2022-6-7 00:0:49 Author: www.sentinelone.com(查看原文) 阅读量:58 收藏
Researchers have recently noted the emergence of a new ransomware operator calling itself ‘Mindware’. The gang is thought to be responsible for a number of attacks beginning around March to April 2022, with suggestions that the malware was used to attack a not-for-profit mental health provider. Aside from targeting organizations in the Healthcare sector, Mindware has posted data on its leaks site belonging to organizations in sectors such as Finance, Engineering and Manufacturing. Mindware has a number of overlaps with an earlier ransomware strain known as SFile (aka SFile2, Escal). In this post, we review how Mindware differs from other ransomware families, note its similarities to SFile, and provide technical indicators to aid threat hunters and detection teams.

Overview
According to one source, the Mindware gang first became active in March 2022. By April, the group was practicing double extortion and operating its own leaks site. Mindware received further attention in April when it was noted by a different researcher to have attacked a mental health provider.
Mindware samples use a distinctive Reflective DLL injection technique. This, along with other indicators described below, show strong overlaps with SFile ransomware samples. Although we do not yet have specifics as to how Mindware attacks are initiated, SFile is known to use RDP bruteforce as an entry vector into an organization.
Each Mindware payload is configured for a specific target. Upon infection and successful execution, the payload drops a hardcoded ransomware note containing a combination of instructions and threats.

In common with a move made by other ransomware groups recently, Mindware attempts to discourage victims from contacting ‘recovery companies’, negotiators or authorities, threatening to immediately leak data should they do so. Victims are provided with a .onion URL as a means to make contact with the attackers and to decrypt two “random files” as proof that the operators possess a decryption key. Victims that refuse to pay are listed on the Mindware ransomware public leaks site.

Mindware Technical Analysis
As noted above, Mindware uses Reflective DLL Injection, a technique in which the shellcode dynamically retrieves handles to key API functions like LoadLibraryA() and GetProcAddress() by locating function addresses through the Export Address Table loaded by the host process.
This allows the shellcode to be position-independent by building its own import table and parsing through when executed in memory. This means a PE file could be loaded in the form of shellcode or a DLL entirely from memory.
The technique, which has also been noted in other ransomware families such as BlackMatter, avoids searching for module names directly and instead checks for hashes precalculated with a ROT13 algorithm.
Mindware and SFile samples require kernel32.dll and ntdll.dll. The APIs are searched for using a combination of the PEB (Process Environment Block) of the module and the EAT (Export Address Table) and enumerating all function names.

As noted, the same technique is characteristic of SFile ransomware samples, first seen in 2020 and active through 2021. Interestingly, SFile attacks seem to have been on hiatus over the last 9 months or so, and the emergence of Mindware samples with strong overlaps is indicative, as other researchers have noted, of a possible rebrand.
Both SFile and Mindware ransomware payloads accept the following parameters:
--enable-shares -> encrypt network shares
--kill-susp -> Triggers process termination
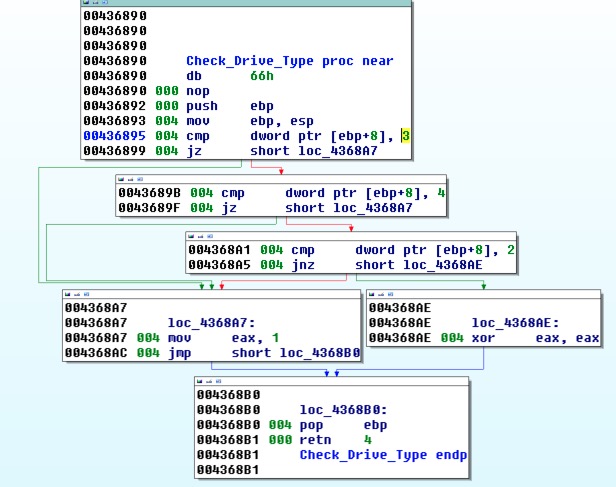
The ransomware checks for and then encrypts internal, removable and remote drive types.

Over 200 file types are targeted for encryption, denoted by a hardcoded list of file extensions. However, the following files are specifically excluded from encryption:
- autorun.inf
- desktop.ini
- ntuser.ini
- boot.ini
- iconcache.db
- thumbs.db
- bootfont.bin
- ntuser.dat
- bootmgr
- bootsect.bak
- ntuser.dat.log
- message_to_<<redacted>>.txt
- ! cynet ransom protection(don’t delete)
Similarly, files in the following locations are also excluded from encryption:
| %windir% | \all users\microsoft\ | \cache2\ |
| \google\ | \All Users\Microsoft\ | :\$RECYCLE.BIN\ |
| \Program Files\Internet Explorer\ | \far manager\ | \mozilla\ |
| \Roaming\Microsoft\ | \windows\system32\ | :\system volume information\ |
| \ida 7.0\ | \tor browser\ | \Local\Microsoft\ |
| \windows\syswow64\ | \Program Files\Microsoft Games\ | \ida 6.8\ |
| \windows.old\ | \Local Settings\Microsoft\ | \windows\system\ |
| \inetpub\logs\ | \Default\Extensions\ | \intel\ |
| \LocalLow\Microsoft\ | \windows\winsxs\ | :\boot\ |
| \Temporary Internet Files\ | \msocache\ | \Common\Microsoft\ |
| \System\msadc\ | :\drivers\ | \Temp\ |
| \perflogs\ | \Sophos\ | \Common Files\ |
| :\wsus\ | $windows.~bt | \ProgramData\Microsoft\ |
| \Symantec\ | \WindowsPowerShell\ | \cache\ |
| $windows.~ws | \Application Data\Microsoft\ | \Leaked\ |
| \Mozilla Firefox\ |
In order to protect itself and prevent other running processes from interfering with the encryption process, Mindware kills all other processes, with the exception of the following:
| explorer.exe | powershell.exe | rundll32.exe |
| vmnetdhcp.exe | vmware-authd.exe | vmware-hostd.exe |
| vmware-tray.exe | vmware-usbarbitrator.exe | vmware-usbarbitrator32.exe |
| vmware-usbarbitrator64.exe | webroot_updater.exe | werfault.exe |
| windowsupdate.exe |

