2022-2-10 16:55:56 Author: blog.elcomsoft.com(查看原文) 阅读量:65 收藏
The fifth beta of iOS Forensic Toolkit 8 for Mac introduces forensically sound, checkm8-based extraction of Apple Watch Series 3. How to connect the watch to the computer, what data is available and how to apply the exploit? Check out this comprehensive guide!
The USB adapter
There are several types of Apple Watch adapters on the market that can be easily sourced from multiple vendors. Some of these are shown on the picture below:
For the purpose of this guide, we used the S-Dock adapter shown on the bottom left of the image.
You are welcome to read about the different adapters in Apple Watch Forensics: The Adapters. Note that you need an adapter compatible with the Series 3 watch. This is how the watch looks when docked in the adapter:
Compatibility
This guide is applicable to the Apple Watch Series 3 devices running any version of watchOS.
Before you begin
Checkm8 is a complex exploit with several pre-requisites. Make sure you have everything handy before you begin.
- A Mac computer. You will need a Mac to install the exploit and perform the extraction. We support both Intel and M1-based Macs with a universal build of iOS Forensic Toolkit. At this time, Windows is not supported.
- iOS Forensic Toolkit 8.0 beta for Mac. You will require the Mac edition of the tool. Apple Watch 3 support has appeared in the fifth beta of the tool.
- Apple Watch Series 3. The watch must be functional enough to be placed into DFU mode.
- Apple Watch passcode must be known or empty. Otherwise, limited BFU extraction may be available, but very little information can be obtained this way.
- A compatible USB adapter to connect the watch to the computer.
- You must be able to download the official Apple firmware (download link will be provided during the extraction) that matches watchOS version installed on the device.
Note that, while Apple had partially patched the vulnerability in iOS 14 and 15, watchOS 7 and 8, which are based on those versions of iOS, did not receive the same treatment. As a result, you will not have to remove the watch screen lock passcode in order to apply the exploit. We are not quite sure what’s going on here, but it does appear the patch was simply forgotten.
Analyzing the data
We have a separate article on analyzing Apple Watch data. In addition, please refer to the following two articles written by Mattia Epiphany for the more detailed analysis of Apple Watch and Apple TV devices.
Installing iOS Forensic Toolkit 8.0
Please refer to checkm8 Extraction of iPhone 8, 8 Plus and iPhone X for detailed installation instructions. The only difference will be the folder name; EIFT8B5 instead of EIFT8B4. Please note that there are two different images for Intel and M1-based Macs.
Command line parameters
Once again, refer to checkm8 Extraction of iPhone 8, 8 Plus and iPhone X to understand the basic command line parameters of iOS Forensic Toolkit. We’ll use those commands in the subsequent step-by-step manual.
Apple Watch 3 checkm8 extraction walkthrough
When extracting the Apple Watch, follow these steps:
- Launch iOS Forensic Toolkit 8.0
- Connect the Apple Watch 3 to the computer via a USB adapter (in a powered-off state)
- Place the Watch into DFU
- Run ./EIFT_cmd boot
- Run ./EIFT_cmd unlockdata -s (enter passcode when prompted, or ENTER if you don’t know the passcode)
- Run ./EIFT_cmd ramdisk keychain -o {filename} to extract the keychain
- Run ./EIFT_cmd ramdisk tar -o {filename} to extract the file system
- Run ./EIFT_cmd ssh halt to power off the Apple Watch
Apple Watch 3 checkm8 extraction step by step
Launch iOS Forensic Toolkit, then connect the Apple Watch to the computer by using a commercially available adapter. At this time, the watch must be powered down.
Then, place the watch into DFU:
Press and hold both the Digital Crown and the Side button for ten seconds, then release the Side button while still holding the Digital Crown for 10 more seconds.
There will be no indication on the watch; the display should remain black. If you see an Apple logo, the timings were wrong, and you’ll have to repeat the procedure.
