Apple ecosystem includes a comprehensive backup ecosystem that includes both local and cloud backups, and data synchronization with end-to-end encryption for some categories. Today we’ll discuss the iCloud backups, particularly targeting issues that are not covered in the official documentation.
Apple describes backups of both types in Backup methods for iPhone, iPad and iPod touch; some information specific to iCloud backups is published in How to back up your iPhone, iPad, and iPod touch with iCloud. Let’s start with basic information, and then proceed with some technical data and tips & tricks.
User experience
iCloud backups are enabled by default, along with the many synchronization options. Please note:
- Almost the same risks are imposed by iCloud synchronization, which is silently enabled by default.
- Everyone should have a recovery plan for lost or broken devices. Remember, your data can be either unique or valuable: if you don’t have a backup, you don’t value that data at all.
Another issue is that Apple only provides 5 GB of iCloud storage for free, and that’s definitely not enough to keep a full device backup. Once you are over your free cloud quota, further backups cannot be created. Since iOS 15, however, Apple offers an iCloud+ plan with lots of benefits, including 50 GB of cloud storage at a very fair price.
iCloud backups, when enabled, are created automatically when all of the following conditions are met:
- The device is connected to a power source, and
- The device is connected to Wi-Fi network, and
- The screen is locked.
The backups are created once a day, usually around 2 AM. Creating the initial (full) backup takes some time, while subsequent (differential) backups are created much faster as they are incremental, and only the changes are being uploaded.
In the past, Apple used to keep three backup snapshots regardless of the user’s iCloud plan. There was no setting to adjust the number of snapshots. These days, only two most recent snapshots are stored.
A fresh iCloud backup can be created manually by tapping the Back Up Now command in the Settings app. In this mode, the phone does not need to be connected to a power source, yet a Wi-Fi connection is still required. iOS 16 adds the ability to create backups using your mobile plan.
There are a few other things worth mentioning. Apple only provides some very basic backup management. By logging in to an iCloud account (or accessing backups from any logged-in device), you can only see the list of backups including device name and last backup date and size. You can also delete individual backups by device. No other options are available. You can restore a new device from almost any backup (the iOS version on the device being restored should be the same or newer than the OS version of the original device). Note that you can only restore from a cloud (or local) backup during the initial device setup (for new devices or devices after a factory reset).
What’s inside
There is almost no documentation on iCloud backups content. In What does iCloud back up? Apple says:
Here’s what iCloud Backup includes
- App data
- Apple Watch backups1
- Device settings
- Home screen and app organization
- iMessage, text (SMS), and MMS messages2
- Photos and videos on your iPhone, iPad, and iPod touch2
- Purchase history from Apple services, like your music, movies, TV shows, apps, and books3
- Ringtones
- Visual Voicemail password (requires the SIM card that was in use during backup)
The other one mentions something slightly different:
iCloud backups include nearly all data and settings stored on your device. iCloud backups don’t include:
- Data that’s already stored in iCloud, like Contacts, Calendars, Notes, iCloud Photos, iMessages, Voice Memos, text (SMS) and multimedia (MMS) messages, and Health data
- Data stored in other cloud services, like Gmail and Exchange mail
- Apple Mail data
- Apple Pay information and settings
- Face ID or Touch ID settings
- iCloud Music Library and App Store content
I would say that iCloud backups contain about the same set of data as local (iTunes-style) backups without a password, yet there is a notable difference:
Your iPhone, iPad, and iPod touch backups only include information and settings stored on your device. They do not include information already stored in iCloud such as Contacts, Calendars, Bookmarks, Notes, Reminders, Voice Memos, Messages in iCloud, iCloud Photos, and shared photos. Some information is not included in an iCloud backup but can be added to iCloud and shared across multiple devices like Mail, Health data, call history, and files you store in iCloud Drive.
So, local backups do contain all of the above, but iCloud backups miss at least media files, messages and voice memos if the user enables iCloud sync; see Set up and use iCloud Photos and Use Messages in iCloud. Software such as Elcomsoft Phone Breaker allows downloading this data directly from iCloud. Just note that messages and voice memos use “end-to-end encryption” (see iCloud security overview); in order to decrypt them, you need the passcode of one of the trusted devices in addition to the user’s iCloud credentials.
Also, iCloud backups do not include call logs, Safari browsing history and Health data; this data is synced directly through iCloud (call logs appear to sync directly across devices; they may be the only category that cannot be extracted from the cloud, even if you have all credentials including the second authentication factor and the passcode, and even the trusted device itself).
