2022-7-13 08:0:0 Author: www.trustwave.com(查看原文) 阅读量:20 收藏
Decade Retrospective: The State of Vulnerabilities
The Spanish philosopher George Santayana is credited with the aphorism “Those who cannot learn from history are doomed to repeat it.” This statement is particularly true when it comes to cybersecurity. Threat actors reuse well-known and previously patched vulnerabilities and attempt to take advantage of organizations making the same error over and over. So, if one does not know what has recently taken place it leaves you vulnerable to another attack.
With that in mind the Trustwave team believed this was a suitable time to take a minute and review some of the watershed moments that had a major impact on cybersecurity between 2011 and 2021.
Tremendous Growth in Reported Vulnerabilities Over the Past Few Years
It is difficult to tell the complete story about the network security landscape from the past decade because security tools and event loggers have evolved so much recently that many of the metrics that we take for granted today simply did not exist 10 years back. Nevertheless, the data that is available provides enough information to spot some significant trends. The most obvious trend, based on sources like the National Vulnerability Database (NVD), Exploit-DB, VulnIQ, and Trustwave’s own security data, is that security incidents and individual vulnerabilities have been increasing in number and becoming more sophisticated.
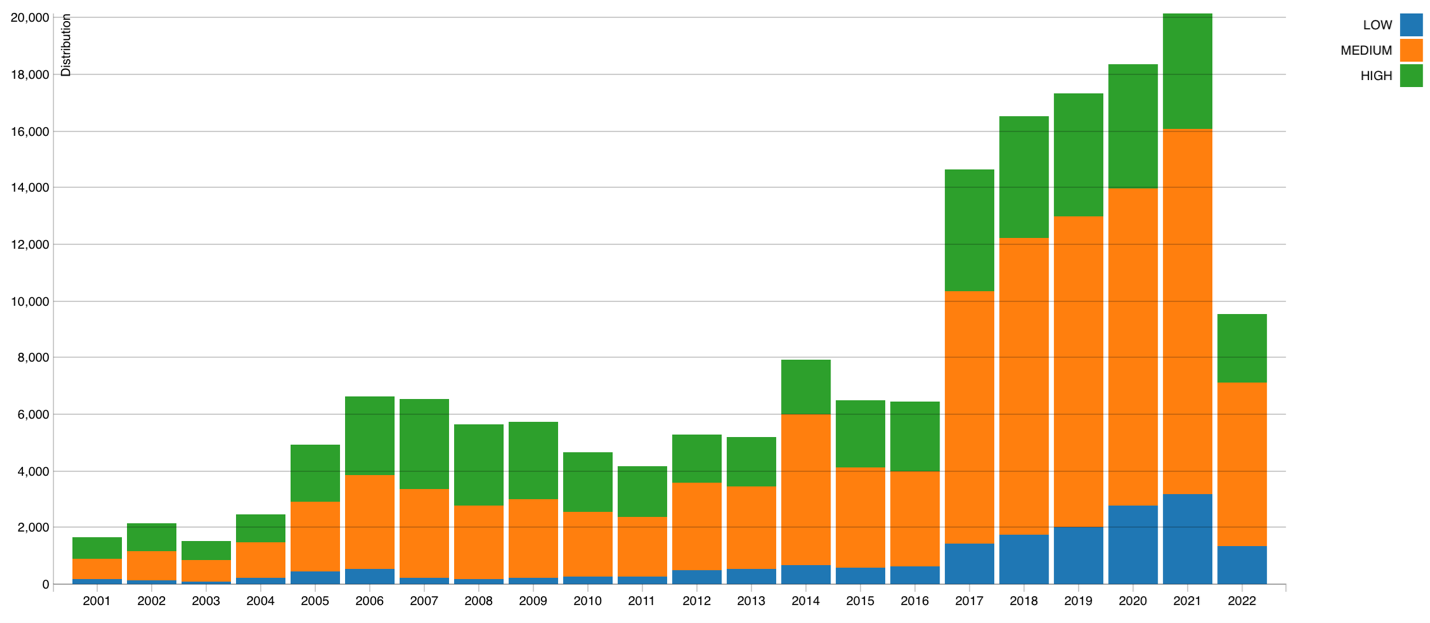
Figure 1: Vulnerability Severity Distribution over time (Source: NVD)
The chart above shows a steady increase in the number of vulnerabilities reported to NVD from 2011 through 2016, followed by an exponential increase in 2017 and then a continued increase every year thereafter. The surge in 2017 may have come from a more extensive collection of software products being catalogued in NVD. However, it is significant to note that web application exploits have dominated the decade as seen in the chart below (See Figure 2).