Once the watch is in DFU mode, execute the following command in iOS Forensic Toolkit:
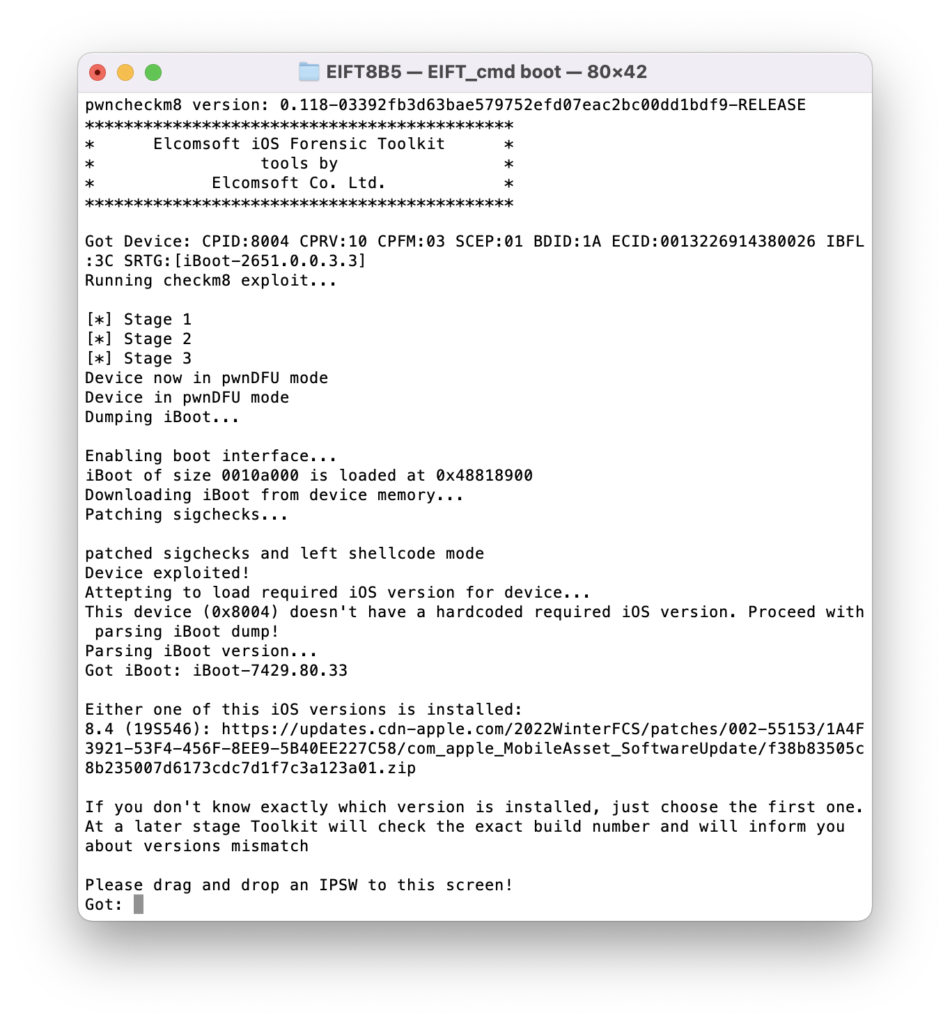
./EIFT_cmd boot
The command launches the exploit. The code detects the OS version installed on the watch, and provides a download link. If there are multiple potential matches, several download links will be displayed; we recommend taking the last link from the list. Download the file from the link, and drop it onto the console window, then press ENTER.
The watch screen will display the “Booting” message.
Our extraction solution does not use the operating system installed on the Apple Watch to boot the device. Instead, a copy of the original Apple firmware is patched on-the-fly and then is booted in the device RAM. This process requires you to have a copy of the original Apple firmware image that matches the device’s watchOS version and build number exactly.
In many cases, the watchOS version will be detected automatically by EIFT during the first stage of the exploit. The detection is based on the detected iBoot version and device hardware. However, in some cases the iBoot version may correspond to several OS builds. If the wrong build is used, you will have an option to either repeat the process with a different version of firmware, or continue with the current firmware image (which works in many cases).
If the process was successful, you will see a confirmation.
