In this post, you'll learn how to get started using the Falco tool to examine logs of harmful activity in containers.
Hello, world! Once the running container is deployed there is only one way I have discussed so far using the docker diff tool to look for file changes. There are some actions that don't require any operation on the files, for example, file-less malware, running a privileged container after you got access to the docker socket or starting an exec instance for a running container.
How would we detect these actions? Have they even logged anywhere? Well, the answer is quite long but I will try to give you an overview of this. When you start the Falco via docker image, you provide it privileged access to insert the kernel modules and then they take care of syscall execution via docker engine.
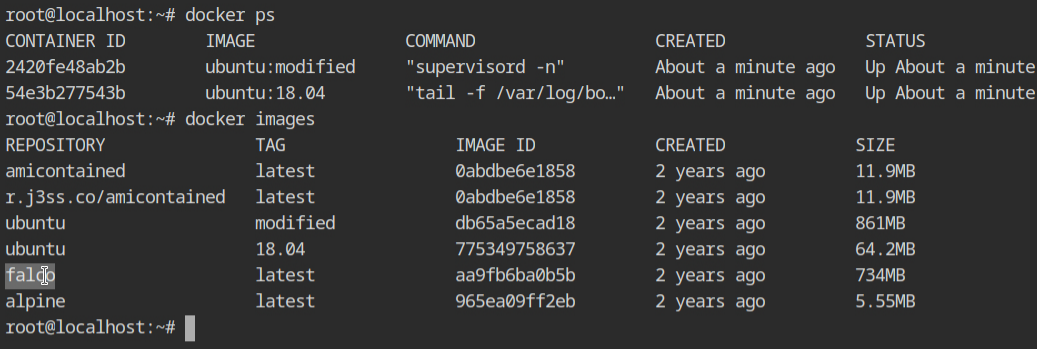
In this lab, the falco image is provided to us, although it is 2 years old. There are two containers already running.
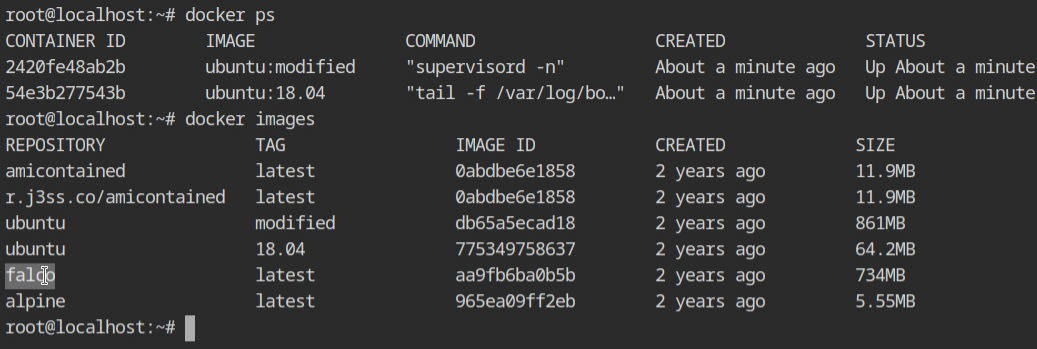
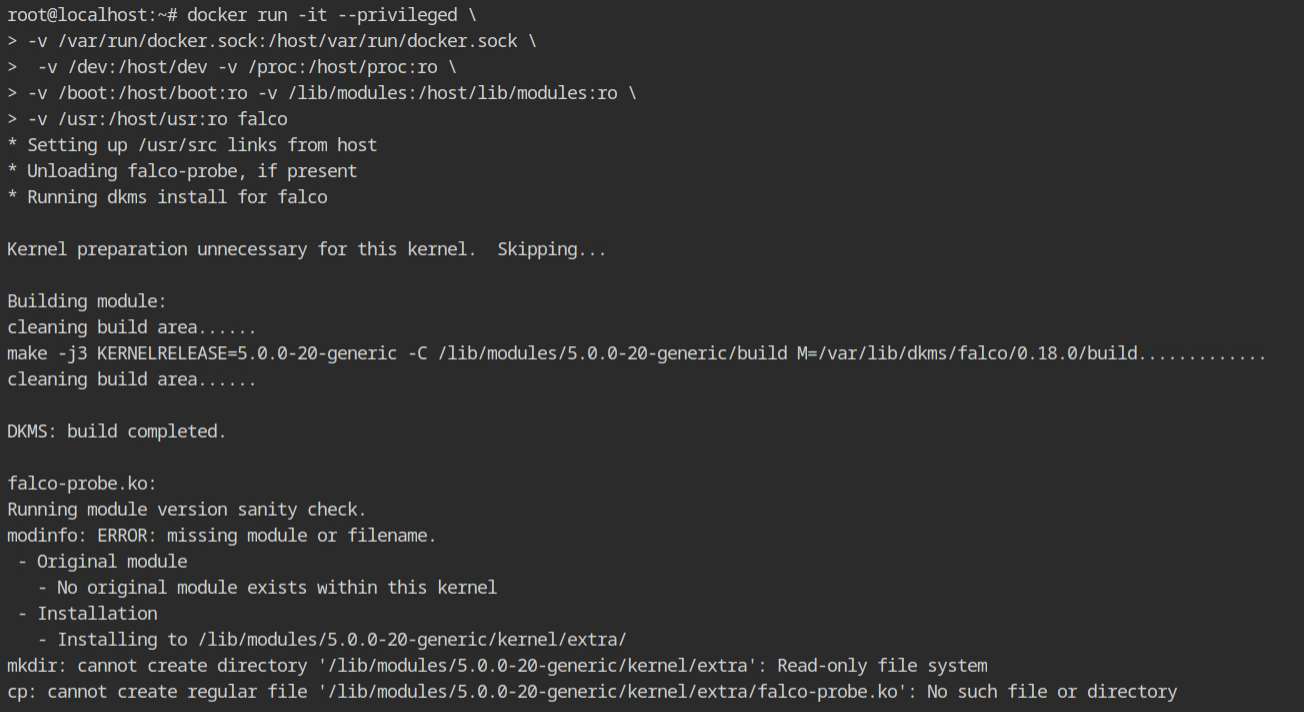
falco image and list running containersStart the container with falco image as described in the lab description and wait for it to load the kernel modules and initialize its monitoring modules.
This shouldn't take much time if you see the message "Kernel prepration unnecessary for this kernel. Skipping...".
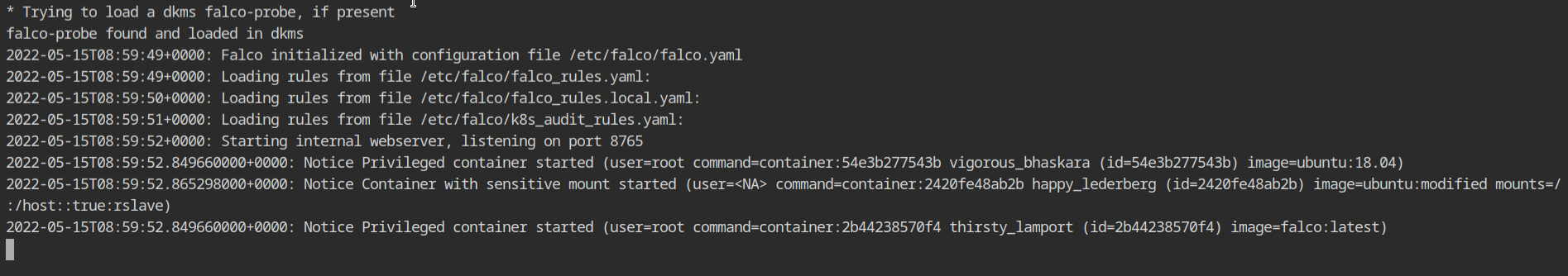
falco imageOnce the Flaco is up and running you will see some initial logs with the message "Privileged container started". These can be ignored for now because a privileged container is required for the Flaco.