Figure 2: Exploits by Type over the decade (Source: Exploit-DB)
Ports 80 and 443 lead the list of commonly open ports, so it is no surprise that web application exploits dominated the decade. Reviewing CWE over time (Figure 3), CWE-79, aka ‘XSS,’ seemed to be the flaw that was high on the list every year.
Our pick of top 10 network vulnerabilities that defined the decade
With over 100,000 tracked vulnerabilities on NVD from 2011 to 2021 and a wide range of vendors/products involved, choosing 10 of the most egregious network security flaws was not easy. It was also not feasible to call out and list all vulnerabilities that threatened the IT world in the past decade, However, with that said, here is our pick of the 10 most (in no particular order) prominent and notable network security issues and breaches that won’t be forgotten.
- SolarWinds Hack and FireEye Breach
Date of Detection: December 8, 2020 (FireEye)
Date of Initial Patch: December 13, 2020
Current Status: ACTIVE
Infected servers currently exist, and attacks still take place due to companies being unaware of dormant attack vectors set up before patch.
The most crippling and devastating breach of the decade was the cyberattack on SolarWinds Orion, a network monitoring tool. In December 2020, the cybersecurity company FireEye disclosed that hackers had stolen the firm’s “red team tools” and internal threat intelligence data. Days later, reports of a suspected nation-state cyberattack of SolarWinds Orion dominated the cybersecurity headlines. Various corporations and U.S. government agencies were victims of this supply chain attack. The hackers planted a malicious backdoor update, dubbed SUNBURST into ~18,000 customers granting the attackers the ability to modify, steal and destroy data on the networks. FireEye also released countermeasures to reduce the effectiveness of the red team tools along with a list of vulnerabilities that were exploited by the The breach was discussed in Trustwave’s Network Security 2020 Roundup. Please refer to https://www.trustwave.com/en-us/resources/library/documents/2021-network-security-report/ for more information.
- EternalBlue exploit and the ransomware saga
Date of Detection: April 14, 2017, (initial leak)
Date of Patch: March 14, 2017 (Patched after NSA alerted Microsoft)
Current Status: ACTIVE
Shodan, a popular search engine for Internet-connected devices, currently lists more than 7,500 vulnerable systems. (See Figure 4)
Figure 4: Shodan findings for EternalBlue (Source: Shodan.io)
Another big story that dominated headlines was in 2017 when several new and significant exploits were stolen from the U.S. National Security Agency (NSA), leading to the highly damaging WannaCry and Petya ransomware outbreaks. In April 2017, the hacking group Shadow Brokers leaked several hundred megabytes of alleged NSA material, including multiple Windows exploits and a framework called FuzzBunch that could be used to load the exploit binaries onto computers. Several of the most serious exploits targeted vulnerabilities in the Server Message Block (SMB) protocol used for local network communication in various versions of Microsoft Windows.
The most significant exploit, dubbed EternalBlue, targeted a vulnerability identified by CVE-2017-0144 that Microsoft had patched one month prior to the Shadow Brokers’ leak. In May 2017, the world was rocked by a new ransomware family that spread across the globe at nearly unprecedented speed. Dubbed WannaCry, the ransomware used the EternalBlue exploit along with other leaked NSA tools to propagate itself to more than 200,000 computers in more than 150 countries that had not applied the MS17-010 security update. Among the largest victims of the attack was the United Kingdom’s National Health Service (NHS), which lost control not only of desktop workstations but also of critical medical equipment.
One month later, in June 2017, a second ransomware attack used the EternalBlue exploit to cripple thousands of computers, mostly located in Ukraine. This time the culprit was an updated version of Petya, an older ransomware family, which had been modified to use EternalBlue for self-propagation. Dubbed “NotPetya” for its differences from the original Petya, this new variant was a highly destructive worm that overwrites the computer’s master boot record with a custom bootloader that displays its ransom notes, making a full recovery difficult or impossible. Upon reviewing a sample of scan results, EternalBlue is the most detected vulnerability on our customer networks. (See Figure 5)
- Heartbleed
Date of Detection: March 21, 2014
Date of Patch: April 7, 2014
Current Status: ACTIVE
Currently more than 200,000 vulnerable systems are found on Shodan.
In 2014, security researchers discovered a serious flaw (CVE-2014-0160) in OpenSSL, the encryption technology that secures the web. The vulnerability was dubbed Heartbleed, because the bug existed in OpenSSL's implementation of the TLS/DTLS (transport layer security protocols) heartbeat extension (RFC6520) and allowed anyone on the Internet to read the memory of the systems. The discovery of this vulnerability created a worldwide panic because more than 65% of servers used OpenSSL, and experts labeled this as one of the worst security bugs in the Internet’s history. Six years later, this vulnerability continues to be targeted by attackers due to the volume of unpatched public-facing servers. Running a quick report on Shodan returns over 200,000 vulnerable installations (See Figure 5).