The Watch will display the following screen:
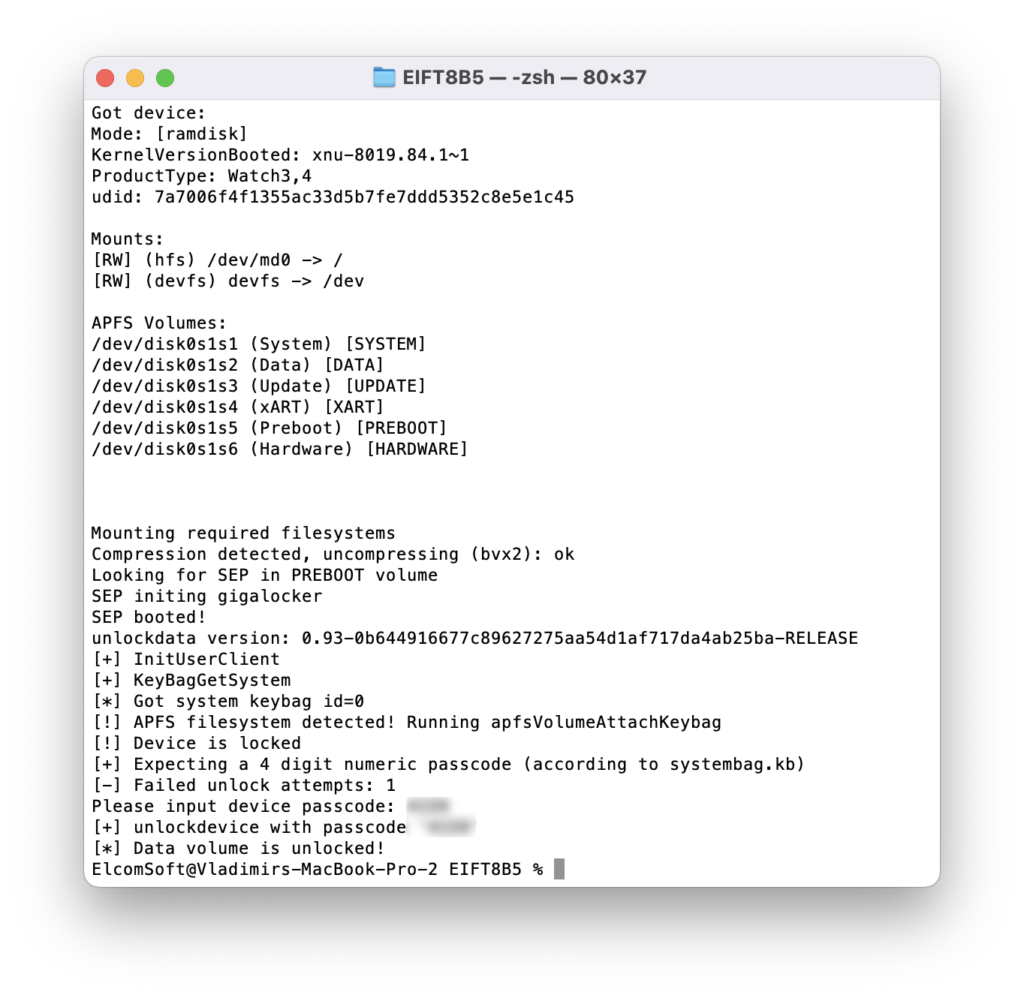
./EIFT_cmd ramdisk unlockdata -s
This command unlocks the data partition and mounts it read-only. You may be prompted for the passcode; enter the passcode if you know it, or press ENTER to skip (limited DFU extraction will be performed in that case).
If you enter the wrong passcode, an error will be displayed. With correct passcode, the volume is fully unlocked and you can proceed with data (keychain and file system) extraction). If you don’t know the passcode, press ENTER on the screen below. In this case, a very limited BFU extraction will be performed.
