Taking a minute or two to ask a few questions about an application before downloading it can greatly reduce your chances of downloading a malicious app.
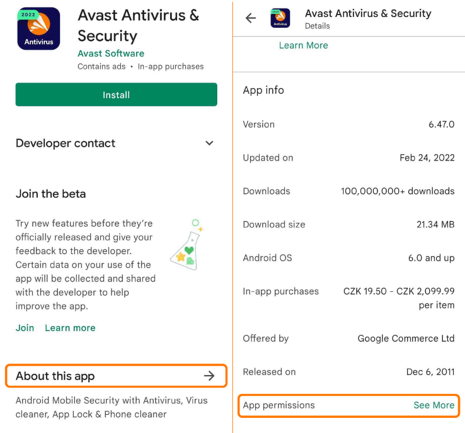
Before you download another application from the more than three million that are in the Google Play Store, read on to learn a few simple things you can do to protect yourself. Before we get into that, let’s establish why this is worthwhile. As noted by Tech Advisor, “The Google Play Store continues to be targeted with malware attacks. Several apps posing as useful tools have infected more than 300,000 Android devices” which exposed users' personal data. You should assume that everything within the store has already been vetted and is safe. Knowing that some apps are designed to look innocent but steal your data, there are some simple things to do to better protect yourself: 1. Check the number of downloads. Malicious apps do not usually last long on the Google Play Store as they are removed when they are identified and reported, so these bad apps usually don't have the chance to accumulate lots of downloads. Moreover, with more people using an app the chances of spotting undesired behavior of a system increases. The majority of the apps on the Google Play Store have less than one hundred downloads. 65.4% of all downloads are from the top 0.055% apps. 2. Check if an app has a link to a privacy policy and that the link leads to an actual privacy policy. Overall, it's good practice when an app or a web page has a privacy policy so users can get a better understanding of what data is collected and how it is being processed. If an app handles private or sensitive data, it’s required to have a privacy policy in many countries. However, the fact that an app has a link to a privacy policy listed in the Google Play Store does not necessarily mean that the policy is still available or leads to relevant content. By checking where such a link goes, you can easily take steps to verify the legitimacy of an app. 3. Check the list of the permissions the app is asking for. The names of the permissions can be confusing, and there are literally hundreds of them. There are more general ones (access to the internet, access to Bluetooth), but also very sensitive ones (access to your location, microphone, camera, contacts). If you are downloading a “simple” app it might be a red flag if the list of permissions is long. For example, the app Real Drum, a drum simulator, asks for access to all of the contacts and current cellular network information, the status of any ongoing calls, and a list of any phone accounts registered on the device. All of those permissions seem quite unnecessary. Another example is ibis Paint X, which is a drawing app that requests permission to record audio. Below, you can see which dangerous permissions are most commonly used by apps. Taking a minute or two to ask a few questions about an application before downloading it can greatly reduce your chances of downloading a malicious app.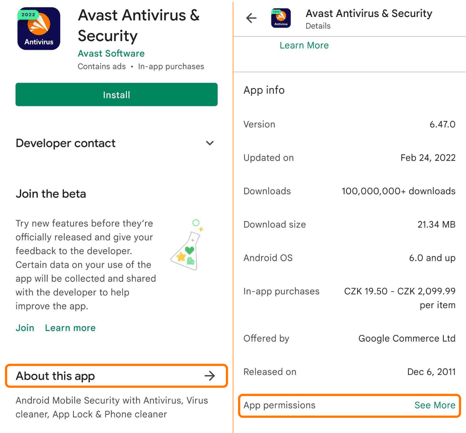
如有侵权请联系:admin#unsafe.sh