Microsoft has made it a bit harder for macro viruses to proliferate with a recent change to its default macro security policies.
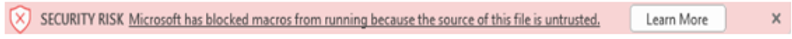
Malware-infected Microsoft Office macros have been around for close to three decades. These exploits involve inserting code into a seemingly innocuous Word or Excel macro, which is then downloaded by an unsuspecting user by clicking on a phishing lure or just a simple misdirected email attachment. That link above will take you to a more detailed explanation of how they work and why they have been so hard to stop. The good news? We may have finally turned a corner in the fight against this malware. Microsoft has made it a bit harder for macro viruses to proliferate with a recent change to its default macro security policies. The change is only for the Windows-based Office applications Access, Excel, PowerPoint, Visio, and Word. It's now being rolled out across various versions of Office. Before we get into what has changed, you should know that macro-like malware is still an issue. About a month ago, a new zero-day vulnerability named Follina was reported. It exploits Word’s Remote Template feature and can remotely execute PowerShell commands. The name comes from the area code of an Italian town, a number that was found by researchers embedded in the malware's code. It will work if users download the document and are running older Office versions. Researchers have found evidence of Follina being deployed since last October. While technically not a macro, it's another clever way that hackers have figured out how to worm their way into a network. The changes to this setting are easy to spot. If you clicked on a macro before, you got a warning such as this: But once the new setting is applied, this is what you see: That's great for the default setting, but what if you still need to use legit macros? One IT manager that I spoke to told me that he can’t turn off macros by default because they are used by too many people across his organization for actual purposes, such as running their CRM system. This is a very typical situation, and it's one of the reasons why it has taken Microsoft so long to address the macro malware issue — because they are too useful, and thus are part and parcel to many employees’ productivity. Microsoft has two group policy settings available to unblock internet-sourced macros: the Block macros from running in Office files from the internet policy and the VBA Macro Notification Settings policy. There is still a great deal of work to set this up, since the policies have to be configured for each individual Office application. Not quite, as Follina has illustrated. You still need to be on the lookout for these instances of macro-style malware. As a rule of thumb, don’t click on anything that you get online without at least some protection installed on your computer. What has Microsoft done to help protect against rogue macros?


So are we in the clear completely?
如有侵权请联系:admin#unsafe.sh