2022-7-19 21:0:0 Author: blog.avast.com(查看原文) 阅读量:20 收藏
A reminder that you can’t be too careful, especially when it comes to clicking on those PDFs.
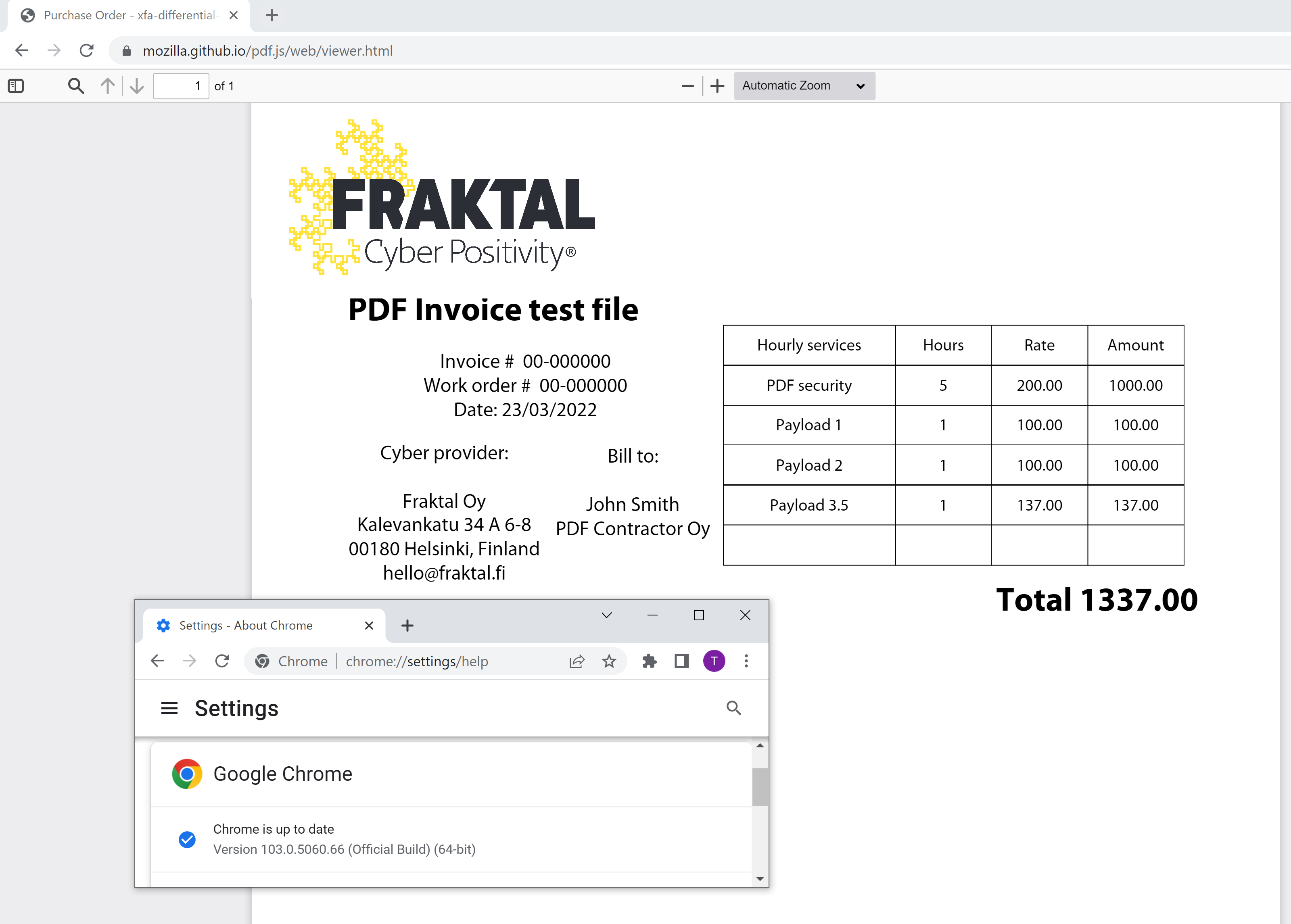
The next time someone sends you an email with a PDF attachment, take a moment before clicking to open it. While most PDF files are benign, hackers have recently been using PDFs in new and very lethal ways. Malicious PDFs are nothing new. A good place to start is this talk at the 2020 Black Hat conference, which dives into how malicious PDFs can be created and some of the various threats involved. These exploits can also be useful for security personnel, such as this open source tool that can test your own defenses by creating your own threats. Let’s take a look at a couple of recent news items, how the PDF landscape has changed, and the lessons that we all can learn from these developments. First, we examine what researcher Toni Huttunen calls “a parser differential attack targeting PDF readers.” This is a theoretical attack where a specially crafted document looks differently, depending on the PDF reading software used to view it. The attack challenges our belief that a document’s content is the same, no matter how it is viewed. Certainly, I was guilty of this assumption until I read Huttunen’s blog post. One of the reasons why the PDF is so popular is because of its universality – it can be viewed by users no matter what device, operating system, or app they are using. However, a hacker can encode a malicious PDF quite easily – the above post describes a test invoice that shows a different amount due, depending on the browser chosen, as you can see in the below screen caps. Image credit: Fraktal The author reported the issue to both Mozilla and Adobe, both of whom declined to fix the problem and rejected the claim as a security issue. It has not yet been observed in the wild, but clearly, something like this is a possibility. The second PDF problem is more visceral and concerns how a malicious PDF can be used to subvert the job application process. Earlier this year, a hacker created a fake job opening and sent a phishing message to a target working for Sky Mavis, the company behind Axie Infinity, a popular crypto-based computer game. The target was an engineer, and the message was sent via LinkedIn, which immediately gave it some credibility. The engineer went through what appeared to be legitimate interviewing rounds and was eventually offered the job with a big raise. The offer letter was, as you've undoubtedly figured out by now, a PDF attachment that contained malware to log the engineer’s keystrokes and use this information to infiltrate the company’s blockchain logins. About $600M in equivalent value was stolen from their crypto accounts. The FBI and other security researchers have said the North Korean state-sponsored Lazarus group was responsible. Sky Mavis posted this port-mortem analysis of the hack. Since the time of the attack, the company has implemented a series of security measures, including better authentication and internal review procedures, a bug bounty program, more code security audits, and a move towards more zero-trust frameworks. While these are all steps in the right direction, these measures should have been in place from the beginning, especially given the financial orientation of their application. Ultimately, what these two instances demonstrate is that you can’t be too careful, especially when it comes to clicking on those PDFs. Adobe has suggestions in this post, and the tips involve running antivirus, being more aware of common phishing exploits, and not downloading any untrusted PDF readers.
Creating fake job listings
如有侵权请联系:admin#unsafe.sh