Figure 5: Hosts on Shodan vulnerable to Heartbleed (Source: Shodan.io)
- Shellshock: Remote Code execution in BASH
Date of Detection: September 12, 2014
Date of Patch: September 24, 2014
Current Status: INACTIVE
Last exploited with the Sea Turtle Campaign.
Another vulnerability that garnered wide attention in 2014 was Shellshock. Shellshock (CVE-2014-7169) is a bug in the “Bourne Again Shell” (Bash) command-line interface and existed for 30 years before its discovery in 2014. The vulnerability was considered even more severe than Heartbleed since it allowed an attacker to take complete control of a system without having a username and password. Exploitation is trivial and given the fact that the Bash environment is used in several configurations, including CGI, ssh, rsh and rlogin, this meant all those services were affected by the bug. Five years later, the vulnerability campaign called “Sea Turtle” used DNS hijacking to gain access to sensitive systems. Shellshock was one of the vulnerabilities used for successful attacks.
- Apache Struts Remote Command Injection & Equifax breach
Date of Detection: March 6, 2017
Date of Patch: September 5, 2017
Current Status: INACTIVE
Another noteworthy exploit from 2017 was CVE-2017-5638, a critical zero-day vulnerability affecting the Jakarta Multipart parser in Apache Struts 2, a web application development framework. This vulnerability allowed remote command injection attacks by incorrectly parsing an attacker’s invalid Content-Type HTTP header. Shortly after it was disclosed, Apache issued emergency security patch S2-045 for the vulnerability. Months later, credit reporting giant Equifax announced that hackers had gained access to company data, potentially compromising sensitive information for 143 million people in the U.S., UK, and Canada. The compromised data included driver’s license and Social Security numbers. Later analysis of the attack revealed that hackers accessed Equifax systems from May 2017 through July 2017, using CVE-2017-5638 as the initial attack vector.
Figure 6: Chart showing a sample of scan results for vulnerabilities in our Top 10 list
- Chipocalypse: Speculative Execution Vulnerabilities Meltdown & Spectre
Current Status: INACTIVE (No exploit found in the wild)
In early 2018, security researchers disclosed significant vulnerabilities in the CPUs that run most of the world’s computers. These flaws were dubbed Meltdown and Spectre and belong to a class of flaws called speculative execution vulnerabilities.
To improve performance, modern CPUs are designed to anticipate and execute certain instructions before they are requested. In some cases, an attacker can exploit this feature to gain access to data stored in the memory of other running programs, which is ordinarily not allowed. Meltdown (CVE-2017-5754) breaks the mechanism that keeps applications from accessing arbitrary system memory. Spectre (CVE-2017-5753 and CVE-2017-5715) tricks other applications into accessing arbitrary locations within their memory. Both attacks use side channels to obtain the information from the targeted memory location. The vulnerable speculative execution techniques have been used by all modern mainstream CPUs since the 1990s, which made for an attack surface of extraordinary size.
Unfortunately, because the vulnerabilities result from the fundamental design of the processor rather than badly written code, they can’t be effectively mitigated in software without impacting the processor’s performance to some degree. So, while microcode fixes are available for these speculative execution vulnerabilities, applying the fixes comes with the side effect of slightly degraded performance.
- BlueKeep: Remote Desktop as an access vector
Date of Detection: Jan. 2018
Date of Patch: April 2018
Current Status: ACTIVE
Over 30,000+ vulnerable instances found o
Figure 7: Shodan findings for BlueKeep (Source: Shodan.io)
Since 2016, attackers have increasingly used the Remote Desktop Protocol (RDP) to target computers for compromise, exploiting vulnerable RDP sessions to steal personal data, login credentials, as well as install ransomware.
In May 2019, Microsoft released a patch for a remote code execution vulnerability in Remote Desktop Services dubbed “BlueKeep” (CVE-2019-0708). Security researchers considered BlueKeep especially severe because it was “wormable,” meaning attackers could use it to spread malware from computer to computer without human intervention, similar to the WannaCry epidemic discussed earlier in this post. Testifying to the severity of the vulnerability, Microsoft took the unusual step of releasing the BlueKeep patch for Windows XP, which had been out of support for five years at the time and did not ordinarily receive new security updates.
The NSA issued a rare cybersecurity advisory on BlueKeep, citing concerns about malicious cyber actors using the vulnerability in ransomware and exploit kits.
