Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp Suite Pro, with powerful features tailored to the needs of the infosec and bug bounty community.
Features
- Machine-in-the-middle (MITM) HTTP proxy, with logs and advanced search
- HTTP client for manually creating/editing requests, and replay proxied requests
- Scope support, to help keep work organized
- Easy-to-use web based admin interface
- Project based database storage, to help keep work organized
ℹ️ Hetty is in early development. Please see the backlog for details.
💬 Join the Hetty Discord server.
Documentation
Installation
The quickest way to install and update Hetty is via a package manager:
macOS
brew install hettysoft/tap/hetty
LINUX
sudo snap install hetty
WINDOWS
scoop bucket add hettysoft https://github.com/hettysoft/scoop-bucket.git
scoop install hettysoft/hetty
Alternatively, you can download the latest release from GitHub for your OS and architecture, and move the binary to a directory in your $PATH. If your OS is not available for one of the package managers or not listed in the GitHub releases, you can compile from source (link?) or use a Docker image (link?).
Run
Once installed, start Hetty from the command line:
When invoked without any options, this:
- Creates a root CA certificate and private key, stored on disk at
~/.hetty/ - Creates a BadgerDB database, stored on disk at
~/.hetty/db/ - Runs an HTTP server that listens on
0.0.0.0:8080, used for proxying and serving the admin interface
You should see the following console output:
2022/03/01 11:09:15 INFO [main] Hetty (v0.5.1) is running on :8080 ...2022/03/01 11:09:15 INFO [main] Get started at http://localhost:8080👉 You can now visit http://localhost:8080 to access the admin interface.
TIP
To easily use the HTTP proxy without manual setup, Hetty can invoke Chrome (if installed) on startup with the correct predefined settings, via:
Alternatively, you can trust the root CA certificate system wide.
Create a project
- Visit the admin interface at http://localhost:8080 and click “Manage Projects”.
- Use the “New project” form to create an open new project:
Once you have a project created and opened, any incoming HTTP requests proxied by Hetty will be logged.
Use the proxy
To use Hetty’s HTTP proxy, you have several options:
- Run Hetty with
hetty --chromeand use a preconfigured Chrome instance (recommended) - Use a browser extension like FoxyProxy (Firefox) or Proxy SwitchyOmega (Chrome)
- Configure system wide HTTP proxy settings (not recommended)
When using a browser extension for proxying, you can use http://localhost:8080 as the proxy URL (unless you’ve specified a custom listen to address with the --addr option).
NOTE
If you’re planning to use the proxy from a machine different than the one running Hetty (e.g. another device in your LAN), you’ll need to use a non-loopback network address, e.g. the IP address assigned by your DHCP server.
👉 With one of the above options, use the proxy by visiting a website to incur some logs we’ll use in the next section.
