We know that software vulnerabilities remain one of the primary causes of external attacks. We also know that on average, vulnerabilities are exploited for the first time just days after they’re disclosed. You may be managing many third-party applications, so how can you make sure you can drive remediation and reduce the risk for all your software? Once vulnerabilities are discovered, how will you know which ones should be prioritized?
Keeping up with Software Vulnerabilities
A common misconception is that every vulnerability in your organization should be addressed immediately, but keeping up with vulnerability disclosures that affect your environment is a constant, ongoing challenge. It can take hours and sometimes days to manually package, test and release any given update. But with the right vulnerability prioritization in place, you could work faster and smarter with greater impact, focusing on patching just 10 percent of the vulnerabilities affecting your environment.
Having direct access to valuable vulnerability and threat intelligence allows you to stay ahead of potential threats in your organization. With the help of our Secunia Research team, customers can use Software Vulnerability Manager (SVM) to access helpful security advisories which validate, score and document remediation steps. The team has more than 19 years of experience, tracks more applications than any other solution on the market, and delivers 95 percent of advisories within one day of disclosure. The days of tracking vulnerabilities through unmanageable spreadsheets are over. In fact, if you’d like to see advisories on software not currently covered, our team responds to new addition requests within 72 hours. Knowing this, you can rest assured that all your software can be easily monitored.
How to Prioritize Software Vulnerabilities
With rapid awareness in of the vulnerabilities that affect you, how do you know which vulnerabilities need to be addressed first? It comes down to four categories to determine the highest priority based on the needs of your organization: Threat, Prevalence, Criticality and Asset Sensitivity.
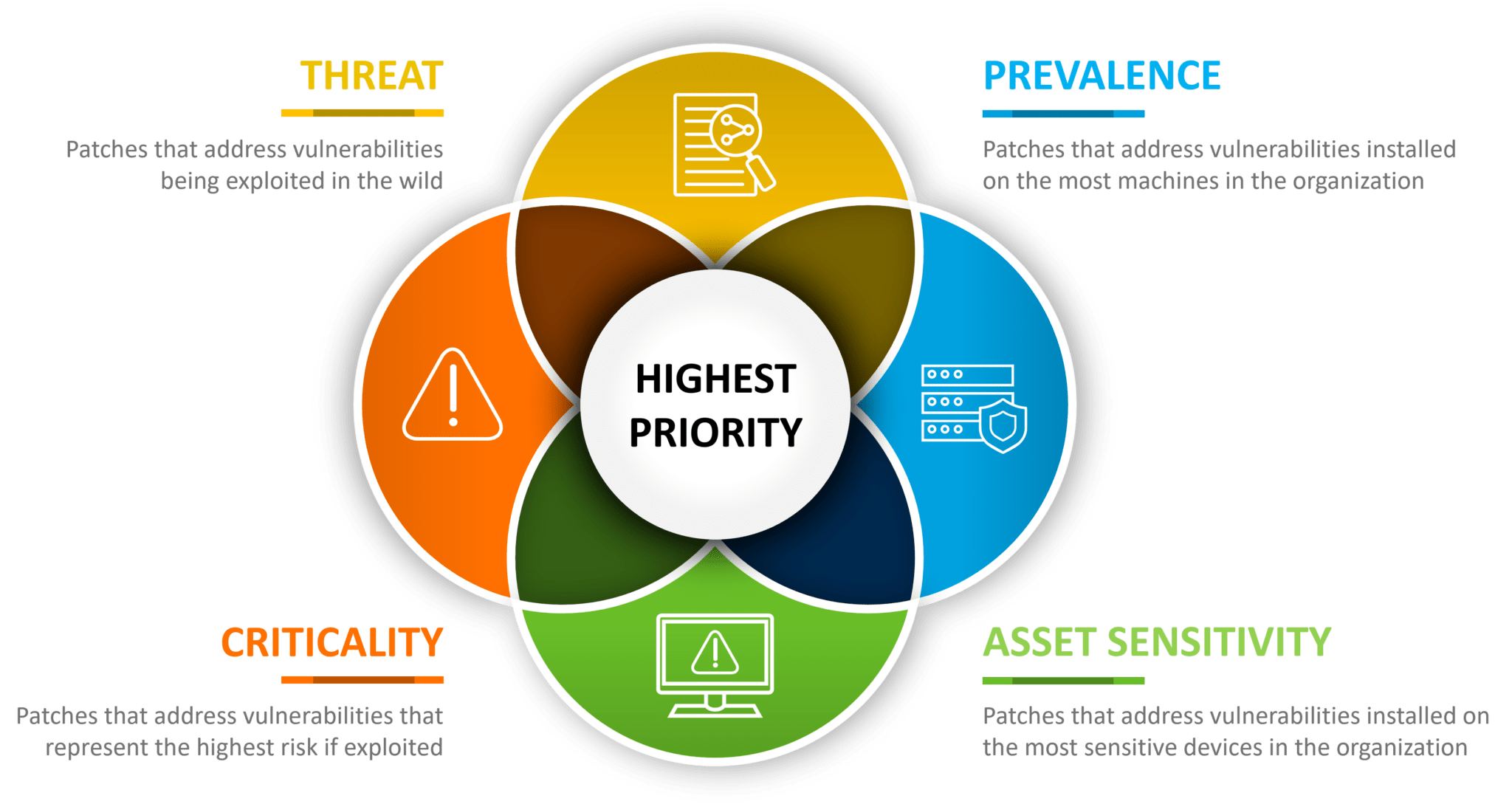
Prevalence focuses on how many systems the update would address. The more it addresses, the greater the value it may have. In the past, IT organizations would subscribe to various third-party patch catalogs, but we have a better approach. Flexera has the most extensive patch catalog on the market, and powerful automation capabilities to help quickly remediate those deemed significant priority. Instead of hoping third-party patch catalogs would protect your applications, organizations can discover which vulnerabilities in your unpatched products have the highest risk of exploitation.