Finally, the keychain. The keychain is included in iCloud backups; it can be downloaded along with the rest of the data; however, you’ll be unable to decrypt it as it is encrypted with a device-specific key that cannot be extracted even from the device itself. However, the keychain can be also being synchronized through iCloud; see Set up iCloud Keychain for more details. iCloud keychain also uses end-to-end encryption, yet Elcomsoft Phone Breaker can download and decrypt it.
The technical side
iCloud has a very complex structure; I’d say it is not just a cloud service but an ecosystem. All the files are stored in third-party datacenters all over the world. Some servers are hosted by Google, Amazon, Microsoft, and others; Apple’s own infrastructure is also there, but the company does not have a lot of physical servers. The data is split into chunks of variable size, and every chunk is encrypted using its own key. The keys are exclusively stored on Apple-owned servers.
As this topic is slightly outside of scope of this article, please watch our presentations to get more details on iCloud internals (protocols, encryption etc.):
- Cracking and analyzing iCloud protocols
- Advanced Smartphone Forensics
- Breaking into the iCloud Keychain
- iCloud syncing and 2FA
- iCloud Security: What if someone gets your password?
Acquisition
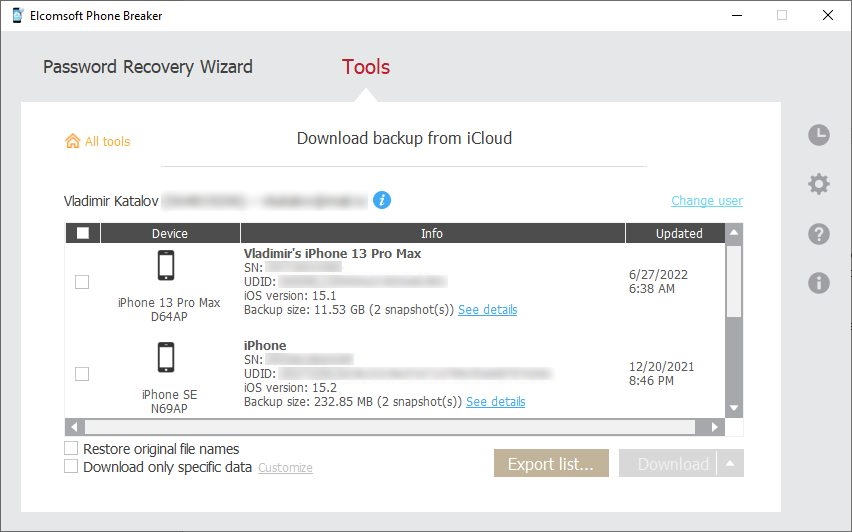
While Apple dos not provide the ability to download a cloud backup, you’ll have to resort to third-party tools such as Elcomsoft Phone Breaker for obtaining a copy of the data without restoring a new Apple device (and attempting to extract the data from the device afterwards). We were the first who implemented this feature almost 9 years ago (the news came out in August 2013).
At that time, iCloud security was much lower than it is now. For example, there was no two-factor authentication for backups; also, we have discovered a way to access backups without an Apple ID and password by using an authentication token that can be easily extracted from a Windows or macOS desktop logged into the same iCloud account.
Since then, Apple learned their lessons, and current iCloud backups are more difficult to download and to decrypt.
The (not so) fun side
Quite a few Apple users never enable iCloud backups because of privacy and security concerns. These are valid concerns. There were several cases related to iCloud hacks; here are just a few:
- 2014 celebrity nude photo leak
- Hackers sell information from Medvedev’s gadgets
- La Puente man steals 620,000 iCloud photos in plot to find images of nude woman
And that’s not only about stealing someone’s credentials and downloading iCloud data using third-party software. Apple, under certain circumstances, hands the data to law enforcement officials; see Examining a Leaked Criminal Warrant for Apple iCloud Data in a High Profile Case (part one, part two) for example.
Conclusion
Let me speculate about the future. I believe Apple will eventually get rid of local (iTunes-style) backups entirely, leaving iCloud backups as the only option. This may or may not coincide with the removal of the Lightning port from iPhones. Whether you are using iCloud backups or not, educate yourself about the security risks:
- Acquiring and Utilizing Apple ID Passwords, Mitigating the Risks and Protecting Personal Information
- Apple vs. Google: If you get hacked, which account could be bigger trouble?
REFERENCES:
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
如有侵权请联系:admin#unsafe.sh