan, I got details and followed the remote IP, it was something like 62.XX…. and by default it was using HTTP (insecure) protocol and it showed me a hint.
3. Then I studied the certificate and found a base 64 string hidden in the ISSUER section along with other details as follows :
4. Finally, I decoded the base64 string and got the required flag, as follows :
Challenge No 3 : Reggie Rich
Flag: hq5{3nc2yp7*m45732}
Points: 100
Description: Matching PHP string using preg_match().
Solution/Approach :
1. In this, I noticed that in the source code, by using inspect element it said it used a specific pattern using the php preg_match() function.
2. So I used, first the initial string in a prefix manner, then the original string, and string in the suffix manner, like we get hackhackquestchampquestchamp as the magical string by referring to the below function.
3. So, here we can say that Pattern1 was hack then Pattern2 was the original string and atlast Pattern3 was questchamp .
4. Finally, after using the magical string, I got the flag as follows :
Challenge No 4 : Pandemic Inhibitor
Flag: hq5{HopeWeReturnToTheOldNormal}
Points: 400 (The only major challenge I got at that time)
Description: Vaccine manufacturers and POST requests were the only clues I got after reading it.
Solution/Approach :
1. In this, I got that we need to forward an API request externally, so I used postman for it as I had basic knowledge of it.
2. I used the parameters given in tcshackquest portal, the main directory of API parameters by locating to it. (below is the directory snippet)
3. Then I realized that I need to pass several parameters, like a SQL injection pattern.
4. Then, I used the earlier cookie, which we used for main login (for hackquest portal) as follows :
5. Finally, after the Covaxin value I got my flag and it showed me a doubtful warning when I used Pfizer vaccine as the value like (will it really cure it?) #atmanirbharbharat
如有侵权请联系:admin#unsafe.sh