2022-2-15 01:24:50 Author: www.sentinelone.com(查看原文) 阅读量:26 收藏
Historically, most corporate applications and solutions that store corporate data were protected behind the corporate network. The adoption of cloud applications and the mobile workforce has changed this paradigm dramatically. Whereas once it would have been unthinkable to allow employees to access applications outside of the corporate network, today such applications are accessible virtually anywhere thanks to cloud-native solutions. For this reason, the old perimeter that security professionals would set and protect no longer exists, and perimeter-based security models are obsolete.

Pandemic-Enabled Digital Transformation
The COVID-19 pandemic has accelerated digital transformation efforts for organizations that need to rapidly stand up infrastructure to support an instant remote and later hybrid workforce. IT teams deployed new solutions to enable business continuity, including cloud infrastructure and Software-as-a-Service (SaaS) platforms like Zoom and Office 365.
Organizations adopted solutions that could scale and deploy without needing access to the physical data center, in some cases deploying applications that were exposed to the open internet. In parallel, many organizations needed to provide endpoints for new remote employees and roll out bring your device (BYOD) programs. In reality, securing these new operating environments was a secondary concern.
These radical shifts resulted in users accessing applications and data outside of the traditional corporate network. While some organizations tried to scale their on-premises infrastructure to cope, creating a new perimeter around the new compute-where-you-are environment with legacy tooling requires too much effort and is prohibitively expensive.
The modern organization’s attack surfaces now encompass the cloud, containers, mobile devices, IoT, and storage. As attack vectors multiply, many enterprises address each vector with a best-in-class solution to protect those specific vulnerabilities. However, these point tools don’t connect the dots across the entire technology stack. As a result, security data is collected, analyzed, and investigated in isolation, creating gaps in what security teams can see and detect.
In addition, as the number of deployed security solutions grows in the enterprise, the capacity to manage them and effectively respond to their alerts also grows. Administrators can quickly become overwhelmed by the entirety of data produced from multiple systems and a consistent stream of security alerts. All of this results in long adversary dwell times, potentially causing material damage to an organization.
Security teams need a new way of working, one that enables productivity for end-users and security for the organization—one that provides frictionless protection from endpoint to network to application.
XDR and Zero Trust as Frameworks for Improving Security for Remote Workers
XDR is the evolution of EDR, Endpoint Detection, and Response. While EDR collects and correlates activities across multiple endpoints, XDR broadens the scope of detection beyond endpoints to provide detection, analytics, and response across endpoints, networks, servers, cloud workloads, SIEM, and more.
XDR automatically collects and correlates data across multiple security vectors, facilitating faster threat detection so that security analysts can respond quickly before the scope of the threat broadens. Out-of-the-box integrations and pre-tuned detection mechanisms across multiple different products and platforms help improve productivity, threat detection, and forensics.
Forrester defines Zero Trust as “moving security from a network-oriented, perimeter-based security model to one based on continuous verification of trust.” For organizations, this means rethinking the trust-by-default approach and replacing it with a default-deny posture that only authenticates users to least privilege after assessing multiple sources of risk and context. This approach assumes that attackers are already within the network and ensures that every attempt to access the resources or applications be continuously scrutinized to ensure the request is legitimate.
Fundamentally XDR and Zero Trust solve the same challenge with a different approach and methodology. While Zero Trust is risk-centric and XDR is threat-centric, both involve deep integration of the technology stack to exchange telemetry between solutions and to respond in the face of a changing threat or risk landscape. Both seek to minimize enterprise risk and attack surface while enabling end-user productivity and efficiency.
End-to-End Protection from Endpoint to Cloud
SentinelOne and Zscaler joint solution delivers end-to-end protection from endpoint to cloud while streamlining SOC workflows.
SentinelOne and Zscaler combine to simplify enterprise security across endpoint, network, and cloud, enabling enhanced end-to-end visibility, automated response, and conditional access.
