2022-4-26 01:27:23 Author: www.sentinelone.com(查看原文) 阅读量:40 收藏
Technology is an ever-changing landscape where we evolve and improve year over year much like the Moore’s Law theory with processor speeds. Cybersecurity, on the other hand, becomes more complicated and more diverse with the evolution of software and hardware vulnerabilities, which drives a larger and more complicated digital landscape for security professionals. According to Gartner, among the top seven trends in Cyber Security for 2022 is Digital Supply Chain Risk. Given the recent history of successful supply chain attacks, this should come as no surprise to CISOs and CIOs. The question is: how can you prepare your organization to effectively protect against a supply chain attack?

What Is A Supply Chain Attack?
Rather than attacking an organization directly, a software supply chain attack targets the vendors of apps and other code used by the organization. Typically, the bad actors will look to exploit some weakness in the vendor’s development cycle and attempt to inject malicious code into a signed and certified application.
By contaminating update servers or development tools, inserting code into executables, or simply replacing real packages with fake ones, adversaries can gain access to victims further along the supply chain.
A Brief History Of Supply Chain Attacks In The News
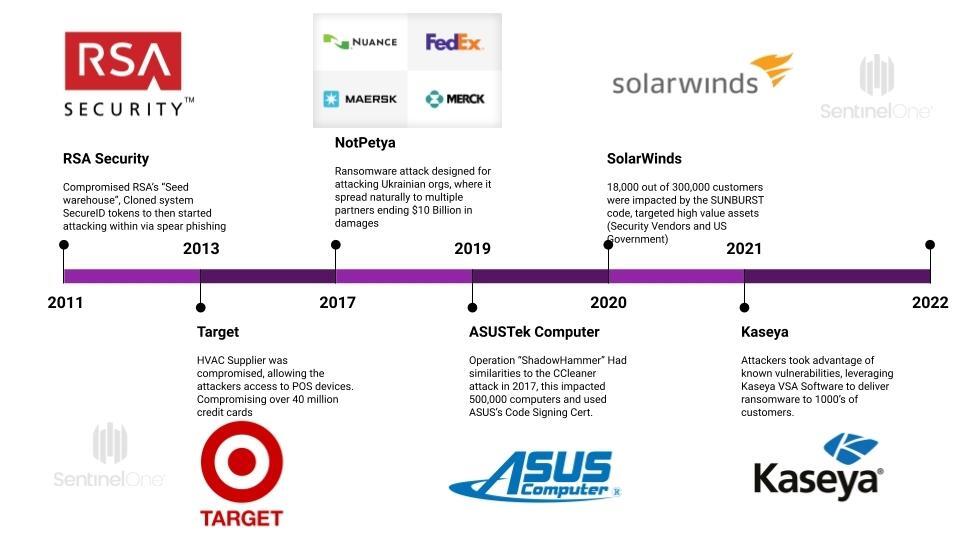
Here’s a quick breakdown of the most impactful supply chain attacks over the last decade or so.
RSA Security – 2011
- Compromised RSA’s “seed warehouse” for SecurID tokens
- Allowing for the attacker to clone to break into other systems leveraging SecurID tokens
- Attack delivered via spearphish with attachment “2011 Recruitment plan.xls” from a HR partner org!
- Used zero day Adobe Flash Player to drop a Poison Ivy RAT
Target – 2013
- A heating, ventilation, and air conditioning (HVAC) supplier allowed access into Target
- The hackers compromised Target’s server and placed the malware on POS devices across their entire store network.
- Compromised over 40 million credit and debit cards
- 18.5 million in settlement claims and untold reputation damage. Even Target has estimated this has had over $200 million in impact.
CCleaner – March 2017
- Hugely popular software (2BN total downloads by 2017) compromised to include a backdoor ‘ShadowPad’.
- Piriform breached via stolen TeamViewer creds, then installed ShadowPad malware to infect software distribution systems
- Binaries were being legitimately signed!
- Allowed the attacker to record keystrokes and included a password stealer
- 2.27M compromised downloads, with 1.65M communicated with CnC server
- 40 PCs targeted with 2nd stage infection
ASUSTek Computer – 2019
- ASUS Live Update Utility service delivered malware to 1000s of customers
- Impacted up to 500,000 computers
- Targeted 600 specific hardcoded MAC addresses
- Legitimate code signing certificate used
- Operation ShadowHammer had similarities to ShadowPad, group also linked to CCleaner attack.
SolarWinds – December 2020
- SUNBURST malicious code deployed by SolarWinds Orion official updates
- Widely trusted software vendor with 300,000 customers
- Impacted some 18,000 customers
- Malware waits 12 days before executing and initiating to its C2
- 264 days from malware compilation, to detection in December
- High value targets including security vendor and US Gov
Kaseya – July 2021
- Kaseya VSA software used to deliver ransomware
- Compromised approx. 1500 customers
- Attackers leveraged two (known) vulnerabilities in the VSA software
- Financially motivated – $70M ransom
- Russia linked group REvil took credit leveraging their ransomware; also, behind June 2021’s JBS ransomware attack.

More examples can be found in our previous post here.