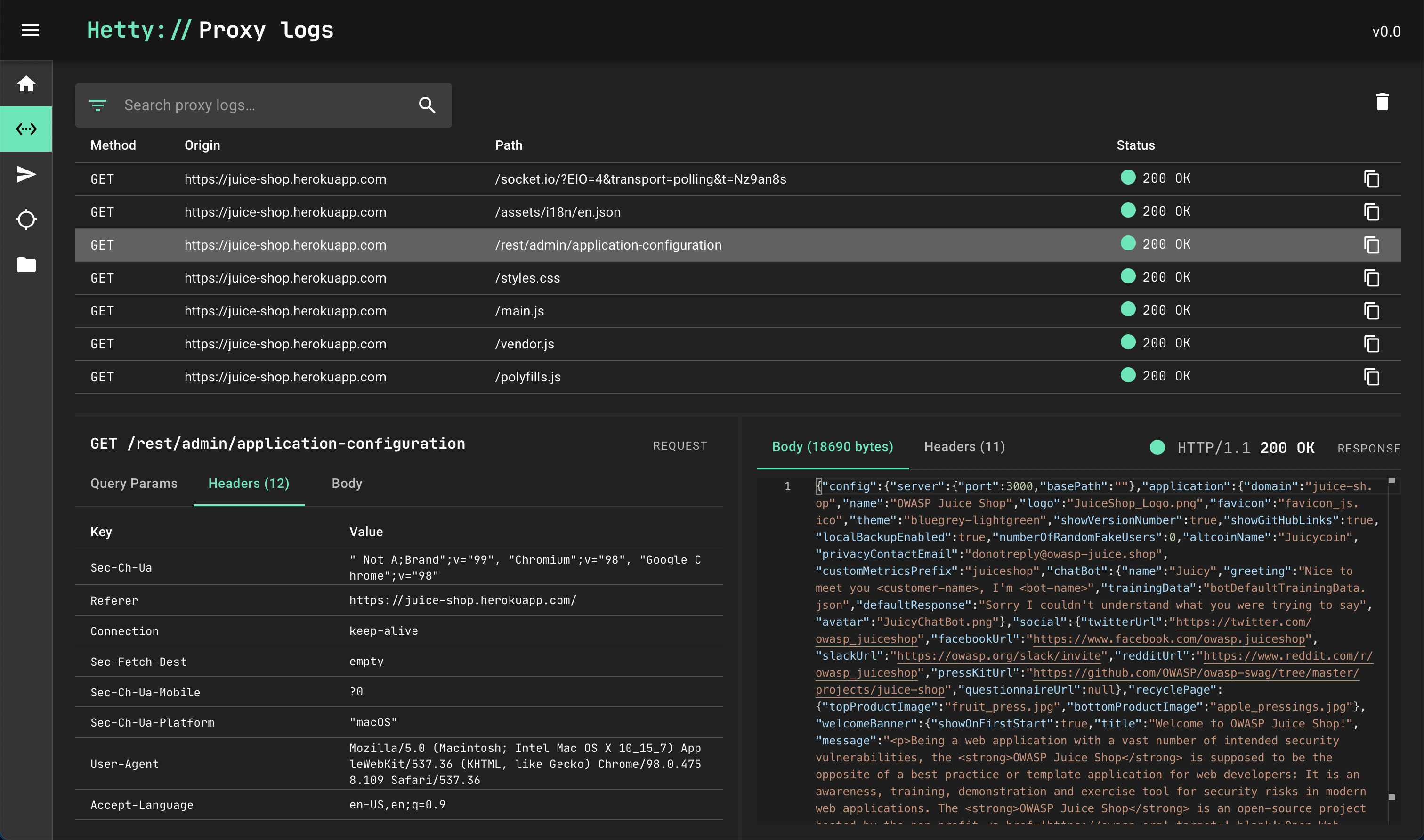
View proxy logs
Once you’ve generated some traffic on the HTTP proxy, there should be some requests logged. Let’s review them by opening the Proxy logs page in the admin interface, found in the vertical menu bar on the left.
