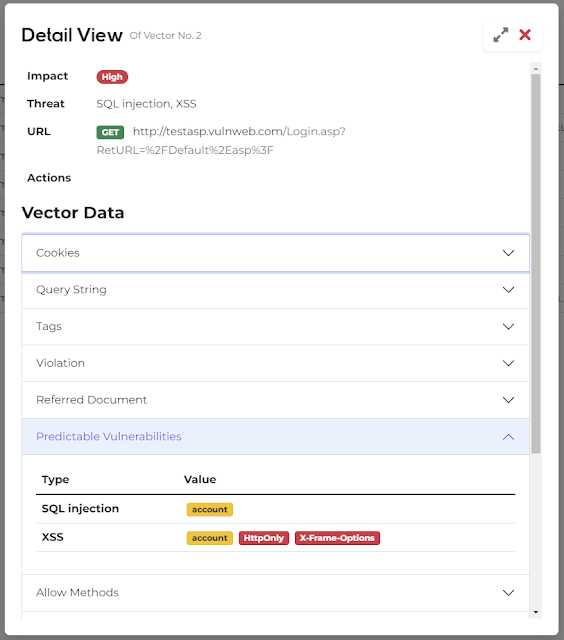
The BoB Web Application Security Project (BWASP) is an open-source, analysis tool to support for Web Vulnerability Manual Analysis hackers.
The BWASP tool basically provides predicted information through vulnerability analysis without proceeding with an attack.
BWASP supports performing automated analysis and manual analysis.
The BWASP Project supports:
- Find Attack vector automatically. (e.g. SQL Injection, Cross-site Scripting)
- Detect website technology.
- Log4J vulnerability scan (Partially supports java language)
- HTTP REST API
- GuideLine Result
- Test payload option(attack test)
Getting started
pip3 install -r requirements.txtpython3 start.py
BWASP Tool Guide
Roadmap
- Add OSINT feature (find subdomains)
Reference
Web Infra Environment Analysis: wappalyzer(https://github.com/AliasIO/wappalyzer)
Contact
Contributor
- Dohun Koo (@dohunny)
- Sanghyeon Lee (@isanghyeon)
- Joowon Kim (@arrester)
- Jongmin Kim (@Universe1122)
- Joonyoung Jeong (@jeongjy0317)
- Joomyeong Lee (@PecentZero)
- PL: Jiheon Choi (@jiheon-dev)
- Mentor: Gangseok Lee (@codeengn), Sehan Park (@combab0)
Acknowledgement
This work was supported by Korea Information Technology Research Institute (KITRI) Best of the Best (BoB) Program 10th vulnerability analysis track.
[Project Name: BoB Web Application Security Project]