Based on these previous attacks, we can determine the following are the primary focus for threat actors:
- Targeting insecure software for building systems or large-scale updating platforms
- Targeting custom in-house development or specialized code/firmware
- Using stolen certificates to sign apps, making themselves look like a trusted 3rd-party product or a product developed in house.
- Exploiting vulnerable devices, from network gear to IoT and POS, allowing for the shipment and movement of pre-installed malware.
How To Protect Against Supply Chain Attacks?
As we’ve learned from the trends of supply chain attacks, we need to encourage strong security practices from our software vendors and developers, then prepare for those who are not meeting those standards.
For the organization looking to protect against supply chain attacks, there are a number of action points that should be implemented.
First of all, be sure to enforce strong code application integrity policies to allow only authorized apps to run. This can be accomplished by leveraging SSO Authorization Code Grant or leverage an Application Control platform for your organization
Next, make sure that you leverage a strong Endpoint Detection and Response (EDR) solution that can automatically detect and remediate suspicious activities in real timeWhen looking into an EDR solution, make sure it’s meeting your company’s minimum criteria and view the MITRE ATT&CK Evaluations when comparing products. Some crucial questions to take into consideration are:
- How does the EDR solution protect your assets? Does it require an Agent? Is it Agentless? If you don’t have an agent, what features are you missing leveraging an Agentless EDR solution?
- What Devices or Operating Systems (OS) are not Covered by the EDR Security Solution? How many different types of agents/policies are needed to expand to these different OS’s?
- Does this EDR Solution expand to Cloud Platforms?
- Does this EDR software provide easy integrations with other systems?
- How much automation does the EDR provide out of the box?
- How long can I store data with this EDR solution? Most organizations need a minimum of two to three months of logs for audit purposes.
- If your company has a merger and acquisition, how complicated would it be to combine your EDR solution with theirs?
Aside from ensuring you have the right endpoint detection and response solution to meet your business needs, consider using an open and flexible security platform that can maximize your visibility. An Extended Detection & Response (XDR) platform can offer flexibility, visibility and peace of mind knowing you have a single place to go in the event of a cyber security attack. XDR also offers better ROI and can make your company more cost efficient by finding trends and bad practices within your organization.
Of course, even with the right technology in place, it’s still vital to be prepared for data loss or denial of service with secure backups and regular redeployment testing. While ransomware attackers have evolved their extortion tactics to beyond mere denial of service, effective backups remain necessary due to the possibility of local disasters or just general hardware failure. You should follow a standard that meets the risk level you’re comfortable with, whether that is the 3-2-1 backup rule or 3-2-1-1-0 or 4-3-2. Stick with a plan and make sure you’re securing these backups to prevent tampering, then have a schedule or audit where you test these backups.
Drive a Cybersecurity-Centric Culture
Besides making sure your technology stack is up to scratch for a modern enterprise, there are other changes needed. It’s crucial to drive a Cybersecurity-Centric Culture in your company to make sure that your investment in technology reaches its full potential.
There has been plenty of good research into how to effectively implement a cybersecurity-first culture, but in essence it boils down to the following.
- Empowering People—Cybersecurity culture empowers people with the sociological and psychological skills that are required to work with cybersecurity technology and processes.
- Projecting cybersecurity meaning—Within the enterprise, the importance of the people, technology and processes of cybersecurity is understood. The consequences of ignoring cybersecurity’s technological and financial risk are addressed.
- Establishing stakeholder partnership and collaboration of key players—A network of cybersecurity stakeholders is defined and managed. Stakeholders include employees, managers, government agencies, senior executives, boards of directors, technology providers, consulting providers, and education and training providers.
- Providing an education and training road map—An appropriate education and training program that encompasses the people, technology and processes of cybersecurity is integrated and delivered.
Empower Security Hygiene for Developers
For the software vendors and developers needing to improve their security posture to prevent the opportunity of supply chain attacks, start considering the following options:
- Maintain a secure infrastructure around update/build management
- Don’t delay on security patches for either OS/Software driven vulnerabilities
- Require mandatory integrity controls to ensure only trusted tools can run in your organization; investigate into implementing CISA Zero Trust Maturity Model
- Look into passwordless authentication and require Multi-Factor Authentication (MFA) for all admins
- If you haven’t already, build secure software updaters as part of your Secure Software Development Lifecycle (SSDLC)
- Require SSL for update channels and implement certificate pinning
- Everything should be signed, including configuration files, scripts, XML Files, and packages
- Don’t allow your updater to accept generic input or commands, require digital signatures
- Develop an Incident Response (IR) plan for supply chain attacks, create a runbook and actually stress-test it with attack simulations
Conclusion
Bad actors are always looking for an easy buck, with the least amount of resistance for the biggest opportunity, and supply chain attacks are still on the radar for these groups. The landscape is getting even more complicated with 9 out of 10 companies leveraging open-source software projects. Add to that the growing use of Internet of things (IoT) for cars and smart devices like appliances, door locks and thermostats, as well as the growth of IoT in healthcare and industrial/energy, and you have a never-ending expansion of the attack surface in almost every organization.
It is essential that organizations review their cybersecurity requirements, gain visibility into supply chain dependencies, and be prepared with modern tools and practices to help contain and prevent future supply chain attacks.
Want to know more about how SentinelOne can help? Contact us for more information, or request a free demo.
如有侵权请联系:admin#unsafe.sh