2022-7-10 03:30:8 Author: infosecwriteups.com(查看原文) 阅读量:34 收藏

Hi, Everyone. hope you’re well. I’m Aziz. Through this write-up, I will share some security issues I’ve found on the official Voter ID card maintaining platform http://nvsp.in. I was filling out a correction form for my mom’s card, I’m not really interested in finding bugs on gov websites :`) that moment burpsuite was running in the background and I thought let's have a try. After spending half an hour I found some critical issues that I’m going to share. All these issues are already fixed by the government.
In India, a Voter ID card is an identity document issued by the Election Commission of India to adult domiciles of India who have reached the age of 18, which primarily serves as an identity proof for Indian citizens while casting their ballot in the country’s municipal, state, and national elections. More than 780 million Voter IDs are active at present.
While registering a new account it shows two options “I have EPIC number” and “I don’t have EPIC number”. EPIC stands for Electors Photo Identification Card and the EPIC number is nothing but Voter ID no. If we chose we don’t have a Voter ID number then they will give you an option to add after registering on the portal. After registration, I tried to add any random EPIC no. with my account but it show it's not valid. So I sent that HTTP request to burp intruder for brute-forcing.

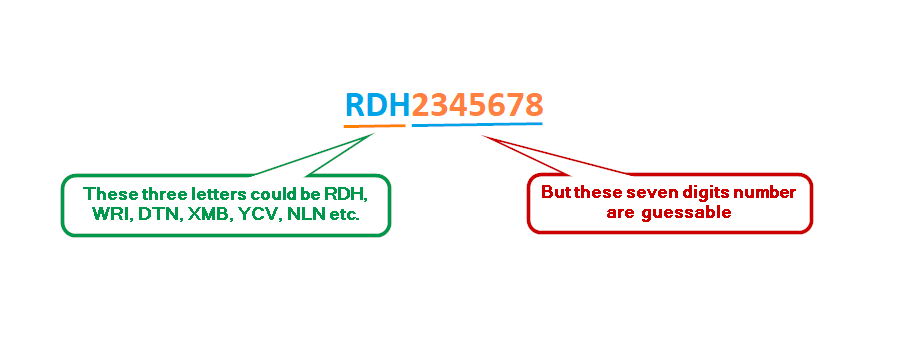
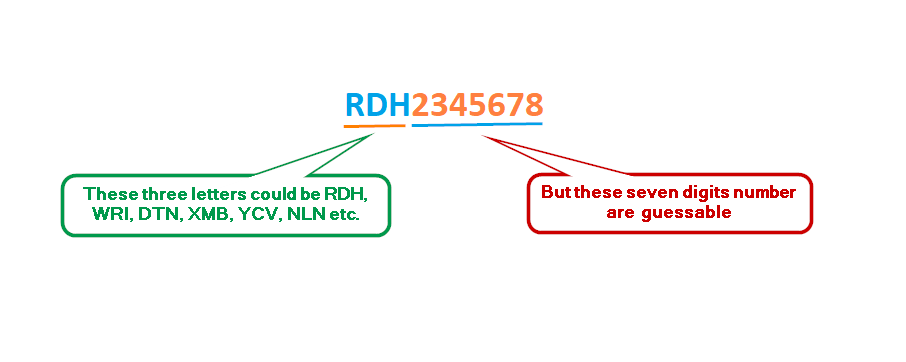
A Voter ID also known as EPIC number is an alphanumerical ID, it contains three Alphabets at starting and seven numbers i.e. WRI2345678, RDH2345678, DTN2345678, YCV2345678, NLN2345678, XMB2345678, etc. These three alphabets are Not random alphabets, you can find similar IDs with similar these three alphabets in beginning but the rest seven digits are different.
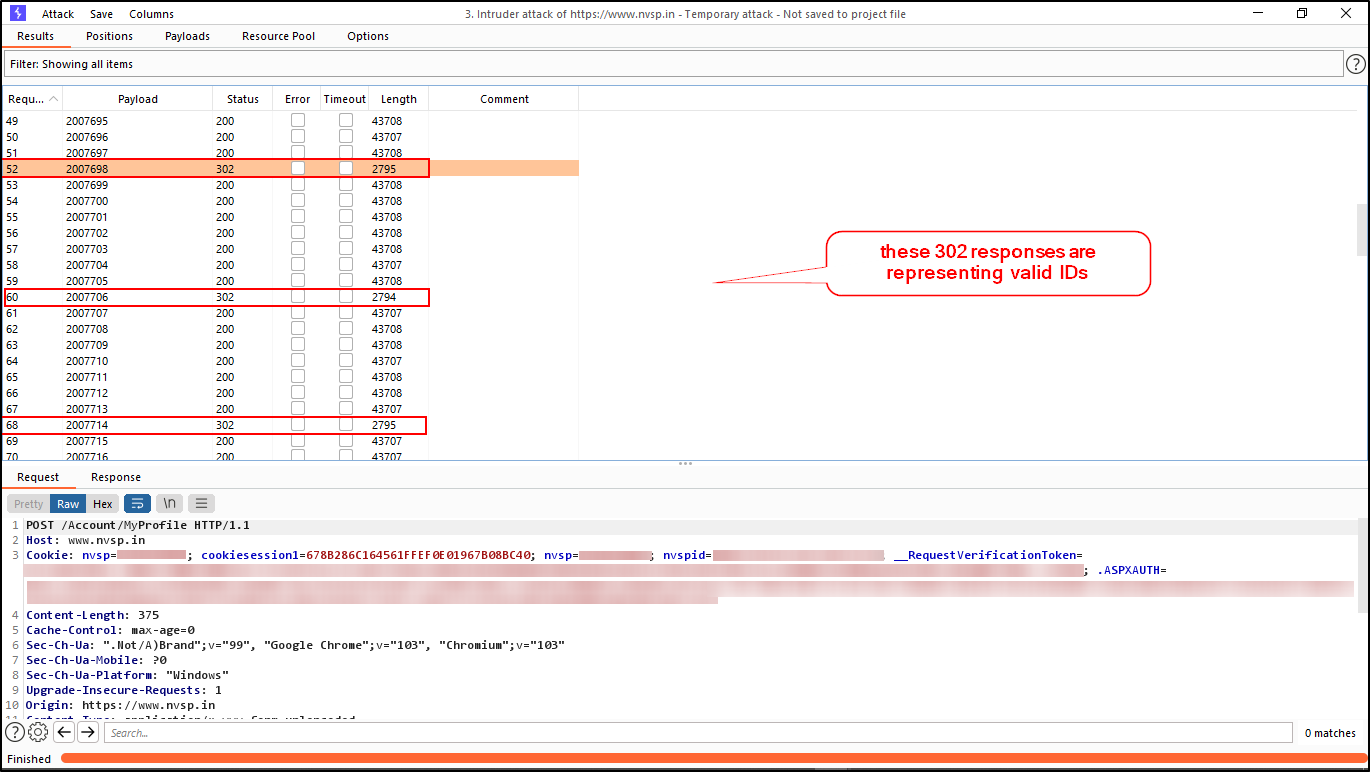
I added the payload position on these seven-digit numbers on`Epic_no=` parameter i.e “ Epic_no=WRI$2345678$ ” (as you can see in the below screenshot.)

