2022-3-16 21:54:27 Author: hakin9.org(查看原文) 阅读量:19 收藏

Dear Readers, today we would like you to meet one of our great authors and reviewers, Daniel W. Dieterle! Enjoy the reading.
[Hakin9 Magazine]: Hello Daniel! Thank you for agreeing to the interview! How have you been doing? Can you tell our readers something about yourself?
Hi Magdalena, thank you for having me! I am doing very well, and you? Yes, I have been in the IT field for most of my life. For the last 10 years or so I’ve been mostly working solely in Security. I’ve been busy writing, teaching, and helping new security students, I really enjoy it!
[H9] You recently published your newest book - “Advanced Security Testing with Kali Linux”. Could you tell us a little bit more about it?
Of course, thanks for asking. „Advanced Security Testing with Kali Linux” (available through Amazon) is my 7th (total) book focused on Kali Linux. In essence, it is the last and final book of my Kali Linux series. It picks up right where my Basic Kali book finished and takes the reader much deeper into more advanced topics.
It covers topics like using the MITRE [email protected] Framework, Web Application Pentesting, Advanced Password Cracking, using Command & Control (C2) Frameworks, Offensive Forensics and I even cover a little bit about using IoT Devices for Pentesting. Another nice thing is the book is over 700 pages, so when you are finished you could use it as a monitor stand or to hold doors open, lol!
[H9] Why did you decide to write this book?
This book was actually planned for a long time. When I wrote my Basic and Intermediate Kali books, the plan was to follow them up immediately with the Advanced book. Instead, I ended up writing two different books, my NetHunter and Raspberry Pi security books, and then updating my Basic Kali book before writing the Advanced book. I know, right, just a small gap in time, lol. It was actually good though that I wrote this book last; in it, I address many topics that readers have brought up over the years.
[H9] What was the most challenging part of writing this book?
The largest challenge was mostly the fact of how fast things change in our field. The book was mostly finished last year, but then there were some large changes for multiple tools, and I ended up re-writing several of the chapters. Though in the end, it was a good thing, I ended up adding a lot of new material that wasn’t initially planned. So, overall, it was worth taking the extra time with it!
[H9] What did your research for this book look like?
I wanted this book to really help those new to the field and those prepping for industry security tests, like the OSCP. So, I spent a lot of time talking with senior Pentesters and Red Team members about the tools and techniques they are really using in the field. I took a close look at the material being covered in the exams. I also investigated what tools and techniques the successful test takers used. Lastly, I included a lot of things from my own experience.
[H9] What makes this book different from other Kali guides?
A lot of the Kali Linux books cover the same material over and over. With my Advanced book I tried to include a lot of tools and techniques that are being actively used that other books don’t cover. For example, I have an entire section on using the MITRE [email protected] framework. I don’t just cover the framework itself, but the offensive tools like Atomic Red Teams, „Invoke-Atomic” that you can use to test security using the outline of the framework. Also, I wanted my book to be used as a reference guide - so I included a lot of information that security professionals constantly look up from several different sources. Hence the huge size, lol!
[H9] As an author, do you think writing is an overlooked skill in cybersecurity?
Oh, very much so! I recently talked with a friend who is extremely talented, but didn’t include enough information on the written report portion of a mock pentest that an employer used as part of the interview process. You need the technical skills, but you also need to be able to communicate and interface with clients. Being able to write comprehensive „after engagement” reports are part of the profession.
[H9] What usually overlooked tools would you recommend for pentesting with Kali Linux?
One of the things that immediately comes to mind are Command & Control (C2) Frameworks. Kali has basically relied on ”Metasploit” as their standby C2 for ages. Metasploit is an amazing platform but there are many different C2 options available now. The website „The C2 Matrix” lists a lot of them, including their capabilities, in a spreadsheet type interface.
Though Metasploit is a very robust and feature rich platform, the Kali developers have been listening to the request for additional C2s to be added. Two have already been included - „Empire” and its graphical interface „StarKiller” were added last year. This year’s latest version of Kali includes „PoshC2”.