Now head over to another browser for the ttyd shell and exec into any container with the privileged shell. Here I used docker exec -it --privileged 2420fe48ab2b bash.
Now try to access the contents from the normal files like .bashrc or /etc/passwd and then read the contents from /etc/shadow and so on. You will not be blocked for doing all such activities but there will be logs printing on the previous ttyd session with reference to such actions and the file names.
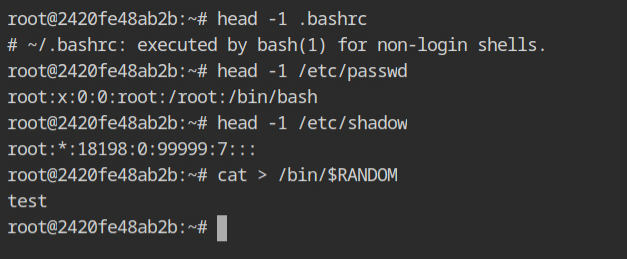
/bin directoryAs you can see, when the exec session was created it was logged with all the required details like the current user, shell name, parent process responsible for spawning it and the container id and its name.
Below that there will be logs of sensitive files read on /etc/shadow file and sensitive write operation on the /bin/$RANDOM file.
I first tried accessing /etc/shadow file before capturing the previous screenshot. So that is why you are seeing two mentions of read operation on that file.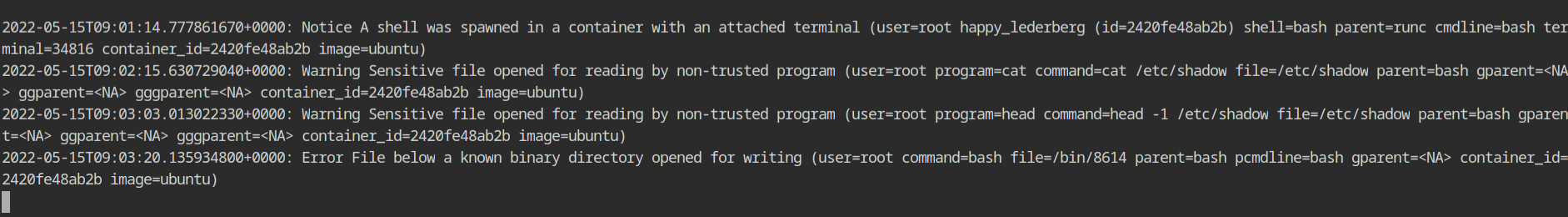
All these detections are based on the rules defined in the rules config file which is located in the /etc/falco directory which exists in the container. There are multiple files and all of them are currently included by the Falco tool (can be verified by the falco.yaml configuration)
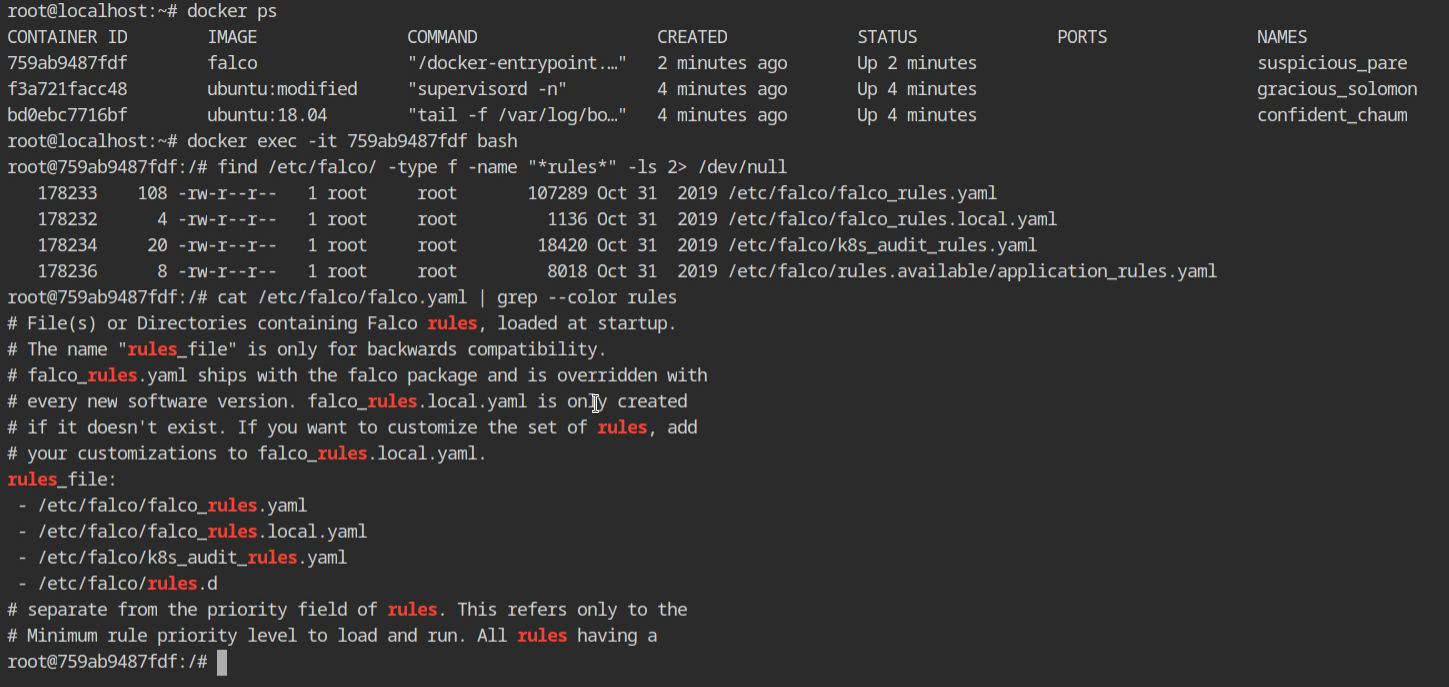
The "binary directory opened" string may be found in the /etc/falco/falco rules.yaml file, which contains both the detection and reporting logic.
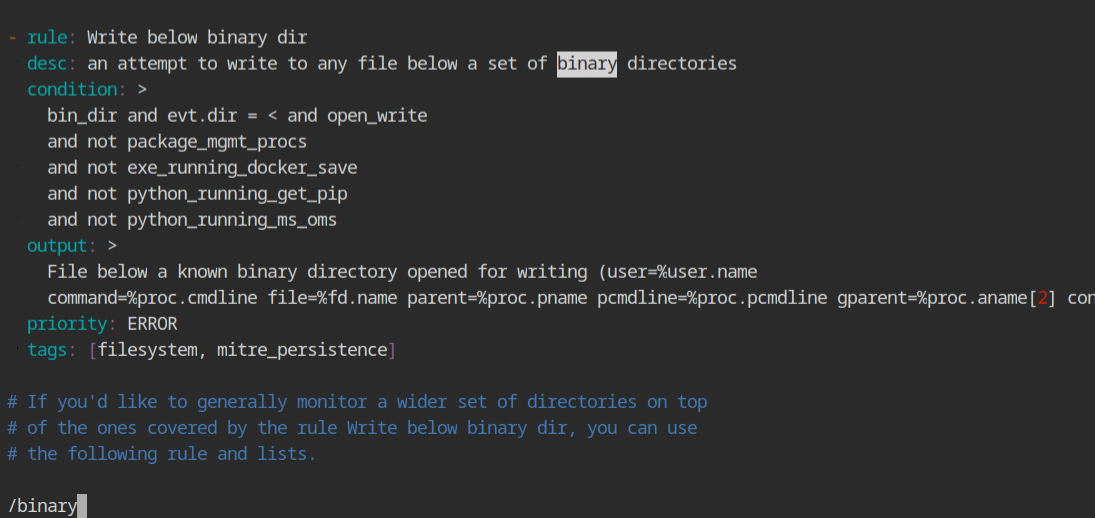
/bin directory💡
Surprisingly, it can also be configured to send alerts via email, SNS, or even a Slack channel. Check out the alert configuration for more – https://falco.org/docs/alerts/.