Attacks using BlueKeep were discovered in the wild, but these first attacks merely installed a cryptocurrency miner on the compromised computer and did not take advantage of the wormable aspect of the vulnerability.
- Drupalgeddon Series: CMS Vulnerabilities
Date of Detection: January 2018
Current Status: ACTIVE
Considered an active threat by the FBI. More than 2,000 vulnerable instances were found on Shodan
Figure 8: Shodan findings for Drupalgeddon2
Content management systems (CMS) were frequent targets of attackers and black hat security researchers this decade. In 2014, Drupageddon or Drupalgeddon (CVE-2014-3704), a highly critical SQL injection vulnerability in Drupal Core resulted in threat actors hacking a massive number of websites.
Four years later, the Drupal security team disclosed another extremely critical vulnerability nicknamed Drupalgeddon2 (CVE-2018-7600) that resulted from insufficient input validation on the Drupal 7 Form API and allowed an unauthenticated attacker to perform remote code execution on default or common Drupal installations. Attackers used the Drupalgeddon2 vulnerability to mine for Monero cryptocurrency on servers with compromised Drupal installations. Reports of large-scale scanning and exploitation began circulating within 24 hours of the release of the public exploit for Drupalgeddon2.
A botnet called Muhstik was also reported to be exploiting the vulnerability using XMRig, an open-source mining utility, to mine cryptocurrency with a self-built mining pool.
- Microsoft Windows OLE Vulnerability: Sandworm exploit
Date of Detection: September 3
Date of Patch: October 15, 2014
Current Status: INACTIVE
Another 0-day that received its fair share of coverage was the Microsoft Windows Object Linking and Embedding (OLE) vulnerability (CVE-2014-4114) that was present in every supported version of Windows at that time. The flaw was used in Russian cyber-espionage campaigns targeting NATO, Ukrainian and Western government organizations, and firms in the energy sector. The group of attackers that launched the campaign of attackers was dubbed the “Sandworm Team.” The vulnerability exists in the way the OLE package manager downloaded and executed INF files. The vulnerability allegedly has been in use since August 2013, distributed primarily through weaponized PowerPoint documents.
- Ripple20 Vulnerabilities: Growing IoT landscape
Date of Disclosure: June 16
Date of patch: March 3, 2020
Current Status: ACTIVE
We expect Internet of Things (IoT) vulnerabilities to be a significant player the coming decade, so it was only proper to highlight vulnerabilities that affected IoT in the decade under review. In June 2020, JSOF publicly disclosed a set of 19 vulnerabilities. The vulnerabilities were collectively called Ripple20 to illustrate the "ripple effect" these security defects will have on connected devices for years to come. The vulnerabilities were present in the Treck networking stack, used by more than 50 vendors and millions of devices, including mission-critical devices in healthcare, data centers, power grids and critical infrastructure. When properly exploited, an attacker could gain total control over an internal network device from outside the network perimeter through the Internet-facing gateway. The Ripple20 vulnerabilities also made the term supply chain vulnerabilities popular.
Why is this relevant?
As you have read throughout this report, most of these vulnerabilities were discovered almost a decade ago. Unfortunately, even with fixes and patches being made available, attackers still exploited them in the wild. Our previous report on active state of vulnerabilities showed the same trend for newer and popular vulnerabilities, as well.
So, the questions we now need to ask are: Why are there so many vulnerable publicly exposed servers? Why aren’t patches being applied? Why aren’t organizations working towards fixing their security flaws?
A few causations:
- The lack of ability to track and log various services running on a network
- The ability to vouch for and apply patches to assets of the organization without disrupting workflow
- The slow reaction to discovered zero-days
What lies ahead? The Age of Zero Days
With 2021 opening on a grand note with the Exchange Server RCE bugs and ending with the Log4j exploit, we see a sharp increase in the number of zero-day vulnerabilities. This zero-day tracking project shows the number of zero-days increased two-fold compared to 2020. More than 59 zero-days were logged in 2021. These zero-day vulnerabilities created a cybersecurity nightmare for organizations incurring about $6 trillion in damages. Making matters worse for cybersecurity teams is the fact that as Proof of Concepts (POCs) have become publicly available major threat actors and even hobbyists have joined in on hunting and exploiting vulnerable instances adding to more logging woes.
Many researchers sell their zero-day exploits for hefty sums of money either to bounty programs like
With the addition of new approaches of security, Improved firewall technology, Sophisticated end point detection and response systems (EDR) and Implementation of AI shows how necessity breeds rapid innovation. Cybersecurity solutions have seen major progress over the years and are in great shape to face what is yet to come.
如有侵权请联系:admin#unsafe.sh







