2022-5-31 23:48:15 Author: www.sentinelone.com(查看原文) 阅读量:17 收藏
The State of Email Security
As tactics change, the sophistication of threat actors increases, and new vulnerabilities are constantly discovered, security operations teams are stretched to the limit investigating and remediating each incident. Email remains one of the most highly leveraged attack vectors. A staggering 79% of respondents to Mimecast’s State of Email Security 2022 study reported an increase in email volume at their organization, while 72% reported the number of email-based threats had risen during the past 12 months. Organizations today seek integrated defenses to protect email and improve incident response capabilities, while helping to reduce complexity, minimize risk, and decrease the demand on an already over-extended and under-staffed security team.

The State of Threat Intelligence
As email-based cyber attacks continue to rise, security teams are stretched and suffering from alert fatigue. They are still challenged by decision making and find themselves relying on limited data found during the investigation, accepting decisions will be made based on incomplete knowledge because they do not have time to investigate further.
Another common challenge: Security teams spend so much time gathering data that they do not have time to solve the problem. Organizations have to reduce complexity, minimize risk, and decrease the demand they put on already overtasked security teams. In the meantime, threats can move laterally throughout the organization before they are properly identified and remediated.
The Cybersecurity Skills Gap
And while the volume, intensity, and intelligence of cyberthreats increase, the world is simultaneously seeing a shortage of skilled cybersecurity talent that continues to widen. Tight job market or not, SOC analysts remain fatigued with the collection, normalization, and prioritization of data, unable to focus on cybersecurity incident response and resolution. Organizations face challenges hiring and retaining skilled security professionals. The deluge of alerts from security tooling and repetitive nature of the Tier 1 analyst position makes burnout one of the leading contributors to this shortage.
A New Solution Has Become Necessary
Security teams look to automation to help alleviate some of the repetitive tasks of incident response to focus their limited resources on the highest impact and most critical incidents, increasing throughput and reducing the time to respond. Integrating automation tools can help alleviate some of the alert and decision-making fatigue, data gathering woes, worker burnout, and pain caused by a lack of skilled workers, but we can leverage technoogy to do much more than that. As threats become more complex and organizations face worker shortages, a more advanced method of detection – XDR – has become necessary for most organizations.
What Is XDR, and Why Is It So Critical?
In an era where there are essentially no network perimeters, and disastrous breaches can come from anywhere at any time, security teams must sharpen their focus on threat detection and response.
In many organizations, earlier approaches such as first-generation security information and event management (SIEM) systems have proven unwieldy. They can be difficult to deploy and integrate, and are too costly and too susceptible to false positives. Linking SIEM to security orchestration and response (SOAR) systems has helped some organizations build response playbooks for automating responses to certain threats, but creating these has often been more complex and difficult than anticipated.
Cloud-native XDR solutions promise to overcome each of these problems, providing more focused and actionable data, better integration, more relevant insights, fewer false positives, and easier automation of responses. As XDRs move beyond endpoint-only EDR solutions, they promise to provide the fuller visibility and faster response that couldn’t be achieved with earlier tools.
Integrated Solutions Stop Threats
Strategic integrations lessen SOC teams’ pain by using automation between email and endpoint security solutions to prevent the lateral movement of threats throughout the organization.
Mimecast and SentinelOne provide an integrated solution that stops threats and streamlines response across the organization. Customers can be confident their devices will be protected from zero-day threats across each endpoint. By correlating response between email and endpoint security solutions, analysts automate repetitive tasks for faster and more comprehensive incident response. When integrated, the two solutions deliver accelerated incident response and reduced mean time to response.
How the Mimecast and SentinelOne Integration Works
SentinelOne Singularity XDR provides AI-powered prevention, detection, and response across endpoints, cloud workloads, and IoT devices. When a threat is detected in SentinelOne, SentinelOne StorylineTM correlates detections and activity data across security layers, including email, endpoints, mobile, and cloud. Analysts can streamline the organization’s response by automatically suspending email for a given user, blocking the user email, or quarantining them. Upon detection of the threat, SentinelOne can automatically suspend the last logged-in user’s ability to send an email, helping secure a critical lateral movement path.
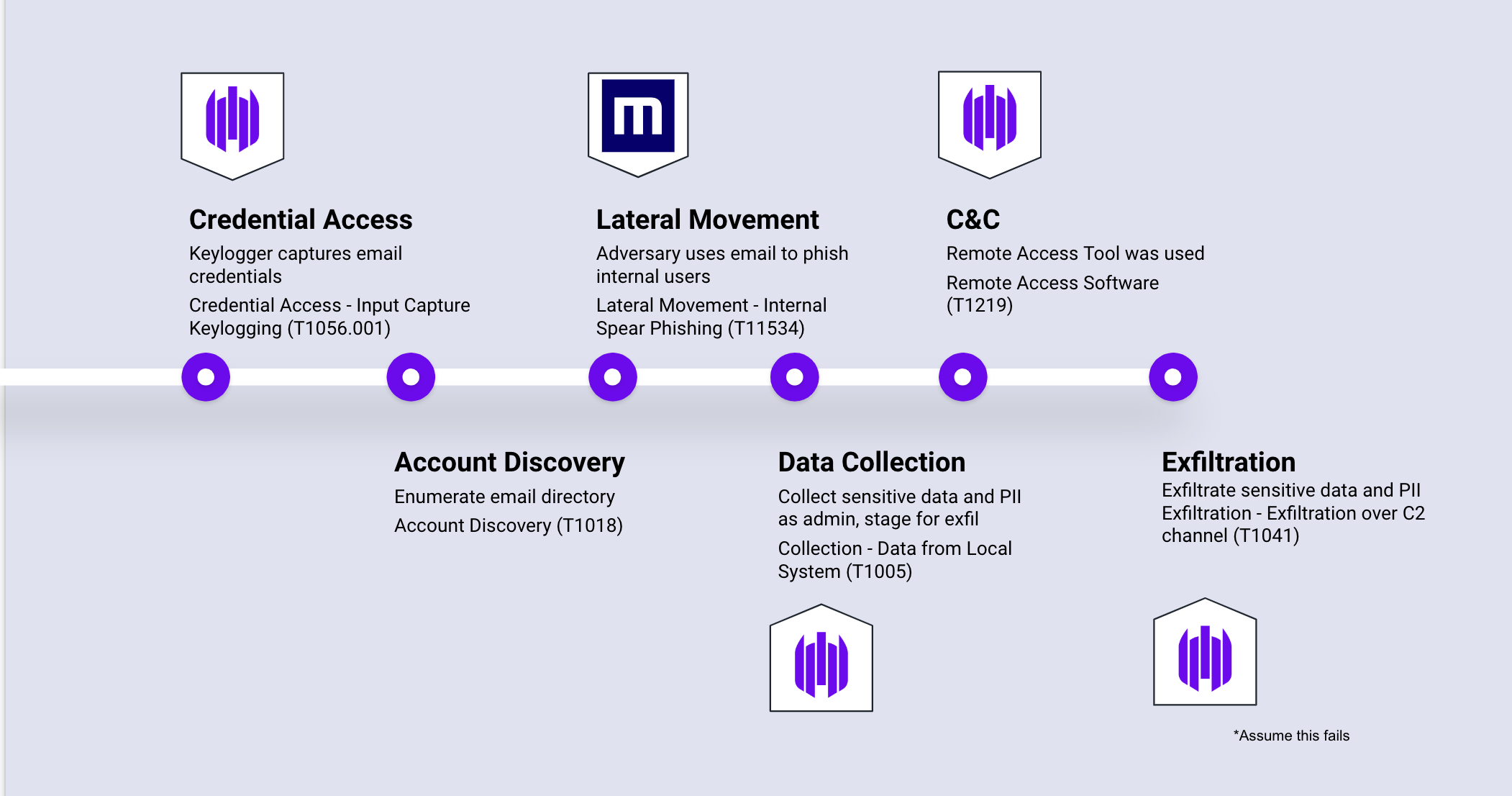
Sample Attack Timeline Without XDR Integration