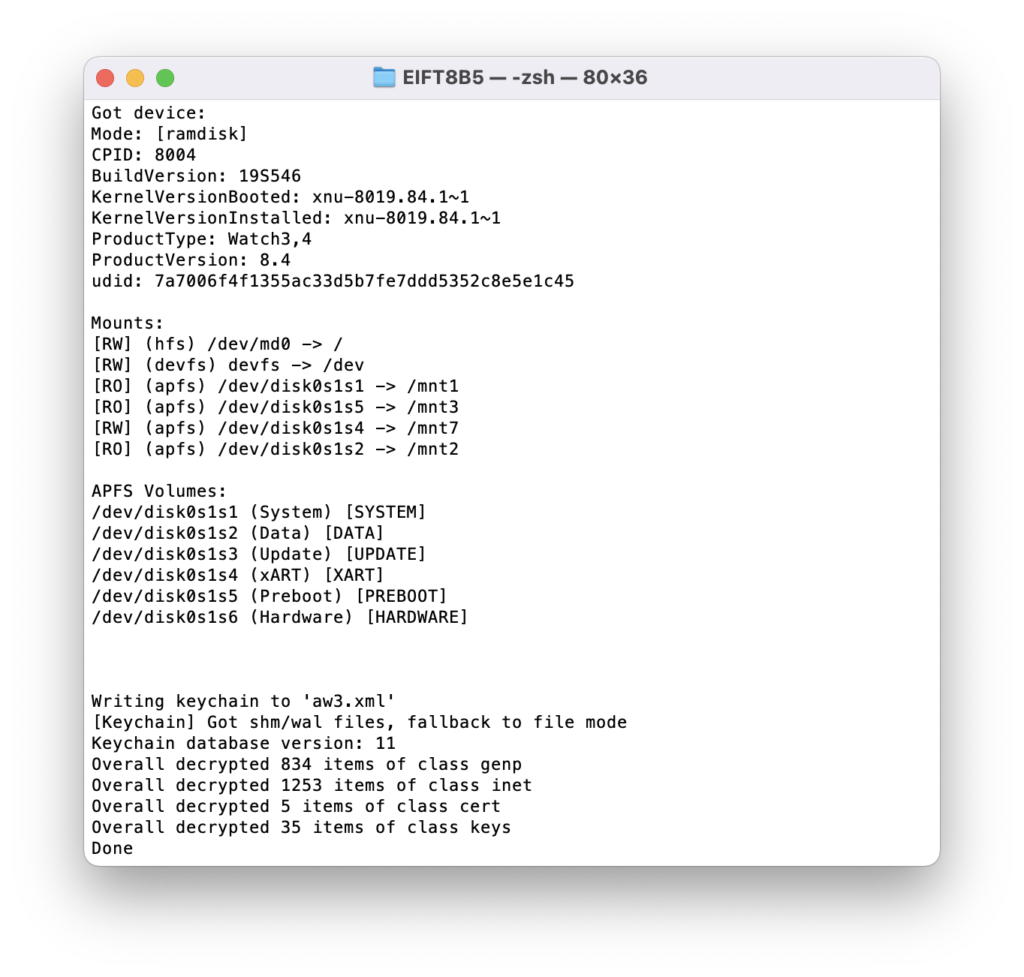
./EIFT_cmd ramdisk keychain -o {filename}
This command extracts and decrypts the keychain. If no path is specified, it will be saved into the current folder.
./EIFT_cmd ramdisk tar -o {filename}
This command images file system. The checksum (hash value) is calculated on the fly and displayed once the extraction is finished.
The SoC and USB controller in the Apple Watch are significantly slower than the phone version, which results in comparatively slow extraction speeds of approximately 3 MB/s.
BFU extraction
If you do not know the screen lock passcode, just press ENTER when prompted. Despite “Device is not unlockable” error, you will be still able to perform a limited BFU (Before First Unlock) extraction.
Analyzing the data
After extracting the data, load the file system image and a copy of the keychain in the forensic tool of your choice. For the time being, few if any third-party forensic tools have been optimized to support watch-specific data sets. We are updating Elcomsoft Phone Viewer to recognize the specific data types. In this article, we demonstrate some of the types of data extracted from the Apple Watch.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh