2022-5-19 17:16:55 Author: hakin9.org(查看原文) 阅读量:32 收藏

What is Osmedeus?
Osmedeus is a Workflow Engine for Offensive Security. It was designed to build a foundation with the capability and flexibility that allow you to automatically run your reconnaissance methodology on a large number of targets.
CREDIT:
https://github.com/j3ssie/osmedeus
Installation
NOTE that you need some essential tools like
curl, wget, git, zipand login as root to start
bash <(curl -fsSL https://raw.githubusercontent.com/osmedeus/osmedeus-base/master/install.sh)
Install from a base repository
NOTE that you need some essential tools like curl, wget, git, zip, tmux and login as root to start
bash <(curl -fsSL https://raw.githubusercontent.com/osmedeus/osmedeus-base/master/install.sh)
Install for MacOS (experimental)
NOTE that you need to install homebrew first.
bash <(curl -fsSL https://raw.githubusercontent.com/osmedeus/osmedeus-base/master/install-macos.sh)
Some other changes you might need to make if you're really want to use Osmedeus on MacOS
Install from a build release
Make sure you login as root otherwise run sudo su first then put build-osm.zip to any folder (e.g: /opt/)
unzip -q build-osm.zip && cd build-osm
./build.sh
# verify your installation with health command
osmedeus health
Using Docker
Pull the Docker image by running docker pull j3ssie/osmedeus and follow this page for in-depth usage.
Verify the installation process
Just run the command osmedeus health. If you see the content like the image below then it means the installation process has been a success.
The installation process is still successful if you see this message. It's just one of many Premium features
[-] Cloud config setup incorrectly. If you install osmedeus on a single machine then it's okay to ignore the cloud setup
Build the engine from the source
Make sure you installed golang >= v1.17
mkdir -p $GOPATH/src/github.com/j3ssie
git clone --depth=1 https://github.com/j3ssie/osmedeus $GOPATH/src/github.com/j3ssie/osmedeus
cd $GOPATH/src/github.com/j3ssie/osmedeus
make buildor
go install -v github.com/j3ssie/[email protected]Usage
# Scan Usage:
osmedeus scan -f [flowName] -t [target]
osmedeus scan -m [modulePath] -T [targetsFile]
osmedeus scan -f /path/to/flow.yaml -t [target]
osmedeus scan -m /path/to/module.yaml -t [target] --params 'port=9200'
osmedeus scan -m /path/to/module.yaml -t [target] -l /tmp/log.log