SFile and Mindware samples are PEs typically around 250-300KB in size.
SFile and Mindware Ransomware Targeting
Analysis of the SFile payloads shows that SFile ransomware was mostly used against U.S organizations in Manufacturing, Mechanical, and Automobile sectors.
| SHA1 – SFile Samples | Targeted Sector/Industry |
| 28f73b38ace67b48e525d165e7a16f3b51cec0c0 | Automotive Engineering |
| bdb0c0282b303843e971fbcd6d2888d834da204c | Other Personal Services |
| 5ffac9dff916d69cd66e91ec6228d8d92c5e6b37 | Investment |
| 6960beedbf4c927b75747ba08fe4e2fa418d4d9b | Manufacturing |
| 665572b84702c4c77f59868c5fe4d0b621f2e62a | Insurance |
| a67686b5ce1d970a7920b47097d20dee927f0a4d | Retail |
| 14e4557ea8d69d289c2432066d860b60a6698548 | Sample has hardcoded org name as CCCR [parent organization could not be determined] |
| 0f20e5ccdbbed4cc3668577286ca66039c410f95 | Engineering |
Mindware samples also show a strong preference for businesses in similar industries.
| SHA1 – Mindware Samples | Targeted Sector/Industry |
| ae974e5c37936ac8f25cfea0225850be61666874 | Engineering |
| e9b52a4934b4a7194bcbbe27ddc5b723113f11fe | Healthcare |
| 9bc1972a75bb88501d92901efc9970824e6ee3f5 | Manufacturing |
| f91d3c1c2b85727bd4d1b249cd93a30897c44caa | Finance |
| 46ca0c5ad4911d125a245adb059dc0103f93019d | Engineering |
How To Protect Against Mindware and SFile Ransomware
The SentinelOne Singularity platform detects and prevents execution of Mindware and SFile ransomware strains.

For organizations not currently protected by SentinelOne, please see the list of Indicators of Compromise at the end of this post and the technical indicators described above.
Conclusion
Indications suggest Mindware is likely a rebrand of SFile, or at least that the same source code or builder for SFile is available to Mindware operators. While neither strain has achieved the notoriety of some of the more well-known ransomware strains that have been circulating recently, it may be that flying under the radar and hitting selective targets without attracting too much public attention is exactly what the gang are aiming for.
We hope that the information in this post serves to enable security teams to ensure that they have adequate resources to detect and prevent this threat. The SentinelOne Singularity platform detects and protects against SFile, Mindware and all other known ransomware threats. For more information about ransomware protection, see here. To learn more about how SentinelOne can help protect your organization from ransomware and other threats, contact us or request a free demo.
Indicators of Compromise
Mindware Onion Address
https[:]//dfpc7yvle5kxmgg6sbcp5ytggy3oeob676bjgwcwhyr2pwcrmbvoilqd[.]onion/
Mindware Samples, SHA1
ae974e5c37936ac8f25cfea0225850be61666874
e9b52a4934b4a7194bcbbe27ddc5b723113f11fe
9bc1972a75bb88501d92901efc9970824e6ee3f5
f91d3c1c2b85727bd4d1b249cd93a30897c44caa
46ca0c5ad4911d125a245adb059dc0103f93019d
Mindware Samples, SHA256
c306254b44d825e008babbafbe7b07e20de638045f1089f2405bf24e7ce9c0dc
00309d22ab53011bd74f4b20e144aa00bf8bb243799a2b48f9f515971c3c5a92
32c818f61944d9f44605c17ca8ba3ff4bd3b2799ed31222975b3c812f9d1126c
81828762ebe7ea99b672c8ac07dc3c311487a5a246db494c7643915f6c673562
d1a0a2dc26603b2e764ee9ab90f3f55a2f11a43e402dd72f4a32a19b0ac414b5
MITRE ATT&CK
TA0005 – Defense Evasion
T1485 – Data Destruction
T1486 – Data Encrypted for Impact
T1027.002 – Obfuscated Files or Information: Software Packing
T1007 – System Service Discovery
T1059 – Command and Scripting Interpreter
T1112 – Modify Registry
TA0010 – Exfiltration
T1018 – Remote System Discovery
T1082 – System Information Discovery
如有侵权请联系:admin#unsafe.sh