Asset Sensitivity aims to help you determine which systems would cause the most damage if compromised. Criticality is an indicator of risk based on possible damage if exploited. And Threat Intelligence helps you quantify which vulnerabilities are likely to be exploited. This is one of the newest approaches for determining how to effectively prioritize your software vulnerabilities and is incredibly valuable in helping to determine which patches you should focus on first (or not at all).
Our threat intelligence data provides a metric that helps you to prioritize based on the likelihood of exploitation and is generated by machine learning, artificial intelligence and human curation from thousands of sources in the open, deep and dark web to provide the ultimate vulnerability prioritization tool for your busy desktop operation teams.
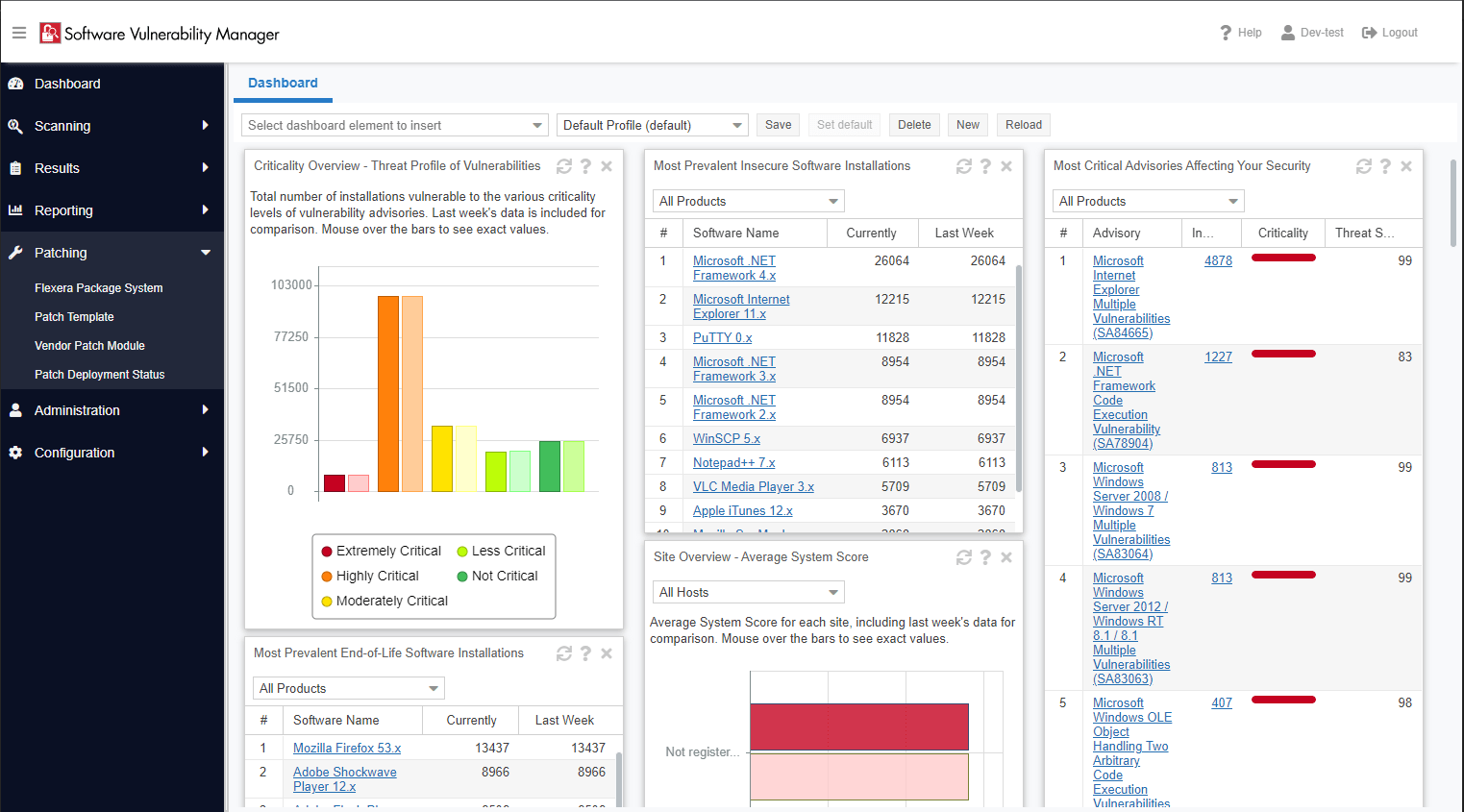
Now that you have an understanding of how overwhelming patch management can be with software vulnerabilities, you can easily see how having a tool like Software Vulnerability Manager could easily help you stay informed and secure.
Stay up to date on Software Vulnerabilities with our webinar featuring Forrester where we break down current vulnerabilities trends and how we can help you address them through tools like Software Vulnerability Manager and Software Vulnerability Research.
