On Sunday, February 13th, Adobe pushed an emergency update to their Magento2 ecommerce software patching a critical unauthenticated remote code execution vulnerability. It is marked as CVE-2022-24086 with a CVSS score of 9.8. Website administrators of Magento stores should patch immediately.
Shop owners of Magento 2.3 or 2.4 stores can find the patch to install here. Instructions on how to install Magento security patches via Composer can be found here.
Our website firewall generic rules block RCE exploitation attempts by default but given the severity of the vulnerability website administrators should not leave their websites unpatched.
Further Details are Scarce
Fortunately, the issue was found by Magento’s internal security team before widespread exploitation attempts could be identified. That being said, they report that the vulnerability is already being exploited in very limited numbers. Now that the public (and, by extension, the attackers) have been made aware we can expect threat actors to be on the move without much further delay.
No further details have been provided publicly by Adobe and the CVE details are categorized as Reserved in order to discourage exploitation by other threat actors. This should allow Magento store owners sufficient time to patch their websites before more details emerge.
The Patch
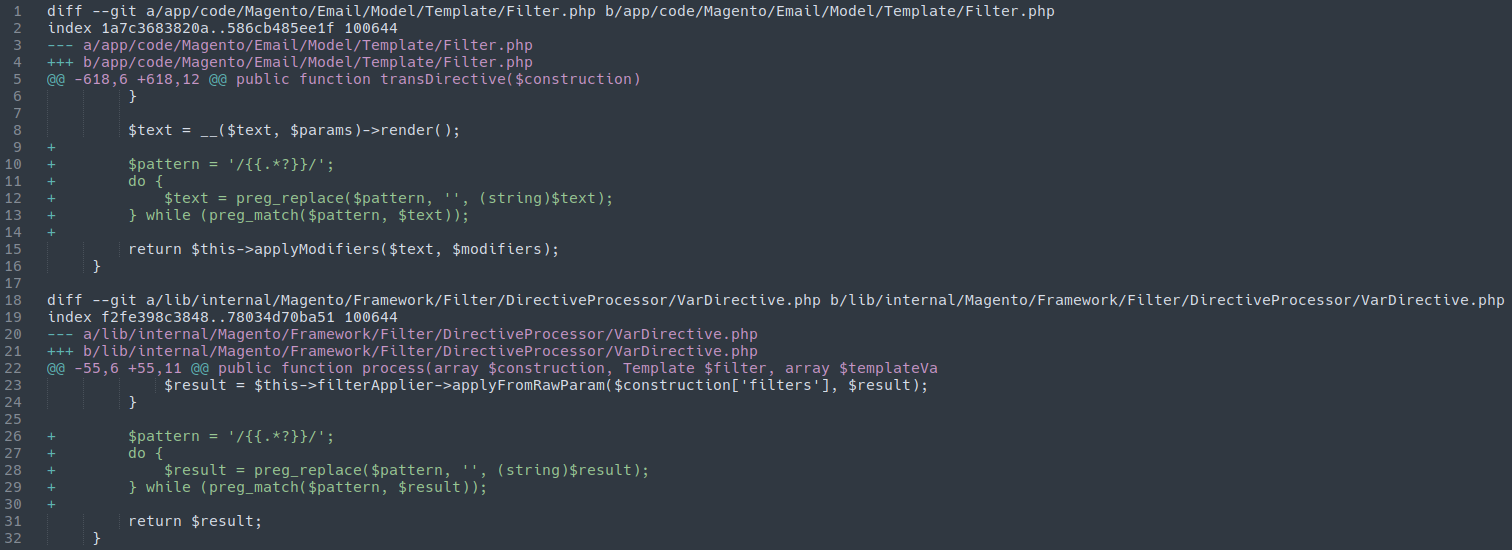
The emergency patch is small but crucial and affects the following files:
./app/code/Magento/Email/Model/Template/Filter.php
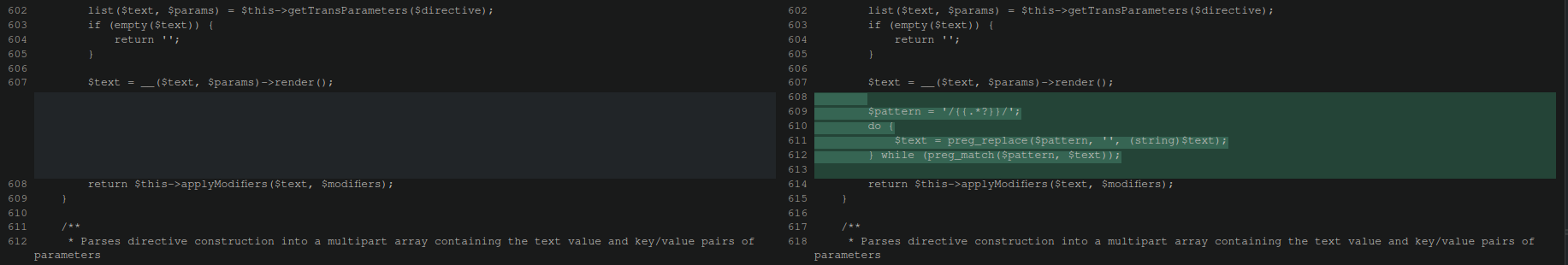
./lib/internal/Magento/Framework/Filter/DirectiveProcessor/VarDirective.php

Adobe reports that the issue stems from improper input validation.
Ecommerce Sites are Valuable Targets
Most website compromises that we see on the web are opportunistic – that is, attackers will exploit any and all websites that they can identify with a particular vulnerability, usually in automated fashion.
As we first pointed out in our 2019 Threat report, ecommerce website compromises are, in contrast, increasingly targeted attacks. Threat actors spend much more time crafting well-hidden payloads in order to maximize the number of compromised credit card details that they can steal from victim websites. Sometimes payloads are even crafted that are tailor-made to specific websites, if the attackers deem them a valuable enough target.
In Conclusion
This vulnerability is a great example of the ever-chaotic state of website security. Software deemed safe one day can be a huge liability the next. Website owners need to stay ever-vigilant to protect their websites from threat actors and ensure that they are staying on top of security patches and other updates.
Are you an ecommerce website owner? Consider our website protection service and file integrity monitoring to help keep your website safe.