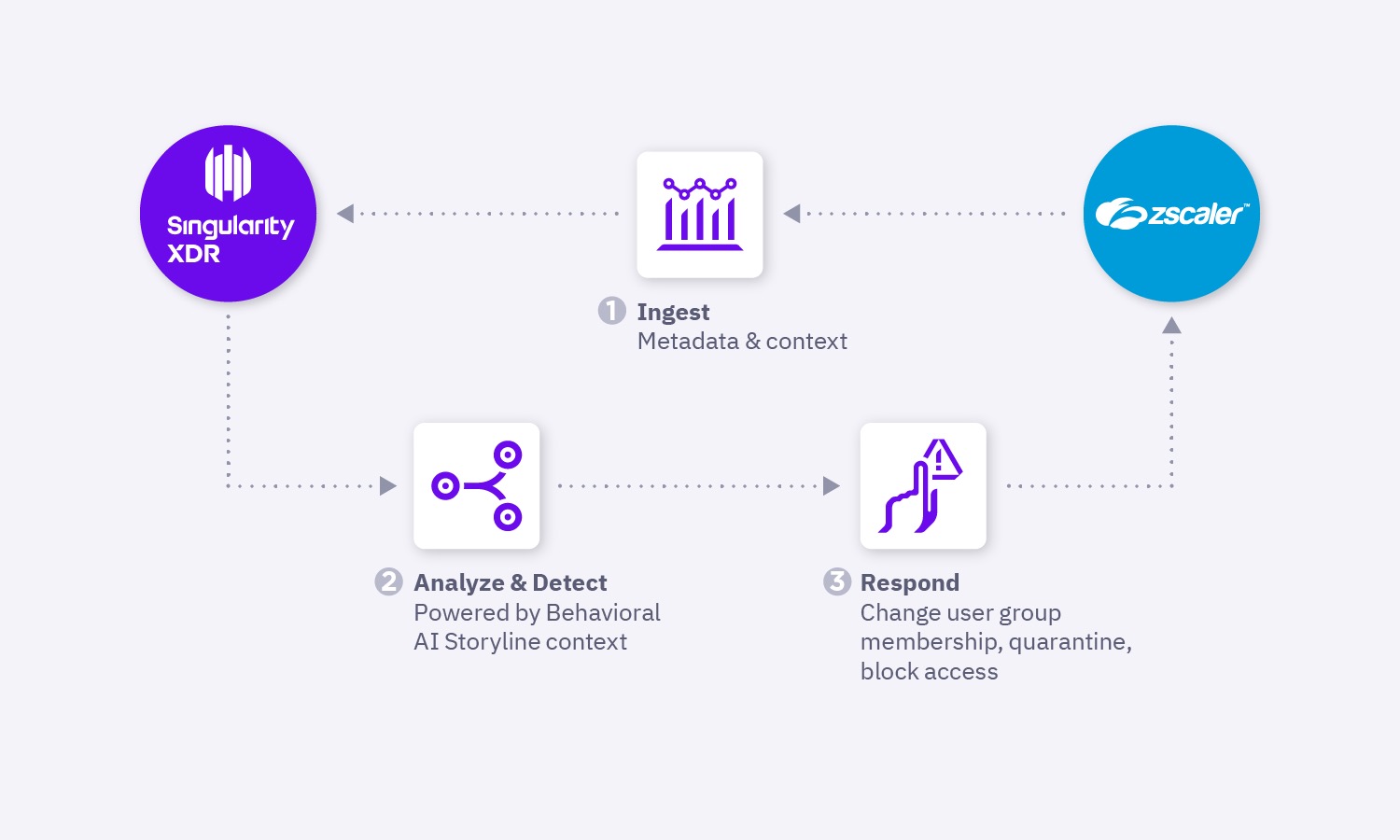
With integration into SentinelOne’s new data platform, Zscaler logs are ingested into SentinelOne. They can then be queried and faceted, allowing security operations teams to quickly triage and respond to attacks.
This joint solution empowers SOC teams to accelerate response with policy-driven actions that remediate threats automatically in Zscaler before an endpoint compromise results in cloud data exfiltration or other damage.
