Features
- Blazing fast as we are using
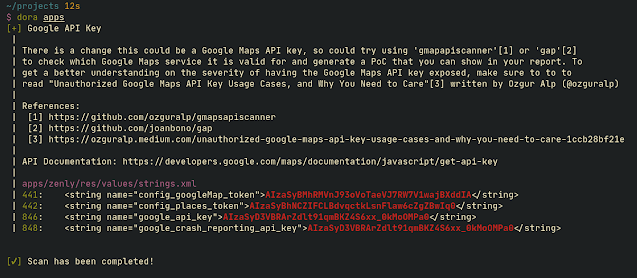
ripgrepin backend - Exploit/PoC steps for many of the API key, allowing to write a good report for bug bounty hunting
- Unlike many other API key finders,
doraalso shows the path to the file and the line with context for easier analysis - Can easily be implemented into scripts. See Example Use Cases
Installation
Make sure to install ripgrep
directory to sherlock $ cd dora # install dora $ python3 setup.py install --user">
# clone the repo
$ git clone https://github.com/sdushantha/dora.git# change the working directory to sherlock
$ cd dora
# install dora
$ python3 setup.py install --user
Usage
debugging information --no-color Don't show color in terminal output">
$ dora --help
usage: dora [options]positional arguments:
PATH Path to directory or file to scan
optional arguments:
-h, --help show this help message and exit
--rg-path RG_PATH Specify path to ripgrep
--rg-arguments RG_ARGUMENTS
Arguments you want to provide to ripgrep
--json JSON Load regex data from a valid JSON file (default: db/data.json)
--verbose, -v, --debug, -d
Display extra debugging information
--no-color Don't show color in terminal output
Example Use Cases
- Decompile an APK using
apktooland rundorato find exposed API keys - Scan GitHub repos by cloning it and allowing
dorato scan it - While scraping sites, run
dorato scan for API keys
Contributing
You are more than welcome to contribute in one of the following ways:
- Add or improve existing regular expressions for matching API keys
- Add or improve the
infoin the JSON data for an API key to better help the user getting a valid bug bounty report when reporting an API key they have found - Fix bugs (kindly refrain from creating bugs)
Credits
Original creator - Siddharth Dushantha
Many of the regular expressions where taken from the following GitHub repositories:
- truffleHogRegexes by dxa4481
- secretx by harry1080
- gitGraber by hisxo
- shhgit by eth0izzle
- w13scan by w-digital-scanner
- SecretFinder by m4ll0k
- nuclei-templates by projectdiscovery
- AdvancedKeyHacks by udit-thakkur
- pentest-tools by gwen001
- gitleaks by zricethezav
- dalfox by hahwul
Majority of the exploitation/POC methods were taken from keyhacks repository by streaak