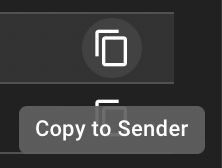
Copy to Sender
Use the “copy” icon next to any log entry to copy this request to the Sender module, allowing you to edit and resend the HTTP request:
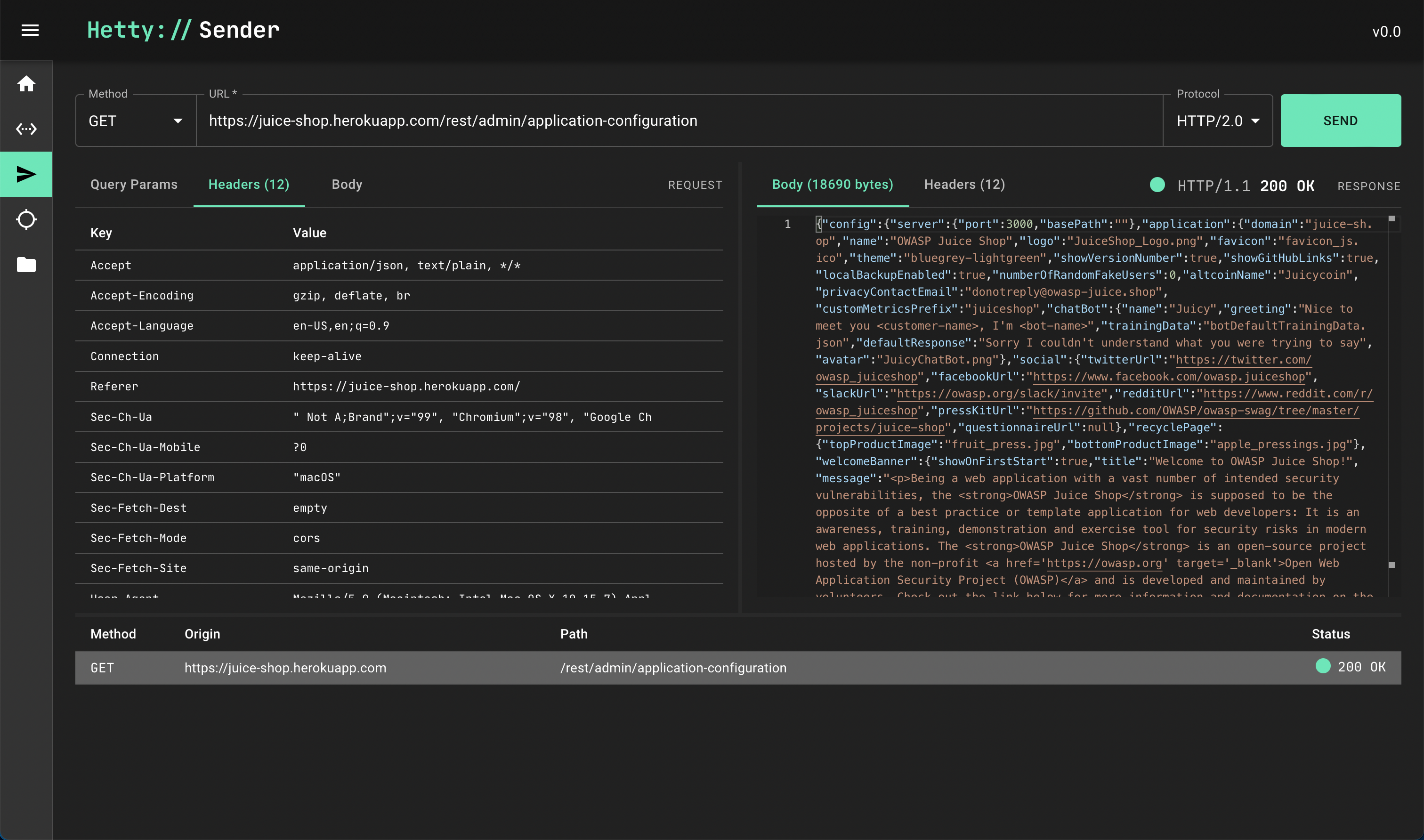
Edit & send request
Browse to the Sender module via the vertical menu bar on the left.
At the bottom of the screen, click the request we just copied from the Proxy logs.
Now you can edit the method, URL, request headers and body of the request. Every time you click Send, a new request is sent and recorded in the history pane at the bottom of the screen.
What’s next?
You should now be up and running with Hetty! 🎉 Check out the guides for more detailed feature documentation.
Support
Use issues for bug reports and feature requests, and discussions for questions and troubleshooting.
💬 Join the Hetty Discord server.
Contributing
Want to contribute? Great! Please check the Contribution Guidelines for details.
Acknowledgments
- Thanks to the Hacker101 community on Discord for all the encouragement and feedback.
- The font used in the logo and admin interface is JetBrains Mono.
如有侵权请联系:admin#unsafe.sh