Sample Attack Timeline With XDR Integration

Stopping Attacks Like LAPSUS$
Integrated solutions like the one from SentinelOne and Mimecast can stop prominent and damaging attacks like the recent LAPSUS$ attacks.
Threat actors such as LAPSUS$ take the time needed to research employees at a company they have decided to target. They first compromise the employee’s personal network and search for credentials that can be used to access corporate systems. This is particularly easy if the employee uses the same passwords for both their personal and private credentials. Even if the attacker does not find the credentials they are looking for, they can use the information they have already obtained to reset passwords and complete account recovery actions. Attackers like LAPSUS$ have even been known to call a company’s IT Helpdesk to attempt to get credentials reset.
The SentinelOne and Mimecast integration can stop attacks like LAPSUS$ by preventing them from moving laterally. The two solutions share information about threats that have been identified, reducing the likelihood that an attack will be successful. Security Awareness Training can also play an important part in thwarting attacks like LAPSUS$, giving employees an edge in identifying potential threats that can arrive in either their personal or work email.
The Bottom Line
Email security and XDR are the ideal pairing for security teams that are overtasked and struggling to keep up with alert volume and a never-ending stream of threats delivered via email. For more information about how your organization can benefit from this joint SentinelOne and Mimecast solution, read our joint solution brief.
如有侵权请联系:admin#unsafe.sh