Analysts can trigger automatic and manual response actions from SentinelOne into Zscaler, such as revoking access or moving them into a more restrictive group, automatically limiting an attacker’s ability to infiltrate and launch an attack.
Coordinated user access control via the Zscaler Zero Trust Exchange provides secure conditional access to private and SaaS applications based on Zero Trust principles. Additional Zero Trust integration points include device posture checks by the Zscaler Cloud Connector agent to enable conditional access policies based on whether the SentinelOne agent is installed and running. This approach minimizes the enterprise attack surface with a zero-trust policy for conditional access.
With seamless integration, Zscaler and SentinelOne enable security teams to accelerate investigations and remediate threats without pivoting between consoles. Security Operation Centers can triage, investigate, and remediate threats much more efficiently and with greater confidence.
“Today’s security challenges require defense in depth. SentinelOne and Zscaler are key components in our security stack that help us advance our overall security posture. Together, Singularity XDR and Zscaler automate the triage and investigation functions in the SOC, enabling a small team to respond against threats with speed and accuracy.” — John McLeod, CISO, NOV
Use Case 1: Extended Visibility and Holistic Remediation Between Endpoint and Cloud
This joint solution enables SentinelOne to consume Zscaler logs for expanded visibility and enables security analysts to configure flexible response policies right from the SentinelOne console.
Analysts can quickly and automatically mitigate threats such as limiting user access, quarantining a user, blocking access to one or a group of critical applications, or restricting access to specific applications only with browser isolation.
Here’s how it works:
- Install the free app from Singularity Marketplace and provide it with Zscaler API credentials.
- Ingest the Zscaler logs into the SentinelOne Singularity XDR framework
- Use default or custom policies to trigger response actions by changing user group membership such as predefined restrictive or browser isolated groups. Ensure that users are granted access to enterprise applications and data based on the dynamic conditions of threats and user risk, with speed and consistency.

Use Case 2: Zero Trust Conditional Access Based on Endpoint Security Posture
The SentinelOne and Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) integration enable seamless conditional access, ensuring that the trusted identity on a trusted device can directly access authorized corporate applications without exposing the network.
The guiding principles of Zero Trust are to assume that attackers are already in the network, which means never implicitly trusting users or applications before verifying. Assuming that the environment is already compromised, nothing should be trusted until users, devices, and applications demonstrate their trustworthiness.
Zscaler and SentinelOne combine best-in-class Zero Trust access control with unparalleled visibility, AI-powered detection, and automated response across endpoints, applications, and cloud workloads. SentinelOne continuously checks policy and enforces compliance on the endpoint. At the time of access, Zscaler checks whether SentinelOne is installed and running, considers the endpoint’s security posture, and grants access to corporate applications.
Here’s how it works:
- SentinelOne secures endpoints with enterprise-grade prevention, detection, response, and hunting.
- Zscaler Client Connector (ZCC) verifies the presence of SentinelOne by using device posture as an additional authorization vector for access control. Zscaler ZIA and ZPA can be configured to allow only compliant endpoints – ones that pass the posture check – to access selected applications.
- Zscaler admins can specify (for Windows and Mac workstations) that SentinelOne is installed and running for an endpoint to be granted access to critical business applications.

Parting Thoughts
With attack vectors multiplying due to hybrid work models and BYOD programs, enterprises struggle to secure increasing numbers of vulnerable assets inside and outside the traditional network perimeter. SentinelOne and Zscaler help organizations prevent, detect, and respond to threats more quickly and effectively by providing a comprehensive view of threats across the cloud and endpoints.
Together, SentinelOne and Zscaler provide joint customers with increased SOC efficiency, streamlined workflows, and enhanced threat protection across endpoint, cloud, and network.
To learn more, check out the SentinelOne and Zscaler joint solution brief or attend our upcoming webinar.
Solving for X(DR) | Modernizing Security Operations with SentinelOne and Zscaler
Webinar: Thursday, March 3rd at 10:00am PST / 1:00pm EST
如有侵权请联系:admin#unsafe.sh