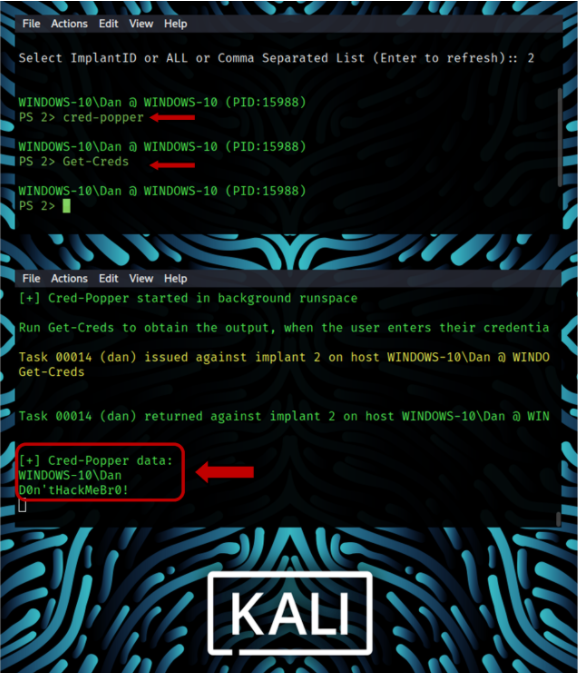
An example of pulling creds from a Windows 10 system with the new PoshC2
If things go as planned, several more will be added to the base Kali install in upcoming releases. Trying to jump ahead of the curve a bit, lol, I cover using multiple C2’s in my new book, including Empire, SharpSploit, SilentTrinity and an overview of the Professional version of Cobalt Strike.
[H9] What is the most difficult part of security testing?
I would say the most difficult thing is how fast the field is evolving. On average, tools and techniques that are „state of the art” right now, many times are obsolete in a couple years. Attackers are constantly learning, adapting and changing attack strategies and tools. Defenders must constantly adapt to the changes.
Cyber Espionage is a huge issue - nations attacking nations to steal secrets or intellectual property, influence elections or to sabotage industrial controls is surging. Also, a quick look at current events, and you can see the use and increase of modern „Hybrid Warfare” - using cyberattacks along with conventional attacks. This is only going to increase and many nations that don’t have robust cyber defense capabilities are struggling to rapidly create National Defense entities.
[H9] From your experience, what do you think separates advanced from intermediate? What are skills that make you consider someone as an advanced user?
Usually, when I think of an intermediate security professional, I think of one who knows the standard tools and tactics and is able to use them in actual security tests with clients. I think advanced security professionals are those that go the next step and actually create the tools that they need for the job. I see this a lot in the top Red Teams. Many of their tools are either modified or custom created. They are also able to work closely with and teach enterprise Blue Team members on how they exploited vulnerabilities and show them ways to address and correct the issues.
[H9] What changes in pentesting do you think will be the most important in the coming years?
One thing is the rise of machine learning and artificial intelligence use in security. I was able to attend a special government security conference on modern attack strategies. The work that is being developed and available now with Artificial Intelligence and Deep Fakes is much further along than many think. At some point in the future, AI systems will be attacking systems that are protected by AI systems. The attacks will be so fast that very little human interaction will be possible. This is both exciting and concerning. Truly very interesting times!
[H9] What is one of the most common mistakes when it comes to security testing?
The most common mistake I see is apathy. Time and again, I have seen companies use security testing teams for a security assessment. The teams exploit systems and give the reports to correct the issues, and then, nothing is done! No changes or very few changes are made. This is especially true when they are internal company testing teams. Sometimes, the targeted department sees it more as the other department made them look bad. Then when the next scheduled test takes place, the same exploits are used, some successfully, because the target did not take it seriously nor correct the issues.
The biggest issue overall that I see is the huge need for well trained cyber security professionals. I hope with my book, „Advanced Security Testing with Kali Linux”, I can encourage many readers and students to take the „next step” and become the next security professionals and leaders in the field.
Thank you so much for talking with me Magdalena, I truly enjoyed it!
[H9] Thank you for agreeing to talk with us!
如有侵权请联系:admin#unsafe.sh