Surprisingly there is no limitation implemented in the backend and I was able to send unlimited requests without getting blocked by firewall. As a result backend server responding 302 redirections for every valid voter ID. (As shown in the screenshot below)
Then I wrote a python script that will brute force the values and give output all valid voter_IDs for me.

Now I have valid Voter IDs of random persons then, I added these IDs with my profile under “/Account/MyProfile”. Then there is an option under the “/forms/”section which is form001 and this form is already filled with Name, father’s name, address, Date of birth, etc. according to that valid EPIC ID added to my profile.

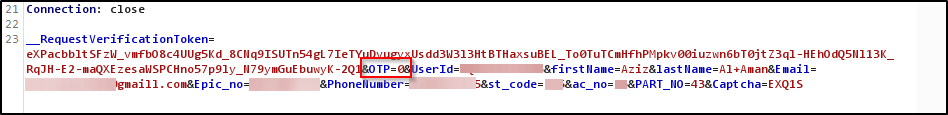
On the profile details updating section I was trying to add another user's number. So I created another account for it. But there was an OTP implanted there, and I tried to brute-force it but it didn’t work :( I remember reading an article last year, you can read it here, where the author just added 0 after intercepting the request. And I did the same thing here on OTP parameter and it worked :)

After bypassing I thought it just can register the victim’s number then I’ll reset the password, But surprisingly on replacing the victim’s number my profile data automatically changed with the victim’s details, And I can own his account.

From the 1st bug, we can get and add any random user’s Voter ID to our account, From that on the home page there is an option for “Deletion of Enrolment”. And nothing to be needed after an attacker added any random Voter ID on his profile section. then he can easily delete any random user’s Voter ID permanently.

I reported these three issues to [email protected] and they fixed these issue
I hope you liked this article, If you have any questions then you can dm me on Twitter: https://twitter.com/nxtexploit
Thanks for reading,
如有侵权请联系:admin#unsafe.sh