cat targets | osmedeus scan -f sample
# Practical Scan Usage:
osmedeus scan -T list_of_targets.txt -W custom_workspaces
osmedeus scan -t target.com -w workspace_name --debug
osmedeus scan -f general -t www.sample.com
osmedeus scan -f gdirb -T list_of_target.txt
osmedeus scan -m ~/.osmedeus/core/workflow/test/dirbscan.yaml -t list_of_urls.txt
osmedeus scan --wfFolder ~/custom-workflow/ -f your-custom-workflow -t list_of_urls.txt
# Provider Usage:
osmedeus provider build
osmedeus provider build --token xxx --rebuild --ic
osmedeus provider create --name 'sample'
osmedeus provider health --debug
# Cloud Usage:
osmedeus cloud -f [flowName] -t [target]
osmedeus cloud -m [modulePath] -t [target]
osmedeus cloud -c 10 -f [flowName] -T [targetsFile]
osmedeus cloud --token xxx -G -c 10 -f [flowName] -T [targetsFile]
osmedeus cloud --chunk -c 10 -f [flowName] -t [targetsFile]
# Utilities Usage:
osmedeus health
osmedeus version --json
osmedeus utils tmux ls
osmedeus utils tmux logs -A -l 10
osmedeus utils ps
osmedeus utils ps --proc 'jaeles'
osmedeus utils cron --cmd 'osmdeus scan -t example.com' --sch 60
osmedeus utils cron --for --cmd 'osmedeus scan -t example.com'LINKS:
Manifest
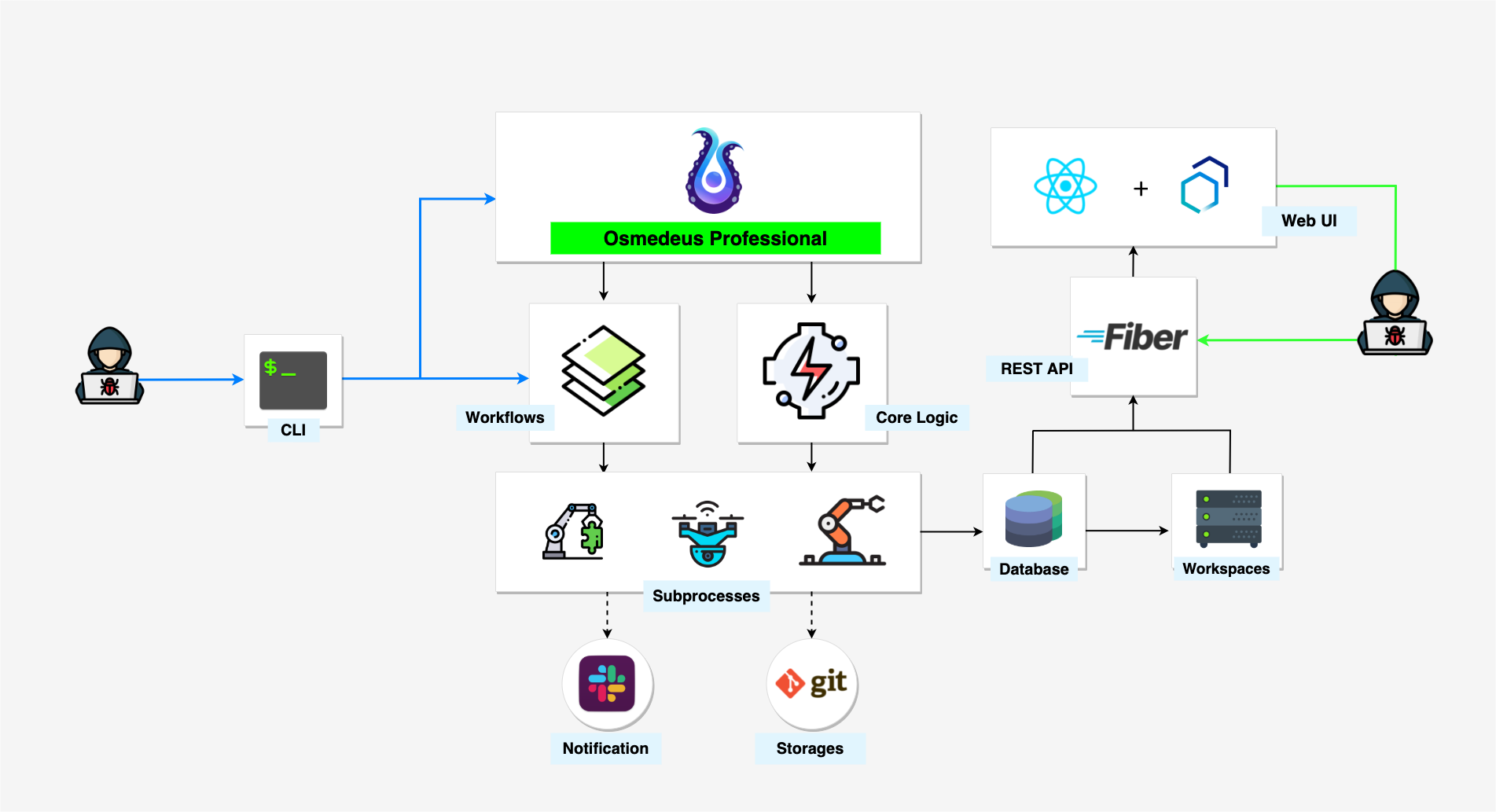
The main philosophy of Osmedeus was never meant to be the that replace your tools or any other tools. It was designed to build a foundation with the capability and flexibility that allow you to make your recon system faster, cleaner and much more powerful.
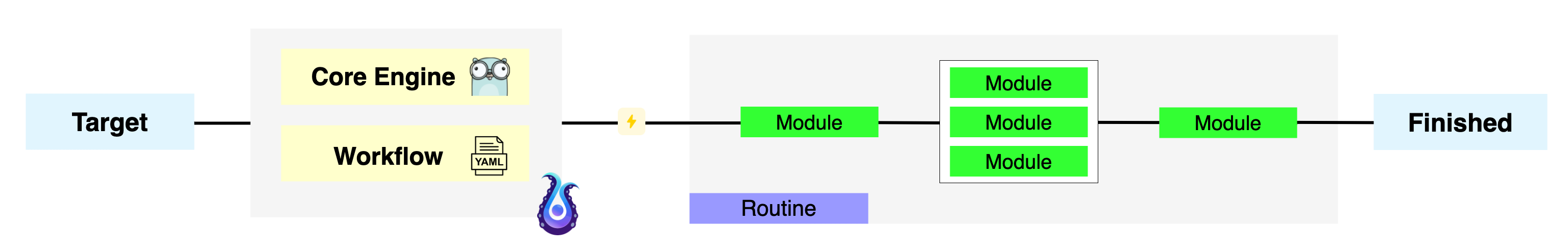
The structure of the Osmedeus
The tool has two main components:
- Core Engine Written in Golang which is responsible for handling all the complex logic and provides a lot of built-in utilities to run your workflow much more efficiently.
- Workflow is a collection of YAML files that describe your methodology.
Target can be the domain, URL, IP, CIDR, or anything that fit your workflow.
How does Osmedeus actually work?
Osmedeus will take your input along with the selected flow/module to create a routine that contains a list of commands and logic to complete the scan.
Behind the scene, it actually runs other 3rd party tools with a special logic generated by Osmedeus core.
💬 Community & Discussion
Join Our Discord server here
💎 Donation & Sponsor
Check out for a couple of donation methods here to get a premium package
如有侵权请联系:admin#unsafe.sh